Due to the growth of the internet and communication technologies, electronic financial systems are becoming popular. Physical cash is losing its preeminence, and digital numbers on computers represent money. However, electronic financial systems, mostly operated by private entities, have defects to be compensated for, such as high charges for using the system, security issues, and the problem of exclusion. As a solution, many countries around the world are considering central bank digital currency. For central bank digital currency to be utilized as a national legal tender, it must be universal and accessible regardless of time and place, similar to physical cash. Therefore, offline payment functions that extend the accessibility of central bank digital currency are becoming attractive.
1. Central Bank Digital Currency
Physical cash, paper notes, and coins have been the key medium of exchange in conventional financial systems for a long time
[1]. However, in the last few decades, due to the growth of the internet and communication technologies, physical cash has been losing its preeminence
[1]. Electronic financial systems have become widespread, with digital numbers on computers representing money rather than physical cash. It is a well-known fact that monetary policies, such as the open market operation, quantitative easing (QE), or quantitative tightening (QT), are executed not by printing or collecting paper notes but by using electronic funds created with keystrokes on computers
[2][3].
The changes can be seen more easily in the retail sector. Technological advances are deregulating the financial industry, and many people have already become used to various payment methods operated by various entities, such as credit cards, online banking services, mobile payments, etc.
[1][4][5]. Some countries are already at the stage of a so-called “cashless society”
[6]. In 2016, the share of cash used for all payments in South Korea was only 14%; in China, 18%; and in the UK, 24%. The share of cash used in the United States in 2020 was 19%
[7][8][9].
Electronic financial systems are considered to have advantages compared to conventional financial systems mainly for two reasons. First, electronic financial systems are considered to be more transparent than conventional financial systems. Unlike conventional financial systems based on physical cash, which has the characteristic of anonymity, in electronic financial systems, transactions between users can be watched and logged. Therefore, malicious users and unlawful acts can be traced and detected. Second, electronic financial systems can enable flexible and easy use of money and help vitalize the economy. In countries where electronic financial systems are in use, people can use bank services and join in e-commerce anytime and anywhere they want, as the digital currency used in the systems is free from physical constraints. This could increase the amount of currency in circulation and contribute to economic stabilization
[10].
Even with these advantages, electronic financial systems still have some defects to be compensated for. First, electronic financial systems usually have charges for using the system, resulting in an additional cost to use money or currency
[11]. For example, credit card networks routinely charge card fees of 3%
[11]. E-wallet (electronic wallet) services managed by Sticpay charge 1~3.85% of deposit fees
[12]. Such high charges can attenuate economic activity and commerce
[11]. Second, without proper security policies, personal data breaches can occur in electronic financial systems. Electronic financial systems are vulnerable to digital attacks by their nature. Access to the systems via the internet, or any other possible measures, is open to anonymous users at all times. Further, when personal data breaches occur, the quantity of data breached at once could be large. In 2019, when Capital One, the fifth largest credit card issuer in the United States, was hacked, the personal data of 106 million customers were leaked
[13]. In 2014, the user information of at least 20 million people was leaked in Korea, a country of 50 million
[14]. Third, in electronic financial systems, the problem of financial exclusion, which refers to individuals and populations without access to common financial services, can occur. For instance, China is a country where electronic financial systems such as Alipay and Wechat are widely used. However, China’s rural and farm communities use internet technologies only half as much as all users, and less than 2% access credit through the internet
[15]. Additionally, many commercial electronic financial systems are closed to people with low credit ratings
[16].
As a solution to these problems, many countries are considering central bank digital currency (CBDC). The International Monetary Fund (IMF) defined CBDC as a digital representation of a sovereign currency issued by and a liability of a jurisdiction’s central bank or other monetary authority
[17]. Under the CBDC system, the central bank directly manages the whole currency circulation, which is the biggest difference from the current electronic financial systems operated by various commercial entities and brings many advantages. First, the central bank’s intervention in the payment system will minimize many steps in money circulation and promote competition between entities operating the electronic financial systems. As JP Morgan predicted, this could save charges for the system use that are spent in the present electronic financial systems
[18]. Second, users will not need to use various commercial payment systems, and thus, the possibility of personal data breaches will be reduced. Unlike electronic financial systems that leave data trails through a number of commercial entities, under the CBDC system, the central bank directly manages personal data
[19]. Third, the CBDC system can solve the problem of financial exclusion. Unlike electronic financial systems that do not provide financial services to unbanked people, estimated to be almost 1.7 billion people worldwide, under the CBDC system, CBDCs can be directly provided to users without using traditional bank accounts
[20][21]. Blockchain technology is regarded as the option that can strengthen the merits of the CBDC system, as it is based on distributed ledger technology (DLT), which does not need intermediaries and is well known for its strong security.
2. Countries Developing CBDCs and Types of CBDCs
Numerous countries are developing CBDCs through pilot projects, and some of those countries have already introduced them as the national legal tender. Sweden is one of the countries currently considering adopting CBDC, E-krona, to decrease dependence on foreign electronic financial systems, such as Visa and Mastercard. The cash in circulation has fallen to 1% of its gross domestic product (GDP)
[22][23][24][25]. Uruguay is also considering introducing CBDC, E-peso, to overcome the underdeveloped infrastructure issue in electronic financial systems
[26][27]. The Bahamas is one of the countries that have already adopted CBDC. In 2020, the government of the Bahamas introduced the Sand Dollar, and it boosted digital transactions between people using smartphones, regardless of the existing electronic financial systems
[28]. The Republic of the Marshall Islands, where the US dollar has been the public currency, issued a CBDC named Sovereign (SOV) to reduce the dependence on the US dollar and activate cross-border transactions
[29][30]. China introduced the world’s largest CBDC system, E-CNY (digital yuan). To date, the number of digital yuan wallets exceeds 123 million, and the accumulated amount of E-CNY used in transactions is almost CNY 56 billion
[31]. The Cambodian government and the Nigerian government also introduced CBDCs named Bakong and E-Naira.
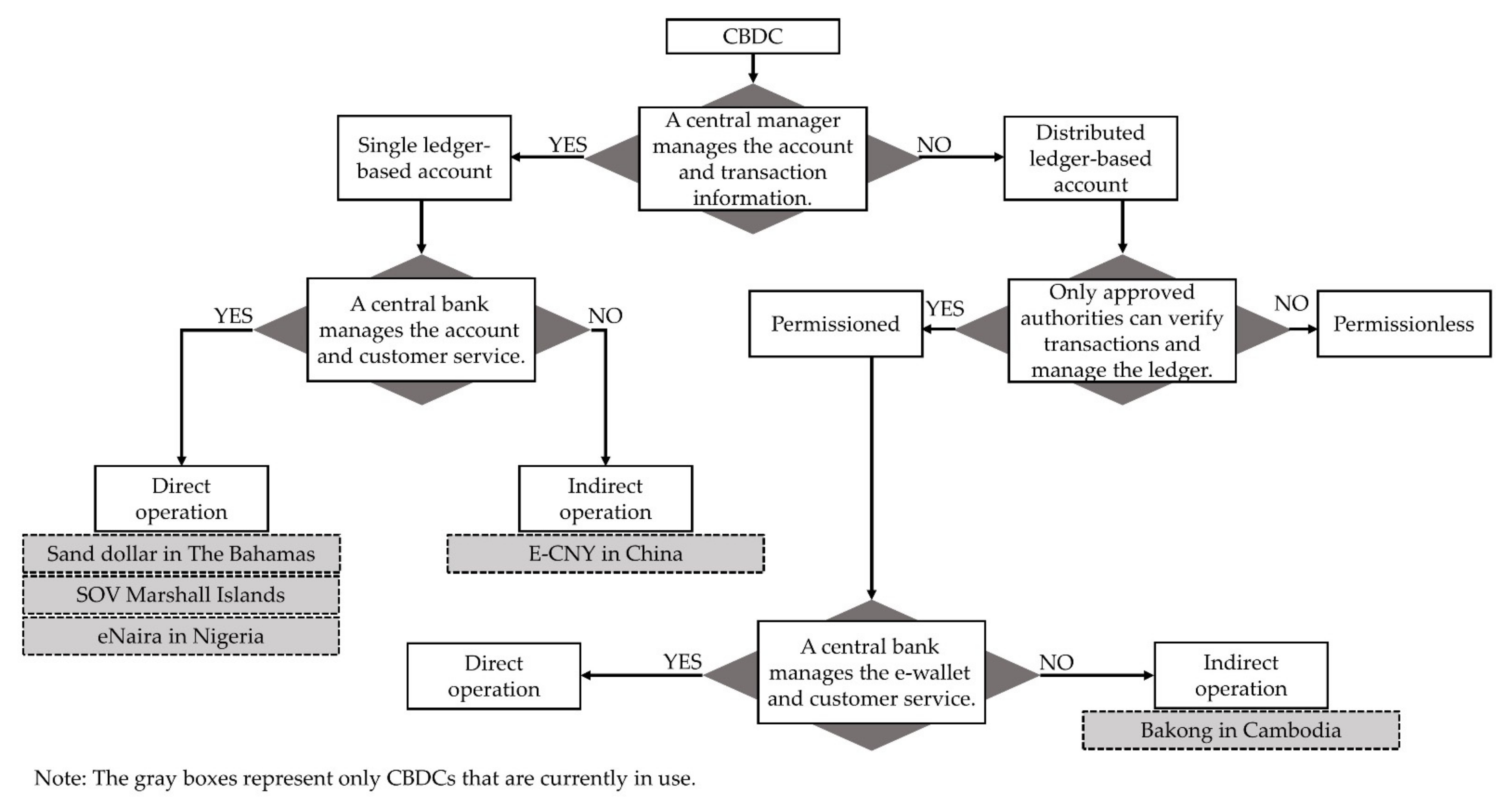
The CBDC systems that various countries are testing or already using take various forms depending on the purpose and can be classified according to three criteria
[26]. First, the CBDC systems can be classified into the single-ledger-based system and the distributed-ledger-based system, according to the number of entities that manage the ledgers. Under the single-ledger-based system, it is the central authority, such as the central bank alone, which manages the ledger, and the central organization can manage the whole financial system with a uniform standard. However, this type of CBDC system can become vulnerable if the central authority is accidentally or maliciously shut down
[32]. Under the distributed-ledger-based CBDC system, a concept opposite to the single-ledger-based system, transaction records are consensually shared and synchronized through a ledger that multiple entities can access
[33]. The distributed-ledger-based system provides transparency by sharing the authority of managing among multiple entities and helps reduce the possibility of a concentrated digital attack through the distributed structure
[34]. Second, the CBDC systems can be classified into the permissioned system and the permissionless system depending on whether only authorized entities can access the ledger or not. The permissioned CBDC system is based on a distributed ledger that is not publicly accessible. In this system, only users authenticated through certificates or other digital means can access the ledger and perform specific actions approved by the managing authority
[35]. The permissionless CBDC system refers to a CBDC in which all entities can use the system without special permission. The permissioned CBDC system is regarded as faster and more efficient than permissionless CBDC but is not transparent and not helpful in solving the problems of financial exclusion
[36]. Third, depending on whether the central bank directly provides financial services, the CBDC systems can be classified into the direct CBDC system and the indirect CBDC system. In the direct CBDC system, the central bank provides financial services to users, and all transaction records are managed by the central bank. On the other hand, under the indirect CBDC system, the central bank delegates the managing authority of financial systems to intermediaries, and the central bank only manages the intermediaries
[37]. The various forms of CBDCs mentioned so far are expressed in
Figure 1, and following the classification criteria, the CBDC systems currently in operation are categorized in
Figure 1 and
Table 1.
Figure 1. Different forms of the CBDC systems.
Table 1. CBDCs in use worldwide.
3. Importance of the Offline Payment Function of CBDCs and Security Requirements
Regardless of type, all CBDCs have one important feature in common—CBDCs are the national currency that is to be used as legal tender replacing the physical cash. Like cash, it should be accepted irrespective of all circumstances. However, the CBDC system is basically an electronic financial system where users are required to be connected to the internet, and for this reason, so far, CBDCs have not truly worked as a national legal tender.
CBDCs, which can be used only with the internet, can exclude many people who cannot use the internet from financial services. Further, if the system is shut down due to power outages and cyberattacks, financial services could turn out to be unavailable, which could cause a lot of confusion. Therefore, China and the Bahamas, where the CBDC system is already introduced, are reviewing the offline payment function of CBDCs, and the number of countries that are considering the offline payment function of CBDCs is expected to increase in the future
[38].
The offline payment function of electronic financial systems is defined as a transaction function that does not require internet or telecom connectivity
[39]. Under the electronic financial system with an offline payment function, people can use digital money stored in portable devices regardless of the communication environment, and therefore, the problems of financial exclusion or system malfunction, mentioned previously, are expected to be solved. However, the electronic financial system with an offline payment function is in a blind spot of security problems—not only portable devices but also transactions in an offline situation are isolated from the main system. Malicious behaviors, such as hacking attempts on portable devices or fraudulent transactions that exploit the system, cannot be detected in real time.