
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Behrouz Zolfaghari | -- | 5068 | 2022-07-21 09:06:49 | | | |
| 2 | Vivi Li | -1 word(s) | 5067 | 2022-07-22 03:35:50 | | | | |
| 3 | Vivi Li | + 52 word(s) | 5119 | 2022-07-27 10:16:03 | | |
Video Upload Options
Chaos is the characteristic of a system whose current state is guaranteed to be highly sensitive to the previous state (spatial chaos), the initial conditions (temporal chaos), or both (spatio-temporal chaos). Such a sensitivity makes the output or the behavior of a chaotic system difficult to predict. Chaos theory justifies and formulates the apparent disorder of chaotic systems on the basis of orderly patterns, structured feedback loops, iterative repetitions, self-organization, self-similarity, fractals, etc. Chaotic maps, attractors, and sequences all refer to the mathematical structures used for this formulation. Chaotic systems, maps, attractors, and sequences have been of great interest to the research community. They have been used for security purposes in a broad variety of applications ranging from smart grids to communication systems. Especially, chaotic encryption has been used for encrypting a variety of content types in addition to images.
1. Introduction
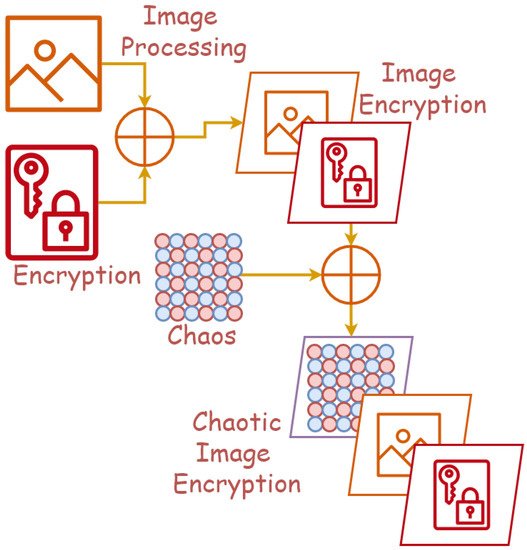
2. Chaotic Image Encryption
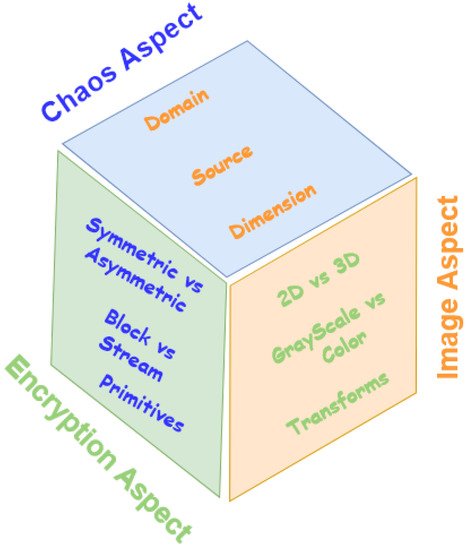
2.1. State-of-the-Art in Chaos Aspect
2.1.1. Chaos Domains
Spatial Chaos
Temporal Chaos
Spatiotemporal Chaos
2.1.2. Chaos Sources
Mathematical Sources
-
Chaotic systems and mapsThese are functions originally designed for creating chaos. Chaotic systems and maps play a critical role in chaotic image encryption. To mention a few, one may refer to the following:
- –
-
Fractional-order chaotic systemFractional calculus goes back more than 300 years, with modern studies focusing on systems such as the fractional-order Chen, Lorenz, and Liu systems [15]. A novel switching fractional-order chaos system was proposed by Hou [15] and utilizes controlling switches to switch between its sub-systems and achieve a strong chaos source for applying the exclusive Or (XOR) operation against the plaintext image.Another algorithm utilizing fractional-order systems was proposed by Wei [16], which opts to use a more standard third-order fractional system, as well as a novel Josephus scrambling algorithm and circular diffusion to achieve desirable encryption properties and resilience against common attacks.
- –
-
Arnold cat mapArnold mapping is a well-know transposition chaotic map that, in the context of cryptography, was used by Ranimol and Gopakumar [17], as well as Zhang et al. [18] to provide a method of permutating and de-correlating adjacent pixels in their proposed encryption algorithms. Both algorithms were proven to exhibit a large keyspace with high key sensitivity and be capable of resisting common attacks such as brute force, entropy, CPT, and KPT.
- –
-
Coupled map latticeA Coupled Map Lattice (CML) is a form of spatiotemporal chaos map efficient for random number stream generation. In one use case, Wu [19] proposed a novel implementation of the CML to create encryption streams dependent not only on initial values, but also on intermediate cipher images by using said ciphertexts to modify the CML parameters. This adds a layer of plaintext dependency, which aids in the defense against several attacks.
- –
-
Lorenz mapA Lorenz system is a type of differential equation that is highly susceptible to initial conditions. Jiang and Fu [20] proposed an image encryption procedure in which the key is composed of the three inputs to a 3D Lorenz system and utilizes the chaotic nature of said system to provide strong security.
- –
-
Logistic mapA logistic map is a relativity simplistic mathematical mapping function, which when influenced by particular control values, acts chaotically. An algorithm proposed by Sharma and Bhargava [21] utilizes a two-step interactive logistic map, where the next input is dependent on the previous two outputs, as a source of chaos. Similar work was performed by Li-Hong et al. [22], where they used a more standard logistic map and paired it with a hyper-chaos system to improve key generation effectiveness. Likewise, Mu and Lui [23] also found success utilizing the logistic map for key generation.
- –
-
Tent mapWu et al. [24] proposed an image encryption algorithm using the CTM, and the rectangular transform was later analyzed by Zhu et al. [25] and improved upon to better protect against plaintext attacks such as CPT and KPT. The Chaotic Tent Map (CTM) is a mapping function that, when configured with control values in a particular range, behaves chaotically.
- –
-
Lotka–VolterraA Lotka–Volterra chaotic system is a third-order differential equation in a similar family to other systems such as Lorenz, Rossler, Shua, and Chen. In a particular case study by Zahir et al. [26], an encryption procedure was proposed that utilizes the Lotka–Volterra chaotic system to aid in the creation of Substitution boxes (S-boxes) with strong confusion properties. The resulting S-boxes were found to satisfy the five criteria (bijective, non-linearity, strict avalanche, bit independence, input/output XOR distribution) required for acceptable use in cryptographic algorithms.
- –
-
Henon mapThe Henon map was first discovered in 1978 and can be described as a 2D mapping function with two control parameters, which, when chosen strategically, enable the map to behave chaotically. Tresor et al. [27] proposed an image encryption algorithm utilizing Henon maps for shuffling the pixels of the image and 4D Qi hyper-chaos to generate keys for encryption. Experimental analysis of the algorithm demonstrates strong cryptographic properties and resistance against common attacks.
- –
-
Logistic-sine systemA Logistic-Sine System (LSS) is a discrete combination of the logistic and sine maps, both of which exhibit chaotic behavior under particular initial conditions. Zeng and Chen [28] referred to such a combination of the two maps as a compound chaotic map and utilized it in a novel encryption algorithm using XOR and modulus operations.Zhao et al. [29] investigated the inefficiencies with single chaos systems and proposed a novel algorithm utilizing LSS and cascade chaos to improve upon said inefficiencies. Experimental analysis through simulation has proven the new algorithm to be highly resilientIn another study, Lu et al. [30] conducted cryptanalysis on an existing algorithm based on multiple S-boxes, but were able to break it using CPT attacks. A new algorithm was proposed to improve upon the old one and involved only a single S-box constructed utilizing LSS. Further cryptanalysis of the new algorithm showed improvement over the original and was also quite fast.Variants of LSS have also been employed in encryption algorithms, such as a 2D Logistic Modulated Sine Coupling Logistic (LSMCL) map proposed by Zhu et al. [31], a Logistic Sine Modulation Map (LSIMM) proposed by Zhang et al. [32], and a 2D Logistic Adjusted Sine Chaotic Map (LASCM) proposed by Balakrishnan and Mubarak [33]. In all cases, theoretical analysis and simulations determined the algorithms to be both secure and efficient.
- –
-
Baker mapThe baker map is a bijective permutation function that operates on an MxM matrix by randomizing its cells according to a secret key and is well respected in the image encryption community. Elshamy et al. [34] utilized the baker map in an image encryption algorithm to improve upon a classic technique known as Double Random Phase Encoding (DRPE). The proposed algorithm uses the map to pre-process the image before applying DRPE, and experimental analysis showed significant increases in security as opposed to using DRPE alone.Another algorithm utilizing the baker map was proposed by Tong et al. [35], where high-dimensional dynamical multiple chaos was paired with the baker map to achieve a larger avalanche effect. Experimental results again showed significant increases in security when
- –
-
Tinkerbell mapKrishna [36] proposed an encryption algorithm utilizing Tinkerbell maps, a pair of chaotic functions, to inject strong pseudo-random numbers in multiple points during the encryption and decryption process. Differential and correlational analysis of the algorithm showed the proposed method to be highly efficient.
- –
-
Cubic mapA cubic map is a single-dimensional chaotic function that produces values on the interval [0, 1] and can be controlled by a single mapping parameter. Kavinmozhi et al. [37] proposed an encryption technique that employs a hybrid chaos source composed of the cubic and tent maps, as well as the Iterative Chaotic Map with Infinite Collapses (ICMICs). The resulting hybrid map is used with the XOR operation to achieve encryption, and an analysis of the algorithm showed that it is suitable for repeated use and is resilient against attacks.
- –
-
Gingerbreadman mapSavitri et al. [38] used the Gingerbreadman map, a 2D chaotic map, to generate encrypted keys for use with the well-known Cipher Block Chain (CBC) encryption algorithm. Using the map in this algorithm greatly improves CBC’s performance when applied to images, and a visual comparison demonstrated massive improvements.
- –
-
Tangent mapMoysis et al. [39] proposed a Random Number Generation (RNG) algorithm based on the usage of the mathematical hyperbolic tangent function. When the RNG algorithm was applied to image encryption, the resulting procedure demonstrated strong cryptography
- –
-
Multiple mapsMixing multiple mapping functions in image encryption algorithms can serve multiple purposes. For example, Bisht et al. [40] employed a verity of different maps to achieve tasks such as more chaotic permutation, diffusion, and RNG. A similar technique employing various maps in different stages of the encryption procedure was also proposed by Wang et al. [41].Fu et al. [42] proposed a novel keystream generation technique utilizing multiple chaotic maps that incorporates the plaintext itself into the stream. The algorithm was motivated by the need to defend against CPT and KPT attacks, and an analysis of the algorithm showed it is effective in achieving its goal.In terms of areas of application, stronger algorithms enforced by the use of multiple chaotic maps are important in numerous fields. For example, Choi et al. [43] proposed an algorithm using multiple maps for encrypting colored medical images, which can be seen as unique in their size and sensitivity. Experimental and statistical analysis of the resulting procedure showed it is secure for use with healthcare images.
-
Other mathematical sourcesIn addition to chaotic systems and maps, some researchers have used the following mathematical designs, which have not been originally defined for chaos creation:
- –
-
Space-filling curvesFractal geometry has several intriguing properties, such as self-similarity, composition by iterative methods, and a complex structure. Zhang et al. [44] utilized Hilbert curves and H-fractals, types of self-filling curves, in a novel image encryption algorithm. This algorithm alternates the use of both curves to efficiently scramble the pixels of the image.
- –
-
Memory cellular automataCellular Automata (CA) can best be described as a grid of cells with a finite set of states and a transition function that governs how cells change state over time. Whereas a standard CA only depends on the generation t-1, Memory Cellular Automata (MCA) depend on more parameters. When the MCA’s rules are defined by chaotic maps, the structure becomes a powerful tool for image encryption. Several algorithms using various-order MCAs have been proposed, for example a 4D MCA by Aslam et al. [45], a 2D MCA by Hibibipour et al. [46], and an indefinite CA by Hibibipour et al. [47].
- –
-
Transcendental numbersIn mathematics, a transcendental number has the characteristic that digits to the right of the decimal have no pattern [48]. Garcia et al. [48] proposed an image encryption algorithm that uses chaos and the transcendental number Pi, dubbed Chaotic Pi Ciphering (CPC). The algorithm uses Pi and a chaos source created using differential equations to generate cipher keys and substitution boxes.
Physical Sources
-
Optical ChaosOur physical world can provide many forms of chaos, with just one example being light. In studies by Xie et al. [49] and Lui et al. [50], they found success in producing a chaotic base for image encryption algorithms using lasers. Extensive security testing of both algorithms showed them to be highly secure and feasible for practical use.
-
Chaotic circuits
- –
-
Chua circuitSome physical electronic circuits such as the Chua circuit can produce chaotic behavior. AlMutairi et al. [53] utilized the circuit as a key generator in their proposed image encryption algorithm. By contrast, Lin et al. [54] proposed a similar encryption model, but instead utilized a variant of the classic Chua circuit with a PWL memristor. In both cases, analysis showed the algorithms to exhibit strong security properties.
- –
-
Memristive circuitsA memristor is a form of electrical component that is capable of exhibiting chaotic behavior. Liu et al. [55] proposed an image encryption algorithm that utilizes 4D memristive hyper-chaos to create chaos matrices. Security analysis showed strong security and cryptographic properties.Another image encryption algorithm was proposed by Sun et al. [56] using a memristive chaotic system. The presented system demonstrates a unique property known as multistability, which further improves the chaoticness of the system. Again, security analysis showed the algorithm to possess strong cryptographic properties.
- –
-
Physically Unclonable Functions (PUFs)True Random Number Generators (TRNGs), although very important in cryptography, are impossible to achieve in software. To counter this fact, Muhammad et al. [57] proposed an encryption algorithm using a hardware device, a form of physically unclonable function, to generate true random numbers. Through extensive experiments and analysis, the TRNG was successful in passing all tests required for safe use in cryptographic algorithms.
2.1.3. Chaos Dimension
-
One-dimensionalWork with one-dimensional chaos includes that by Wang and Lui [58], where the novel 1D Sine Chaotic System (1DSCS) was proposed. This system exhibits a large parameter interval as compared to the standard sine map it was built upon.Elghandour et al. [59] proposed an image encryption algorithm utilizing the 1D tent map. A similar algorithm also using the tent map was proposed by Tiwari et al. [60]. Extensive testing proved both algorithms to be effective at resisting common cryptographic attacks. The former paper also elaborated on the low chaotic range for the tent map and suggested that future work use a variant with a larger range such as the tent-sine map.
-
Two-dimensionalAn image encryption algorithm based on two-dimensional chaos was proposed by Yang and Tong [61]. This algorithm uses the 2D logistic chaotic system and a novel block image encryption procedure. Experimental results demonstrated the algorithm to have strong randomness, low pixel correlations, and high key sensitivity.
-
Three-dimensionalMany image encryption algorithms utilize three-dimensional chaos. One such algorithm was proposed by Qian et al. [62], where they utilized the 3D logistic and cat maps. The novel usage of image reconstruction techniques also improved the effectiveness of the algorithm.In an algorithm proposed by Asl et al. [63], the 2D image was converted into three-dimensional space by creating three streams from the red, green, and blue channels of the image. The 3D modular chaotic map was used as the chaos source for encryption.
-
Four-dimensionalHuang et al. [66] proposed a novel four-dimensional chaos system based on concepts known as “shape synchronization” and “driver-response”. The complex mathematical underpinnings make the algorithm very difficult to break, and experimental tests in the application of image encryption showed promising results for its effectiveness.
-
Five-dimensionalZhu and Zhu [67] proposed a novel five-dimensional chaotic map composed of the 2D logistic map and 3D discrete Lorenz map. Experimental simulations of the system when applied to image encryption resulted in high scores in many common encryption strength tests.
-
Multiple dimensionalWork related to mixing maps of varying dimensions in image encryption has also been performed. For example, Qui and Yan [68] proposed an image encryption algorithm using both the 1D logistic map and 3D Lorenz system. Experimental results demonstrated that the algorithm has strong security.Parida et al. [69] proposed a novel image encryption and transmission procedure based on Elliptic Curve Cryptography (ECC). Encryption is achieved using 3D and 4D Arnold cat maps as chaos sources, and the Elliptic Curve Diffie–Hellman (EDCH) key exchange algorithm is utilized to establish a shared key between parties. Digital signatures allow the algorithm to authenticate the encrypted message before decryption, and experimental results showed the method to be effective.
2.2. State-of-the-Art in the Image Aspect
2.2.1. Two-Dimensional versus Three-Dimensional Image
2.2.2. Gray-Scale versus Color Image
2.2.3. Transforms
Wavelet
Zigzag Transform
Cosine Transform
Contourlet Transform
Linear Canonical Transform (LCT)
2.3. State-of-the-Art in the Encryption Aspect
2.3.1. Symmetric versus Asymmetric Cryptography
2.3.2. Block Cipher vs. Stream Cipher
-
BlowflishBora et al. [89] proposed a block cipher using the Blowfish algorithm and cross-chaos map. Cryptanalysis results showed strong security.
-
Ecliptic Curve Cryptography (ECC)Abbas et al. [90] proposed an Ecliptic-Curve (EC)-based algorithm that utilizes pixel-level parallelism for faster encryption speeds. A different proposal by Benssalah and Rhaskali et al. [91] uses ECC combined with the Hill cipher and Arnold cat map to achieve a strong encryption algorithm targeted at medical images.
-
El-GamalEl-Gamal is a type of EC commonly utilized in cryptography. For example, Luo et al. [92] proposed a public-key-based image encryption algorithm utilizing the El-Gamal EC to address common issues with key management. In another proposal by Yousif et al. [91], El-Gamal was used to encrypt images that were first permutated using zigzag and spiral scanning.
-
RijindalDsouza and Sonawane [93] proposed a novel technique of using images as the key to encrypt/decrypt a directory in a file system. This technique employs both AES and Rijideal ciphers, and evaluation results demonstrated its effectiveness.
-
Rivest–Shamir–Adleman Cryptosystem (RSA)Nkapkop et al. [94] developed a novel asymmetric image encryption algorithm using RSA to solve the issue of key management. This algorithm uses the RSA key pairs to encrypt the initial values and parameters of the chaotic function so that the public key can encrypt images and only the private key can decrypt.
-
Data Encryption Standard (DES)Zhang et al. [95] proposed an image encryption algorithm utilizing the logistic chaos sequence for chaotic sequence generation and an improved DES algorithm for encryption. Simulation results demonstrated good security and speed, making it suitable for real-time use.
-
Novel block ciphersGupta et al. [96] proposed a novel block cipher using two keys where the image is split into four blocks; each is encrypted n times, and finally, the keys are inverted and the blocks further encrypted m more times. Evaluation through standard tests demonstrated strong cryptographic properties, making the algorithm usable for real-time connections.Rani and Kumar [97] proposed a novel stream cipher using a modified RC4 algorithm. The algorithm converts the image into three vectors for each color channel and uses the modified RC4 stream algorithm to encrypt them. Another algorithm utilizing the RC4 stream cipher was proposed by Ginting and Dillak [98]. This algorithm uses the logistic map to generate a keystream for encryption. The algorithm is lossless, which was verified by comparing the hash values of the image before encryption and the image after encrypting, then decrypting.
-
Hybrid ciphersA hybrid approach utilizing both block and stream ciphers was proposed by Goumidi and Hachouf [99]. This algorithm splits the image into two sub-images and encrypts one using the block cipher and the other using the stream ciphers. The encrypted sub-images are then merged back together to form the final image. The use of two different types of ciphers greatly increases the complexity of the algorithm, leading to stronger cryptographic properties.
2.3.3. Primitives
Scrambling
Bit Shuffling
Hashing
Permutation, Substitution, Confusion, and Diffusion
-
Permutation and diffusionPermutation is the process of rearranging elements in a structure, which, in the context of images, refers to scrambling the pixels. Abd-El-Hafiz et al. [107] performed an evaluation on three different permutation methods (discrete chaos, vectors, and Arnold cat map) and found that discrete performed the best.Diffusion is the process of ensuring there is no statistical significance to the resulting structure. In the context of images, this refers to scrambling the pixels of the image to eliminate the correlation between adjacent pixels. Ping et al. [108] proposed a novel digit-level permeation algorithm that additionally employs a high-speed diffusion algorithm. Evaluation results demonstrated high security and efficiency.Combining permutation with diffusion into the same stage of encryption aims to combat hackers who try to break each stage separately [109]. Liu et al. [110] proposed an algorithm to perform permutation and diffusion simultaneously. The algorithm additionally uses a Hopfield chaotic neural network to perform further diffusion, which gives the algorithm greater key sensitivity.
-
ConfusionConfusion in encryption refers to the level of dependency elements of the cipher-text have with the key. As seen with permutation, confusion is often integrated with diffusion for the same reasons. For example, Run-he et al. [111] proposed an image encryption algorithm that achieves an integration of confusion and diffusion by XORing the plain image with chaotically generated offset matrices.
-
SubstitutionSubstitution involves replacing an element with something else in a predictable and invertible manner. The substitution requirement is commonly implemented using S-boxes, which are matrices that define how each input maps to its substituted value.For image encryption, chaos-based S-boxes include those generated from the chaotic sine map [112] and the logistic map [113]. Wang and Zhang [114] also proposed an algorithm with multiple S-box substitutions, where the order of the boxes is determined by a random chaos sequence. Another algorithm proposed by Khan et al. [115] splits the image into four blocks and applies a different S-box to each block. These S-boxes each originate from a different encryption algorithm (AES, PQL, APL, and Shipjack). Another paper by Lidong et al. [116] proposes a dynamic encryption algorithm so that the cipher image is always different even if the same key and plain image are used.
One-Time Key
Secret Sharing
References
- Preishuber, M.; Hütter, T.; Katzenbeisser, S.; Uhl, A. Depreciating motivation and empirical security analysis of chaos-based image and video encryption. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2137–2150.
- Lin, C.; Pham, D.; Huynh, T. Encryption and decryption of audio signal and image secure communications using chaotic system synchronization control by tsk fuzzy brain emotional learning controllers. IEEE Trans. Cybern. 2021, 1–15.
- Zolfaghari, B.; Bibak, K.; Koshiba, T. The odyssey of entropy: Cryptography. Entropy 2022, 24, 266.
- Bibak, K.; Ritchie, R.; Zolfaghari, B. Everlasting security of quantum key distribution with 1k-dwcdm and quadratic hash. Quantum Inf. Comput. 2021, 21, 181–202.
- Dong, T.; Huang, T. Neural cryptography based on complex-valued neural network. IEEE Trans. Neural Netw. Learn. Syst. 2020, 31, 4999–5004.
- Zolfaghari, B.; Bibak, K.; Nemati, H.R.; Koshiba, T.; Mitra, P. Statistical Trend Analysis on Physically Unclonable Functions: An Approach via Text Mining; CRC Press: Boca Raton, FL, USA, 2021.
- Dai, J.; Hao, X.; Yan, X.; Li, Z. Adaptive false-target recognition for the proximity sensor based on joint-feature extraction and chaotic encryption. IEEE Sens. J. 2022, 11, 10828–10840.
- Liu, S.; Liu, S.; Sun, F.S. Spatial chaos-based image encryption design. Sci. China Ser. Phys. Mech. Astron. 2009, 52, 177–183.
- Faragallah, O.S.; Afifi, A.; El-Shafai, W.; El-Sayed, H.S.; Naeem, E.A.; Alzain, M.A.; Al-Amri, J.F.; Soh, B.; El-Samie, F.A. Investigation of chaotic image encryption in spatial and frft domains for cybersecurity applications. IEEE Access 2020, 8, 42491–42503.
- Wang, J.; Chen, G. Design of a chaos-based digitlal image encryption algorithm in time domain. In Proceedings of the IEEE International Conference on Computational Intelligence & Communication Technology, Ghaziabad, India, 13–14 February 2015.
- Ge, X.; Liu, F.; Lu, B.; Wang, W.; Chen, J. An image encryption algorithm based on spatiotemporal chaos in dct domain. In Proceedings of the 2nd IEEE International Conference on Information Management and Engineering, Chengdu, China, 16–18 April 2010.
- Luo, Y.; Du, M.; Liu, D. Jpeg image encryption algorithm based on spatiotemporal chaos. In Proceedings of the Fifth International Workshop on Chaos-fractals Theories and Applications, Dalian, China, 18–21 October 2012.
- He, B.; Zhang, F.; Luo, L.; Du, M.; Wang, Y. An image encryption algorithm based on spatiotemporal chaos. In Proceedings of the 2nd International Congress on Image and Signal Processing, Tianjin, China, 17–19 October 2009.
- Wang, X.; Feng, L.; Wang, S.; Chuan, Z.; Zhang, Y. Spatiotemporal chaos in coupled logistic map lattice with dynamic coupling coefficient and its application in image encryption. IEEE Access 2018, 6, 2169–3536.
- Hou, J.; Xi, R.; Liu, P.; Liu, T. The switching fractional order chaotic system and its application to image encryption. IEEE/CAA J. Autom. Sin. 2017, 4, 381–388.
- Wei, J.; Zhang, M.; Tong, X. Image encryption algorithm based on fractional order chaotic system. In Proceedings of the IEEE 12th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 20–22 August 2021.
- George, R.T.; Gopakumar, K. Spatiotemporal chaos in globally coupled nca map lattices using 3-d arnold cat map for digital image encryption. In Proceedings of the First International Conference on Computational Systems and Communications (ICCSC), Trivandrum, India, 17–18 December 2014.
- Zhang, Y.; Xie, J.; Sun, P.; Huang, L. A new image encryption algorithm based on arnold and coupled chaos maps. In Proceedings of the International Conference on Computer and Communication Technologies in Agriculture Engineering, Chengdu, China, 12–13 June 2010.
- Wu, X. A novel chaos-based image encryption scheme using coupled map lattices. In Proceedings of the 10th International Conference on Fuzzy Systems and Knowledge Discovery (FSKD), Shenyang, China, 23–25 July 2013.
- Jiang, H.Y.; Fu, C. An image encryption scheme based on lorenz chaos system. In Proceedings of the Fourth International Conference on Natural Computation, Jinan, China, 18–20 October 2008.
- Sharma, M.; Bhargava, A. Chaos based image encryption using two step iterated logistic map. In Proceedings of the International Conference on Recent Advances and Innovations in Engineering (ICRAIE), Jaipur, India, 23–25 December 2016.
- Lei, L.-H.; Bai, F.-M.; Han, X.-H. New image encryption algorithm based on logistic map and hyper-chaos. In Proceedings of the International Conference on Computational and Information Sciences, Shiyang, China, 21–23 June 2013.
- Mu, Z.; Liu, H. Research on digital media image encryption algorithm based on logistic chaotic map. In Proceedings of the International Conference on Robots & Intelligent System (ICRIS), Sanya, China, 7–8 November 2020.
- Wu, X.; Zhu, B.; Hu, Y.; Ran, Y. A novel color image encryption scheme using rectangular transform-enhanced chaotic tent maps. IEEE Access 2017, 5, 6429–6436.
- Zhu, C.; Sun, K. Cryptanalyzing and improving a novel color image encryption algorithm using rt-enhanced chaotic tent maps. IEEE Access 2018, 6, 18759–18770.
- Muhammad, Z.M.Z.; Özkaynak, F. A cryptographic confusion primitive based on lotka–volterra chaotic system and its practical applications in image encryption. In Proceedings of the IEEE 15th International Conference on Advanced Trends in Radioelectronics, Telecommunications and Computer Engineering (TCSET), Lviv-Slavske, Ukraine, 25–29 February 2020.
- Tresor, L.O.; Sumbwanyambe, M. A selective image encryption scheme based on 2d dwt, henon map and 4d qi hyper-chaos. IEEE Access 2019, 7, 103463–103472.
- Zeng, H.; Chen, D. Image encryption algorithm based on logistic-sine compound chaos. In Proceedings of the International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Chongqing, China, 29–30 October 2020.
- Zhao, F.; Li, C.; Liu, C.; Zhang, J. Image encryption algorithm based on sine-logistic cascade chaos. In Proceedings of the 5th International Conference on Control, Automation and Robotics (ICCAR), Beijing, China, 19–22 April 2019.
- Lu, Q.; Zhu, C.; Deng, X. An efficient image encryption scheme based on the lss chaotic map and single S-box. IEEE Access 2020, 8, 25664–25678.
- Zhu, H.; Zhao, Y.; Song, Y. 2d logistic-modulated-sine-coupling-logistic chaotic map for image encryption. IEEE Access 2019, 7, 14081–14098.
- Zhang, H.; Zhu, J.; Zhao, S.; He, Q.; Zhong, X.; Liu, J. A new image encryption algorithm based on 2d-lsimm chaotic map. In Proceedings of the 12th International Conference on Advanced Computational Intelligence (ICACI), Dali, China, 14–16 August 2020.
- Balakrishnan, B.; Mubarak, D.M.N. An improved image encryption using 2d logistic adjusted sine chaotic map with shuffled index matrix. In Proceedings of the International Conference on Advances in Electrical, Computing, Communication and Sustainable Technologies (ICAECT), Bhilai, India, 19–20 February 2021.
- Elshamy, A.M.; Rashed, A.N.Z.; Mohamed, A.E.-N.A.; Faragalla, O.S.; Mu, Y.; Alshebeili, S.A.; El-Samie, F.E.A. Optical image encryption based on chaotic baker map and double random phase encoding. J. Light. Technol. 2013, 31, 2533–2539.
- Tong, X.; Liu, Y.; Zhang, M.; Wang, Z. A novel image encryption scheme based on dynamical multiple chaos and baker map. In Proceedings of the 11th International Symposium on Distributed Computing and Applications to Business, Engineering & Science, Guilin, China, 19–22 October 2012.
- Krishna, P.R.; Surya Teja, C.V.M.; Renuga, D.S.; Thanikaiselvan, V. A chaos based image encryption using tinkerbell map functions. In Proceedings of the Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018.
- Kavinmozhi, G.; Premkumar, R.; Anand, S.; Robinson, S. A hybrid chaos approach for image encryption using ctic map. In Proceedings of the International Conference on Current Trends towards Converging Technologies (ICCTCT), Coimbatore, India, 1–3 March 2018.
- Savitri, N.; Johan, A.W.S.B.; Islama, F.A.; Utaminingrum, F. Efficient technique image encryption with cipher block chaining and gingerbreadman map. In Proceedings of the International Conference on Sustainable Information Engineering and Technology (SIET), Lombok, Indonesia, 28–30 September 2019.
- Moysis, L.; Kafetzis, I.; Volos, C.; Tutueva, A.V.; Butusov, D. Application of a hyperbolic tangent chaotic map to random bit generation and image encryption. In Proceedings of the IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (ElConRus), St. Petersburg and Moscow, Russia, 26–29 January 2021.
- Bisht, A.; Jaroli, P.; Dua, M.; Dua, S. Symmetric multiple image encryption using multiple new one-dimensional chaotic functions and two-dimensional cat man. In Proceedings of the International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 11–12 July 2018.
- Wang, X.; Zhu, X.; Zhang, Y. An image encryption algorithm based on josephus traversing and mixed chaotic map. IEEE Access 2018, 6, 23733–23746.
- Fu, C.; Li, W.; Meng, Z.; Wang, T.; Li, P. A symmetric image encryption scheme using chaotic baker map and lorenz system. In Proceedings of the Ninth International Conference on Computational Intelligence and Security, Emeishan, China, 14–15 December 2013.
- Choi, U.S.; Cho, S.J.; Kang, S.W. Color image encryption algorithm for medical image by mixing chaotic maps. In Proceedings of the 12th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2020.
- Zhang, X.; Wang, L.; Zhou, Z.; Niu, Y. A chaos-based image encryption technique utilizing hilbert curves and h-fractals. IEEE Access 2019, 7, 74734–74746.
- Aslam, M.N.; Belazi, A.; Kharbech, S.; Talha, M.; Xiang, W. Fourth order mca and chaos-based image encryption scheme. IEEE Access 2019, 7, 66395–66409.
- Habibipour, M.; Maarefdoust, R.; Yaghobi, M.; Rahati, S. An image encryption system by 2d memorized cellular automata and chaos mapping. In Proceedings of the 6th International Conference on Digital Content, Multimedia Technology and Its Applications, Seoul, Korea, 16–18 August 2010.
- Habibipour, M.; Yaghobi, M.; Rahati-Q, S.; souzanchi k, Z. An image encryption system by indefinite cellular automata and chaos. In Proceedings of the 2nd International Conference on Signal Processing Systems, Dalian, China, 5–7 July 2010.
- García, V.M.S.; Ramírez, M.D.G.; Carapia, R.F.; Vega-Alvarado, E.; Escobar, E.R. A novel method for image encryption based on chaos and transcendental numbers. IEEE Access 2019, 7, 163729–163739.
- Xie, Y.; Li, J.; Kong, Z.; Zhang, Y.; Liao, X.; Liu, Y. Exploiting optics chaos for image encryption-then-transmission. J. Light. Technol. 2016, 34, 5101–5109.
- Liu, X.; Guo, R.; Li, M.; Wei, Z. Research on image encryption in secure communication system of space laser chaos keying. In Proceedings of the International Conference on Wireless Communications and Smart Grid (ICWCSG), Qingdao, China, 12–14 June 2020.
- Li, L.; Xie, Y.; Liu, Y.; Liu, B.; Ye, Y.; Song, T.; Zhang, Y.; Liu, Y. Exploiting optical chaos for color image encryption and secure resource sharing in cloud. IEEE Photonics J. 2019, 11, 1–11.
- Liu, B.; Xie, Y.; Zhang, Y.; Ye, Y.; Song, T.; Liao, X.; Liu, Y. Arm-embedded implementation of a novel color image encryption and transmission system based on optical chaos. IEEE Photonics J. 2020, 12, 1–12.
- AlMutairi, F.; Bonny, T. Image encryption based on chua chaotic oscillator. In Proceedings of the International Conference on Signal Processing and Information Security (ICSPIS), Dubai, United Arab Emirates, 25–26 November 2020.
- Lin, Z.H.; Wang, H.X. Image encryption based on chaos with pwl memristor in chua’s circuit. In Proceedings of the International Conference on Communications, Circuits and Systems, Milpitas, CA, USA, 23–25 July 2009.
- Liu, Z.; Wu, C.; Wang, J.; Hu, Y. A color image encryption using dynamic dna and 4-d memristive hyper-chaos. IEEE Access 2019, 7, 78367–78378.
- Sun, J.; Li, C.; Lu, T.; Akgul, A.; Min, F. A memristive chaotic system with hypermultistability and its application in image encryption. IEEE Access 2020, 8, 139289–139298.
- Muhammad, A.S.; Özkaynak, F. Siea: Secure image encryption algorithm based on chaotic systems optimization algorithms and pufs. Symmetry 2021, 13, 824.
- Wang, X.; Liu, P. A new image encryption scheme based on a novel one-dimensional chaotic system. IEEE Access 2020, 8, 174463–174479.
- Elghandour, A.N.; Salah, A.M.; Elmasry, Y.A.; Karawia, A.A. An image encryption algorithm based on bisection method and one-dimensional piecewise chaotic map. IEEE Access 2021, 9, 43411–43421.
- Tiwari, H.; Satish, K.N.; Harshitha, R.; Shilpa, N.; Rakshatha, S.; Archana, K.N. Ensuring confidentiality in bsn with 1-d chaos based image encryption scheme. In Proceedings of the International Conference on Advances in Computing, Communication Control and Networking (ICACCCN), Greater Noida, India, 12–13 October 2018.
- Yang, S.; Tong, X. A block image encryption algorithm based on 2d chaotic system. In Proceedings of the IEEE 12th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 20–22 August 2021.
- Qian, X.; Yang, Q.; Li, Q.; Liu, Q.; Wu, Y.; Wang, W. A novel color image encryption algorithm based on three-dimensional chaotic maps and reconstruction techniques. IEEE Access 2021, 9, 61334–61345.
- Asl, A.M.; Broumandnia, A.; Mirabedini, S.J. Scale invariant digital color image encryption using a 3d modular chaotic map. IEEE Access 2021, 9, 102433–102449.
- Cao, Y.y.; Fu, C. An image encryption scheme based on high dimension chaos system. In Proceedings of the International Conference on Intelligent Computation Technology and Automation (ICICTA), Changsha, China, 20–22 October 2008.
- Mu, X.; E-Nuo, S. A new color image encryption algorithm based on 3d lorenz chaos sequences. In Proceedings of the First International Conference on Pervasive Computing, Signal Processing and Applications, Harbin, China, 17–19 September 2010.
- Huang, Y.; Huang, L.; Wang, Y.; Peng, Y.; Yu, F. Shape synchronization in driver-response of 4-d chaotic system and its application in image encryption. IEEE Access 2020, 8, 135308–135319.
- Zhu, S.; Zhu, C. Plaintext-related image encryption algorithm based on block structure and five-dimensional chaotic map. IEEE Access 2019, 7, 147106–147118.
- Qiu, W.C.; Yan, S.J. An image encryption algorithm based on the combination of low-dimensional chaos and high-dimensional chaos. In Proceedings of the 3rd International Conference on Electronic Information Technology and Computer Engineering (EITCE), Xiamen, China, 18–20 October 2019.
- Parida, P.; Pradhan, C.; Gao, X.; Roy, D.S.; Barik, R.K. Image encryption and authentication with elliptic curve cryptography and multidimensional chaotic maps. IEEE Access 2021, 9, 76191–76204.
- Xu, J.; Zhao, C.; Mou, J. A 3d image encryption algorithm based on the chaotic system and the image segmentation. IEEE Access 2020, 8, 145995–146005.
- Firdous, A.; Rehman, A.U.; Missen, M.M.S. A gray image encryption technique using the concept of water waves, chaos and hash function. IEEE Access 2021, 9, 11675–11693.
- Ravichandran, D.; Balasubramanian, V.; Fathima, S.; Banu, A.; Anushiadevi; Amirtharajan, R. Chaos and iwt blended image encryption for grey scale image security. In Proceedings of the International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019.
- Hu, X.; Wei, L.; Chen, W.; Chen, Q.; Guo, Y. Color image encryption algorithm based on dynamic chaos and matrix convolution. IEEE Access 2020, 8, 12452–12466.
- Sun, Y.J.; Zhang, H.; Wang, C.P.; Li, Z.Y.; Wang, X.Y. Networked chaotic map model and its applications in color multiple image encryption. IEEE Photonics J. 2020, 12, 1–18.
- Yin, P.; Min, L. A color image encryption algorithm based generalized chaos synchronization for bidirectional discrete systems for audio signal communication. In Proceedings of the International Conference on Intelligent Control and Information Processing, Dalian, China, 13–15 August 2010.
- Wang, J. Image encryption algorithm based on 2-d wavelet transform and chaos sequences. In Proceedings of the International Conference on Computational Intelligence and Software Engineering, Wuhan, China, 11–13 December 2009.
- Zhang, Q.; Shen, M.; Li, B.; Fang, R. Chaos-based color image encryption scheme in the wavelet domain. In Proceedings of the 7th International Congress on Image and Signal Processing, Dalian, China, 14–16 October 2014.
- Wang, Q.; Ding, Q.; Zhang, Z.; Ding, L. Digital image encryption research based on dwt and chaos. In Proceedings of the Fourth International Conference on Natural Computation, Jinan, China, 18–20 October 2008.
- Zhang, S.; Cai, R.; Jiang, Y.; Guo, S. An image encryption algorithm based on multiple chaos and wavelet transform. In Proceedings of the 2nd International Congress on Image and Signal Processing, Tianjin, China, 17–19 October 2009.
- Macovei, C.; Răducanu, M.; Datcu, O. Image encryption algorithm using wavelet packets and multiple chaotic maps. In Proceedings of the International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 5–6 November 2020.
- Li, X.; Zhang, Y. Digital image encryption and decryption algorithm based on wavelet transform and chaos system. In Proceedings of the IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Xi’an, China, 3–5 October 2016.
- Karmakar, J.; Mandal, M.K. Chaos-based image encryption using integer wavelet transform. In Proceedings of the 7th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 27–28 February 2020.
- Gao, H.; Wang, X. Chaotic image encryption algorithm based on zigzag transform with bidirectional crossover from random position. IEEE Access 2021, 9, 105627–105640.
- Zhang, L.; Wu, J.; Zhou, N. Image encryption with discrete fractional cosine transform and chaos. In Proceedings of the Fifth International Conference on Information Assurance and Security, Xi’an, China, 18–20 August 2009.
- Jiang, A.; Yu, J.; Cang, X. Image encryption algorithm based on chaos and contourlet transform. In Proceedings of the First International Conference on Pervasive Computing, Signal Processing and Applications, Harbin, China, 17–19 September 2010.
- Li, X.M.; Dai, L. Reality-preserving image encryption assosiated with the chaos and the lct. In Proceedings of the 3rd International Congress on Image and Signal Processing, Yantai, China, 16–18 October 2010.
- Ashtiyani, M.; Birgani, P.M.; Hosseini, H.M. Chaos-based medical image encryption using symmetric cryptography. In Proceedings of the 3rd International Conference on Information and Communication Technologies: From Theory to Applications, Damascus, Syria, 7–11 April 2008.
- Wu, Z.; Zhang, X.; Zhong, X. Generalized chaos synchronization circuit simulation and asymmetric image encryption. IEEE Access 2019, 7, 37989–38008.
- Bora, S.; Sen, P.; Pradhan, C. Novel color image encryption technique using blowfish and cross chaos map. In Proceedings of the International Conference on Communications and Signal Processing (ICCSP), Melmaruvathur, India, 2–4 April 2015.
- Abbas, A.M.; Alharbi, A.A.; Ibrahim, S. A novel parallelizable chaotic image encryption scheme based on elliptic curves. IEEE Access 2021, 9, 54978–54991.
- Yousif, S.F.; Abboud, A.J.; Radhi, H.Y. Robust image encryption with scanning technology, the el-gamal algorithm and chaos theory. IEEE Access 2020, 8, 155184–155209.
- Luo, Y.; Ouyang, X.; Liu, J.; Cao, L. An image encryption method based on elliptic curve elgamal encryption and chaotic systems. IEEE Access 2019, 7, 38507–38522.
- Dsouza, C.A.; Sonawane, K. Securing folder directory using image encryption by chaos and rijndael algorithm. In Proceedings of the International Conference on Communication information and Computing Technology (ICCICT), Mumbai, India, 25–27 June 2021.
- Nkapkop, J.D.D.; Effa, J.Y.; Toma, A.; Cociota, F.; Borda, M. Chaos-based image encryption using the rsa keys management for an efficient web communication. In Proceedings of the 12th IEEE International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 27–28 October 2016.
- Zhang, Y.; Liu, W.; Cao, S.; Zhai, Z.; Nie, X.; Dai, W. Digital image encryption algorithm based on chaos and improved des. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, San Antonio, TX, USA, 11–14 October 2009.
- Gupta, K.; Gupta, R.; Agrawal, R.; Khan, S. An ethical approach of block based image encryption using chaotic map. Int. J. Secur. Appl. 2015, 9, 105–122.
- Rani, M.; Kumar, S. A novel and efficient approach to encrypt images using chaotic logistic map and stream cipher. In Proceedings of the International Conference on Green Computing and Internet of Things (ICGCIoT), Greater Noida, India, 8–10 October 2015.
- Ginting, R.U.; Dillak, R.Y. Digital color image encryption using rc4 stream cipher and chaotic logistic map. In Proceedings of the International Conference on Information Technology and Electrical Engineering (ICITEE), Yogyakarta, Indonesia, 7–8 October 2013.
- Goumidi, D.E.; Hachouf, F. Hybrid chaos-based image encryption approach using block and stream ciphers. In Proceedings of the 8th International Workshop on Systems, Signal Processing and Their Applications (WoSSPA), Algiers, Algeria, 12–15 May 2013.
- Chapaneri, S.; Chapaneri, R. Chaos based image encryption using latin rectangle scrambling. In Proceedings of the Annual IEEE India Conference (INDICON), Pune, India, 11–13 December 2014.
- Qu, J. Image encryption algorithm based on logistic chaotic scrambling system. In Proceedings of the IEEE 3rd International Conference on Information Systems and Computer Aided Education (ICISCAE), Dalian, China, 11–13 September 2020.
- Zhang, P.; Chen, M.; Zhang, J. Image encryption algorithm of hyper-chaotic system based on spiral scrambling. In Proceedings of the IEEE International Symposium on Product Compliance Engineering-Asia (ISPCE-CN), Chongqing, China, 6–8 November 2020.
- Krishnamoorthi, R.; Murali, P. Chaos based image encryption with orthogonal polynomials model and bit shuffling. In Proceedings of the International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 20–21 February 2014.
- Bhadke, A.A.; Kannaiyan, S.; Kamble, V. Symmetric chaos-based image encryption technique on image bit-planes using sha-256. In Proceedings of the Twenty Fourth National Conference on Communications (NCC), Hyderabad, India, 25–28 February 2018.
- Slimane, N.B.; Bouallegue, K.; Machhout, M. A novel image encryption scheme using chaos, hyper-chaos systems and the secure hash algorithm sha-1. In Proceedings of the International Conference on Control, Automation and Diagnosis (ICCAD), Hammamet, Tunisia, 19–21 January 2017.
- Liu, J. A novel sensitive chaotic image encryption algorithm based on sha-3 and steganography. In Proceedings of the IEEE 3rd International Conference of Safe Production and Informatization (IICSPI), Chongqing City, China, 28–30 November 2020.
- Abd-El-Hafiz, S.K.; AbdElHaleem, S.H.; Radwan, A.G. Permutation techniques based on discrete chaos and their utilization in image encryption. In Proceedings of the 13th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), Chiang Mai, Thailand, 28 June–1 July 2016.
- Ping, P.; Fan, J.; Mao, Y.; Xu, F.; Gao, J. A chaos based image encryption scheme using digit-level permutation and block diffusion. IEEE Access 2018, 6, 59108–59130.
- Liu, L.; Lei, Y.; Wang, D. A fast chaotic image encryption scheme with simultaneous permutation-diffusion operation. IEEE Access 2020, 8, 27361–27374.
- Liu, L.; Zhang, L.; Jiang, D.; Guan, Y.; Zhang, Z. A simultaneous scrambling and diffusion color image encryption algorithm based on hopfield chaotic neural network. IEEE Access 2021, 7, 185796–185810.
- Koduru, S.C.; Chandrasekaran, V. Integrated confusion-diffusion mechanisms for chaos based image encryption. In Proceedings of the IEEE 8th International Conference on Computer and Information Technology Workshops, Sydney, NSW, Australia, 8–11 July 2008.
- Rehman, M.U.; Shafique, A.; Khalid, S.; Hussain, I. Dynamic substitution and confusion-diffusion-based noise-resistive image encryption using multiple chaotic maps. IEEE Access 2021, 9, 52277–52291.
- Hassan, J.M.; Kadhim, F.A. New S-box transformation based on chaotic system for image encryption. In Proceedings of the 3rd International Conference on Engineering Technology and Its Applications (IICETA), Najaf, Iraq, 6–7 September 2020.
- Wang, D.; Zhang, Y. Image encryption algorithm based on S-boxes substitution and chaos random sequence. In Proceedings of the International Conference on Computer Modeling and Simulation, Macau, China, 20–22 February 2009.
- Khan, J.S.; Rehman, A.U.; Ahmad, J.; Habib, Z. A new chaos-based secure image encryption scheme using multiple substitution boxes. In Proceedings of the Conference on Information Assurance and Cyber Security (CIACS), Rawalpindi, Pakistan, 18 December 2015.
- Lidong, L.; Jiang, D.; Wang, X.; Zhang, L.; Rong, X. A dynamic triple-image encryption scheme based on chaos, S-box and image compressing. IEEE Access 2020, 8, 210382–210399.
- Rehman, A.U.; Firdous, A.; Iqbal, S.; Abbas, Z.; Shahid, M.M.A.; Wang, H.; Ullah, F. A color image encryption algorithm based on one time key, chaos theory, and concept of rotor machine. IEEE Access 2020, 8, 172275–172295.
- Guo, J.; Riyono, D.; Prasetyo, H. Improved beta chaotic image encryption for multiple secret sharing. IEEE Access 2018, 6, 46297–46321.





