
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Hamed Taherdoost | + 11018 word(s) | 11018 | 2021-12-14 04:05:08 | | | |
| 2 | Jason Zhu | -1913 word(s) | 9105 | 2021-12-15 03:15:38 | | |
Video Upload Options
Businesses are bombarded with great deals of risks, vulnerabilities, and unforeseen business interruptions in their lifetime, which negatively affect their productivity and sustainability within the market. Such risks require a risk management system to identify risks and risk factors and propose approaches to eliminate or reduce them.
Risk management involves highly structured practices that should be implemented within an organization, including organizational planning documents. Continuity planning and fraud detection policy development are among the many critically important practices conducted through risk management that aim to mitigate risk factors, their vulnerability, and their impact.
Information systems play a pivotal role in any organization by providing many benefits, such as reducing human errors and associated risks owing to the employment of sophisticated algorithms. Both the development and establishment of an information system within an organization contributes to mitigating business-related risks and also creates new types of risks associated with its establishment. Businesses must prepare for, react to, and recover from unprecedented threats that might emerge in the years or decades that follow.
1. Introduction
2. Principles and Aims of Risk Management
-
Delineating which risks are financially, energetically, and temporally worth an investment;
-
Isolating and optimizing risks;
-
Eliminating destructive risks and improving progressive risks;
-
Developing alternative sets of action spaces;
-
Reserving time and money to withstand the threats that cannot be mitigated;
-
Ensuring no breach over the organizational risk boundaries.
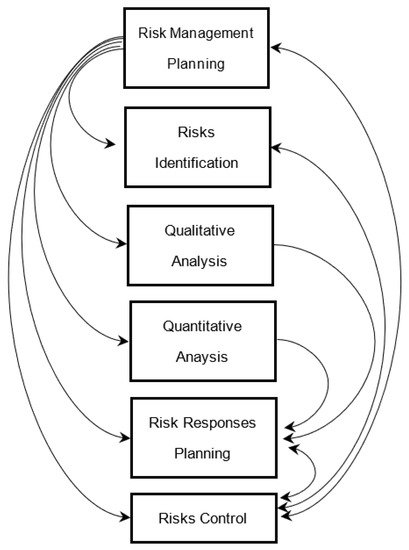
2.1. Risk Management Planning
2.2. Identifying Risk
-
Software development, implementation, and post-implementation;
-
System interfaces (e.g., internal and external connectivity);
-
Data and information within a system;
-
People who support and use IT systems;
-
System and data criticality (e.g., the value of the system or importance to an organization);
-
System and data sensitivity;
-
System security policies (organizational policies, federal requirements, laws, industry practices);
-
System security architecture;
-
Information storage protection;
-
Data availability, integrity, and confidentiality.
2.3. Qualitative Analysis
-
Ensuring the validity of data sources to include them further in the process;
-
Specifying the areas of risk with varying degrees of concern/attention;
-
Determining the urgency of a given risk which delineates an appropriate vision over the time-dependency of an action.
2.4. Quantitative Analysis
-
Interviewing technical experts to rate and rank risks in a quantitative manner;
-
Using the expected monetary value (the result of multiplying probability and impact of risk to obtain a novel quantitative parameter);
-
Decision trees through which rich information is presented in an easy-to-interpret format;
-
The program evaluation: Embedding multi-data-point duration estimates in network systems to provide specific risk values for schedules;
-
Risk Simulation tools, e.g., Monte Carlo method.
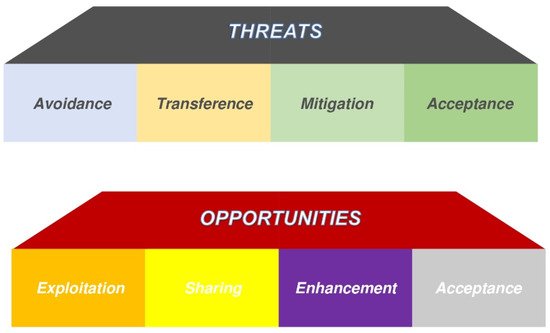
2.5. Planning Risk Response
2.6. Risk Control
3. Risk Policies and Continuity Planning
-
The recognition of a problem;
-
Applying particular analysis;
-
Processing phase, including developing policy instrumentation, consulting, and coordination;
-
Decision-making;
-
Execution;
-
Final evaluation (assessing the effectiveness of the policy).
-
Risk assessment and associated analysis;
-
Development and documentation of a business continuity plan;
-
Testing and implementing a business continuity plan.
-
Accepting the existing condition;
-
Diminishing the impact of a specific crisis/risk down to a satisfactory degree;
-
Diminishing or eradicating the potential effects.
-
Minimum number of personnel required for critical operative sectors;
-
Minimal requirements for implementing critical functions regarding alternate manufacturing, warehousing, operating systems, etc.;
-
Means and resources of obtaining required materials;
-
The time frame through which each of these specified actions are required;
-
Recovery alternatives.
-
Well-organized writing formats to contribute to the cohesiveness and conformity of the plan;
-
The specific assumption on which the strategies might be relied on should be written;
-
If the planner encounters difficulty in preparing the plan, it may pertain to the fact that he/she is trying to plan for areas that do not need to be planned.
4. Risk Control and Fraud Detection
-
Prevention;
-
Detection;
-
Deterrence;
-
Response.
4.1. Fraud Prevention
4.2. Detecting Fraud
4.3. Fraud Deterrence
-
Senior management’s solid commitment to ethical behavior must be supported by acts as well as words. It has often been demonstrated that simply establishing a written code of ethics is insufficient to avoid ethical misconduct. Such enormous codes are widely acknowledged to be merely a showpiece that does not influence behavior [60].
-
Skepticism is widely recognized in audit procedures as a fraud deterrent; however, it also plays an essential role in financial reporting. Skepticism manifests itself in people at all levels of the accounting profession and encompassing specific characteristics including:
-
Accounting professionals consider all elements of economic activity rather than just accepting the first certain response or what someone in authority states. That is why they have a questioning mind that leads to suspending final judgment and seeking more information and backup.
-
Interpersonal knowledge assists accountants in recognizing that people’s views and reasons for reaching a specific result might be skewed.
-
Accountants with integrity and determination to make their own decisions, along with self-confidence, can determine and research matters for themselves rather than accepting the assertions of others.
-
-
Finally, effective communication among participants in the financial reporting process is critical for fraud prevention and deterrence. It is the inevitable outcome of a strong ethical culture; however, it is still worth mentioning. Understanding any extra data that supports accounting findings can assist in preventing or eliminating the suspicion of misconduct when no illegal or unethical activity exists. In other words, improved communication enables everyone involved in the process to have a better understanding of the logic and evidence that underpin accounting choices and conclusions. As a result, there is less guessing and speculation while making an effort to comprehend intentions [59].
4.4. Responding to Fraud
5. Conclusions
References
- Nikoloski, K. The role of information technology in the business sector. Int. J. Sci. Res. (IJSR) 2014, 3, 303–309.
- Rochmah, T.N.; Fakhruzzaman, M.N.; Yustiawan, T. Hospital staff acceptance toward management information systems in Indonesia. Health Policy Technol. 2020, 9, 268–270.
- Mutwiri, W. Amazon Business Information Systems. Data Acquisition and Management in Its Value Chain; GRIN Verlag: Munich/Ravensburg, Germany, 2020.
- Lucas, H.C., Jr. Performance and the use of an information system. Manag. Sci. 1975, 21, 908–919.
- Abe, S.; Ozawa, M.; Kawata, Y. Science of Societal Safety: Living at Times of Risks and Disasters; Springer Nature: Berlin/Heidelberg, Germany, 2019.
- Samimi, A.; Samimi, M. Investigation of Risk Management in Food Industry. Int. J. Adv. Stud. Humanit. Soc. Sci. 2020, 9, 195–204.
- Finne, T. Information systems risk management: Key concepts and business processes. Comput. Secur. 2000, 19, 234–242.
- Stackpole, C.S. A User’s Manual to the PMBOK Guide; John Wiley & Sons: Hoboken, NJ, USA, 2013.
- Suroso, J.S.; Fakhrozi, M.A. Assessment of information system risk management with octave allegro at education institution. Procedia Comput. Sci. 2018, 135, 202–213.
- Aven, T. Risk assessment and risk management: Review of recent advances on their foundation. Eur. J. Oper. Res. 2016, 253, 1–13.
- Sherer, S.A.; Alter, S. Information systems risks and risk factors: Are they mostly about information systems? Commun. Assoc. Inf. Syst. 2004, 14, 2.
- Stoneburner, G.; Goguen, A.; Feringa, A. Risk management guide for information technology systems. Nist Spec. Publ. 2002, 800, 800–830.
- Boiko, A.; Shendryk, V.; Boiko, O. Information systems for supply chain management: Uncertainties, risks and cyber security. Procedia Comput. Sci. 2019, 149, 65–70.
- Longerstaey, J.; Spencer, M. Riskmetricstm—Technical Document; Morgan Guaranty Trust Company of New York: New York, NY, USA, 1996; Volume 51, p. 54.
- Benjamin, C.W.; Chou, H.-Y.; Wu, M.B.; Chang, D.H. The Risks of Risk Management. In Proceedings of the 2006 IEEE International Conference on Management of Innovation and Technology, Singapore, 21–23 June 2006; pp. 708–712.
- Chalmers, J.; Armour, M. The Delphi Technique; Springer: Singapore, 2019.
- Kaveh, A.; Rahami, H.; Shojaei, I. Swift analysis of linear and non-linear structures and applications using reanalysis. In Swift Analysis of Civil Engineering Structures Using Graph Theory Methods; Springer: Berlin/Heidelberg, Germany, 2020; pp. 201–245.
- Zhang, Y.; Guan, X. Selecting project risk preventive and protective strategies based on bow-tie analysis. J. Manag. Eng. 2018, 34, 04018009.
- Brown, D.F.; Dunn, W.E. Application of a quantitative risk assessment method to emergency response planning. Comput. Oper. Res. 2007, 34, 1243–1265.
- Kumar, L.; Jindal, A.; Velaga, N.R. Financial risk assessment and modelling of PPP based Indian highway infrastructure projects. Transp. Policy 2018, 62, 2–11.
- Fang, C.; Marle, F.; Xie, M.; Zio, E. An integrated framework for risk response planning under resource constraints in large engineering projects. IEEE Trans. Eng. Manag. 2013, 60, 627–639.
- Okta. What Is Identity Management and Access Control? Available online: https://www.okta.com/identity-101/what-is-identity-management-and-access-control/ (accessed on 10 November 2021).
- Bugge, C.; Williams, B.; Hagen, S.; Logan, J.; Glazener, C.; Pringle, S.; Sinclair, L. A process for Decision-making after Pilot and feasibility Trials (ADePT): Development following a feasibility study of a complex intervention for pelvic organ prolapse. Trials 2013, 14, 1–13.
- Alsmadi, I.; Burdwell, R.; Aleroud, A.; Wahbeh, A.; Al-Qudah, M.; Al-Omari, A. Security and access controls: Lesson plans. In Practical Information Security; Springer: Berlin/Heidelberg, Germany, 2018; pp. 53–71.
- Beres, Y.; Baldwin, A.; Mont, M.C.; Shiu, S. On identity assurance in the presence of federated identity management systems. In Proceedings of the 2007 ACM workshop on Digital Identity Management, Fairfax, VA, USA, 2 November 2007; pp. 27–35.
- Yeluri, R.; Castro-Leon, E. Identity management and control for clouds. In Building the Infrastructure for Cloud Security; Springer: Berlin/Heidelberg, Germany, 2014; pp. 141–159.
- Blyth, M. Business Continuity Management: Building an Effective Incident Management Plan; John Wiley & Sons: Hoboken, NJ, USA, 2009.
- Jose, D.; Rosa, P.D.S.; Rosa, S. Crisis Management; Ateneo Graduate School of Business: Makati City, Philippines, 2020.
- Moşteanu, D.; Roxana, N. Management of disaster and business continuity in a digital world. Int. J. Manag. 2020, 11, 169–177.
- Moşteanu, N.R.; Faccia, A.; Cavaliere, L.P.L. Disaster Management, Digitalization and Financial Resources: Key factors to keep the organization ongoing. In Proceedings of the 2020 4th International Conference on Cloud and Big Data Computing, Liverpool, UK, 26–28 August 2020; pp. 118–122.
- Moşteanu, N.R. Challenges for Organizational Structure and design as a result of digitalization and cybersecurity. Bus. Manag. Rev. 2020, 11, 278–286.
- Fezzey, T.; Batchelor, J.H.; Burch, G.F.; Reid, R. Cybersecurity Continuity Risks: Lessons Learned from the COVID-19 Pandemic; Kennesaw State University: Kennesaw, GA, USA, 2021.
- Lindström, J.; Samuelsson, S.; Hägerfors, A. Business continuity planning methodology. Disaster Prev. Manag. Int. J. 2010, 19, 243–255.
- Syed, A.; Syed, A. Business Continuity Planning Methodology; Sentryx: Austerlitz, The Netherlands, 2004.
- Yang, C.-H.; Lee, K.-C. Developing a strategy map for forensic accounting with fraud risk management: An integrated balanced scorecard-based decision model. Eval. Program Plan. 2020, 80, 101780.
- Lahuta, P.; Kardoš, P.; Hudáková, M. Integrated Risk Management System in Transport. Transp. Res. Procedia 2021, 55, 1530–1537.
- Jafar, E.; Taneja, U. Business continuity planning—A survey of hospitals in Delhi. J. Public Health 2017, 25, 699–709.
- Civča, D.; Atstāja, D.; Koval, V. Business continuity plan testing methods in an international company. Restruct. Manag. Increase Compet. Trading Co. Latv. 2021, 5, 341.
- Sasaki, H.; Maruya, H.; Abe, Y.; Fujita, M.; Furukawa, H.; Fuda, M.; Kamei, T.; Yaegashi, N.; Tominaga, T.; Egawa, S. Scoping review of hospital business continuity plans to validate the improvement after the 2011 Great East Japan Earthquake and Tsunami. Tohoku J. Exp. Med. 2020, 251, 147–159.
- Niemimaa, M.; Järveläinen, J.; Heikkilä, M.; Heikkilä, J. Business continuity of business models: Evaluating the resilience of business models for contingencies. Int. J. Inf. Manag. 2019, 49, 208–216.
- Setiawan, A.; Wibowo, A.; Susilo, A.H. Risk analysis on the development of a business continuity plan. In Proceedings of the 2017 4th International Conference on Computer Applications and Information Processing Technology (CAIPT), Kuta Bali, Indonesia, 8–10 August 2017; pp. 1–4.
- Goldstein, J.; Benaroch, M.; Chernobal, A. IS-Related Operational Risk: An Exploratory Analysis. In Proceedings of the AMCIS, Toronto, ON, Canada, 14–17 August 2008.
- Pourhabibi, T.; Ong, K.-L.; Kam, B.H.; Boo, Y.L. Fraud detection: A systematic literature review of graph-based anomaly detection approaches. Decis. Support Syst. 2020, 133, 113303.
- Hooi, B.; Shin, K.; Song, H.A.; Beutel, A.; Shah, N.; Faloutsos, C. Graph-based fraud detection in the face of camouflage. ACM Trans. Knowl. Discov. Data (TKDD) 2017, 11, 1–26.
- Karpoff, J.M. The future of financial fraud. J. Corp. Financ. 2021, 66, 101694.
- Files, R.; Martin, G.S.; Rasmussen, S.J. Regulator-cited cooperation credit and firm value: Evidence from enforcement actions. Account. Rev. 2019, 94, 275–302.
- Morgan, R.E. Financial Fraud in the United States, 2017; US Department of Justice, Office of Justice Programs, Bureau of Justice Statistics, NCJ: Washington, USA, 2021; Volume 255817.
- Samociuk, M.; Iyer, N.; Doody, H. A Short Guide to Fraud Risk: Fraud Resistance and Detection; Routledge: London, UK, 2017.
- Baldree, J. Fraud Risk Management: A Guide to Good Practice; CIMA Publisher Wokingham: Wokingham, UK, 2008.
- Baesens, B.; Höppner, S.; Verdonck, T. Data engineering for fraud detection. Decis. Support Syst. 2021, 113492.
- Stojanović, B.; Božić, J.; Hofer-Schmitz, K.; Nahrgang, K.; Weber, A.; Badii, A.; Sundaram, M.; Jordan, E.; Runevic, J. Follow the trail: Machine learning for fraud detection in Fintech applications. Sensors 2021, 21, 1594.
- Temuçin, T.S.; Erbaş, S.; Anıl, A. Using Big Data in Internal Fraud Detection. TIDE Acad. Res. 2021, 3, 55–82.
- Todorović, Z.; Tomaš, D.; Todorović, B. Anti-Fraud Strategy. Economics 2020, 8, 69–78.
- Suh, J.B.; Shim, H.S. The effect of ethical corporate culture on anti-fraud strategies in South Korean financial companies: Mediation of whistleblowing and a sectoral comparison approach in depository institutions. Int. J. Law Crime Justice 2020, 60, 100361.
- Dolan, S.; Hawkins, S.; Albrecht, C.; Richley, B. Raising the ethical bar: Ethical audits and positive culture transformation. The European Business Review. 11 January 2021. Available online: https://www.europeanbusinessreview.com/raising-the-ethical-bar-ethical-audits-and-positive-culture-transformation/ (accessed on 10 November 2021).
- Jackson, P.M. Debate: Fraud risk management in the public sector. Public Money Manag. 2013, 33, 6–8.
- Eusebio, N. Anti-Fraud Strategy; Technical Note ACCID; Associació Catalana de Comptabilitat i Direcció: Vic, Spain, 2017.
- Sofia, I.P. The impact of internal control and good corporate governance on fraud prevention. In Proceedings of the International Seminar on Accounting Society, Kota Tangerang Selatan, Indonisea, 21 November 2020.
- Reporting, D.F. Three pillars of fraud deterrence and detection. Strateg. Financ. 2015, 96, 17–18.
- Araj, F.G. Responding to Fraud Risk; The Institute of Internal Auditors Research Foundation (IIARF): Lake Mary, FL, USA, 2015.




