
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Håkon Harnes | -- | 1808 | 2024-03-14 13:30:20 | | | |
| 2 | Wendy Huang | -1 word(s) | 1807 | 2024-03-15 08:19:23 | | |
Video Upload Options
WebAssembly is a low-level bytecode language that enables high-level languages like C, C++, and Rust to be executed in the browser at near-native performance. WebAssembly has gained widespread adoption and is natively supported by all modern browsers. Despite its benefits, WebAssembly has introduced significant security challenges, primarily due to vulnerabilities inherited from memory-unsafe source languages. Moreover, the use of WebAssembly extends beyond traditional web applications to smart contracts on blockchain platforms, where vulnerabilities have led to significant financial losses. WebAssembly has also been used for malicious purposes, like cryptojacking, where website visitors’ hardware resources are used for crypto mining without their consent.
1. Introduction
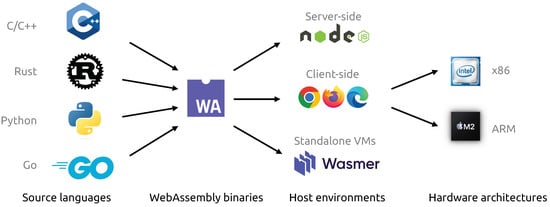
2. Security
3. Vulnerabilities
4. Smart Contracts
5. Cryptojacking
References
- w3Techs. Usage Statistics of JavaScript as Client-Side Programming Language on Websites. December 2022. Available online: https://w3techs.com/technologies/details/cp-javascript (accessed on 4 November 2022).
- Contributors to Wikimedia Projects. ActiveX-Wikipedia. 2022. Available online: https://en.wikipedia.org/wiki/ActiveX (accessed on 4 November 2022).
- Google. Native Client-Chrome Developers. 2021. Available online: https://developer.chrome.com/docs/native-client (accessed on 4 November 2022).
- mdn web docs. asm.js-Game Development | MDN. 2022. Available online: https://developer.mozilla.org/en-US/docs/Games/Tools/asm.js?source=post_page (accessed on 4 November 2022).
- Can I Use WebAssembly | Can I Use… Support Tables for HTML5, CSS3, etc. 2022. Available online: https://caniuse.com/wasm (accessed on 12 November 2022).
- Møller, A. Technical perspective: WebAssembly: A quiet revolution of the Web. Commun. ACM 2018, 61, 106.
- Pop, V.A.B.; Virtanen, S.; Sainio, P.; Niemi, A. Secure Migration of WebAssembly-Based Mobile Agents between Secure Enclaves. Master’s Thesis, University of Turku, Turku, Finland, 2021.
- Fastly. Fastly Docs. 2022. Available online: https://docs.fastly.com/products/compute-at-edge (accessed on 23 November 2022).
- Ewasm. Ethereum WebAssembly (Ewasm)-Ethereum WebAssembly. 2021. Available online: https://ewasm.readthedocs.io/en/mkdocs (accessed on 7 November 2022).
- Eosio. EOS Virtual Machine: A High-Performance Blockchain WebAssembly Interpreter–EOSIO. 2021. Available online: https://eos.io/news/eos-virtual-machine-a-high-performance-blockchain-webassembly-interpreter (accessed on 9 November 2022).
- NEARWhat Is a Smart Contract?|NEAR Documentation. 2022. Available online: https://docs.near.org/develop/contracts/whatisacontract (accessed on 11 November 2022).
- Liu, R.; Garcia, L.; Srivastava, M. Aerogel: Lightweight Access Control Framework for WebAssembly-Based Bare-Metal IoT Devices. In Proceedings of the 2021 IEEE/ACM Symposium on Edge Computing (SEC), San Jose, CA, USA, 14–17 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 94–105.
- Mäkitalo, N.; Mikkonen, T.; Pautasso, C.; Bankowski, V.; Daubaris, P.; Mikkola, R.; Beletski, O. WebAssembly modules as lightweight containers for liquid IoT applications. In Proceedings of the International Conference on Web Engineering, Biarritz, France, 18–21 May 2021; Springer: Cham, Switzerland, 2021; pp. 328–336.
- Scheidl, F. Valent-Blocks: Scalable high-performance compilation of WebAssembly bytecode for embedded systems. In Proceedings of the 2020 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 17–18 August 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 119–124.
- Haas, A.; Rossberg, A.; Schuff, D.L.; Titzer, B.L.; Holman, M.; Gohman, D.; Wagner, L.; Zakai, A.; Bastien, J. Bringing the web up to speed with WebAssembly. In Proceedings of the 38th ACM SIGPLAN Conference on Programming Language Design and Implementation, Barcelona, Spain, 18–23 June 2017; pp. 185–200.
- w3c. World Wide Web Consortium (W3C) Brings a New Language to the Web as WebAssembly Becomes a W3C Recommendation. 2019. Available online: https://www.w3.org/2019/12/pressrelease-wasm-rec.html.en (accessed on 16 November 2022).
- Mozilla Using the WebAssembly JavaScript API-WebAssembly | MDN. 2022. Available online: https://developer.mozilla.org/en-US/docs/WebAssembly/Using_the_JavaScript_API (accessed on 29 November 2022).
- Node.js. Node.js. 2022. Available online: https://nodejs.org/en (accessed on 27 November 2022).
- Wasi. WASI|. 2022. Available online: https://wasi.dev (accessed on 25 November 2022).
- Emscripten. Main—Emscripten 3.1.26-git (dev) Documentation. 2022. Available online: https://emscripten.org (accessed on 1 December 2022).
- Rustwasm. Wasm-Pack. 2022. Available online: https://rustwasm.github.io/wasm-pack (accessed on 23 November 2022).
- WebAssembly. Wabt. 2022. Available online: https://github.com/WebAssembly/wabt (accessed on 26 November 2022).
- w3c. Same Origin Policy-Web Security. 2022. Available online: https://www.w3.org/Security/wiki/Same_Origin_Policy (accessed on 26 November 2022).
- Docs, W. Security-WebAssembly. 2022. Available online: https://webassembly.org/docs/security/#users (accessed on 3 November 2022).
- Lehmann, D.; Kinder, J.; Pradel, M. Everything Old is New Again: Binary Security of WebAssembly. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), 12–14 August 2020; USENIX Association: Berkeley, CA, USA, 2020; pp. 217–234.
- McFadden, B.; Lukasiewicz, T.; Dileo, J.; Engler, J. Security Chasms of Wasm. 2018. NCC Group Whitepaper. Available online: https://git.edik.cn/book/awesome-wasm-zh/raw/commit/e046f91804fb5deb95affb52d6348de92c5bd99c/spec/us-18-Lukasiewicz-WebAssembly-A-New-World-of-Native_Exploits-On-The-Web-wp.pdf (accessed on 5 January 2024).
- Hilbig, A.; Lehmann, D.; Pradel, M. An Empirical Study of Real-World WebAssembly Binaries: Security, Languages, Use Cases. In Proceedings of the Web Conference 2021, Ljubljana, Slovenia, 19–23 April 2021; WWW ’21. pp. 2696–2708.
- Fastly. Summary of June 8 Outage. 2021. Available online: https://www.fastly.com/blog/summary-of-june-8-outage (accessed on 29 November 2022).
- Szabo, N. Smart Contracts. 1994. Available online: https://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart.contracts.html (accessed on 5 February 2024).
- PeckShield. Defeating EOS Gambling Games: The Tech Behind Random Number Loophole. Medium 2018. Available online: https://peckshield.medium.com/defeating-eos-gambling-games-the-tech-behind-random-number-loophole-cf701c616dc0 (accessed on 5 January 2024).
- Huang, Y.; Jiang, B.; Chan, W.K. EOSFuzzer: Fuzzing EOSIO Smart Contracts for Vulnerability Detection. In Proceedings of the 12th Asia-Pacific Symposium on Internetware, Singapore, 1–3 November 2020; ACM: New York, NY, USA, 2020.
- He, N.; Zhang, R.; Wang, H.; Wu, L.; Luo, X.; Guo, Y.; Yu, T.; Jiang, X. EOSAFE: Security Analysis of EOSIO Smart Contracts. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Vancouver, BC, Canada, 11–13 August 2021; USENIX Association: Berkeley, CA, USA, 2021; pp. 1271–1288.
- Alliance, C.T. The Illicit Cryptocurrency Mining Threat. 2018. Available online: https://cyberthreatalliance.org/wp-content/uploads/2018/09/CTA-Illicit-CryptoMining-Whitepaper.pdf (accessed on 25 November 2022).
- Musch, M.; Wressnegger, C.; Johns, M.; Rieck, K. New Kid on the Web: A Study on the Prevalence of WebAssembly in the Wild. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Gothenburg, Sweden, 19–20 June 2019; Springer: Cham, Switzerland, 2019; pp. 23–42.
- Lonkar, A.; Chandrayan, S. The dark side of WebAssembly. In Proceedings of the Virus Bulletin Conference, Montreal, QC, Canada, 3–5 October 2018.





