
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Ammar Odeh | -- | 2064 | 2023-12-08 19:08:57 | | | |
| 2 | Peter Tang | Meta information modification | 2064 | 2023-12-11 02:02:24 | | |
Video Upload Options
Cybersecurity finds widespread applications across diverse domains, encompassing intelligent industrial systems, residential environments, personal gadgets, and automobiles. This has spurred groundbreaking advancements while concurrently posing persistent challenges in addressing security concerns tied to IoT devices. IoT intrusion detection involves using sophisticated techniques, including deep learning models such as convolutional neural networks (CNNs), recurrent neural networks (RNNs), and anomaly detection algorithms, to identify unauthorized or malicious activities within IoT ecosystems. These systems continuously monitor and analyze network traffic and device behavior, seeking patterns that deviate from established norms. When anomalies are detected, security measures are triggered to thwart potential threats. IoT intrusion detection is vital for safeguarding data integrity, ensuring users’ privacy, and maintaining critical systems’ reliability and safety.
1. Introduction
2. IoT Security Challenges
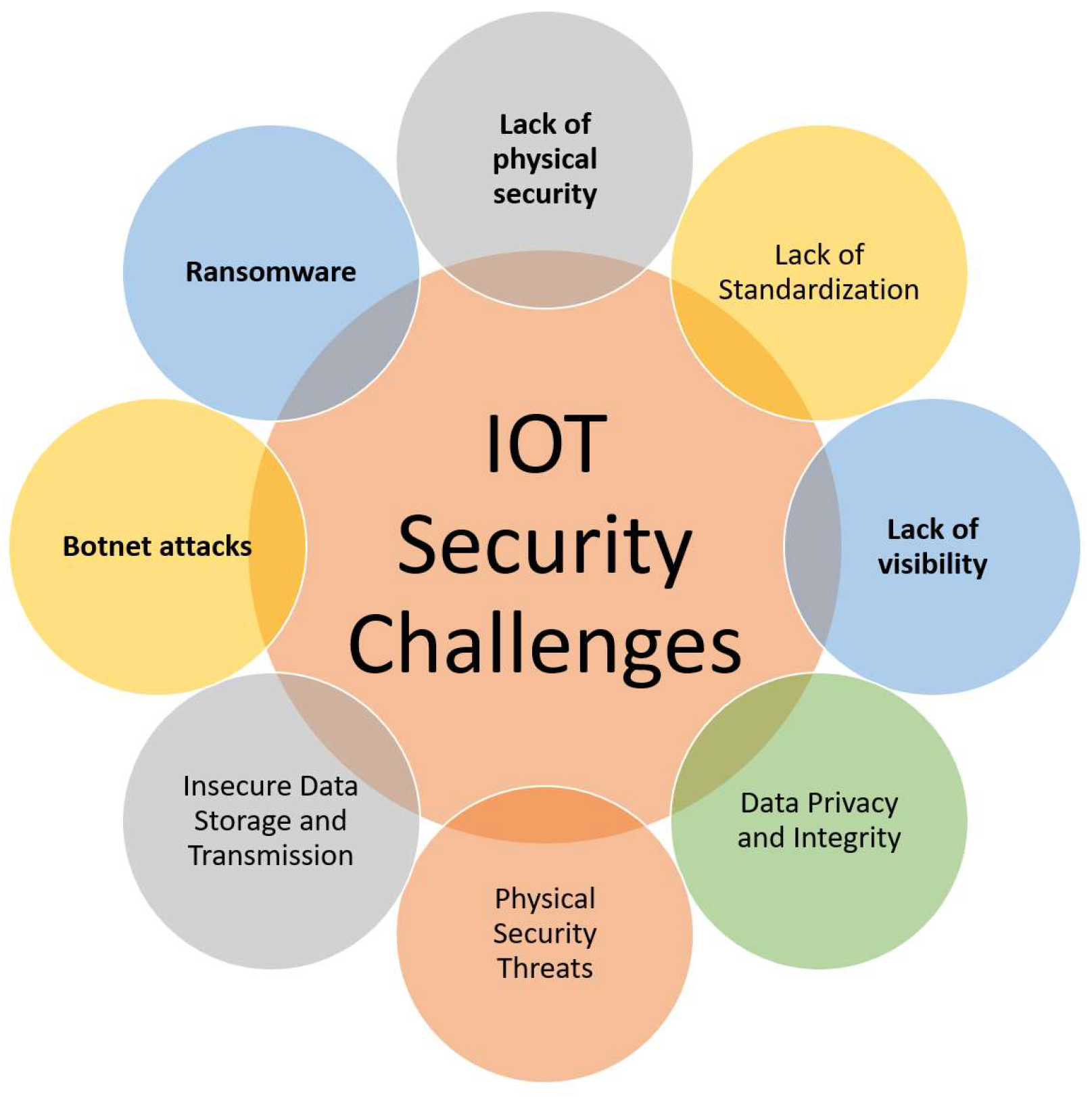
2.1. Lack of Physical Security
2.2. Lack of Standardization
2.3. Lack of Visibility
2.4. Data Privacy and Integrity
2.5. Physical Security Threats
2.6. Insecure Data Storage and Transmission
2.7. Botnet Attacks
2.8. Ransomware
3. Intrusion Detection Systems (IDS)
References
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294.
- Ibrahim, H. A Review on the Mechanism Mitigating and Eliminating Internet Crimes using Modern Technologies: Mitigating Internet crimes using modern technologies. Wasit J. Comput. Math. Sci. 2022, 1, 76–108.
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the Internet of things (IoT): A security taxonomy for IoT. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018.
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for Internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685.
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946.
- Køien, G.M. Zero-Trust Principles for Legacy Components: 12 Rules for Legacy Devices: An Antidote to Chaos. Wirel. Pers. Commun. 2021, 121, 1169–1186.
- Chen, Z.; Liu, J.; Shen, Y.; Simsek, M.; Kantarci, B.; Mouftah, H.T.; Djukic, P. Machine learning-enabled iot security: Open issues and challenges under advanced persistent threats. ACM Comput. Surv. 2022, 55, 1–37.
- Le-Dang, Q.; Le-Ngoc, T. Internet of Things (IoT) infrastructures for smart cities. In Handbook of Smart Cities: Software Services and Cyber Infrastructure; Springer: Berlin/Heidelberg, Germany, 2018; pp. 1–30.
- Shaukat, K.; Alam, T.M.; Hameed, I.A.; Khan, W.A.; Abbas, N.; Luo, S. A review on security challenges in Internet of things (IoT). In Proceedings of the 2021 26th International Conference on Automation and Computing (ICAC), Portsmouth, UK, 2–4 September 2021.
- Ahanger, T.A.; Aljumah, A. Internet of Things: A comprehensive study of security issues and defense mechanisms. IEEE Access 2018, 7, 11020–11028.
- Omolara, A.E.; Alabdulatif, A.; Abiodun, O.I.; Alawida, M.; Alabdulatif, A.; Arshad, H. The internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 2022, 112, 102494.
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481.
- Cuppari, R.; Schmeier, S.; Demuth, S. Preventing Conflicts, Fostering Cooperation—The Many Roles of Water Diplomacy; ICWRGC: Koblenz, Germany, 2017.
- Kotenko, I.; Izrailov, K.; Buinevich, M. Static analysis of information systems for IoT cyber security: A survey of machine learning approaches. Sensors 2022, 22, 1335.
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.-S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 18, 2796.
- Qin, J.; Wang, J.; Lei, T.; Sun, G.; Yue, J.; Wang, W.; Chen, J.; Qian, G. Deep learning-based software and hardware framework for a noncontact inspection platform for aggregate grading. Measurement 2023, 211, 112634.
- Chen, X.; Wang, Z.; Hua, Q.; Shang, W.-L.; Luo, Q.; Yu, K. AI-empowered speed extraction via port-like videos for vehicular trajectory analysis. IEEE Trans. Intell. Transp. Syst. 2022, 24, 4541–4552.
- Shen, Y.; Zhu, J.; Deng, Z.; Lu, W.; Wang, H. EnsDeepDP: An Ensemble Deep Learning Approach for Disease Prediction Through Metagenomics. IEEE/ACM Trans. Comput. Biol. Bioinform. 2022, 20, 986–998.
- Ali, B.; Awad, A.I. Cyber and physical security vulnerability assessment for IoT-based smart homes. Sensors 2018, 18, 817.
- Attkan, A.; Ranga, V. Cyber-physical security for IoT networks: A comprehensive review on traditional, blockchain and artificial intelligence based key-security. Complex Intell. Syst. 2022, 8, 3559–3591.
- Kumar, N.M.; Mallick, P.K. Blockchain technology for security issues and challenges in IoT. Procedia Comput. Sci. 2018, 132, 1815–1823.
- Frustaci, M.; Pace, P.; Aloi, G. Securing the IoT world: Issues and perspectives. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 18–20 September 2017.
- Ahmed, S.; Kalsoom, T.; Ramzan, N.; Pervez, Z.; Azmat, M.; Zeb, B.; Ur Rehman, M. Towards supply chain visibility using Internet of things: A dyadic analysis review. Sensors 2021, 21, 4158.
- Kothari, S.S.; Jain, S.V.; Venkteshwar, A. The impact of IOT in supply chain management. Int. Res. J. Eng. Technol 2018, 5, 257–259.
- Wang, T.; Bhuiyan, M.Z.A.; Wang, G.; Qi, L.; Wu, J.; Hayajneh, T. Preserving balance between privacy and data integrity in edge-assisted Internet of Things. IEEE Internet Things J. 2019, 7, 2679–2689.
- Kim, T.; Ochoa, J.; Faika, T.; Mantooth, H.A.; Di, J.; Li, Q.; Lee, Y. An overview of cyber-physical security of battery management systems and adoption of blockchain technology. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 10, 1270–1281.
- Khalaf, O.I.; Abdulsahib, G.M. Optimized dynamic storage of data (ODSD) in IoT based on blockchain for wireless sensor networks. Peer Peer Netw. Appl. 2021, 14, 2858–2873.
- Zhang, L.; Peng, M.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Secure and efficient data storage and sharing scheme for blockchain-based mobile-edge computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4315.
- Injadat, M.; Moubayed, A.; Shami, A. Detecting botnet attacks in IoT environments: An optimized machine learning approach. In Proceedings of the 2020 32nd International Conference on Microelectronics (ICM), Aqaba, Jordan, 14–17 December 2020.
- Ali, I.; Ahmed, A.I.A.; Almogren, A.; Raza, M.A.; Shah, S.A.; Khan, A.; Gani, A. Systematic literature review on IoT-based botnet attack. IEEE Access 2020, 8, 212220–212232.
- Humayun, M.; Jhanjhi, N.; Alsayat, A.; Ponnusamy, V. Internet of things and Ransomware: Evolution, mitigation and prevention. Egypt. Inform. J. 2021, 22, 105–117.
- Zahra, S.R.; Chishti, M.A. Ransomware and Internet of things: A new security nightmare. In Proceedings of the 2019 9th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 10–11 January 2019.
- Abu Al-Haija, Q.; Al Badawi, A. High-performance intrusion detection system for networked UAVs via deep learning. Neural Comput. Appl. 2022, 34, 10885–10900.
- Alsulami, A.A.; Abu Al-Haija, Q.; Tayeb, A.; Alqahtani, A. An Intrusion Detection and Classification System for IoT Traffic with Improved Data Engineering. Appl. Sci. 2022, 12, 12336.
- Prajapati, P.; Bhatt, B.; Zalavadiya, G.; Ajwalia, M.; Shah, P. A review on recent intrusion detection systems and intrusion prevention systems in IoT. In Proceedings of the 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 28–29 January 2021.
- Kumar, A.; Abhishek, K.; Ghalib, M.R.; Shankar, A.; Cheng, X. Intrusion detection and prevention system for an IoT environment. Digit. Commun. Netw. 2022, 8, 540–551.
- Pandu, V.; Mohan, J.; Kumar, T. Network intrusion detection and prevention systems for attacks in IoT systems. In Countering Cyber Attacks and Preserving the Integrity and Availability of Critical Systems; IGI Global: Hershey, PA, USA, 2019; pp. 128–141.
- Jakka, G.; Alsmadi, I.M. Ensemble Models for Intrusion Detection SystemClassification. Int. J. Smart Sens. Adhoc Netw. 2022, 3, 8.





