Cybersecurity finds widespread applications across diverse domains, encompassing intelligent industrial systems, residential environments, personal gadgets, and automobiles. This has spurred groundbreaking advancements while concurrently posing persistent challenges in addressing security concerns tied to IoT devices. IoT intrusion detection involves using sophisticated techniques, including deep learning models such as convolutional neural networks (CNNs), recurrent neural networks (RNNs), and anomaly detection algorithms, to identify unauthorized or malicious activities within IoT ecosystems. These systems continuously monitor and analyze network traffic and device behavior, seeking patterns that deviate from established norms. When anomalies are detected, security measures are triggered to thwart potential threats. IoT intrusion detection is vital for safeguarding data integrity, ensuring users’ privacy, and maintaining critical systems’ reliability and safety.
1. Introduction
The Internet of Things (IoT) represents a transformative concept where everyday objects, devices, and appliances are interconnected, enabling them to collect and exchange data
[1]. This vast network extends the Internet’s reach beyond traditional devices like computers and smartphones, encompassing everything from household appliances and wearables to vehicles and industrial machinery. This seamless connectivity offers unparalleled convenience, fostering smarter cities, enhanced healthcare, and more efficient industries—
Figure 1 shows the top IoT applications
[2].
Figure 1.
The top IoT Applications.
However, with this rapid expansion and integration of devices into daily life, several challenges arise, particularly in security
[3][4][3,4]. The vast number of connected devices presents a large attack surface, making them potential entry points for malicious actors. Moreover, the lack of standardization, default insecure settings, and limited computational power in many IoT devices compound these security vulnerabilities. As a result, there is an imperative need for robust security solutions to safeguard the ever-evolving IoT landscape
[5].
Furthermore, the IoT ecosystem’s heterogeneous nature, characterized by various manufacturers, protocols, and software stacks, complicates establishing a unified security approach. Many IoT devices, designed primarily for functionality and cost-effectiveness, often lack regular software updates, exposing them to known security threats for prolonged periods
[6][7][6,7]. Data privacy is another pressing concern. As these devices continually collect vast amounts of data, sensitive information can be accessed or misused, threatening individual privacy and corporate confidentiality
[8].
Addressing these security challenges is paramount to ensure that the IoT realizes its full potential without compromising user trust and safety
[9]. As the adoption of IoT continues to surge, there is an increasing emphasis on developing sophisticated security measures, including advanced intrusion detection systems and adaptive threat response mechanisms. Only by prioritizing and innovating in the realm of security can the promise of a truly connected, innovative, and safe world be achieved
[10][11][10,11].
Moreover, the physical nature of IoT devices adds another layer of vulnerability. Unlike purely digital platforms, these devices can be physically tampered with, leading to breaches not just in data but also in their operational integrity. Consider smart infrastructure in cities or hospital health devices; tampering could have real-world, life-threatening consequences
[12].
This interconnectedness, while being the strength of the IoT, also becomes its Achilles’ heel. A breach in one device can potentially cascade, affecting a network of interconnected systems, emphasizing the need for holistic security frameworks. Collaboration across industries, manufacturers, and regulatory bodies is essential to develop and enforce standards that ensure the resilience and safety of the IoT ecosystem. As research and development forge ahead, integrating security from the inception of device design, rather than as an afterthought, will be crucial in defining the future of a secure and efficient IoT landscape
[13][14][15][13,14,15]. The author in
[16][17][16,17] introduces an enhanced aggregate segmentation mask RCNN model (AS Mask RCNN) for grading mixed aggregates. The study conducted three different experiments and found that the AS Mask RCNN achieved an impressive accuracy of over 89.13% across all experimental scenarios. Compared to the faster RCNN and mask R-CNN models, it demonstrated an accuracy improvement of 8.85%. It reduced the processing time for single image segmentation by 1.29 s, making it suitable for near real-time field detection requirements. The paper also presents a self-developed noncontact testing platform for aggregate grading that can be applied in complex environments. This platform facilitates digital, automated, and intelligent noncontact grading of mixed aggregates, ultimately enhancing the accuracy of aggregate grading testing and supporting the high-quality development of reservoir dam construction in China. The author’s work focuses on the significant role of the human microbiome in predicting certain diseases. They acknowledge the challenges posed by limited samples and high-dimensional features in microbiome data for machine learning methods. The author introduces a novel ensemble deep-learning disease prediction method to address this. The approach combines unsupervised and supervised learning techniques. It starts with unsupervised deep learning to discover potential sample representations. Then, these representations are used to develop a disease-scoring strategy, creating informative features for ensemble analysis. A score selection mechanism is implemented to ensure optimal ensemble performance, and performance-enhancing features are incorporated with the original data
[18].
2. IoT Security Challenges
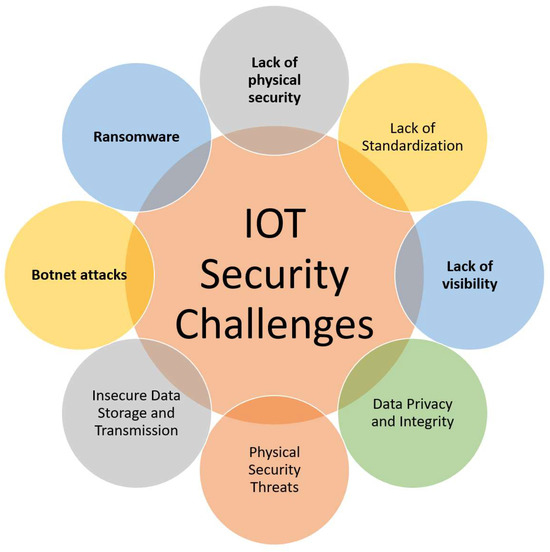
The IoT (Internet of Things) brings about a revolution in connectivity, enabling devices to communicate seamlessly. However, with this increased connectivity comes a myriad of security challenges. Figure 2 depicts some of the most pressing security challenges associated with the IoT.
Figure 2.
IoT security challenges.
2.1. Lack of Physical Security
The absence of robust physical safeguards on IoT devices makes them vulnerable to unauthorized access. Devices stationed in isolated locations over extended periods are particularly susceptible to tampering. The ease with which attackers can exploit IoT devices with minimal physical protection poses significant security challenges
[19].
Consider, for instance, the potential for IoT devices to be compromised via malware-laden USB flash drives. While it is incumbent upon IoT device manufacturers to prioritize their products’ physical security, engineering secure yet cost-effective transmitters and sensors remains a daunting task for them
[20].
2.2. Lack of Standardization
A diverse range of manufacturers produces IoT devices, each adhering to unique standards and protocols. This absence of standardized security measures can lead to vulnerabilities, offering potential entry points for exploitation.
Furthermore, this fragmentation in manufacturing practices and protocols complicates establishing a cohesive security framework for the IoT. Since devices might communicate differently and prioritize varied security aspects, ensuring compatibility and security across the board becomes challenging. This disjointed landscape hinders interoperability and makes it harder to deploy universal security patches or updates. For users, this means a heightened risk, as one weak device can compromise the security of an entire connected network. As the IoT ecosystem continues to expand, industry-wide collaboration is urgently needed to establish and enforce consistent security standards, ensuring a safer and more integrated digital future
[21][22][21,22].
2.3. Lack of Visibility
For I.T. teams, obtaining a comprehensive view of all devices on the network is daunting, primarily because numerous devices are not cataloged in the I.T. inventory. Often overlooked by I.T. teams, devices such as coffee machines, ventilation systems, and air conditioners are not typically tracked
[23].
If security teams are unaware of the devices connected to the network, they can not effectively prevent breaches. The insufficient visibility into IoT devices complicates the I.T. department’s task of accurately identifying and monitoring assets that require protection
[24].
2.4. Data Privacy and Integrity
In IoT, data privacy emerges as a paramount security concern. User data traverses many devices, from medical equipment divulging patient details to intelligent toys and wearables revealing personal information. To illustrate this, a cybercriminal could potentially harvest corporate information, exposing, selling, or leveraging it to blackmail the proprietor
[25].
2.5. Physical Security Threats
Given their physical nature, IoT devices are inherently vulnerable to direct interference and manipulation. Malicious actors can exploit these devices by gaining hands-on access to their hardware components, potentially altering their functionalities or extracting sensitive data. This tangible aspect of IoT emphasizes the importance of digital and physical security measures to protect against unauthorized interventions
[26].
2.6. Insecure Data Storage and Transmission
A significant number of IoT devices lack data encryption for both stored and transmitted information. This oversight exposes the data, allowing potential eavesdroppers to intercept and access it without authorization. Such lax security measures underscore the pressing need for enhanced encryption protocols in the IoT landscape to safeguard against breaches and unauthorized intrusions
[27]. Additionally, the absence of robust encryption practices exacerbates the risk of man-in-the-middle attacks, where malicious actors can intercept and potentially alter data as it is being transmitted between devices. This not only compromises the confidentiality of the information but also its integrity. Furthermore, with the growing reliance on IoT devices in critical sectors such as healthcare, transportation, and energy, the consequences of unauthorized data access could be dire, ranging from personal privacy breaches to large-scale infrastructure disruptions. For these reasons, manufacturers must prioritize and implement advanced encryption techniques, ensuring both the security and trustworthiness of IoT device communications
[28].
2.7. Botnet Attacks
A significant security issue with IoT pertains directly to the devices themselves. Their inherent security vulnerabilities make them prime targets for botnet infiltrations.
Essentially, a botnet is an ensemble of machines compromised by malware. Attackers harness these compromised machines to flood targets with overwhelming request traffic. Unlike conventional computers, IoT devices often lack regular security updates, heightening their susceptibility to malware exploits. Consequently, malicious actors can swiftly transform these devices into botnets, becoming conduits for vast request traffic
[29][30][29,30].
2.8. Ransomware
In the context of IoT security, ransomware poses a significant threat by encrypting and barring access to vital files. To regain access, hackers typically demand a ransom in exchange for the decryption key
[31].
While currently uncommon, IoT devices with subpar security might become future victims of ransomware. As the value and dependence on healthcare devices, smart homes, and other intelligent appliances grow, they could become increasingly attractive targets, especially given their critical importance to users
[32].
3. Intrusion Detection Systems (IDS)
Intrusion detection refers to identifying malicious activities carried out against information systems. These malevolent acts, termed intrusions, are efforts to gain unauthorized access to a computer system. Intruders can be categorized into two main types: internal and external. Internal intruders are individuals within the network who, despite having some legitimate access, aim to elevate their access privileges to misuse resources they are not authorized for. In contrast, external intruders are individuals outside the network aiming to infiltrate it and access system information without permission
[33].
Both types of intruders pose distinct challenges. Internal intruders, already having some degree of legitimate access, can exploit vulnerabilities from within, making their actions more complicated to detect. Their familiarity with the system’s architecture and potential weak points can make their intrusions more targeted and potentially more damaging. On the other hand, external intruders, although initially lacking access, often employ a wide range of techniques, from brute-force attacks to sophisticated phishing schemes, to breach the system’s defenses
[34].
Moreover, the rise of IoT devices and the expanding digital landscape have further complicated intrusion detection. With more entry points and a diverse range of devices, networks are more susceptible than ever. This underscores the importance of robust security measures, continuous system monitoring, and regular updates to defend against evolving threats. Additionally, organizations must foster a culture of security awareness, ensuring that every internal or external user is well-informed about potential risks and best practices to mitigate them.
The evolving dynamics of cyber threats necessitate an adaptive and layered approach to security. Intrusion detection systems (IDS) are just one component of a comprehensive cybersecurity strategy. Beyond simple detection, the focus has shifted towards intrusion prevention systems (IPS) that not only detect but also take proactive measures to prevent unauthorized access
[35][36][35,36].
Furthermore, with the integration of artificial intelligence and machine learning in security systems, there is an opportunity to predict and identify novel threats before they manifest. These predictive systems analyze patterns and behaviors, allowing them to flag anomalous activities even if they do not match known threat signatures.
Yet, technology alone is not the panacea. Human factors play a significant role in security breaches. Regular training sessions, workshops, and awareness campaigns should be organized for employees and users. This ensures that they are aware of the potential risks and equipped with the knowledge to recognize and report suspicious activities
[37].
The principle of least privilege (PoLP) should be strictly adhered to, meaning that users should only be granted access to the information and resources necessary for their specific tasks, reducing the potential damage of an internal intrusion.
In a world where cyber threats continually evolve, staying a step ahead is crucial. This requires cutting-edge technology, strategic planning, and an informed and vigilant user base. By integrating these elements, organizations can fortify their defenses, ensuring data integrity and maintaining the trust of their users
[38].