Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | José Simão | -- | 1775 | 2023-12-07 10:52:05 | | | |
| 2 | Rita Xu | -90 word(s) | 1685 | 2023-12-07 11:01:09 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Severino, R.; Simão, J.; Datia, N.; Serrador, A. Hybrid Intelligent Transport Systems Networks. Encyclopedia. Available online: https://encyclopedia.pub/entry/52483 (accessed on 08 February 2026).
Severino R, Simão J, Datia N, Serrador A. Hybrid Intelligent Transport Systems Networks. Encyclopedia. Available at: https://encyclopedia.pub/entry/52483. Accessed February 08, 2026.
Severino, Ricardo, José Simão, Nuno Datia, António Serrador. "Hybrid Intelligent Transport Systems Networks" Encyclopedia, https://encyclopedia.pub/entry/52483 (accessed February 08, 2026).
Severino, R., Simão, J., Datia, N., & Serrador, A. (2023, December 07). Hybrid Intelligent Transport Systems Networks. In Encyclopedia. https://encyclopedia.pub/entry/52483
Severino, Ricardo, et al. "Hybrid Intelligent Transport Systems Networks." Encyclopedia. Web. 07 December, 2023.
Copy Citation
Cooperative intelligent transport systems (C-ITS) continue to be developed to enhance transportation safety and sustainability. The communication of vehicle-to-everything (V2X) systems is inherently open, leading to vulnerabilities that attackers can exploit. This represents a threat to all road users, as security failures can lead to privacy violations or even fatalities.
C-ITS
ITS-G5
cellular network
hybrid network
1. Introduction
Transportation has always been crucial in human society. It connects people, allows access to essential services and promotes prosperity. However, the growing number of vehicles [1] has led to concerns about road traffic and safety. Despite stricter European road safety regulations [2], accidents persist, leading to fatalities. Moreover, increased road traffic has resulted in congestion, higher gas emissions and decreased air quality [3]. The 2018 global status report on road safety [1] from the World Health Organisation (WHO) alerts that the number of road traffic deaths worldwide remains unacceptably high, with 1.35 million people dying each year—the eighth leading cause of death for people of all ages and the number one cause for children and young adults.
Considering these circumstances, finding strategies to make transportation safer becomes essential. In the last few years, progress has been made in the field of cooperative intelligent transport systems (C-ITS) [4], particularly in the architecture of solutions that enable vehicles to exchange information with each other (V2V), the road infrastructure (V2I), and with pedestrians (V2P), being therefore known as vehicle-to-everything (V2X). The main C-ITS goal is to enable communication and information exchange among road elements, providing cooperation and, thus, increasing safety, mobility and sustainability [5].
Despite the potential benefits, C-ITS/V2X communications are inherently open. This openness creates vulnerabilities [6] that attackers can exploit, representing a significant threat to all road users, as security failures can lead to privacy violations or even fatalities. These security and privacy challenges must be addressed to ensure that road safety is not compromised [7]. According to Serban et al. [8], “Security plays a crucial role in cooperative applications because a security breach can easily lead to human casualties”. Moreover, C-ITS relies heavily on communication between vehicles that have the necessary equipment installed. This issue is also raised by Yoshizawa et al. [9], where it is referred that, although in the European Norm (EN) 302 665 (V1.1.1) [10], the European Telecommunications Standards Institute (ETSI) has defined handheld devices as one of the types of ITS stations, subsequent ETSI specifications have mainly focused on a vehicle-centric view. In this regard, a high fatality rate is correlated with soft-mobility road users [1]. Therefore, in the development of C-ITS-based systems, it is essential to broaden the perspective beyond connected vehicles, also considering the needs of soft-mobility users (e.g., cyclists) and legacy vehicles that do not have the required equipment—the on-board units (OBUs).
To illustrate these issues, some possible scenarios are described. An attacker could perform a Sybil attack, as illustrated in Figure 1, where he claims the existence of non-existing vehicles at multiple locations [7], creating confusion and disrupting communication. This could lead to inaccurate traffic information (e.g., fake congestion), which can cause misinformed decision-making by drivers.
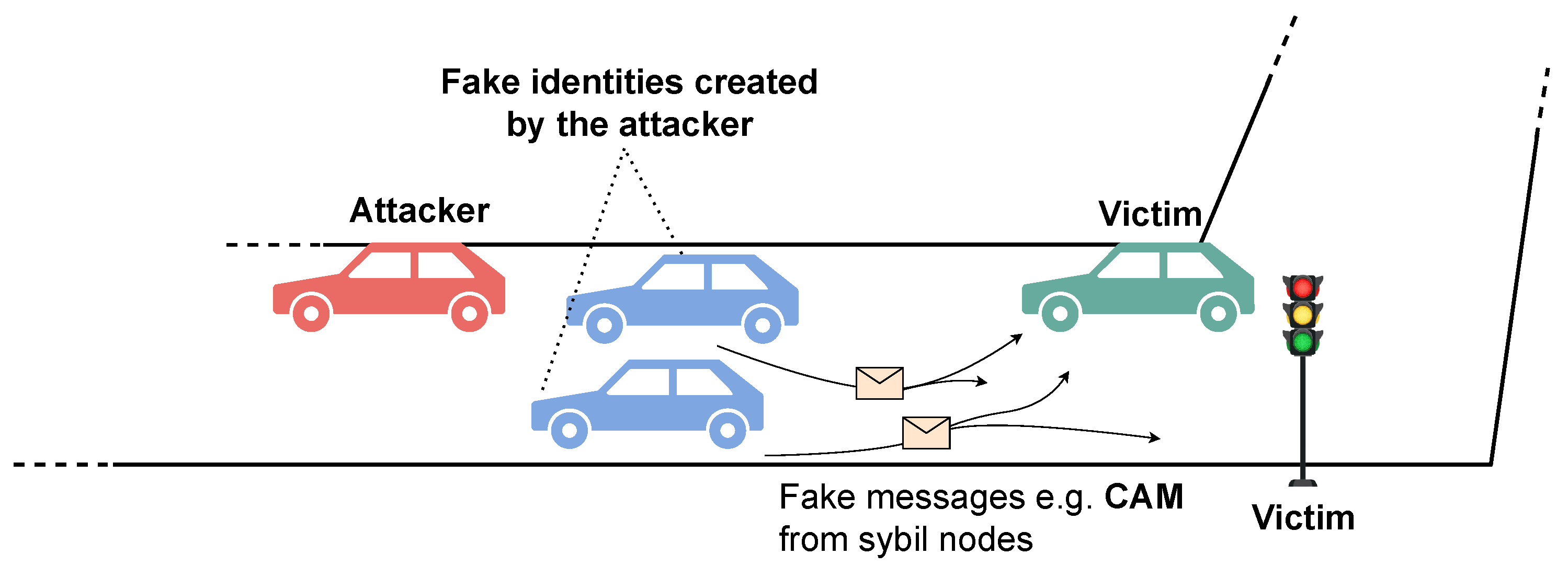
Figure 1. Sybil attack where the attacker claims his existence at multiple locations.
The situation depicted in Figure 2 exemplifies why it is beneficial to include soft-mobility users and legacy vehicles in the C-ITS ecosystem. In this scenario, an accident occurred, and vehicles (legacy and G5-connected) were approaching. The lack of information about the situation makes it unpredictable and unsafe. The cyclist and the pedestrians present could securely notify ITS central systems. Information about this event could then be disseminated to connected vehicles.

Figure 2. Accident where cooperation between soft-mobility users and the G5 network would be beneficial.
2. C-ITS
A general overview of V2X systems will be given for a better understanding of C-ITS technology. V2X is a collective term incorporating several communication modes that enable communication among road elements. V2X communication systems can use technologies based on the IEEE 802.11p protocol that operates in the 5.9 GHz frequency band, having been designed to standardise vehicular communication systems. The IEEE 802.11p protocol is the basis of some standards for V2X communication [9], including:
-
Dedicated short-range communications (DSRC) with wireless access in vehicular environments (WAVE) as the upper layer in the United States of America.
-
ITS-G5 with C-ITS as the upper layer in Europe.
C-ITS refers to the integration of communication and information technologies with the support of transport infrastructures to provide an improvement in terms of traffic safety, mobility and sustainability, thus leading to more efficient and safer transportation [5][11]. Moreover, C-ITS is composed of multiple sub-systems [10], such as handheld ITS sub-systems (such as smartphones); the central ITS sub-system; vehicle ITS sub-system present in vehicles; and roadside ITS sub-systems to be on traffic lights and other roadside infrastructures. An ITS-S is a functional entity specified by the ITS-S reference architecture [10]. The reference architecture follows the principles of the open systems interconnection (OSI) model for layered communication protocols [12].
Many ITS applications require one of two communication strategies [13] or a combination of both: Periodic status exchange, where messages are needed by apps to know about the status of a vehicle or a roadside terminal, and event-driven information—messages informing about a specific event. Therefore, ETSI has defined two essential messaging services:
-
A cooperative awareness message (CAM) [14] provides awareness of the surrounding environment by periodically sending status data to nodes within a single-hop distance.
-
Decentralised environmental notification message (DENM) [15] provides timely and relevant information about the driving environment and traffic events via multi-hop transmission to cover a specific geographic dissemination area.
There are other messages in C-ITS [16], but DENM and CAM are the most widely used.
3. PKI as an Architecture for Securing ITS Communications
Public key infrastructure (PKI) plays a crucial role in ensuring the security of digital communications [17]. Particularly, PKI is a building block for C-ITS security, also referred to as C-ITS communications security architecture and security management in the ETSI specification [18]. The most relevant elements are the ITS-S, the root certificate authority (CA), which serves as a trust anchor and provides certificates to the enrolment authority (EA) and authorisation authority (AA). EA manages enrolment credentials (EC), which are long-term certificates used for authentication and access to ITS communications. AA issues authorisation tickets (AT), also known as pseudonym certificates, which are short-term certificates that allow ITS-S to access specific ITS services while masking their identity. The sequence of interactions that occurs from the moment a vehicle intends to enter the C-ITS network and send messages to another ITS-S is depicted in Figure 3.
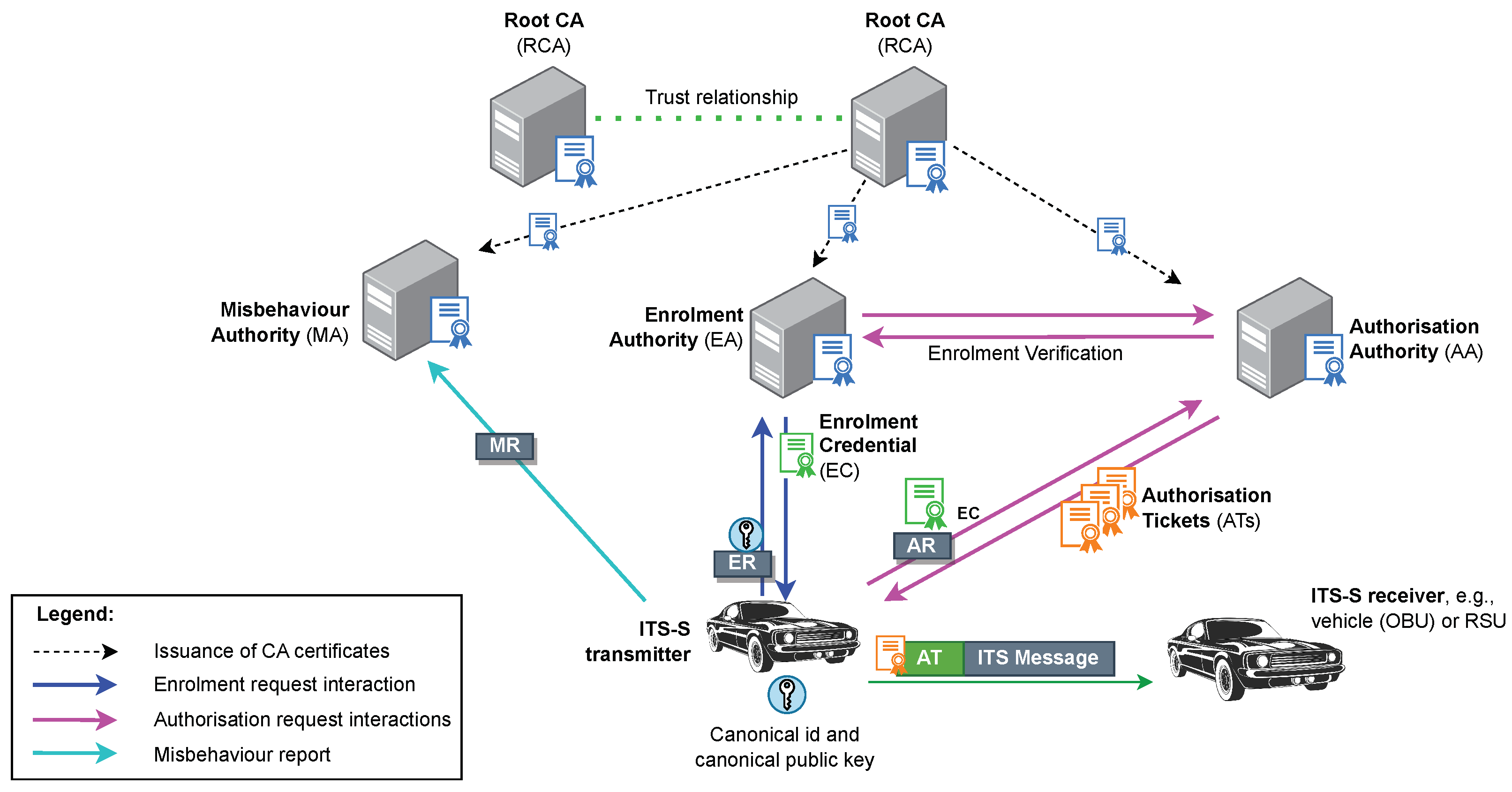
Figure 3. PKI architecture in C-ITS.
PKI for C-ITS achieves a high level of security. Regarding handling privacy issues, C-ITS messages include several identifiers that can be used for privacy violations. As a countermeasure, users’ privacy is protected by a pseudonym scheme, i.e., changing the AT frequently, which also changes all its identifiers. Message integrity, authenticity and non-repudiation allow properties to be ensured by creating a digital signature (using an AT) over the message. The ITS-S transmitter can use its AT to generate a digital signature. When a signed message is received, the receiver can verify the digital signature. Confidentiality can be ensured by encrypting the packets with a key shared with the ITS-S receiver [19].
Despite the high-security level C-ITS PKI provides, it also has its limitations. The main drawbacks of PKI are due to processing and communication overhead latency [20]. The first one is due to the use of asymmetric cryptography to sign and verify each message, which is quite computationally demanding. The ability of each vehicle to check its certificate revocation list for a large number of certificates and verify the senders’ signatures on the received messages in a timely manner forms an inevitable challenge to C-ITS efficiency requirements [21]. Lastly, C-ITS PKI experiences high communication overheads because the certificate sent (AT) for message verification is large, causing inefficiency.
4. Hybrid ITS Networks Approaches
In 2022, Gonçalves et al. [22] aimed to develop a system capable of enhancing users’ awareness regarding potentially dangerous situations around them. They also highlighted the relevance of hybrid networks in ITS, stating that among all types of road users who travel and move daily, those using soft-mobility transportation forms are the most vulnerable. The proposed solution uses hybrid networks (G5 and cellular), allowing ITS equipment to communicate with other devices (not directly) via Wi-Fi or cellular networks.
Bissmeyer et al. [23] analyse PKI as a security concept to secure data in hybrid vehicular communications. However, the concept of hybrid networks differs from the one adopted in this study. In [23], hybrid communications are ideally used to support the reliability of communication by using redundant communication technologies. The security concept is described as securing these communications in the presence of multiple radio technologies using different physical channels to transmit V2X messages.
Lastly, Scholliers et al. [24] conducted performance measurements of communication between vehicles and infrastructure for ITS-G5 and LTE. The goal was to test the connectivity between different network technologies, allowing fast handovers to enable the system to react quickly, thus exploiting multiple networks and prioritising them by preference and signal strength, among other criteria. Similarly to [23], the adopted hybrid network is also applied in the context of using LTE as another access technology through an ITS-S.
Each study has its motivations for the use of hybrid networks. Some approaches, such as the ones followed in [23][24], focus on using hybrid networks to utilise different access technologies (G5 and LTE) within an ITS station. Nonetheless, this work develops a C-ITS hybrid environment that integrates non-ITS station users through a smartphone application. The study proposed in [22] comes closest to this work, although it presents a scenario more focused on road safety. The objective is also to propose a hybrid network architecture while introducing security guarantees, forming a secure hybrid ITS network. Table 1 summarises four relevant aspects of each article.
Table 1. Summary of four relevant aspects in the context of hybrid networks in ITS. Indicates whether the paper: addresses hybrid networks, considers ITS station that uses multiple access technologies, considers users without an OBU and if security aspects are considered.
References
- World Health Organization (WHO). Global Status Report on Road Safety; Technical Report; World Health Organization: Geneva, Switzerland, 2018.
- Vălean, A.I. EU Road Safety Policy Framework 2021–2030, Next Steps towards “Vision Zero”; Technical Report; European Comission: Brussels, Belgium, 2020.
- World Health Organization (WHO). European Regional Status Report on Road Safety; Technical Report; World Health Organization: Geneva, Switzerland, 2019.
- Comission, E. Final Report of the Single Platform for Open Road Testing and Pre-Deployment of Cooperative, Connected and Automated and Autonomous Mobility Platform (CCAM Platform); Technical Report; European Comission: Brussels, Belgium, 2021.
- Forum, I.T. New Directions for Data-Driven Transport Safety Corporate Partnership Board Report; Technical Report; International Transport Forum: Paris, France, 2019.
- Nwakanma, C.I.; Ahakonye, L.A.C.; Njoku, J.N.; Odirichukwu, J.C.; Okolie, S.A.; Uzondu, C.; Ndubuisi Nweke, C.C.; Kim, D.S. Explainable Artificial Intelligence (XAI) for Intrusion Detection and Mitigation in Intelligent Connected Vehicles: A Review. Appl. Sci. 2023, 13, 1252.
- Hasan, M.; Mohan, S.; Shimizu, T.; Lu, H. Securing Vehicle-to-Everything (V2X) Communication Platforms. IEEE Trans. Intell. Veh. 2020, 5, 693–713.
- Serban, A.C.; Poll, E.; Visser, J. A Security Analysis of the ETSI ITS Vehicular Communications. In Proceedings of the Computer Safety, Reliability, and Security Conference, Västerås, Sweden, 18 September 2018; Gallina, B., Skavhaug, A., Schoitsch, E., Bitsch, F., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 365–373.
- Yoshizawa, T.; Singelée, D.; Muehlberg, J.T.; Delbruel, S.; Taherkordi, A.; Hughes, D.; Preneel, B. A Survey of Security and Privacy Issues in V2X Communication Systems. ACM Comput. Surv. 2023, 55, 185.
- ETSI TS 302 665 v1.1.1; ITS Security—Communications Architecture. European Standard (ETSI): Sophia Antipolis, France, 2010.
- Debysern, A. Road Safety in the EU—European Parliamentary Research Service; Technical Report; European Parliamentary: Strasbourg, France, 2019.
- Festag, A. Cooperative intelligent transport systems standards in europe. IEEE Commun. Mag. 2014, 52, 166–172.
- Santa, J.; Pereñìguez, F.; Moragón, A.; Skarmeta, A.F. Experimental evaluation of CAM and DENM messaging services in vehicular communications. Transp. Res. Part C Emerg. Technol. 2014, 46, 98–120.
- ETSI 302 637-2 v1.4.1; ITS Vehicular Communications Basic Set of Applications Part 2: Specification of Cooperative Awareness Basic Service. European Standard (ETSI): Sophia Antipolis, France, 2019.
- ETSI 302 637-3 v1.3.1; ITS Vehicular Communications Basic Set of Applications Part 3: Specification of Decentralised Environmental Notification Basic Service. European Standard (ETSI): Sophia Antipolis, France, 2019.
- ETSI TS 103 301 v1.3.1; ITS Basic Set of Applications—Facilities Layer Protocols and Communication Requirements for Infrastructure Services. European Standard (ETSI): Sophia Antipolis, France, 2020.
- Du, W. Computer & Internet Security: A Hands-On Approach; CreateSpace Independent Publishing Platform: Scotts Valley, CA, USA, 2017.
- ETSI TS 102 940 v2.1.1; ITS Security—ITS Communications Security Architecture and Security Management. European Standard (ETSI): Sophia Antipolis, France, 2021.
- Stotz, J.P.; Kargl, F.; Petit, J. Security Requirements of Vehicle Security Architecture; Technical Report; PRESERVE Project: European Commission: Brussels, Belgium, 2011.
- Abdel Hakeem, S.A.; Abd El-Gawad, M.A.; Kim, H. A Decentralized Lightweight Authentication and Privacy Protocol for Vehicular Networks. IEEE Access 2019, 7, 119689–119705.
- Wasef, A.; Lu, R.; Lin, X.; Shen, X. Complementing public key infrastructure to secure vehicular ad hoc networks (Security and Privacy in Emerging Wireless Networks). IEEE Wirel. Commun. 2010, 17, 22–28.
- Gonçalves, M.; Datia, N.; Serrador, A. A safety perspective for soft mobility in the ITS ecosystem. In Proceedings of the Atas do 13o Simpósio de Informática (Inforum 22), Guarda, Portugal, 8–9 September 2022; pp. 330–341.
- van Dam, J.F.; Bißmeyer, N.; Zimmermann, C.; Eckert, K. Security in Hybrid Vehicular Communication Based on ITS G5, LTE-V, and Mobile Edge Computing. In Proceedings of the AmE 2018 Automotive meets Electronics, 9th GMM-Symposium (Fahrerassistenzsysteme 2018), Dortmund, Germany, 7–8 March 2018; Bertram, T., Ed.; Springer: Wiesbaden, Germany, 2019; pp. 80–91.
- Scholliers, J.; Jutila, M.; Valta, M.; Kauvo, K.; Virtanen, A.; Pyykönen, P. Co-operative Traffic Solutions for Hybrid Communication Environments. Transp. Res. Procedia 2016, 14, 4542–4551.
More
Information
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
554
Revisions:
2 times
(View History)
Update Date:
07 Dec 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




