You're using an outdated browser. Please upgrade to a modern browser for the best experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Pierpaolo Dini | -- | 2612 | 2023-11-24 16:15:46 | | | |
| 2 | Lindsay Dong | + 6 word(s) | 2618 | 2023-11-27 07:08:52 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Dini, P.; Saponara, S. Controller Area Network Cybersecurity. Encyclopedia. Available online: https://encyclopedia.pub/entry/52044 (accessed on 21 December 2025).
Dini P, Saponara S. Controller Area Network Cybersecurity. Encyclopedia. Available at: https://encyclopedia.pub/entry/52044. Accessed December 21, 2025.
Dini, Pierpaolo, Sergio Saponara. "Controller Area Network Cybersecurity" Encyclopedia, https://encyclopedia.pub/entry/52044 (accessed December 21, 2025).
Dini, P., & Saponara, S. (2023, November 24). Controller Area Network Cybersecurity. In Encyclopedia. https://encyclopedia.pub/entry/52044
Dini, Pierpaolo and Sergio Saponara. "Controller Area Network Cybersecurity." Encyclopedia. Web. 24 November, 2023.
Copy Citation
The Controller Area Network, commonly referred to as Controller Area Network (CAN) bus, is a serial standard for field buses that is primarily employed in the automotive industry. It was introduced in the 1980s by Robert Bosch as a means to connect various electronic control units (ECUs).
Controller Area Network (CAN)
Cybersecurity
numerous electronic control units (ECUs)
1. Motivations for Controller Area Network (CAN) Cybersecurity
Rapid technological progress has made it possible for a wide range of industries, such as robotics, mechatronics, automation, and the automotive sector, to operate in a highly networked global environment. Although efficiency has increased significantly, these domains are now more vulnerable to growing cybersecurity threats [1][2][3][4][5]. The extensive usage of automation systems in the field of robotics has made them susceptible to cyber-attacks, which might endanger both human safety and valuable assets [6][7][8][9]. Comparably, industries across the board are now vulnerable to cybersecurity attacks due to the incorporation of software components in mechatronics, which combines electronics, software, and mechanics [10][11][12][13]. Automation in digital networks across several industries has increased the risk of cyber-attacks, which might have major operational and financial consequences [14][15][16][17]. The continuous shift in the automotive industry toward connected and automated vehicles has highlighted how important cybersecurity is for protecting user privacy and vehicle management systems. In digital technology-driven areas, cybersecurity essentially acts as the cornerstone for safeguarding against monetary losses and guaranteeing human welfare. This requirement also applies to car networking systems, where hackers may put human lives in danger. The automotive sector actively works with cybersecurity professionals to strengthen security measures. They concentrate on secure updates, customized communication protocols, and intrusion detection systems for vehicular networks. To sum up, cybersecurity plays a critical role in these many industries, acting as the foundation for guaranteeing safety and smooth functioning.
In modern vehicles, there are numerous electronic control units (ECUs) used for automation and comfort features, both of the driver and passengers [18]. Included in this class are ECUs on which advanced algorithms and features are integrated for cruise control, airbag control, temperature management, assisted parking, infotainment, etc. One of the problems for security in data exchange and enabling cybersecurity issues is related to the interconnections between the various ECUs [19]. The use of remote access points, including Wi-Fi, USB, Bluetooth, 4G/5G, and OBD-II interfaces, has increased dramatically in the automotive industry in recent years [20]. On the other hand, because of their widespread use, automotive networks are now more susceptible to outside attacks. These networks may be targeted by hostile parties who want to take over, change car systems, or steal confidential data. As a result, creating strong security systems that can identify and stop such breaches or assaults is imperative. In the automotive industry, one of the most often used protocols for intra-ECU communication is the Controller Area Network (CAN) bus. The numerous noteworthy characteristics of the CAN protocol include its ease of wiring, strict response times, high immunity to interference, error containment, and multi-master protocol capabilities [21]. The Carrier Sense Multiple Access/Bit-wise Arbitration (CSMA/BA) technique is used by the CAN system to control bus traffic. When two or more nodes initiate transmission simultaneously, an arbitration process based on ID prioritizing is commenced. But it is important to understand that the CAN bus protocol does not include a basic security mechanism, which leaves connected devices vulnerable to adversaries [22]. By taking advantage of weaknesses in the CAN bus protocol, aggressors can initiate various assaults that have the potential to impede vehicle functions. The lack of an authentication element in CAN frames creates this vulnerability, which allows any transmitting ECUs to mimic other ECUs. Additionally, the lack of content encryption in CAN frames gives adversaries a simple way to examine how target ECUs operate using CAN frame records from the past [23].
2. The State-of-the-Art on CAN Cybersecurity
There are several detection algorithms proposed in the literature to address the cybersecurity issues related to the Controller Area Network (CAN) protocol. Here is an overview of some of the state-of-the-art detection algorithms.
- (1)
- (2)
-
Intrusion Detection System (IDS): IDS is a popular security solution that uses crypto- graphic-based software to address CAN network security issues. The IDS ensures that the exchanged CAN data frame between the two end nodes is authorized. Researchers have proposed various IDS algorithms, such as a lightweight algorithm based on the observance of CAN packets frequencies, an anomaly-based detection method based on the time interval feature of the consecutive CAN packets, and a graph-based feature method that uses machine learning algorithms [29][30][31][32][33][34][35][36][37][38][39][40][41].
- (3)
-
CAN-ADF: The Controller Area Network Attack Detection Framework (CAN-ADF) is a framework that uses field classification, modeling, and anomaly detection to detect cyber-attacks on unknown CAN bus networks. The framework uses a holistic approach to detect cyber-attacks and provides a comprehensive solution to the cybersecurity issues related to the CAN protocol [42][43].
- (4)
-
Deep Learning Techniques: Intrusion Detection Systems (IDSs) using deep learning techniques are also proposed in the literature. These IDSs identify cyber-attacks when given a sample of network traffic collected from real-world computer networks. The IDSs using deep learning techniques are powerful and can detect cyber-attacks with high accuracy [44][45][46][47][48].
In summary, various detection algorithms have been proposed in the literature to address the cybersecurity issues related to the CAN protocol. These algorithms use different approaches, such as temporal-spatial analysis, cryptographic-based software, anomaly-based detection, graph-based feature methods, and deep learning techniques. The selection of the detection algorithm depends on the specific requirements of the application and the level of security needed.
Electronic Control Units (ECUs) are an essential component of the Controller Area Network (CAN) protocol used in the automotive industry. ECUs communicate with each other over the CAN bus protocol, which ensures high communication rates. However, the CAN protocol is prone to various cybersecurity attacks, and ECUs are vulnerable to these attacks. To address this issue, researchers have proposed ECU fingerprinting algorithms to detect and prevent cyber-attacks on the CAN bus. Here is an overview of some of the state-of-the-art ECU fingerprinting algorithms:
- (1)
-
Clock-based IDS (CIDS): CIDS is an anomaly-based intrusion detection system that measures and exploits the intervals of periodic in-vehicle messages for fingerprinting ECUs. The fingerprints are then used for constructing a baseline of the ECUs’ clock behaviors with the Recursive Least Squares (RLS) algorithm. Based on this baseline, CIDS uses Cumulative Sum (CUSUM) to detect any abnormal shifts in the identification of errors, which is a clear sign of intrusion [49][50][51][52][53][54][55].
- (2)
-
Physical-Fingerprinting of Electronic Control Unit (ECU) Based on Machine Learning Algorithm: This algorithm uses machine learning algorithms to identify the physical fingerprints of ECUs based on the time and frequency domain features of the consecutive CAN packets. The algorithm classifies the ECUs based on their physical fingerprints and detects any abnormal behavior [56][57][58][59][60][61][62][63].
- (3)
-
ECU Fingerprinting through Parametric Signal Modeling and Artificial Neural Networks: This algorithm uses parametric signal modeling and Artificial Neural Networks to identify the physical fingerprints of ECUs. The algorithm extracts the features of the CAN packets and uses them to train the Artificial Neural Network. The trained network is then used to classify the ECUs and to detect any abnormal behavior [64][65][66][67][68][69].
- (4)
-
Two-Point Voltage Fingerprinting: This algorithm uses voltage measurements to identify the physical fingerprints of ECUs. The algorithm measures the voltage at two points in the CAN bus and uses the difference between the two measurements to identify the ECU. The algorithm can detect any masquerading attacks on the CAN bus [70][71][72][73][74][75].
In summary, ECU fingerprinting algorithms are proposed to detect and to prevent cyber-attacks on the CAN bus. These algorithms use different approaches such as clock-based IDS, machine learning algorithms, parametric signal modeling, and Artificial Neural Networks. The selection of the ECU fingerprinting algorithm depends on the specific requirements of the application and the level of security needed.
3. CAN Protocol Basics
The Controller Area Network, commonly referred to as CAN bus, is a serial standard for field buses that is primarily employed in the automotive industry. It was introduced in the 1980s by Robert Bosch as a means to connect various electronic control units (ECUs). Notably, the CAN protocol offers a range of key advantages:
-
Simplicity of Wiring: The CAN bus operates on a message-oriented approach, rather than an address-oriented one. This design allows for the straightforward addition or removal of peripherals (nodes), simplifying the wiring process.
-
Rigid Response Times: CAN bus technology enables the creation of systems with highly predictable and rigid response times. This is achieved through specific techniques that are designed to minimize time-related delays.
-
High Immunity to Interference: The ISO 11898 standard mandates that the CAN protocol must maintain operability, even in scenarios where one of the two wires is severed, or if a bus line to the power supply experiences a short-circuit.
-
Error Confinement: Each peripheral device connected to the CAN bus possesses the capability to self-diagnose hardware issues. In the event of a malfunction, a peripheral can voluntarily remove itself from the bus, allowing other peripherals to continue using it.
-
Multi-Master Protocol: Within the CAN protocol, every node has the capacity to compete for control of the bus. This means that each node can assume the role of a master, taking control of the bus and initiating transmissions.
To manage traffic on the bus effectively, the CAN protocol employs the CSMA/BA (Carrier Sense Multiple Access/Bit-wise Arbitration) method. In situations where two or more nodes attempt to transmit simultaneously, an arbitration mechanism based on priority is applied.
4. Vulnerabilities and Attack Scenarios
It is brought to attention that the CAN bus, an essential communication protocol in various automotive systems, is deficient in fundamental security measures, rendering the wired units susceptible to potential breaches orchestrated by malevolent entities. According to the CIA (Confidentiality, Integrity, Availability) security model, a comprehensive examination reveals the existence of six critical vulnerabilities within the CAN bus framework. These vulnerabilities emerge from two distinct sources: the vulnerabilities concerning the traffic transmission through the CAN bus and those intrinsic to the protocol’s unique characteristics [76][77][78][79].
Among the pressing concerns, the absence of encryption, authentication, and integrity checking in the data transmission via the CAN bus represents a severe violation of the fundamental principles of data security, particularly confidentiality and integrity. Furthermore, the characteristics inherent in the CAN bus protocol, such as broadcast transmission, priority-based arbitration, and limited bandwidth, contribute to the system’s susceptibility to various security threats. The combination of these factors contributes to the heightened risk of a Denial-of-Service (DoS) attack, thus compromising the system’s availability. The specific vulnerabilities identified within the CAN bus context can be discerned as follows:
-
The broadcast transmission characteristic of the CAN bus, where the frames are disseminated to all interconnected ECUs, acts as a double-edged sword, facilitating system-wide communication, but also enabling unauthorized eavesdropping, which jeopardizes the confidentiality of the communication.
-
The priority-based arbitration, which allows frames with higher priority to dominate the communication channel, poses a significant security risk, as it enables an aggressive Electronic Control Unit (ECU) to manipulate the communication channel, potentially disrupting the entire network’s functioning [87][88][89].
-
The limited bandwidth and payload capacity of the CAN bus results in the insufficiency of robust access control mechanisms, creating a vulnerability that could be exploited by adversaries attempting to compromise the security of the system.
The collective presence of these vulnerabilities within the CAN bus infrastructure calls for urgent attention to fortify the security measures and to establish robust protocols to safeguard against potential breaches and malicious attacks that could compromise the integrity and functionality of the system.
- (1)
- (2)
- (3)
- (4)
- (5)
To address these vulnerabilities, various solutions have been proposed, such as intrusion detection systems, encryption, and authentication mechanisms. However, there is no optimal solution, and the problem is mitigated with network segmentation and intrusion detection systems. It is essential to establish a strong security system for automotive networks to maintain the advances in safe technologies and to advance the state of the art in automotive cybersecurity [118][119][120][121].
To monitor message flow from different ECUs, a modern CAN-based network can be accessed by peripherals like Bluetooth, Wi-Fi, and OBD. This makes it possible for IDs to be replicated, which can prevent some ECUs from communicating. Different vulnerabilities exist based on the hardware, software, and attack surfaces of the ECUs in the CAN network; the idea of Strong and Weak Attackers is explained. Fully and weakly compromised ECUs are the two categories of compromised ECUs that we distinguish. A weakly exploited ECU lacks the capacity to insert fake messages, and can stop some message transmissions or function in listen-only mode. On the other hand, an attacker with complete access to an ECU can take full control, access data stored in memory, and insert any attack message. Because the CAN bus protocol does not provide encryption, authentication, or integrity checking, it is vulnerable to a number of security issues. The system is unable to determine whether the data have been replayed by a malicious node, even in the event that cryptographic techniques are used.
Three are three main attack paths based on these weaknesses. Because integrity checking is not present, the impersonation attack can change CAN frames, and the replay attack can succeed if sufficient defenses are not taken.
-
Replay Attack for CAN: Without authentication and integrity for the CAN frames, a Strong Attack is able to launch the replay attack. As shown in Figure 1, a fully compromised ECU A transmits the CAN frames received from the ECU C, modifying its data field. As a result, the receiver ECU B will function abnormally under the replayed control information.
-
Impersonation Attack for CAN: Having known the IDs of the CAN frames from ECU B, the Strong Attack is able to launch the impersonation attack, as shown in Figure 2. The Weak Attacker first suspends the transmission of ECU B, and the strong attacker then controls ECU A to transmit the CAN frames using the ID of ECU B to manipulate the target, ECU C.
-
Injection Attack for CAN: As shown in Figure 3, a Strong Attacker ECU A is able to inject CAN frames with arbitrary IDs and content. On the one hand, the injected frames with the highest priority ID will always occupy the CAN bus. On the other hand, it can compromise the functionality of the bus occupying the transmission.
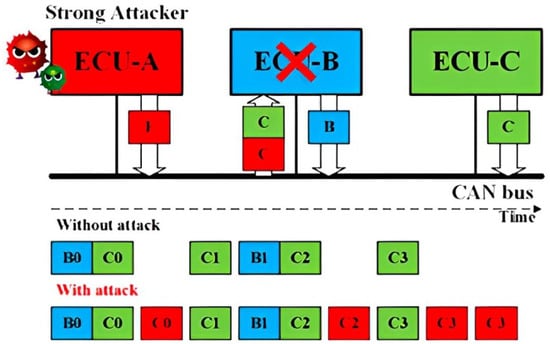
Figure 1. Schematic representation of the Replay attack concept.
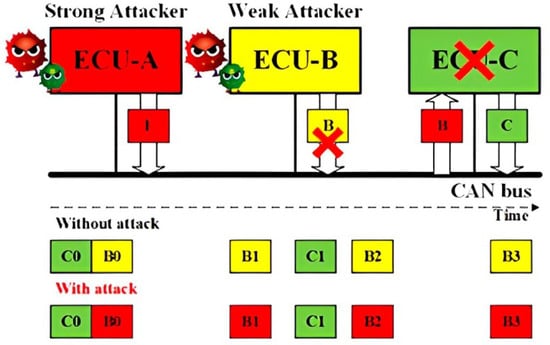
Figure 2. Schematic representation of the Impersonation attack concept.
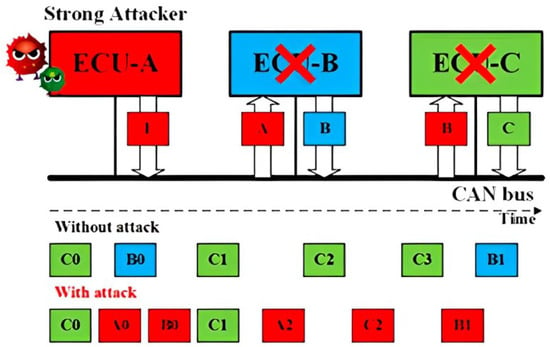
Figure 3. Schematic representation of the Injection attack concept.
References
- Rosadini, C.; Chiarelli, S.; Cornelio, A.; Nesci, W.; Saponara, S.; Dini, P.; Gagliardi, A. Method for Protection from Cyber Attacks to a Vehicle Based upon Time Analysis, and Corresponding Device. US Patent Application 18/163,488, April 2023.
- Rosadini, C.; Chiarelli, S.; Nesci, W.; Saponara, S.; Gagliardi, A.; Dini, P. Method for Protection from Cyber Attacks to a Vehicle Based Upon Time Analysis, and Corresponding Device. US Patent Application 17/929,370, November 2023.
- Dini, P.; Elhanashi, A.; Begni, A.; Saponara, S.; Zheng, Q.; Gasmi, K. Overview on Intrusion Detection Systems Design Exploiting Machine Learning for Networking Cybersecurity. Appl. Sci. 2023, 13, 7507.
- Elhanashi, A.; Gasmi, K.; Begni, A.; Dini, P.; Zheng, Q.; Saponara, S. Machine Learning Techniques for Anomaly-Based Detection System on CSE-CIC-IDS2018 Dataset. In Proceedings of the International Conference on Applications in Electronics Pervading Industry, Environment and Society, Genova, Italy, 26–27 September 2022; pp. 131–140.
- Dini, P.; Begni, A.; Ciavarella, S.; De Paoli, E.; Fiorelli, G.; Silvestro, C.; Saponara, S. Design and Testing Novel One-Class Classifier Based on Polynomial Interpolation with Application to Networking Security. IEEE Access 2022, 10, 67910–67924.
- Dini, P.; Saponara, S.; Colicelli, A. Overview on Battery Charging Systems for Electric Vehicles. Electronics 2023, 12, 4295.
- Pacini, F.; Di Matteo, S.; Dini, P.; Fanucci, L.; Bucchi, F. Innovative Plug-and-Play System for Electrification of Wheel-Chairs. IEEE Access 2023, 11, 89038–89051.
- Begni, A.; Dini, P.; Saponara, S. Design and Test of an LSTM-Based Algorithm for Li-Ion Batteries Remaining Useful Life Estimation. In Proceedings of the International Conference on Applications in Electronics Pervading Industry, Environment and Society, Genova, Italy, 26–27 September 2022; pp. 373–379.
- Dini, P.; Saponara, S.; Chakraborty, S.; Hosseinabadi, F.; Hegazy, O. Experimental Characterization & Electro-Thermal Modeling of Double Side Cooled SiC MOSFETs for Accurate and Rapid Power Converter Simulations. IEEE Access 2023, 11, 79120–79143.
- Bernardeschi, C.; Dini, P.; Domenici, A.; Palmieri, M.; Saponara, S. Do-it-Yourself FMU Generation. In Proceedings of the International Conference on Software Engineering and Formal Methods, Berlin, Germany, 26–30 September 2022; pp. 210–227.
- Pierpaolo, D.; Saponara, S. Control system design for cogging torque reduction based on sensor-less architecture. In Proceedings of the Applications in Electronics Pervading Industry, Environment and Society: APPLEPIES 2019 7, Pisa, Italy, 19–20 November 2020; pp. 309–321.
- Dini, P.; Saponara, S. Review on model based design of advanced control algorithms for cogging torque reduction in power drive systems. Energies 2022, 15, 8990.
- Dini, P.; Ariaudo, G.; Botto, G.; Greca, F.L.; Saponara, S. Real-time electro-thermal modelling & predictive control design of resonant power converter in full electric vehicle applications. IET Power Electron. 2023, 16, 2045–2064.
- Bernardeschi, C.; Dini, P.; Domenici, A.; Saponara, S. Co-simulation and Verification of a Non-linear Control System for Cogging Torque Reduction in Brushless Motors. In Proceedings of the Software Engineering and Formal Methods: SEFM 2019 Collocated Workshops: CoSim-CPS, ASYDE, CIFMA, and FOCLASA, Oslo, Norway, 16–20 September 2019; pp. 3–19.
- Bernardeschi, C.; Dini, P.; Domenici, A.; Mouhagir, A.; Palmieri, M.; Saponara, S.; Sassolas, T.; Zaourar, L. Co-simulation of a model predictive control system for automotive applications. In Proceedings of the International Conference on Software Engineering and Formal Methods, Online, 6–10 November 2023; pp. 204–220.
- Benedetti, D.; Agnelli, J.; Gagliardi, A.; Dini, P.; Saponara, S. Design of a Digital Dashboard on Low-Cost Embedded Platform in a Fully Electric Vehicle. In Proceedings of the 2020 IEEE International Conference on Environment and Electrical Engineering and 2020 IEEE Industrial and Commercial Power Systems Europe (EEEIC / ICPS Europe), Madrid, Spain, 9–12 June 2020; pp. 1–5.
- Cosimi, F.; Dini, P.; Giannetti, S.; Petrelli, M.; Saponara, S. Analysis and design of a non-linear MPC algorithm for vehicle trajectory tracking and obstacle avoidance. In Applications in Electronics Pervading Industry, Environment and Society: APPLEPIES 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 229–234.
- Miller, C.; Valasek, C. A survey of remote automotive attack surfaces. Black Hat USA 2014, 2014, 94.
- Wolf, M.; Weimerskirch, A.; Wollinger, T. State of the art: Embedding security in vehicles. EURASIP J. Embed. Syst. 2007, 2007, 74706.
- Miller, C.; Valasek, C. Remote exploitation of an unaltered passenger vehicle. Black Hat USA 2015, 2015, 1–91.
- Voss, W. Error Detection and Fault Confinement. A Comprehensible Guide to Controller Area Network, 2nd ed.; Copperhill Media Corporation: Greenfield, MA, USA, 2008; pp. 117–122.
- Zhang, H.; Meng, X.; Zhang, X.; Liu, Z. CANsec: A practical in-vehicle controller area network security evaluation tool. Sensors 2020, 20, 4900.
- Kleberger, P.; Olovsson, T.; Jonsson, E. Security aspects of the in-vehicle network in the connected car. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 528–533.
- Cui, X.; Liu, S.; Lin, Z.; Ma, J.; Wen, F.; Ding, Y.; Yang, L.; Guo, W.; Feng, X. Two-Step Electricity Theft Detection Strategy Considering Economic Return Based on Convolutional Autoencoder and Improved Regression Algorithm. IEEE Trans. Power Syst. 2022, 37, 2346–2359.
- Li, X.; Ma, J.; Zhao, X.; Wang, L. Intelligent Two-Step Estimation Approach for Vehicle Mass and Road Grade. IEEE Access 2020, 8, 218853–218862.
- Feng, Y.; Cao, Y.; Yang, S.; Yang, L.; Wei, T. A two-step sub-optimal algorithm for bus evacuation planning. Oper. Res. 2023, 23, 36.
- Liang, J.; Wu, J.; Gao, Z.; Sun, H.; Yang, X.; Lo, H.K. Bus transit network design with uncertainties on the basis of a metro network: A two-step model framework. Transp. Res. Part B Methodol. 2019, 126, 115–138.
- Lombardi, M.; Pascale, F.; Santaniello, D. Two-step algorithm to detect cyber-attack over the can-bus: A preliminary case study in connected vehicles. ASCE-ASME J. Risk Uncertain. Eng. Syst. Part B Mech. Eng. 2022, 8, 031105.
- Dong, C.; Wu, H.; Li, Q. Multiple Observation HMM-Based CAN Bus Intrusion Detection System for In-Vehicle Network. IEEE Access 2023, 11, 35639–35648.
- Bari, B.S.; Yelamarthi, K.; Ghafoor, S. Intrusion Detection in Vehicle Controller Area Network (CAN) Bus Using Machine Learning: A Comparative Performance Study. Sensors 2023, 23, 3610.
- Khan, J.; Lim, D.W.; Kim, Y.S. Intrusion Detection System CAN-Bus In-Vehicle Networks Based on the Statistical Characteristics of Attacks. Sensors 2023, 23, 3554.
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Madzudzo, G.; Petrovski, A.V. Keep the Moving Vehicle Secure: Context-Aware Intrusion Detection System for In-Vehicle CAN Bus Security. In Proceedings of the 2022 14th International Conference on Cyber Conflict: Keep Moving! (CyCon), Tallinn, Estonia, 31 May–3 June 2022; Volume 700, pp. 309–330.
- Jichici, C.; Groza, B.; Ragobete, R.; Murvay, P.S.; Andreica, T. Effective Intrusion Detection and Prevention for the Commercial Vehicle SAE J1939 CAN Bus. IEEE Trans. Intell. Transp. Syst. 2022, 23, 17425–17439.
- Alfardus, A.; Rawat, D.B. Intrusion Detection System for CAN Bus In-Vehicle Network based on Machine Learning Algorithms. In Proceedings of the 2021 IEEE 12th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 1–4 December 2021; pp. 0944–0949.
- Jin, S.; Chung, J.G.; Xu, Y. Signature-Based Intrusion Detection System (IDS) for In-Vehicle CAN Bus Network. In Proceedings of the 2021 IEEE International Symposium on Circuits and Systems (ISCAS), Daegu, Republic of Korea, 22–28 May 2021; pp. 1–5.
- Delwar Hossain, M.; Inoue, H.; Ochiai, H.; Fall, D.; Kadobayashi, Y. An Effective In-Vehicle CAN Bus Intrusion Detection System Using CNN Deep Learning Approach. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6.
- Hossain, M.D.; Inoue, H.; Ochiai, H.; Fall, D.; Kadobayashi, Y. LSTM-Based Intrusion Detection System for In-Vehicle Can Bus Communications. IEEE Access 2020, 8, 185489–185502.
- Hanselmann, M.; Strauss, T.; Dormann, K.; Ulmer, H. CANet: An Unsupervised Intrusion Detection System for High Dimensional CAN Bus Data. IEEE Access 2020, 8, 58194–58205.
- Casillo, M.; Coppola, S.; De Santo, M.; Pascale, F.; Santonicola, E. Embedded Intrusion Detection System for Detecting Attacks over CAN-BUS. In Proceedings of the 2019 4th International Conference on System Reliability and Safety (ICSRS), Rome, Italy, 20–22 November 2019; pp. 136–141.
- Abbott-McCune, S.; Shay, L.A. Intrusion prevention system of automotive network CAN bus. In Proceedings of the 2016 IEEE International Carnahan Conference on Security Technology (ICCST), Orlando, FL, USA, 24–27 October 2016; pp. 1–8.
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. An intrusion detection method for securing in-vehicle CAN bus. In Proceedings of the 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), Sousse, Tunisia, 19–21 December 2016; pp. 176–180.
- Wang, K.; Zhang, A.; Sun, H.; Wang, B. Analysis of Recent Deep-Learning-Based Intrusion Detection Methods for In-Vehicle Network. IEEE Trans. Intell. Transp. Syst. 2023, 24, 1843–1854.
- Tariq, S.; Lee, S.; Kim, H.K.; Woo, S.S. CAN-ADF: The controller area network attack detection framework. Comput. Secur. 2020, 94, 101857.
- Gundu, R.; Maleki, M. Securing CAN Bus in Connected and Autonomous Vehicles Using Supervised Machine Learning Approaches. In Proceedings of the 2022 IEEE International Conference on Electro Information Technology (eIT), Mankato, MN, USA, 19–21 May 2022; pp. 042–046.
- Salunkhe, S.S.; Pal, S.; Agrawal, A.; Rai, R.; Mole, S.S.; Jos, B.M. Energy optimization for CAN bus and media controls in electric vehicles using deep learning algorithms. J. Supercomput. 2022, 78, 8493–8508.
- Abdennour, N.; Ouni, T.; Amor, N.B. Driver identification using only the CAN-Bus vehicle data through an RCN deep learning approach. Robot. Auton. Syst. 2021, 136, 103707.
- Zhang, J.; Wu, Z.; Li, F.; Xie, C.; Ren, T.; Chen, J.; Liu, L. A deep learning framework for driving behavior identification on in-vehicle CAN-BUS sensor data. Sensors 2019, 19, 1356.
- Lin, Y.; Chen, C.; Xiao, F.; Avatefipour, O.; Alsubhi, K.; Yunianta, A. An Evolutionary Deep Learning Anomaly Detection Framework for In-Vehicle Networks-CAN Bus. IEEE Trans. Ind. Appl. 2020.
- Refat, R.U.D.; Elkhail, A.A.; Hafeez, A.; Malik, H. Detecting can bus intrusion by applying machine learning method to graph based features. In Intelligent Systems and Applications: Proceedings of the 2021 Intelligent Systems Conference (IntelliSys); Springer: Berlin/Heidelberg, Germany, 2022; Volume 3, pp. 730–748.
- Lee, S.; Choi, W.; Jo, H.J.; Lee, D.H. ErrIDS: An Enhanced Cumulative Timing Error-Based Automotive Intrusion Detection System. IEEE Trans. Intell. Transp. Syst. 2023, 24, 12406–12421.
- Lee, S.; Jo, H.J.; Cho, A.; Lee, D.H.; Choi, W. TTIDS: Transmission-Resuming Time-Based Intrusion Detection System for Controller Area Network (CAN). IEEE Access 2022, 10, 52139–52153.
- Zhao, Y.; Xun, Y.; Liu, J. ClockIDS: A Real-Time Vehicle Intrusion Detection System Based on Clock Skew. IEEE Internet Things J. 2022, 9, 15593–15606.
- Halder, S.; Conti, M.; Das, S.K. COIDS: A clock offset based intrusion detection system for controller area networks. In Proceedings of the 21st International Conference on Distributed Computing and Networking, Kolkata, India, 4–7 January 2020; pp. 1–10.
- Zhou, X.; Jiang, R.; Tian, M.; Qu, H.; Zhang, H. Temperature-sensitive fingerprinting on ECU clock offset for CAN intrusion detection and source identification. In Proceedings of the ACM Turing Celebration Conference, Hefei, China, 22–24 May 2020; pp. 89–94.
- Zhou, J.; Xie, G.; Yu, S.; Li, R. Clock-Based Sender Identification and Attack Detection for Automotive CAN Network. IEEE Access 2021, 9, 2665–2679.
- Hu, X.; Hu, A.; Yu, J.; Ding, Y.; Hu, H.; Guo, P. Anti-counterfeiting Method of CAN Terminal Based on Device Physical Fingerprint. In Proceedings of the 2023 3rd International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 6–8 January 2023; pp. 394–399.
- Murvay, P.S.; Berdich, A.; Groza, B. Physical Layer Intrusion Detection and Localization on CAN Bus. In Machine Learning and Optimization Techniques for Automotive Cyber-Physical Systems; Springer: Berlin/Heidelberg, Germany, 2023; pp. 399–423.
- Mohan, J. An Integrated Approach to Securing In-Vehicle CAN Bus Network Using ECU Fingerprinting and Image Classification Techniques. Ph.D. Thesis, University of Michigan, Ann Arbor, MI, USA, 2023.
- Popa, L.; Groza, B.; Jichici, C.; Murvay, P.S. ECUPrint—Physical Fingerprinting Electronic Control Units on CAN Buses Inside Cars and SAE J1939 Compliant Vehicles. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1185–1200.
- Hafeez, A.; Rehman, K.; Malik, H. State of the Art Survey on Comparison of Physical Fingerprinting-Based Intrusion Detection Techniques for In-Vehicle Security; Technical Report, SAE Technical Paper; SAE: Warrendale, PA, USA, 2020.
- Tayyab, M. Authenticating the Sender on CAN Bus Using Inimitable Physical Characteristics of the Transmitter and Channel. Ph.D. Thesis, University of Michigan, Ann Arbor, MI, USA, 2018.
- Avatefipour, O. Physical-Fingerprinting of Electronic Control Unit (ECU) Based on Machine Learning Algorithm for In-Vehicle Network Communication Protocol CAN-BUS. Ph.D. Thesis, University of Michigan, Ann Arbor, MI, USA, 2017.
- Avatefipour, O.; Hafeez, A.; Tayyab, M.; Malik, H. Linking received packet to the transmitter through physical-fingerprinting of controller area network. In Proceedings of the 2017 IEEE Workshop on Information Forensics and Security (WIFS), Rennes, France, 4–7 December 2017; pp. 1–6.
- Fang, W.; Yu, J.; Ding, Y.; Hu, X.; Li, S.; Hu, A. Research on Terminal Fingerprint Extraction and Temperature Adaptability Based on CAN Bus. In Proceedings of the 2022 IEEE 22nd International Conference on Communication Technology (ICCT), Nanjing, China, 11–14 November 2022; pp. 1506–1511.
- Verma, K.; Girdhar, M.; Hafeez, A.; Awad, S.S. ECU Identification using Neural Network Classification and Hyperparameter Tuning. In Proceedings of the 2022 IEEE International Workshop on Information Forensics and Security (WIFS), Virtual, 12–16 December 2022; pp. 1–6.
- Hafeez, A.; Mohan, J.; Girdhar, M.; Awad, S.S. Machine Learning based ECU Detection for Automotive Security. In Proceedings of the 2021 17th International Computer Engineering Conference (ICENCO), Giza, Egypt, 29–30 December 2021; pp. 73–81.
- Fugiglando, U.; Massaro, E.; Santi, P.; Milardo, S.; Abida, K.; Stahlmann, R.; Netter, F.; Ratti, C. Driving Behavior Analysis through CAN Bus Data in an Uncontrolled Environment. IEEE Trans. Intell. Transp. Syst. 2019, 20, 737–748.
- Prodanov, W.; Valle, M.; Buzas, R. A Controller Area Network Bus Transceiver Behavioral Model for Network Design and Simulation. IEEE Trans. Ind. Electron. 2009, 56, 3762–3771.
- Hafeez, A.; Topolovec, K.; Awad, S. ECU Fingerprinting through Parametric Signal Modeling and Artificial Neural Networks for In-vehicle Security against Spoofing Attacks. In Proceedings of the 2019 15th International Computer Engineering Conference (ICENCO), Cairo, Egypt, 29–30 December 2019; pp. 29–38.
- Cappelli, I.; Carli, F.; Fort, A.; Intravaia, M.; Micheletti, F.; Peruzzi, G.; Vignoli, V. Enhanced Visible Light Localization Based on Machine Learning and Optimized Fingerprinting in Wireless Sensor Networks. IEEE Trans. Instrum. Meas. 2023, 72, 9503410.
- Thakur, S.; Moreno, C.; Fischmeister, S. CANOA: CAN Origin Authentication through Power Side-Channel Monitoring. ACM Trans. Cyber Phys. Syst. 2022.
- Ahmed, S.; Juliato, M.; Gutierrez, C.; Sastry, M. Two-point voltage fingerprinting: Increasing detectability of ecu masquerading attacks. arXiv 2021, arXiv:2102.10128.
- Lesi, V.; Juliato, M.; Ahmed, S.; Gutierrez, C.; Wang, Q.; Sastry, M. Intrusion Detection and Localization for Networked Embedded Control Systems. arXiv 2021, arXiv:2106.09826.
- Wang, Q.; Qian, Y.; Lu, Z.; Shoukry, Y.; Qu, G. A Delay based Plug-in-Monitor for Intrusion Detection in Controller Area Network. In Proceedings of the 2018 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Hong Kong, China, 17–18 December 2018; pp. 86–91.
- Li, J.; Zhang, M.; Lai, Y. A Light-Weighted Machine Learning Based ECU Identification for Automative CAN Security; Technical Report; EasyChair: Manchester, UK, 2023.
- Khalaf, R.H.; Mohammed, A.H. Confidentiality and integrity of sensing data transmission in iot application. Int. J. Eng. Technol. 2018, 7, 240–245.
- Tchernykh, A.; Schwiegelsohn, U.; Talbi, E.g.; Babenko, M. Towards understanding uncertainty in cloud computing with risks of confidentiality, integrity, and availability. J. Comput. Sci. 2019, 36, 100581.
- Aminzade, M. Confidentiality, integrity and availability-finding a balanced IT framework. Netw. Secur. 2018, 2018, 9–11.
- Samonas, S.; Coss, D. The CIA strikes back: Redefining confidentiality, integrity and availability in security. J. Inf. Syst. Secur. 2014, 10. Available online: https://api.semanticscholar.org/CorpusID:215838643 (accessed on 13 November 2023).
- Jukl, M.; Čupera, J. Using of tiny encryption algorithm in CAN-Bus communication. Res. Agric. Eng. 2016, 62, 50–55.
- Farag, W.A. CANTrack: Enhancing automotive CAN bus security using intuitive encryption algorithms. In Proceedings of the 2017 7th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Sharjah, United Arab Emirates, 4–6 April 2017; pp. 1–5.
- Luo, J.N.; Wu, C.M.; Yang, M.H. A can-bus lightweight authentication scheme. Sensors 2021, 21, 7069.
- Nürnberger, S.; Rossow, C. –vatican–vetted, authenticated can bus. In Proceedings of the Cryptographic Hardware and Embedded Systems—CHES 2016: 18th International Conference, Santa Barbara, CA, USA, 17–19 August 2016; pp. 106–124.
- Van Herrewege, A.; Singelee, D.; Verbauwhede, I. CANAuth-a simple, backward compatible broadcast authentication protocol for CAN bus. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography. ECRYPT, Nara, Japan, 28 September–1 October 2011; Volume 2011, p. 20.
- Páez, F.; Kaschel, H. A Proposal for Data Authentication, Data Integrity and Replay Attack Rejection for the LIN Bus. In Proceedings of the 2021 IEEE CHILEAN Conference on Electrical, Electronics Engineering, Information and Communication Technologies (CHILECON), Online, 6–9 December 2021; pp. 1–7.
- Dee, T.; Tyagi, A. Message Integrity and Authenticity in Secure CAN. IEEE Consum. Electron. Mag. 2021, 10, 33–40.
- Thodi, B.T.; Chilukuri, B.R.; Vanajakshi, L. An analytical approach to real-time bus signal priority system for isolated intersections. J. Intell. Transp. Syst. 2022, 26, 145–167.
- Long, K.; Wei, J.; Gu, J.; Yang, X. Headway-Based Multi-Route Transit Signal Priority at Isolated Intersection. IEEE Access 2020, 8, 187824–187831.
- Wang, S.; Farjam, T.; Charalambous, T. A Priority-Based Distributed Channel Access Mechanism for Control over CAN-like Networks. In Proceedings of the 2021 European Control Conference (ECC), Delft, The Netherlands, 29 June–2 July 2021; pp. 176–182.
- Maithili, K.; Vinothkumar, V.; Latha, P. Analyzing the security mechanisms to prevent unauthorized access in cloud and network security. J. Comput. Theor. Nanosci. 2018, 15, 2059–2063.
- Muslukhov, I.; Boshmaf, Y.; Kuo, C.; Lester, J.; Beznosov, K. Know your enemy: The risk of unauthorized access in smartphones by insiders. In Proceedings of the 15th International Conference on Human-Computer Interaction with Mobile Devices and Services, Munich, Germany, 27–30 August 2013; pp. 271–280.
- AbdAllah, E.G.; Zulkernine, M.; Hassanein, H.S. Preventing unauthorized access in information centric networking. Secur. Priv. 2018, 1, e33.
- Kitova, E.T.; Gorlov, N.I.; Bogachkov, I.V. Unauthorized Access Monitoring in Optical Access Networks. In Proceedings of the 2020 Systems of Signal Synchronization, Generating and Processing in Telecommunications (SYNCHROINFO), Svetlogorsk, Russia, 1–3 July 2020; pp. 1–4.
- Shi, J.; Li, R.; Hou, W. A Mechanism to Resolve the Unauthorized Access Vulnerability Caused by Permission Delegation in Blockchain-Based Access Control. IEEE Access 2020, 8, 156027–156042.
- Razaque, A.; Shaldanbayeva, N.; Alotaibi, B.; Alotaibi, M.; Murat, A.; Alotaibi, A. Big data handling approach for unauthorized cloud computing access. Electronics 2022, 11, 137.
- Aljabri, M.; Alahmadi, A.A.; Mohammad, R.M.A.; Alhaidari, F.; Aboulnour, M.; Alomari, D.M.; Mirza, S. Machine Learning-Based Detection for Unauthorized Access to IoT Devices. J. Sens. Actuator Netw. 2023, 12, 27.
- Chandrasekaran, S.; Ramachandran, K.; Adarsh, S.; Puranik, A.K. Avoidance of Replay attack in CAN protocol using Authenticated Encryption. In Proceedings of the 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 1–3 July 2020; pp. 1–6.
- Xue, H.; Yang, Y.; Liu, J.; Xu, Z.; Dankanti, K.A. Reverse fast replay attack tunnel lighting system based on CAN bus. In Proceedings of the Second International Conference on Electronic Information Engineering, Big Data, and Computer Technology (EIBDCT 2023), Xishuangbanna, China, 6–8 January 2023; Volume 12642, pp. 82–87.
- Ansari, M.R.; Miller, W.T.; She, C.; Yu, Q. A low-cost masquerade and replay attack detection method for CAN in automotive vehicles. In Proceedings of the 2017 IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017; pp. 1–4.
- Rasheed, A.; Baza, M.; Badr, M.; Alshahrani, H.; Choo, K.K.R. Efficient Crypto Engine for Authenticated Encryption, Data Traceability, and Replay Attack Detection over CAN Bus Network. IEEE Trans. Netw. Sci. Eng. 2023, 1–17.
- Thirumavalavasethurayar, P.; Ravi, T. Implementation of Replay Attack in Controller Area Network Bus using Universal Verification Methodology. In Proceedings of the 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS), Coimbatore, India, 25–27 March 2021; pp. 1142–1146.
- Humayed, A.; Li, F.; Lin, J.; Luo, B. Cansentry: Securing can-based cyber-physical systems against denial and spoofing attacks. In Proceedings of the Computer Security—ESORICS 2020: 25th European Symposium on Research in Computer Security, ESORICS 2020, Guildford, UK, 14–18 September 2020; pp. 153–173.
- Amato, F.; Coppolino, L.; Mercaldo, F.; Moscato, F.; Nardone, R.; Santone, A. CAN-Bus Attack Detection with Deep Learning. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5081–5090.
- Cros, O.; Chênevert, G. Hashing-based authentication for CAN bus and application to Denial-of-Service protection. In Proceedings of the 2019 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, 23–25 October 2019; pp. 91–98.
- Palanca, A.; Evenchick, E.; Maggi, F.; Zanero, S. A stealth, selective, link-layer denial-of-service attack against automotive networks. In Proceedings of the Detection of Intrusions and Malware, and Vulnerability Assessment: 14th International Conference, DIMVA 2017, Bonn, Germany, 6–7 July 2017; pp. 185–206.
- Bozdal, M.; Randa, M.; Samie, M.; Jennions, I. Hardware trojan enabled denial of service attack on can bus. Procedia Manuf. 2018, 16, 47–52.
- Levy, E.; Shabtai, A.; Groza, B.; Murvay, P.S.; Elovici, Y. CAN-LOC: Spoofing Detection and Physical Intrusion Localization on an In-Vehicle CAN Bus Based on Deep Features of Voltage Signals. IEEE Trans. Inf. Forensics Secur. 2023, 18, 4800–4814.
- Lalouani, W.; Dang, Y.; Younis, M. Mitigating voltage fingerprint spoofing attacks on the controller area network bus. Clust. Comput. 2023, 26, 1447–1460.
- Dagan, T.; Wool, A. Parrot, a software-only anti-spoofing defense system for the CAN bus. ESCAR Eur. 2016, 34.
- Yang, Y.; Duan, Z.; Tehranipoor, M. Identify a spoofing attack on an in-vehicle CAN bus based on the deep features of an ECU fingerprint signal. Smart Cities 2020, 3, 17–30.
- Iehira, K.; Inoue, H.; Ishida, K. Spoofing attack using bus-off attacks against a specific ECU of the CAN bus. In Proceedings of the 2018 15th IEEE Annual Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 12–15 January 2018; pp. 1–4.
- Ruotsalainen, H.; Shen, G.; Zhang, J.; Fujdiak, R. LoRaWAN Physical Layer-Based Attacks and Countermeasures, a Review. Sensors 2022, 22, 3127.
- Givehchian, H.; Bhaskar, N.; Herrera, E.R.; Soto, H.R.L.; Dameff, C.; Bharadia, D.; Schulman, A. Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 23–25 May 2022; pp. 1690–1704.
- Nooraiepour, A.; Bajwa, W.U.; Mandayam, N.B. Learning-Aided Physical Layer Attacks against Multicarrier Communications in IoT. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 239–254.
- Huang, S.; Lin, C.; Zhou, K.; Yao, Y.; Lu, H.; Zhu, F. Identifying physical-layer attacks for IoT security: An automatic modulation classification approach using multi-module fusion neural network. Phys. Commun. 2020, 43, 101180.
- Salahdine, F.; Kaabouch, N. Security threats, detection, and countermeasures for physical layer in cognitive radio networks: A survey. Phys. Commun. 2020, 39, 101001.
- Mohammed, A.Z.; Man, Y.; Gerdes, R.; Li, M.; Celik, Z.B. Physical layer data manipulation attacks on the can bus. In Proceedings of the International Workshop on Automotive and Autonomous Vehicle Security (AutoSec), San Diego, CA, USA, 24 April 2022.
- Oladimeji, D.; Rasheed, A.; Varol, C.; Baza, M.; Alshahrani, H.; Baz, A. CANAttack: Assessing Vulnerabilities within Controller Area Network. Sensors 2023, 23, 8223.
- Bozdal, M.; Samie, M.; Aslam, S.; Jennions, I. Evaluation of can bus security challenges. Sensors 2020, 20, 2364.
- Bozdal, M.; Samie, M.; Jennions, I. A survey on can bus protocol: Attacks, challenges, and potential solutions. In Proceedings of the 2018 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 201–205.
- Lokman, S.F.; Othman, A.T.; Abu-Bakar, M.H. Intrusion detection system for automotive Controller Area Network (CAN) bus system: A review. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 184.
More
Information
Subjects:
Automation & Control Systems
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.4K
Revisions:
2 times
(View History)
Update Date:
27 Nov 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




