Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Pierpaolo Dini and Version 2 by Lindsay Dong.
The Controller Area Network, commonly referred to as Controller Area Network (CAN)N bus, is a serial standard for field buses that is primarily employed in the automotive industry. It was introduced in the 1980s by Robert Bosch as a means to connect various electronic control units (ECUs).
- Controller Area Network (CAN)
- Cybersecurity
- numerous electronic control units (ECUs)
1. Motivations for Controller Area Network (CAN) Cybersecurity
1. Motivations for CAN Cybersecurity
Rapid technological progress has made it possible for a wide range of industries, such as robotics, mechatronics, automation, and the automotive sector, to operate in a highly networked global environment. Although efficiency has increased significantly, these domains are now more vulnerable to growing cybersecurity threats [1][2][3][4][5][1,2,3,4,5]. The extensive usage of automation systems in the field of robotics has made them susceptible to cyber-attacks, which might endanger both human safety and valuable assets [6][7][8][9][6,7,8,9]. Comparably, industries across the board are now vulnerable to cybersecurity attacks due to the incorporation of software components in mechatronics, which combines electronics, software, and mechanics [10][11][12][13][10,11,12,13]. Automation in digital networks across several industries has increased the risk of cyber-attacks, which might have major operational and financial consequences [14][15][16][17][14,15,16,17]. The continuous shift in the automotive industry toward connected and automated vehicles has highlighted how important cybersecurity is for protecting user privacy and vehicle management systems. In digital technology-driven areas, cybersecurity essentially acts as the cornerstone for safeguarding against monetary losses and guaranteeing human welfare. This requirement also applies to car networking systems, where hackers may put human lives in danger. The automotive sector actively works with cybersecurity professionals to strengthen security measures. They concentrate on secure updates, customized communication protocols, and intrusion detection systems for vehicular networks. To sum up, cybersecurity plays a critical role in these many industries, acting as the foundation for guaranteeing safety and smooth functioning.
In modern vehicles, there are numerous electronic control units (ECUs) used for automation and comfort features, both of the driver and passengers [18]. Included in this class are ECUs on which advanced algorithms and features are integrated for cruise control, airbag control, temperature management, assisted parking, infotainment, etc. One of the problems for security in data exchange and enabling cybersecurity issues is related to the interconnections between the various ECUs [19]. The use of remote access points, including Wi-Fi, USB, Bluetooth, 4G/5G, and OBD-II interfaces, has increased dramatically in the automotive industry in recent years [20]. On the other hand, because of their widespread use, automotive networks are now more susceptible to outside attacks. These networks may be targeted by hostile parties who want to take over, change car systems, or steal confidential data. As a result, creating strong security systems that can identify and stop such breaches or assaults is imperative. In the automotive industry, one of the most often used protocols for intra-ECU communication is the Controller Area Network (CAN) bus. The numerous noteworthy characteristics of the CAN protocol include its ease of wiring, strict response times, high immunity to interference, error containment, and multi-master protocol capabilities [21]. The Carrier Sense Multiple Access/Bit-wise Arbitration (CSMA/BA) technique is used by the CAN system to control bus traffic. When two or more nodes initiate transmission simultaneously, an arbitration process based on ID prioritizing is commenced. But it is important to understand that the CAN bus protocol does not include a basic security mechanism, which leaves connected devices vulnerable to adversaries [22]. By taking advantage of weaknesses in the CAN bus protocol, aggressors can initiate various assaults that have the potential to impede vehicle functions. The lack of an authentication element in CAN frames creates this vulnerability, which allows any transmitting ECUs to mimic other ECUs. Additionally, the lack of content encryption in CAN frames gives adversaries a simple way to examine how target ECUs operate using CAN frame records from the past [23].
2. The State-of-the-Art on CAN Cybersecurity
There are several detection algorithms proposed in the literature to address the cybersecurity issues related to the Controller Area Network (CAN) protocol. Here is an overview of some of the state-of-the-art detection algorithms.- (1)
-
Two-Step Algorithm: This algorithm uses a mixed approach of temporal-spatial analysis to detect cyber-attacks over the CAN bus. The algorithm first detects the abnormal behavior of the CAN bus and then identifies the source of the attack [24][25][26][27][28][25,26,27,28,29].
- (2)
-
Intrusion Detection System (IDS): IDS is a popular security solution that uses crypto- graphic-based software to address CAN network security issues. The IDS ensures that the exchanged CAN data frame between the two end nodes is authorized. Researchers have proposed various IDS algorithms, such as a lightweight algorithm based on the observance of CAN packets frequencies, an anomaly-based detection method based on the time interval feature of the consecutive CAN packets, and a graph-based feature method that uses machine learning algorithms [29][30][31][32][33][34][35][36][37][38][39][40][41][30,31,32,33,34,35,36,37,38,39,40,41,42].
- (3)
-
CAN-ADF: The Controller Area Network Attack Detection Framework (CAN-ADF) is a framework that uses field classification, modeling, and anomaly detection to detect cyber-attacks on unknown CAN bus networks. The framework uses a holistic approach to detect cyber-attacks and provides a comprehensive solution to the cybersecurity issues related to the CAN protocol [42][43][43,44].
- (4)
-
Deep Learning Techniques: Intrusion Detection Systems (IDSs) using deep learning techniques are also proposed in the literature. These IDSs identify cyber-attacks when given a sample of network traffic collected from real-world computer networks. The IDSs using deep learning techniques are powerful and can detect cyber-attacks with high accuracy [44][45][46][47][48][45,46,47,48,49].
- (1)
-
Clock-based IDS (CIDS): CIDS is an anomaly-based intrusion detection system that measures and exploits the intervals of periodic in-vehicle messages for fingerprinting ECUs. The fingerprints are then used for constructing a baseline of the ECUs’ clock behaviors with the Recursive Least Squares (RLS) algorithm. Based on this baseline, CIDS uses Cumulative Sum (CUSUM) to detect any abnormal shifts in the identification of errors, which is a clear sign of intrusion [49][50][51][52][53][54][55][50,51,52,53,54,55,56].
- (2)
-
Physical-Fingerprinting of Electronic Control Unit (ECU) Based on Machine Learning Algorithm: This algorithm uses machine learning algorithms to identify the physical fingerprints of ECUs based on the time and frequency domain features of the consecutive CAN packets. The algorithm classifies the ECUs based on their physical fingerprints and detects any abnormal behavior [56][57][58][59][60][61][62][63][57,58,59,60,61,62,63,64].
- (3)
-
ECU Fingerprinting through Parametric Signal Modeling and Artificial Neural Networks: This algorithm uses parametric signal modeling and Artificial Neural Networks to identify the physical fingerprints of ECUs. The algorithm extracts the features of the CAN packets and uses them to train the Artificial Neural Network. The trained network is then used to classify the ECUs and to detect any abnormal behavior [64][65][66][67][68][69][65,66,67,68,69,70].
- (4)
-
Two-Point Voltage Fingerprinting: This algorithm uses voltage measurements to identify the physical fingerprints of ECUs. The algorithm measures the voltage at two points in the CAN bus and uses the difference between the two measurements to identify the ECU. The algorithm can detect any masquerading attacks on the CAN bus [70][71][72][73][74][75][71,72,73,74,75,76].
3. CAN Protocol Basics
The Controller Area Network, commonly referred to as CAN bus, is a serial standard for field buses that is primarily employed in the automotive industry. It was introduced in the 1980s by Robert Bosch as a means to connect various electronic control units (ECUs). Notably, the CAN protocol offers a range of key advantages:-
Simplicity of Wiring: The CAN bus operates on a message-oriented approach, rather than an address-oriented one. This design allows for the straightforward addition or removal of peripherals (nodes), simplifying the wiring process.
-
Rigid Response Times: CAN bus technology enables the creation of systems with highly predictable and rigid response times. This is achieved through specific techniques that are designed to minimize time-related delays.
-
High Immunity to Interference: The ISO 11898 standard mandates that the CAN protocol must maintain operability, even in scenarios where one of the two wires is severed, or if a bus line to the power supply experiences a short-circuit.
-
Error Confinement: Each peripheral device connected to the CAN bus possesses the capability to self-diagnose hardware issues. In the event of a malfunction, a peripheral can voluntarily remove itself from the bus, allowing other peripherals to continue using it.
-
Multi-Master Protocol: Within the CAN protocol, every node has the capacity to compete for control of the bus. This means that each node can assume the role of a master, taking control of the bus and initiating transmissions.
4. Vulnerabilities and Attack Scenarios
It is brought to attention that the CAN bus, an essential communication protocol in various automotive systems, is deficient in fundamental security measures, rendering the wired units susceptible to potential breaches orchestrated by malevolent entities. According to the CIA (Confidentiality, Integrity, Availability) security model, a comprehensive examination reveals the existence of six critical vulnerabilities within the CAN bus framework. These vulnerabilities emerge from two distinct sources: the vulnerabilities concerning the traffic transmission through the CAN bus and those intrinsic to the protocol’s unique characteristics [76][77][78][-
The broadcast transmission characteristic of the CAN bus, where the frames are disseminated to all interconnected ECUs, acts as a double-edged sword, facilitating system-wide communication, but also enabling unauthorized eavesdropping, which jeopardizes the confidentiality of the communication.
-
The priority-based arbitration, which allows frames with higher priority to dominate the communication channel, poses a significant security risk, as it enables an aggressive Electronic Control Unit (ECU) to manipulate the communication channel, potentially disrupting the entire network’s functioning [87][88][89][88,89,90].
-
The limited bandwidth and payload capacity of the CAN bus results in the insufficiency of robust access control mechanisms, creating a vulnerability that could be exploited by adversaries attempting to compromise the security of the system.
- (1)
-
Unauthorized access: Since the network is centralized, nodes trust each other, and a malicious node that is attached to the network can have access to all the data flowing and can disrupt the data flow [90][91][92][93][94][95][96][91,92,93,94,95,96,97].
- (2)
-
Replay attacks: An attacker intercepts and records a message, and then replays it later to achieve a malicious goal [97][98][99][100][101][98,99,100,101,102].
- (3)
-
Denial of Service (DoS) attacks: An attacker can flood the network with messages, causing the network to become unresponsive [102][103][104][105][106][103,104,105,106,107].
- (4)
-
Spoofing attacks: An attacker can send messages with a fake source address, making it difficult to identify the source of the attack [107][108][109][110][111][108,109,110,111,112].
- (5)
-
Physical layer attacks: An attacker can manipulate the physical layer of the CAN bus to cause malfunctions in CAN nodes [112][113][114][115][116][117][113,114,115,116,117,118].
-
Replay Attack for CAN: Without authentication and integrity for the CAN frames, a Strong Attack is able to launch the replay attack. As shown in Figure 1, a fully compromised ECU A transmits the CAN frames received from the ECU C, modifying its data field. As a result, the receiver ECU B will function abnormally under the replayed control information.
-
Impersonation Attack for CAN: Having known the IDs of the CAN frames from ECU B, the Strong Attack is able to launch the impersonation attack, as shown in Figure 2. The Weak Attacker first suspends the transmission of ECU B, and the strong attacker then controls ECU A to transmit the CAN frames using the ID of ECU B to manipulate the target, ECU C.
-
Injection Attack for CAN: As shown in Figure 3, a Strong Attacker ECU A is able to inject CAN frames with arbitrary IDs and content. On the one hand, the injected frames with the highest priority ID will always occupy the CAN bus. On the other hand, it can compromise the functionality of the bus occupying the transmission.
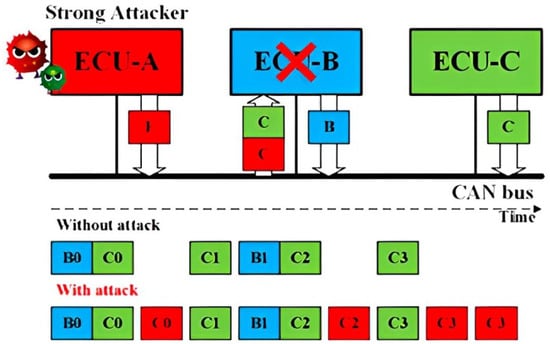 Figure 1.Schematic representation of the Replay attack concept.
Figure 1.Schematic representation of the Replay attack concept.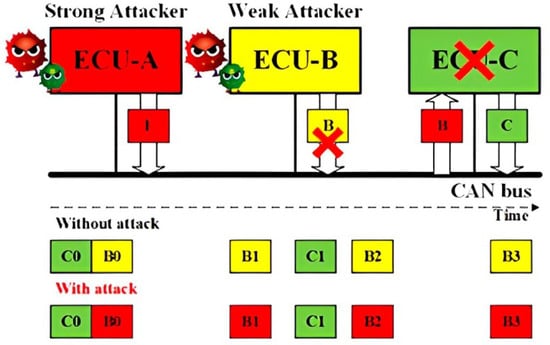 Figure 2.Schematic representation of the Impersonation attack concept.
Figure 2.Schematic representation of the Impersonation attack concept.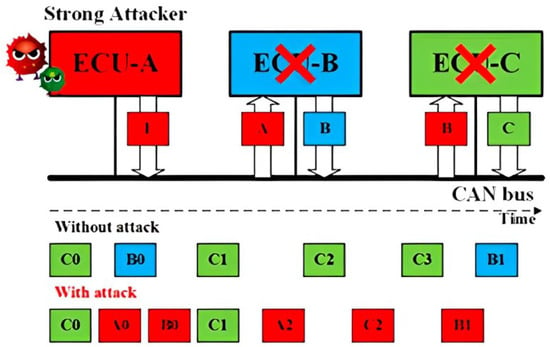 Figure 3.Schematic representation of the Injection attack concept.
Figure 3.Schematic representation of the Injection attack concept.
