1. Battery Energy Storage System Cybersecurity
The operation of bidirectional electric vehicle supply equipment (EVSEs) with Vehicle-to-Grid (V2G) capability (also referred to as smart charging equipment
[1]) should usually be scheduled and coordinated through effective communication channels between different stakeholders, including the electric vehicle (EV) owners, charge station operators, and grid operators
[2]. V2G offers several advantages through different ancillary services such as peak shaving, demand side management, voltage/frequency stability support, reactive power compensation
[1], etc. However, V2G has some challenging security issues
[1]. The sum effect of charge stations can have great impacts on the grid, and cyberattacks against them can endanger the operation and stability of the grid. Compared to low-power EVSEs, the cyberattack impacts on the grid are more important in the case of high-power fast-charging EVSEs
[3]. Several studies have thus analyzed the cybersecurity of charging stations
[4][5]. The authors of
[2] analyzed the impact of the false data injection (FDI) attack falsifying the charge station power request, which resulted in a violation of the peak power constraint and accordingly caused financial penalties and triggered technical problems in the upstream grid
[2]. In
[6], the cybersecurity of wireless power transfer modules (WPTMs) for EV fast charging was discussed. Cyberattacks against charging station controllers were analyzed and it was accordingly concluded that the attacks can disrupt the operation or cause failures in the physical chargers such as the occurrence of short-circuits. In
[4], the vulnerability of the CHAdeMO charge protocol which also has bidirectional energy transfer capability was highlighted. Despite ensuring safety, CHAdeMO does not offer secure communications, which means the messages are not encrypted when the charger is connected to the CAN bus and BMS. The cybersecurity of EVSEs was also explored in
[7][8], which discovered some cybersecurity vulnerabilities of EVSEs, e.g., vulnerability of combined charging system (CCS) charge protocol to electromagnetic side-channel attacks. Nevertheless, CCS has generally higher security compared to CHAdeMO, e.g., it requires the specification of digital certificates to authenticate different devices or transport layer security (TLS)-based encryption, as per ISO 15118
[9]. With CCS, automated authentication and authorization can also be fulfilled through plug and charge (PnC) services
[4]. A comparison of different charging protocols and their security features was presented in
[4]. The impact of integrity attacks on the power electronics components of EV onboard chargers (OBCs) was examined in
[10]. As discussed, such attacks can undesirably influence the FPGA controllers of the OBCs, establish fake messages from OBC to other vehicle ECUs listening to the CAN bus, and interfere with the functionalities of the BMS. Potential attack points can be interfaces of the CAN bus for BMS and OBCs, interfaces of EVSE, V2G interfaces, and IoT interfaces with the vehicle and CBMS
[10].
The cybersecurity of large-scale stationary BESSs for grid applications such as voltage/frequency regulation, black start, etc., has partly been discussed in the literature
[11]. In
[12], published by Sandia National Laboratories, detailed discussions related to the physical security and cybersecurity of stationary BESSs were provided, where it was argued that security should be considered as a design factor in the battery and BMS early development cycles (otherwise it becomes a costly and less effective solution to add at later stages). Some studies have also been fulfilled on other aspects of vehicle cybersecurity, such as cybersecurity in autonomous cars
[13].
In the following, the classification of different attack types/scenarios, potential impacts, and possible countermeasures are presented and discussed.
2. Attack Types and Scenarios
The CBMS is a CPS, and IoT plays the main role in connecting the physical and virtual parts. Thus, many of the IoT security threats and requirements can be applied to CBMSs as well
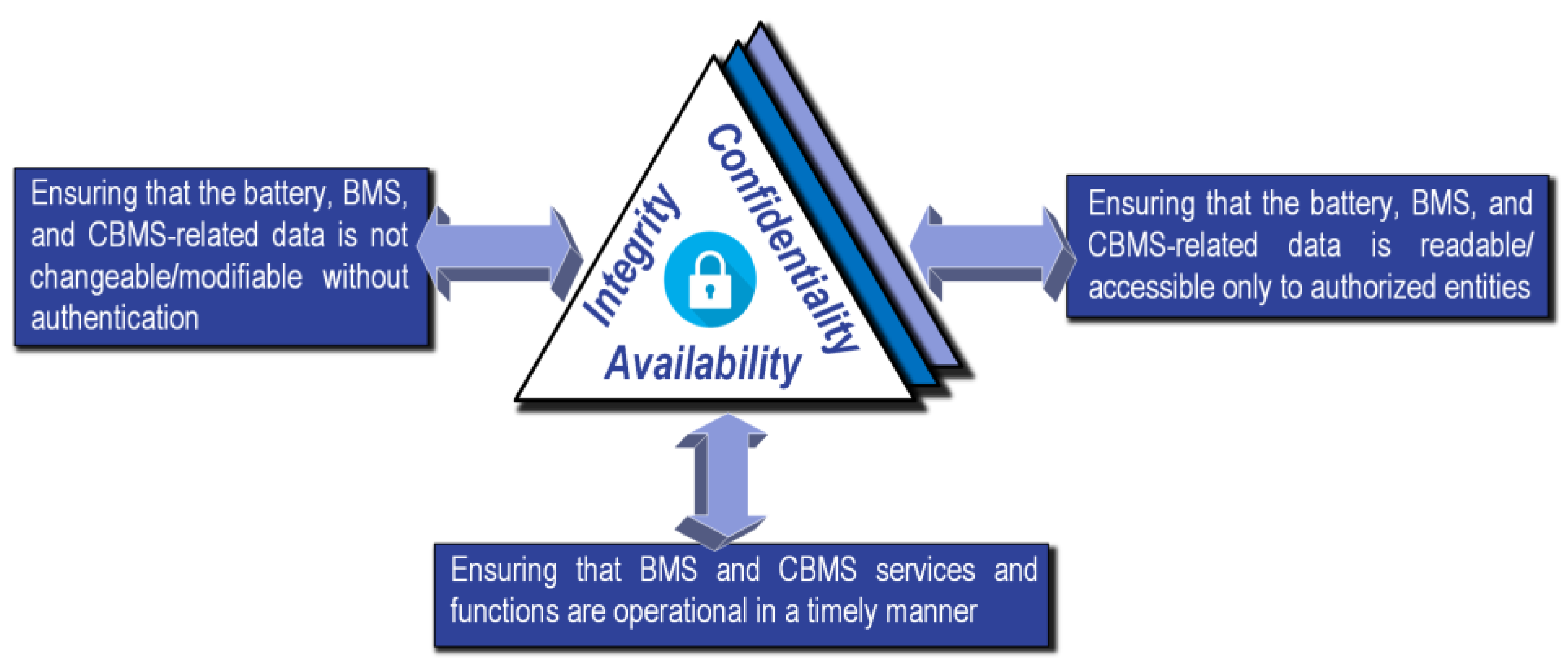
[14][15]. Based on the cybersecurity literature, a secure CPS must satisfy three main requirements, related to confidentiality, integrity, and availability, also known as CIA
[16]. The same CIA security requirements can be applied to the CBMS, as summarized in
Figure 1.
Figure 1. CIA requirements for CBMS cybersecurity.
As explained in the figure, the CIA requirements ensure that the battery and CBMS data cannot be accessed, changed/modified, disrupted, or interrupted without proper authentication. The concurrent assurance of the CIA requirements can result in an acceptably secure CBMS. Different types and scenarios of attacks can be potentially launched to violate the CIA’s conditions. The attack categorization and definitions can be slightly different for different application contexts.
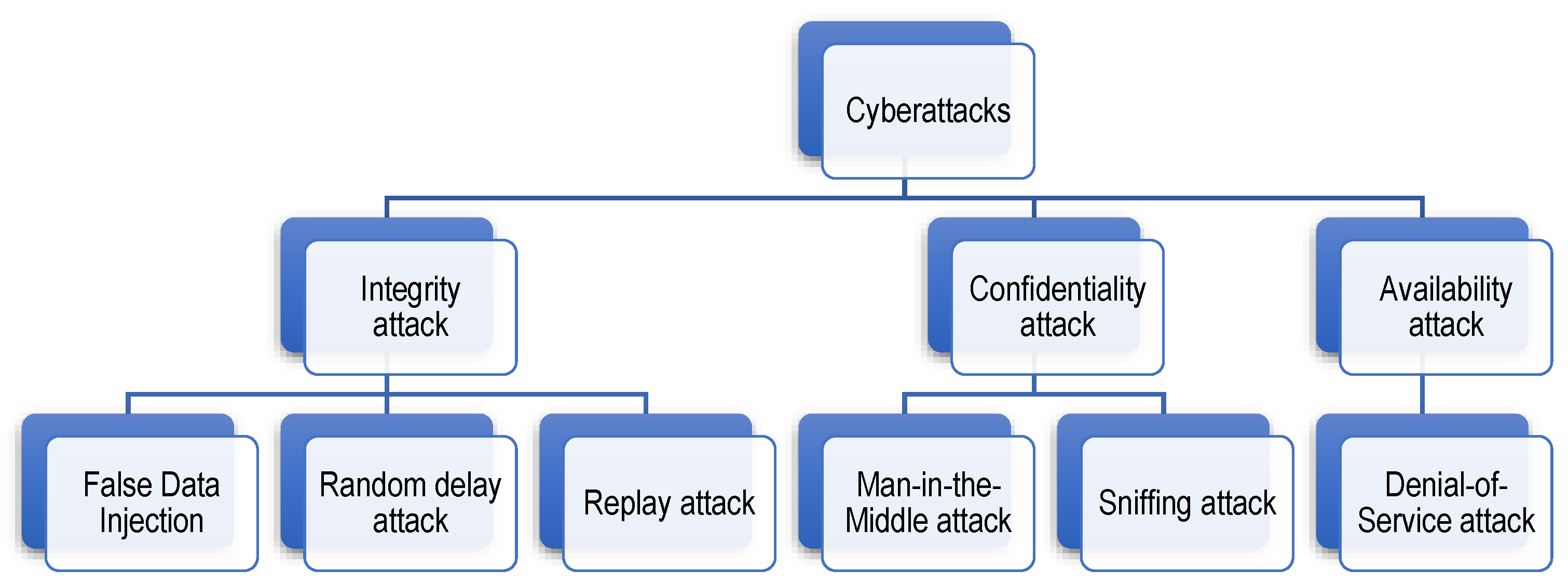
Figure 2 depicts the CBMS cyberattacks classification depending on the CIA requirements attacked
[11][17][18]. It should be noted that in some attack conditions, more than one CIA requirement might become compromised.
Figure 2. Classification of different potential cyberattacks against CBMS.
The CBMS attack scenarios are further explained as follows.
-
Confidentiality attacks: The confidentiality attack refers to unauthorized access to the battery/BMS data without directly targeting to damage the system
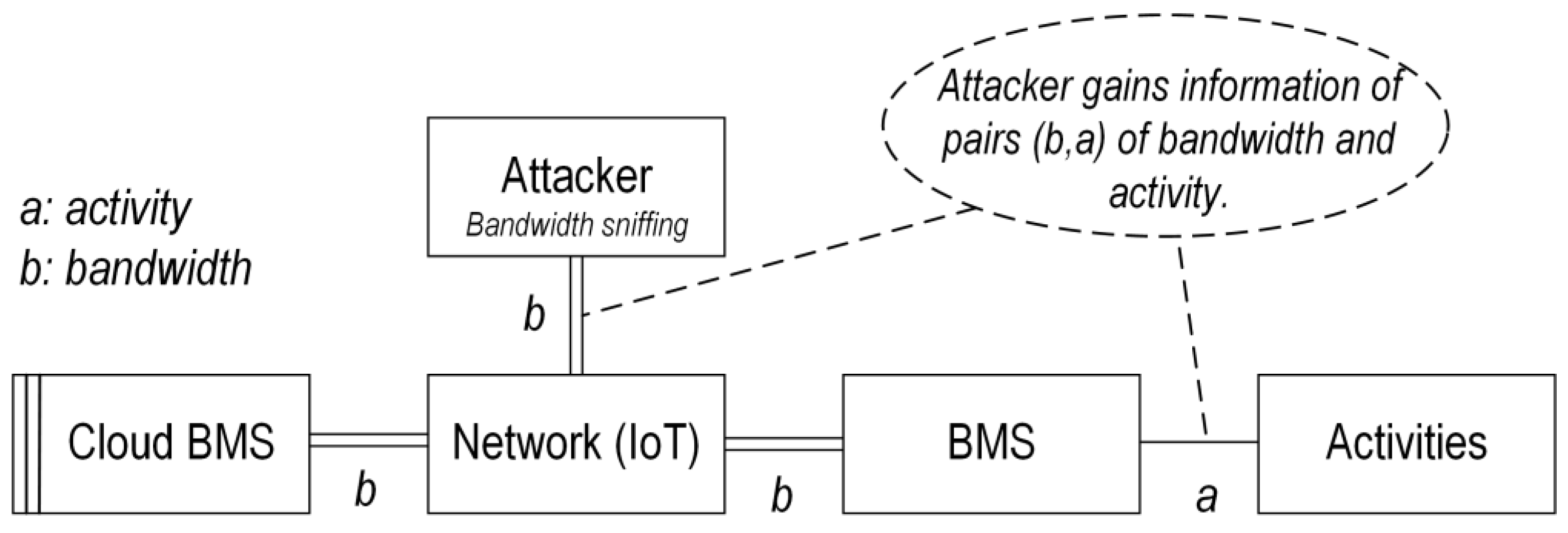
[11]. There are two types of confidentiality attacks: (1) sniffing attack (also known as snooping attack), in which the attacker only can passively listen to the data traffic (in-vehicle through CAN bus or extra-vehicle through IoT communication), and (2) man-in-the-middle (MitM) attack, in which the attacker might also have the possibility to affect the data flow, e.g., via eavesdropping, in which the attacker can relay data between two communication nodes. Regarding sniffing attacks, Ref.
[17] illustrates bandwidth sniffing attacks in which the attacker can gain bandwidth information used between the BMS and CBMS to discover some information about BMS, e.g., active components of the BMS and their related activities. The graphical description of the bandwidth sniffing attack is shown in
Figure 3. This attack is considered an indirect side-channel attack in which indirect information is used to gain knowledge about the system, with the possible intention to construct and launch more complex attack scenarios
[17]. In
Figure 3, activities refer to BMS functions or processes.
Figure 3. Illustration of the bandwidth sniffing attack.
Confidentiality attacks are generally the least dangerous attack type since they can be mostly launched in a passive format and cannot directly compromise functional safety. Nevertheless, the information/data stolen from the CBMS database (storage attack) can be used to design more complicated attack scenarios such as FDI attacks. Confidentiality can be compromised via physical and/or network attacks. The latter can be fulfilled through direct download, spyware/malware, etc. Brute-forcing and cloning may also be considered subcategories of confidentiality attacks. These attacks aim to bypass authentication processes through the hack of passcodes or security tags to access the CBMS servers or the IoT.
-
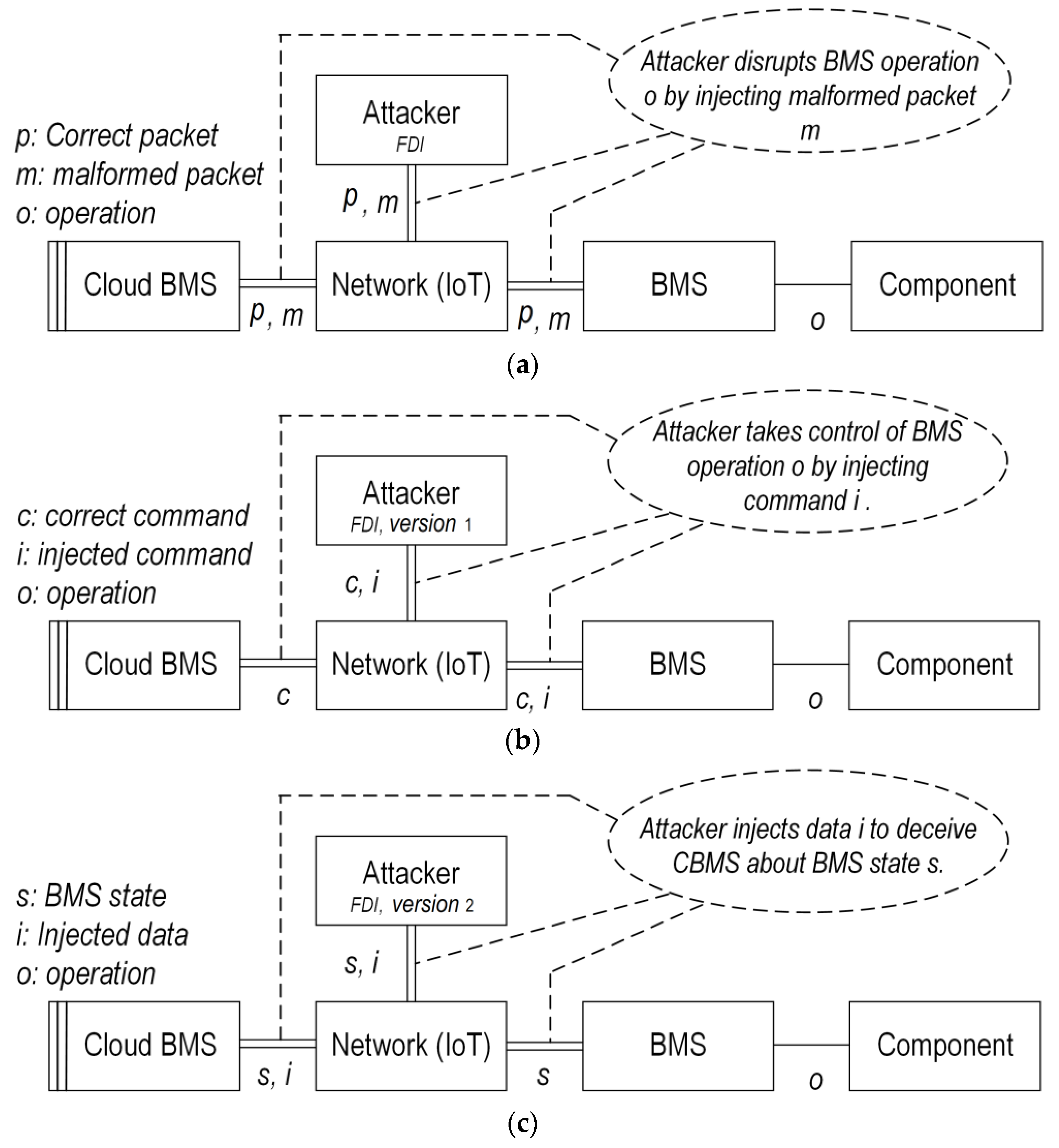
Integrity attacks: These refer to malicious cyberincidents that lead to the corruption, unauthorized modification, or alteration of the CBMS algorithms/data
[4]. Three types of integrity attacks may be considered within the CBMS context: (1) FDI attack refers to deliberate manipulation of the CBMS data such as VIT measurements of cells by injecting false data vectors into the original data. The FDI attacks have a complicated nature and their construction requires some knowledge about the behavior and model of the BESS such that they would normally bypass or circumvent bad data detectors. (2) Random delay attacks are where a random delay will be deliberately introduced to the sequence of BMS control commands or data. (3) Replay attacks occur by wiretapping and repeatedly broadcasting the battery/CBMS measurements/data. Integrity attacks have great potential to compromise EV/pack safety, e.g., to falsify the SoX estimation results, delay the performance of actuators in the battery pack, etc. The graphic illustration of the FDI attack is shown in
Figure 4a. Ref
[17] presents two different versions of the FDI attack: (1) Injecting control commands to take control of the battery pack; (2) injecting falsified data to deceive the BMS as if the data are originally provided by CBMS, causing troubles for BMS algorithms such as SoX estimation. The two FDI versions are illustrated in
Figure 4b,c
[17].
Figure 4. (a) Concept illustration of the FDI attack. (b) Variant 1 of the FDI attack. (c) Variant 2 of the FDI attack.
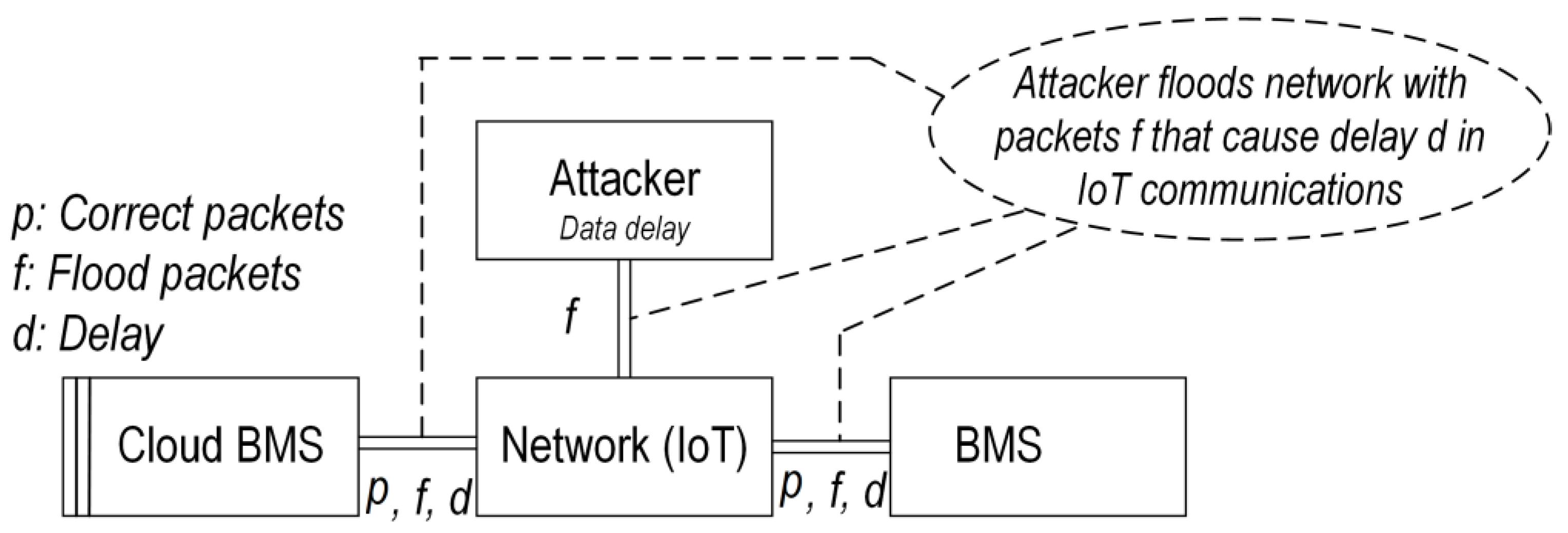
Likewise, Figure 5 shows the block diagram of the delay attack in which the attacker aims to inject a delay in the transmission of data packets in the communication links.
Figure 5. Illustration of the data delay attack.
-
Availability attacks: Refers to the denial-of-service (DoS), in which the attacker seeks to make the CBMS services unavailable to EVs
[19]. DoS can be fulfilled by either flooding the network or crashing the network. Flooding happens when the IoT receives too much information to buffer, which will slow down and eventually stop its services. The most challenging DoS is the distributed DoS (DDoS), in which multiple attackers orchestrate a synchronized DoS attack on CBMS.
In practice, loosely-secured CBMS-IoT networks are vulnerable to all types of attacks described before
[4]. For instance, if the attacker succeeds to create fake routers or unauthorized IoT nodes, it can potentially make spoofed, altered, or replayed routing information in the network layer protocol. Likewise, sending malicious data packets might result in packet collision and data loss. For some protocols, such as MQTT, the entire IoT network will be compromised if the attacker manages to access the broker
[4]. In
[18], different cyberattack possibilities on the stationary BESSs were analyzed. For instance, a random delay attack in which a constant high SOC is introduced to the system was analyzed, where the attack objective was to overdischarge the battery to accelerate the battery degradation.
Malware injection through EVSEs was discussed in
[1]. EVSEs are placed in public without any physical access restrictions. The lack of physical security protocols poses the risk of the injection of malware that can steal sensitive data such as battery/EV data, personal information, payment information, etc. One compromised EVSE opens doors to a variety of exploitable vulnerabilities
[3]. For instance, the polluted EVSEs pose a risk to BMS since the malware can be passed to BMS or other vehicle ECUs through the CAN interface
[1]. The attack surface can be exponentially scaled if malware infection passes to the CBMS that is shared among an EV fleet. For example, if CBMS algorithms are trained and/or operated based on EV fleet data rather than individual EVs, the attack on one EV can impact the performance of other EVs batteries. While this is the worst-case scenario, the exact attack conditions and impacts will depend on the implementation strategy of the CBMS and the communication nodes that will be compromised by attackers.
A potential type of attack that threatens BMSs with wireless communication is the EMI attack. External malicious EMI sources can disrupt the performance of wireless communication links, e.g., in long vehicles such as electric buses where the long physical distance between the slave boards and master PMU weakens the data transmission. A malicious EMI source onboard a bus can potentially disrupt the BMS performance in such conditions. The EMI attack has not been explored in the BMS literature before. EMI attacks are discussed as potential future research.
Regarding the attack paths, communication nodes inside and outside EVs can be potential attack points. This includes in-vehicle ports/connections such as CAN or LIN bus interfaces (internal gateways), OBD-II, SD slot, USB interfaces, etc., or extra-vehicle connections based on Bluetooth, WLAN, IoT gateway MQTT protocol, Modbus TCP/IP
[20][21], CBMS interfaces to the cloud, etc.
[22]. CAN communication or its variations such as CAN 2.0B and CAN-FD (CAN bus with flexible data rate) are the prevailing protocol adopted in the automotive sector for communication between the vehicle ECUs. Due to its robustness and cost-effectiveness, it is usually used for data transmission related to safety-critical systems including BMS, anti-lock braking systems (ABSs), steering systems, etc. Lower important information such as data related to door locks, rain sensors, entertainment, navigation, etc., is generally transmitted using LIN, FlewRay, or MOST protocols
[22]. Despite its robustness, CAN protocols do not have adequate authentication or data encryption mechanisms. The CAN bus access points through the IoT gateway, OBD-II port, etc., are thus potential attack points where malicious attackers can grasp battery and BMS-related data, replay or change the data, etc., to interrupt the performance of the battery pack and EV. A tree diagram of possible attack paths is presented in
[23], which covers vulnerabilities at three different layers, namely, the communication layer through alteration of data packets in the communication channel, the control layer through interruption of the control computations, and the sensing layer through compromising sensor/meter readings. In
[24], evaluation metrics are established to assess the impact of cyberattacks on the ECU of connected or automated EVs. Communications related to V2X IoT, Global Positioning System (GPS) data, wheel sensors, etc., are considered potential attack spots. Likewise, the model predictive control of EV driving speed and torque was considered as the case study, but it is argued that the same metrics can be applied to other EV ECUs, including the CBMS. The analysis was used to identify the potential weak links in the control system design. In a broader sense, Ref.
[25] highlights cyberattacks during BESS manufacturing processes and discusses that such attacks can affect the performance of CBMS and its algorithms that rely on production data, e.g., ML-based techniques.
3. Cyber-Risks and Impacts
Assessment of the cybersecurity risk is challenging and depends on different factors including the use case, implementation mechanisms and strategies, type of interaction between BMS and CBMS, etc. The severity of the damage to the battery may also differ depending on the condition of the battery when it was attacked, e.g., at high SoC values, more severe damage can happen
[25]. The impacts can generally be classified as follows:
As discussed in
[27], the impacts of cyberattacks can also be classified as having a temporary effect (such as draining battery charge, which would temporarily reduce the achievable driving range) or permanent damage (such as reduced battery age). When EVs have interactions with the grid (e.g., through V2G and G2V), attacks on CBMS can cause trouble for the power grid as well. These aspects have been examined in several works. For example, malicious firmware updates can disable EV chargers, which can potentially interrupt emergency and medical services, manufacturing, defense, etc.
[30]. Falsified BMS data such as wrong SoC and charge/power demand data can corrupt the performance of the power system, leading to overfrequency
[31], underfrequency
[32], voltage deviations
[32][33], etc.
[33]. In a recent study
[34], MitM cyberattacks on grid BESSs were emulated, which proved a variety of impacts: prosumer financial losses, including a +36% increase in the electricity bill and a +46% increase in the peak power consumption, which in turn will affect the grid performance.
4. Cloud Battery Management System Attack Detection Methods and Mitigation Strategies
No CPS can be considered 100% secured when they have data flow to/from them, and despite the fact that previously discussed measures can reduce the cyberattack probability, the BMS still might be compromised. Nevertheless, when an attack is successfully launched, the system should be able to detect and take proper action to reduce the risk. In safety-critical situations, the BMS should shut off the battery pack operation, e.g., to avoid a thermal runaway. Some methods have considered nonbinary decisions, for example, slowly backing off the current in some stages
[35], giving a warning to the operator instead of shutting off the battery pack
[36], or extending the time before shutting down the battery. To take timely action, it is critical to devise effective attack detection mechanisms. The literature regarding CBMS cyberattack detection is rare. A basic approach to detect attacks is based on intrusion detection systems (IDSs). An IDS monitors the network traffic and checks it for any sign of intrusion or malicious activities
[37]. For example, it can compare the network traffic against a database of known network patterns under cyberattacks and can send an alarm if a match is found
[37]. Another approach for cyberattack detection is referred to as behavior-based detection
[38]. In this approach, the behavior of a network, system, data, or signal will be compared to a baseline describing nonattack conditions. The residual signals describing the differences between the behavior of the actual index and the baseline index show a potential cyberattack. In this regard, one effective solution is to apply ML techniques to analyze large volumes of BMS data and to identify patterns of attacked and nonattacked conditions and distinguish between them
[38]. An example of ML-based attack detection is presented in
[39], in which an ML-based trust framework for battery sensory data was proposed. The framework is based on false sensor data detection (FSDD) which enables detection of undependable battery data using deep learning algorithms. Likewise, Ref.
[40] presented algorithms for the detection of denial-of-charging and overcharging attacks. Two static and observer-based dynamic cyberattack detectors were designed. The static detector is based on the measurements while the dynamic detector utilizes both battery measurements and models to detect the attacks, and it was shown that the latter achieves superior attack detectability performance
[40]. A more detailed review of cyberattack detection techniques can be found in
[41][42][43].
5. Methods for Enhancing the Cybersecurity of the Battery Management System/Cloud Battery Management System
Security plays a critical role in EV’s functional safety. Different security measures related to hardware security, software update security, penetration test, and code reviews are usually applied in the automotive industry. This includes approaches based on information encryption and authentication or using firewalls for communication between vehicle devices and external networks
[24]. The CBMS should similarly emplace appropriate protection measures at both software and hardware levels to protect it against any unauthorized alteration. According to the literature, several measures can be taken into account to enhance the cybersecurity of the CBMS. As outlined in
[11], these measures can be applied in three different steps: (1) architecture design step (e.g., considering a distributed or decentralized CBMS instead of centralized implementation to enhance security), (2) communication system design step (e.g., considering security protocols, data encryption, user authentication, etc.), and (3) top-up protection (e.g., by protecting BMS sensors, etc.). The protection measures are described in the following:
-
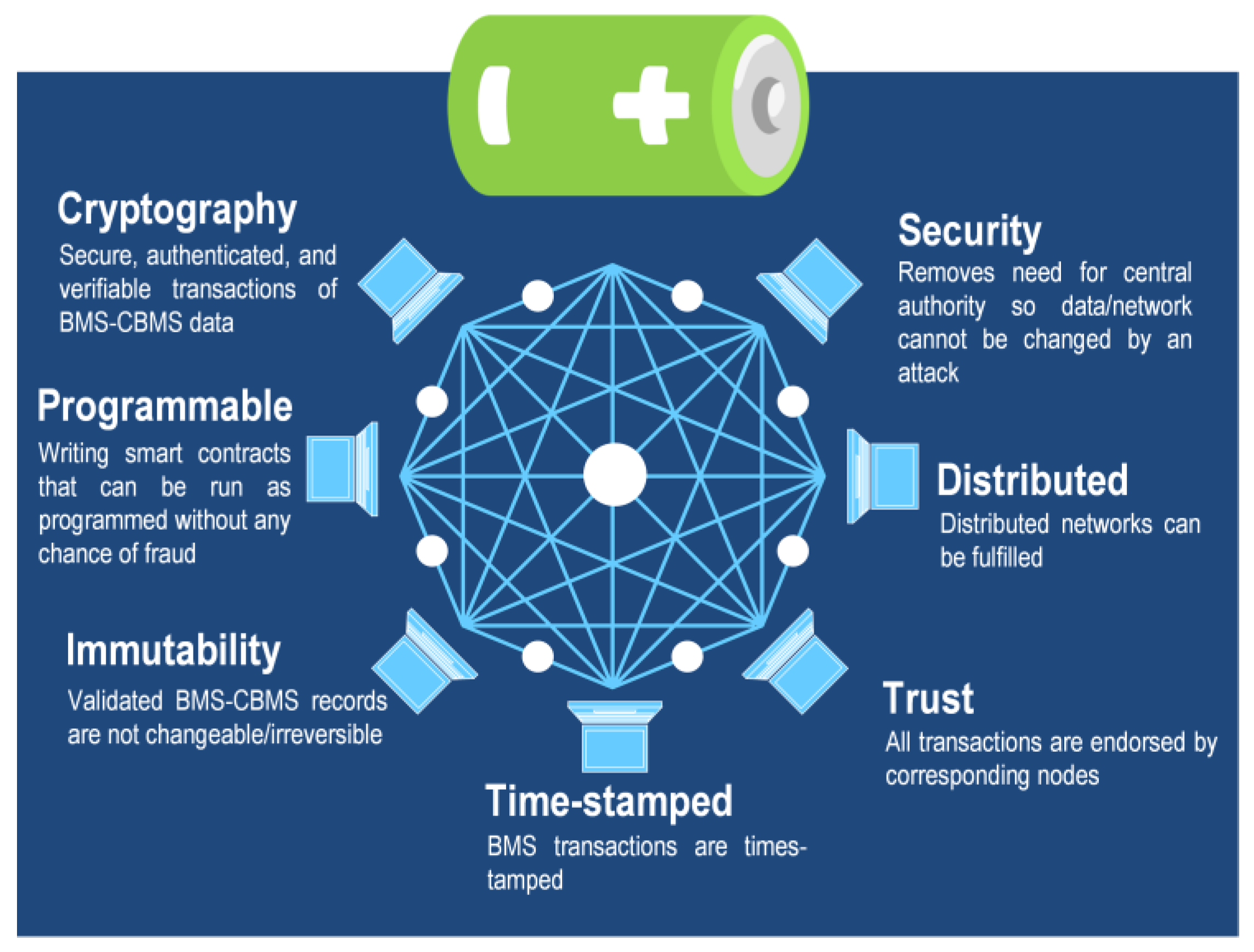
Blockchain technology: Blockchain is a secure distributed database for maintaining constantly growing data records. It was initially developed to secure cryptocurrency transactions, but lately, it has been explored for new cloud applications including CBMSs. Concerning the CBMSs, it has been discussed that the blockchain can be used to enhance both software and hardware aspects
[39]. For instance, the blockchain can be used to manage critical activities related to the transaction and sharing of battery data between the CBMS and the BMS terminal nodes
[19]. The blockchain transactions are time-stamped, cryptic, and immutable, meaning that the data cannot be read or modified from single communication nodes. Furthermore, transactions will be endorsed by corresponding nodes so the authenticity of the communication nodes and data can be validated. Likewise, the distributed/decentralized nature of the blockchain significantly lowers the cybersecurity risk in case of successful attacks on one or more communication nodes. Key features of blockchain technology are described in
Figure 6 [44].
Figure 6. Main features of blockchain technology.
The application of blockchain in the CBMS context has been explored in several research papers. In
[45], the Blockchain-as-a-Service (BaaS) concept was proposed for BESS applications. The main idea of BaaS is to develop a universal secure platform for CBMS implementation to support the implementation of a range of use cases. As suggested and conceptualized, the BaaS can be used to ensure the validity and integrity of battery data throughout the value chain. Other examples were presented in
[46][47][48], where security-hardening technology and blockchain-based firmware security check and recovery frameworks were proposed for application to the (wireless) BMSs to enhance their cybersecurity. Similarly, Ref.
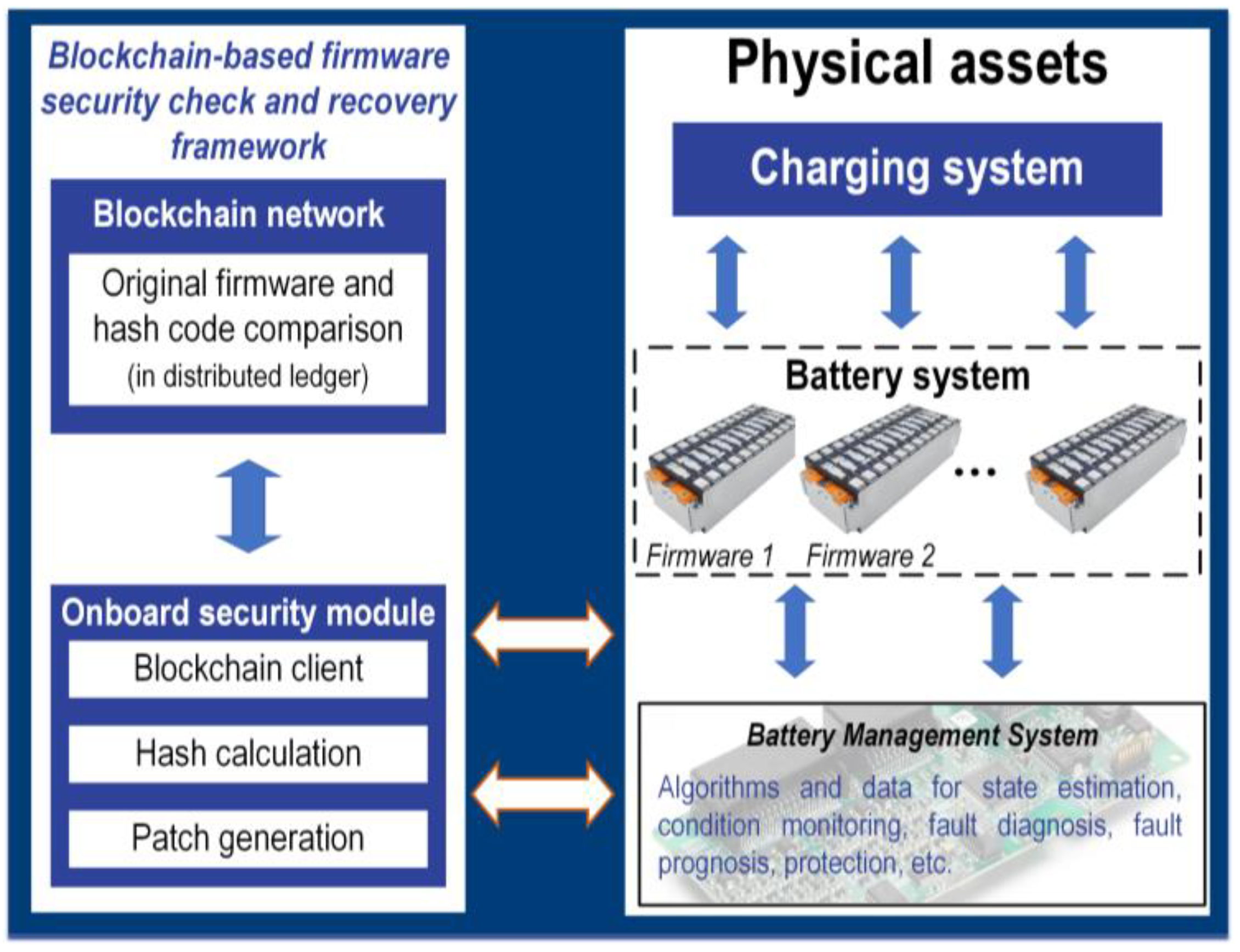
[49] proposed a blockchain-based IoT network for the cybersecurity enhancement of wireless BMSs. A typical blockchain framework applied to the BMS context is shown in
Figure 7.
Figure 7. A typical architecture for blockchain-based firmware security enhancement
[47].
The physical assets including the BMS units or charging equipment can be considered as a blockchain client. With hash calculation, each client will be given a unique fixed-size output that corresponds to a digital fingerprint of the input data. Any change to the input data will result in a different output hash, which can be used to check the authentication of the accesses to the database or codebase of the BMS
[49]. Hash code comparison will be fulfilled in the distributed ledger, which means that hash codes will be stored and processed on a network rather than a single point. Thus, a high level of protection and security against all types of cyberattacks can be assured. A comprehensive discussion of the blockchain-based implementation of the battery control strategies on a distributed network of BMS nodes can be found in
[23].
-
Resilient software design: Design-for-cybersecurity (DFC) can be used to enhance the robustness of the CBMS software against cyberthreats. An example of DFC is the design of robust and resilient state estimation algorithms that are capable of detecting and/or neutralizing cyberattacks and their effects. Several CPS-based applications have reported the use of secure algorithms such as secure state estimators to protect against cyberattacks. For example, Refs.
[50][51] designed a secure Kalman filter (KF)-based algorithm for dynamic state estimation in energy grids. The algorithm was designed to detect the onset of an FDI attack and the location (specific communication nodes) where the attack was launched. Thus, with the resilient algorithm, the state estimations will recover to the true state estimates even though the measurements are manipulated. Another example was presented in
[52], where a resilient algorithm was designed for finite-time secure state estimation in a centrifugal pump to protect it against sensor attacks. A resilient SOC estimation algorithm based on artificial neural networks (ANNs) was proposed in
[53]. The algorithm was designed to neutralize the effect of cyberattacks on the battery data so the SOC estimations remain valid under attack conditions. Such techniques can be used to develop secure algorithms, for example, secure SoX estimation algorithms or cyberattack detection algorithms with the ability to discriminate between a failure (such as a sensor failure of cell failure) and a cyberattack. In this context, Ref.
[11] highlighted the ability of AI-based data-driven methods in sensor measurement forecast (pseudo-measurement generation), which will offer redundancy for when the sensors are attacked. Similarly, Ref.
[54] provided a few recommendations to enhance IoT-related security, e.g., through secure coding, formatting the source codes as libraries, executables, and obfuscation codes, which will prevent source code changes due to cyberattacks. As argued in
[54], secure coding may refer to designing secure CBMS software together with a rule-checker for secure coding and an incorporated weakness analyzer. BMS software updates should also be performed securely. In this regard, researchers have suggested code-signing firmware updates
[55]. The security of BMS source codes should also take into account reliable libraries throughout the source code
[56].
-
Cross-verification of BMS and CBMS: One potential solution to ensure the credibility of the CBMS algorithmic results such as SOX estimation results could be to perform the related calculations in different ways on both BMS and CBMS. The results obtained on the onboard BMS can then be used to cross-verify the accuracy of the CBMS algorithms and their robustness
[25]. A great mismatch between the results of the onboard BMS and the CBMS potentially indicates an unusual situation such as a cyberattack launched against CBMS or IoT communication links.
-
Hardware Security Modules (HSMs): CPUs with security stacks and embedded HSMs are the nuclei of vehicle cybersecurity. They are used to protect safety-critical vehicle tasks such as the functioning of airbags, steering, and braking systems. Similarly, BMS processors can be protected against cyberthreats through the use of HSMs
[57]. As shown, the HSM can be connected to the BMS microprocessor as separate hardware, which includes an individual processor, cryptographic functions, and dedicated memory to support hardware security firmware
[57]. The BMS enhanced by HSM can perform autonomous authenticity and integrity checks, for example, when a software update is to be installed, for secure in-vehicle communications through the CAN bus, and in case of extra-vehicle communications to the IoT and CBMS. Reference
[57] also suggested a procedure for the determination of the ASILs by including the cybersecurity risks in the functional safety analysis. Accordingly, it pinpoints the importance of end-to-end (E2E) protection for the exchange of critical data to ensure an ASIL D requirement, e.g., for data that are linked to the braking signals, steering angle, battery pack safety, etc.
-
Encryption: Encryption refers to the process of encoding BMS/CBMS software data/information to prevent unauthorized access and/or data alternation
[58]. Encryption can help ensure that sensitive battery/BMS data is kept confidential and that only authorized assets have access to the data. Internal communications, such as communication from slave boards to master BMS or vehicle CAN communication, as well as IoT communications from BMS to the CBMS and vice versa, can be effectively protected using cryptographic protocols such as TLS
[54]. For example, end-to-end encryption based on NISTIR guidance on cryptography and key management has been suggested to assure the integrity and confidentiality of battery data
[59][60]. Likewise, to protect against MitM cyberattacks, additional end-point security protocols (such as IEC 62351-7) and role-based access control (RBAC) based on IEC 62351-8 can be considered
[61]. Regarding different battery data stored on CBMS, database encryption is an effective solution to prevent data stealth. Database encryption transfers different battery data (state data, link data, metadata, etc.) into cipher text which cannot be comprehended by unauthorized users (e.g., by attackers). Examples of database encryption methods are the hashing technique, SHA256 encryption, etc.
[54]. In this regard, the National Renewable Energy Laboratory (NREL) also highlights the effectiveness of encryption in protecting both data-at-rest (data stored on BMS and/or CBMS) and data-in-flight (battery transactions real-time data)
[29]. Despite being a powerful solution, encryption has some weaknesses. Encryption requires key management to encrypt and decrypt data or codes, and if the key is stolen, intercepted, or compromised, the data encryption can be broken. To ensure key security, Ref.
[62] suggested a pluggable key management device with a key management protocol and integrated formal analysis to assure security compliance. It is also noteworthy that encryption protocols and algorithms are somehow susceptible to vulnerabilities such as side-channel attacks. Moreover, encryption is useless in the case of specific attack types against CBMS such as random delay attacks.
-
User authentication and access control [63][64]: User authentication provides an additional layer of security against unauthorized access to the battery, CBMS, and related data. Multifactor authentication or passwords can be used when accessing the battery database on the cloud, CAN bus through the OBD port, before performing maintenance, or when configuration/reconfiguration of the BMS or CBMS software is planned. Adopting ISO 15118 multimodal and multipass authentication processes was suggested in
[65]. Likewise, in the case of adopting the MQTT protocol for IoT communications, Ref.
[54] suggested that access to the broker should be restricted by deploying authentication keys on both sides including the clients and broker. In this context, Ref.
[54] recommended using proper tools for checking the login history to track unauthorized access attempts.
In addition to the aforementioned protection mechanisms, physical protection of the communication terminals/nodes, e.g., through secure housing designs, hardwiring, etc., should also be considered a priority in the design of the BMS/CBMS components
[25]. NREL recommends removing BMS unnecessary interfaces and external ports, adding tamper monitoring and resistance
[66], adding secure bootloaders to BMS, removing hard-coded passwords, and certification of CBMS services with the Federal Risk and Authorization Management Program (FedRAMP)
[7]. For example, one can refer to a recent project which investigates a so-called s-NIC card (Secure NETWORK Interface Card) that supports secure boot and tamper resistance for EVSE applications
[67]. Likewise, Refs.
[11][25] highlighted the importance of transparency in battery data and algorithms to secure processes related to testing, verifying, and communicating between BMS and CBMS. This is important to improve the explainability of data/algorithms, since, usually, many factors affect the balance and optimization of algorithms’ performances. Transparency reduces the cybersecurity risk by maintaining human-in-the-loop, which will make cyberattacks more apparent before they turn into a risk
[25].
DFC requires additional effort for designing and implementing proper cybersecurity measures. Thus, the overall cost of the system will be increased. The optimum cybersecurity practice should thus be chosen based on the application area, specific use cases of the CBMS, and the implementation strategy, such as how the BMS and CBMS will talk to each other and how CBMS feedback will be prioritized. Multiple security measures can be simultaneously adopted if a high-security level is demanded.
In the context of digital twins, a detailed review of threats and cybersecurity recommendations were presented in
[68].
Table 1 provides a summary of key CBMS cybersecurity topics discussed in this section.