Battery management systems (BMSs) are critical to ensure the efficiency and safety of high-power battery energy storage systems (BESSs) in vehicular and stationary applications. The proliferation of battery big data and cloud computing advancements has led to the development of a new generation of BMSs, named Cloud BMS (CBMS), aiming to improve the performance and safety of BESSs. The CBMS is a cyber-physical system with connectivity between the physical BMS and a cloud-based virtual BMS, which is realized through a communication channel such as Internet of Things. Compared to the traditional BMS, the CBMS offers significantly higher computational resources, leveraging the implementation of advanced digital twin models and best-in-class algorithms in the BMS software, which will provide superior performances.
- electric vehicle
- battery management systems
- cloud computing
- cybersecurity
- cyberattacks
- blockchain
- cyber-physical systems
- Internet of Things
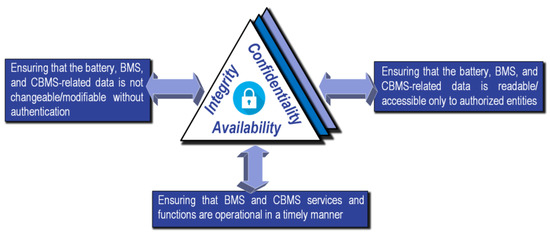
1. BESS Cybersecurity
2. Attack Types and Scenarios
-
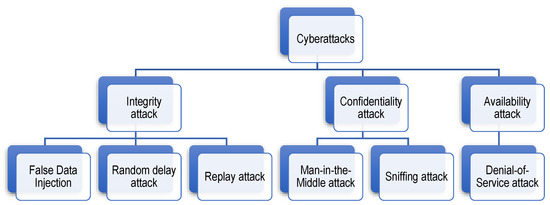
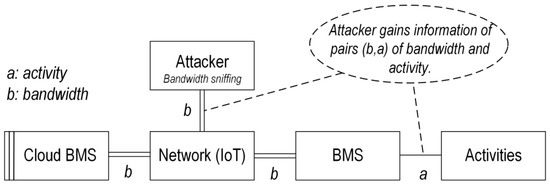
Confidentiality attacks: The confidentiality attack refers to unauthorized access to the battery/BMS data without directly targeting to damage the system [44]. There are two types of confidentiality attacks: (1) sniffing attack (also known as snooping attack), in which the attacker only can passively listen to the data traffic (in-vehicle through CAN bus or extra-vehicle through IoT communication), and (2) man-in-the-middle (MitM) attack, in which the attacker might also have the possibility to affect the data flow, e.g., via eavesdropping, in which the attacker can relay data between two communication nodes. Regarding sniffing attacks, Ref. [50] illustrates bandwidth sniffing attacks in which the attacker can gain bandwidth information used between the BMS and CBMS to discover some information about BMS, e.g., active components of the BMS and their related activities. The graphical description of the bandwidth sniffing attack is shown in Figure 3. This attack is considered an indirect side-channel attack in which indirect information is used to gain knowledge about the system, with the possible intention to construct and launch more complex attack scenarios [50]. In Figure 3, activities refer to BMS functions or processes.
-
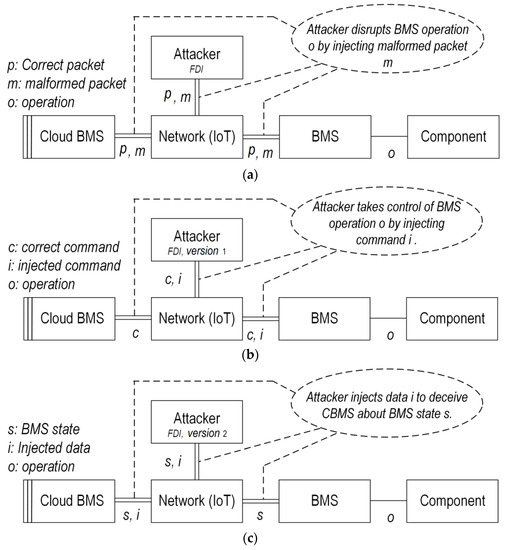
Integrity attacks: These refer to malicious cyberincidents that lead to the corruption, unauthorized modification, or alteration of the CBMS algorithms/data [37]. Three types of integrity attacks may be considered within the CBMS context: (1) FDI attack refers to deliberate manipulation of the CBMS data such as VIT measurements of cells by injecting false data vectors into the original data. The FDI attacks have a complicated nature and their construction requires some knowledge about the behavior and model of the BESS such that they would normally bypass or circumvent bad data detectors. (2) Random delay attacks are where a random delay will be deliberately introduced to the sequence of BMS control commands or data. (3) Replay attacks occur by wiretapping and repeatedly broadcasting the battery/CBMS measurements/data. Integrity attacks have great potential to compromise EV/pack safety, e.g., to falsify the SoX estimation results, delay the performance of actuators in the battery pack, etc. The graphic illustration of the FDI attack is shown in Figure 4a. Ref [50] presents two different versions of the FDI attack: (1) Injecting control commands to take control of the battery pack; (2) injecting falsified data to deceive the BMS as if the data are originally provided by CBMS, causing troubles for BMS algorithms such as SoX estimation. The two FDI versions are illustrated in Figure 4b,c [50].
-
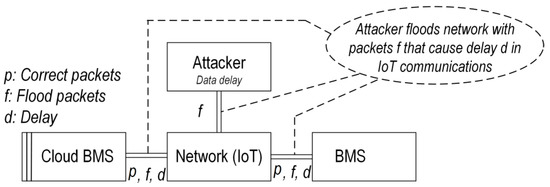
Availability attacks: Refers to the denial-of-service (DoS), in which the attacker seeks to make the CBMS services unavailable to EVs [52]. DoS can be fulfilled by either flooding the network or crashing the network. Flooding happens when the IoT receives too much information to buffer, which will slow down and eventually stop its services. The most challenging DoS is the distributed DoS (DDoS), in which multiple attackers orchestrate a synchronized DoS attack on CBMS.
3. Cyber-Risks and Impacts
-
Functional impacts: These occur when a system, component, function, or algorithm in CBMS is no longer functioning correctly due to a malicious cyberattack. For instance, [56] refers to a “denial-of-charging” cyberattack that falsifies the SoC estimation algorithm in BMS to prevent the battery pack from being fully charged. This could lead to prolonged driving due to the lower charge available. Integrity attacks can lead to malfunctioning of BMS algorithms, e.g., causing divergence of SoX estimators, resulting in suboptimal solutions in thermal and energy management, etc.
-
Financial and privacy losses: Attacks against BMS sensors or algorithms such as voltage sensors or SoC/SoP estimation algorithms can result in BMS malfunctioning, which in turn can result in accelerated degradation of the battery [57]. For example, falsified SoC data can cause the battery to be operated at very high or very low SoC regions, which will speed up the aging processes of the battery. Falsified SoH data can result in wrong battery maintenance implications, e.g., the battery could either be serviced/maintained too soon when maintenance is not required or too late when the battery has undergone expensive damages. Manipulation of the cooling-related sensors and/or algorithms may result in accelerated aging of the battery. In one case example, the BMS was compromised to turn on the battery heater, draining all the charge [29]. Such scenarios can occur, for example, through false injecting of CAN messages to the EV CAN bus (e.g., through CHAdeMO charger connection). Likewise, critical information can be compromised under cyberattacks, which could lead to loss of privacy, e.g., GPS data, driving profiles, etc. Last, but not least, technology and intellectual property theft can occur by stealing confidential manufacturing data (battery cell data, BMS design data, layouts, etc.) through confidentiality attacks.
-
Safety impacts: BMS is usually programmed with hard limits to avoid safety risks, e.g., by comparing cell voltages to the safe voltage limits. However, such limits might be overridden under malicious BMS firmware updates, which may result in battery overcharge and/or overdischarge. Small overcharge will result in accelerated aging of the battery, while overcharge in the scale of minutes might cause more serious risks such as internal short-circuits and thermal runaways [57]. Cooling system performance may also be interpreted through cyberattacks against thermal management systems, leading to the thermal runaway risk. Thus, it is important to devise efficient failsafes (e.g., mechanical override design features) to disconnect the battery in such cases [58]. Poor estimation of SoX data might also result in conditions that compromise the safety, e.g., leading to lower maneuverability of the EV on the road or misleading drivers about the achievable EV performance such as acceleration, etc. There is also a safety risk when the battery pack is disconnected, or its performance is limited due to a cyberattack while the EV is in driving mode.
-
Side impacts: The CBMS large databases can be used to develop battery models and algorithms for other lifecycle stages such as second-life battery applications. Attacks against the CBMS database can result in data poisoning and data corruption and this will further affect the battery and BMS designs that are fulfilled based on these corrupted datasets.
4. CBMS Attack Detection Methods and Mitigation Strategies
5. Methods for Enhancing the Cybersecurity of the BMS/CBMS
-
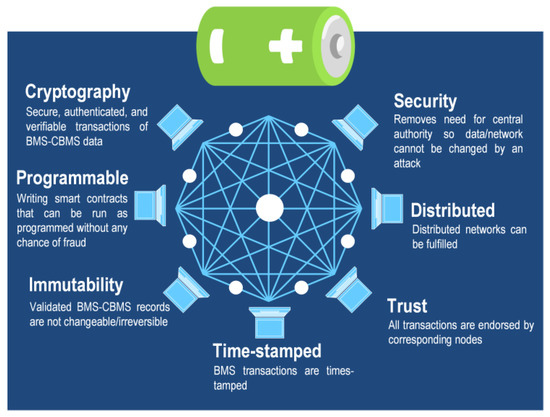
Blockchain technology: Blockchain is a secure distributed database for maintaining constantly growing data records. It was initially developed to secure cryptocurrency transactions, but lately, it has been explored for new cloud applications including CBMSs. Concerning the CBMSs, it has been discussed that the blockchain can be used to enhance both software and hardware aspects [68]. For instance, the blockchain can be used to manage critical activities related to the transaction and sharing of battery data between the CBMS and the BMS terminal nodes [52]. The blockchain transactions are time-stamped, cryptic, and immutable, meaning that the data cannot be read or modified from single communication nodes. Furthermore, transactions will be endorsed by corresponding nodes so the authenticity of the communication nodes and data can be validated. Likewise, the distributed/decentralized nature of the blockchain significantly lowers the cybersecurity risk in case of successful attacks on one or more communication nodes. Key features of blockchain technology are described in Figure 6 [73].
-
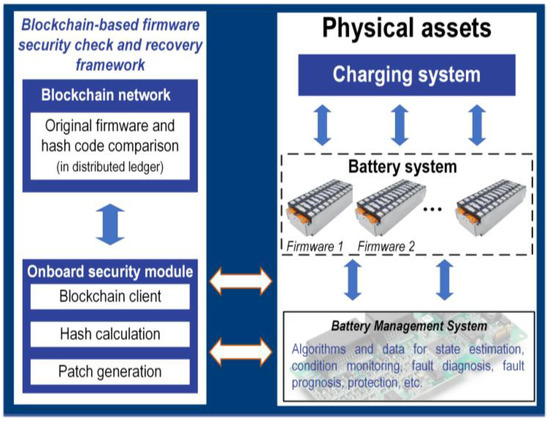
Resilient software design: Design-for-cybersecurity (DFC) can be used to enhance the robustness of the CBMS software against cyberthreats. An example of DFC is the design of robust and resilient state estimation algorithms that are capable of detecting and/or neutralizing cyberattacks and their effects. Several CPS-based applications have reported the use of secure algorithms such as secure state estimators to protect against cyberattacks. For example, Refs. [78,79] designed a secure Kalman filter (KF)-based algorithm for dynamic state estimation in energy grids. The algorithm was designed to detect the onset of an FDI attack and the location (specific communication nodes) where the attack was launched. Thus, with the resilient algorithm, the state estimations will recover to the true state estimates even though the measurements are manipulated. Another example was presented in [80], where a resilient algorithm was designed for finite-time secure state estimation in a centrifugal pump to protect it against sensor attacks. A resilient SOC estimation algorithm based on artificial neural networks (ANNs) was proposed in [30]. The algorithm was designed to neutralize the effect of cyberattacks on the battery data so the SOC estimations remain valid under attack conditions. Such techniques can be used to develop secure algorithms, for example, secure SoX estimation algorithms or cyberattack detection algorithms with the ability to discriminate between a failure (such as a sensor failure of cell failure) and a cyberattack. In this context, Ref. [44] highlighted the ability of AI-based data-driven methods in sensor measurement forecast (pseudo-measurement generation), which will offer redundancy for when the sensors are attacked. Similarly, Ref. [81] provided a few recommendations to enhance IoT-related security, e.g., through secure coding, formatting the source codes as libraries, executables, and obfuscation codes, which will prevent source code changes due to cyberattacks. As argued in [81], secure coding may refer to designing secure CBMS software together with a rule-checker for secure coding and an incorporated weakness analyzer. BMS software updates should also be performed securely. In this regard, researchers have suggested code-signing firmware updates [82]. The security of BMS source codes should also take into account reliable libraries throughout the source code [83].
-
Cross-verification of BMS and CBMS: One potential solution to ensure the credibility of the CBMS algorithmic results such as SOX estimation results could be to perform the related calculations in different ways on both BMS and CBMS. The results obtained on the onboard BMS can then be used to cross-verify the accuracy of the CBMS algorithms and their robustness [28]. A great mismatch between the results of the onboard BMS and the CBMS potentially indicates an unusual situation such as a cyberattack launched against CBMS or IoT communication links.
-
Hardware Security Modules (HSMs): CPUs with security stacks and embedded HSMs are the nuclei of vehicle cybersecurity. They are used to protect safety-critical vehicle tasks such as the functioning of airbags, steering, and braking systems. Similarly, BMS processors can be protected against cyberthreats through the use of HSMs [84]. As shown, the HSM can be connected to the BMS microprocessor as separate hardware, which includes an individual processor, cryptographic functions, and dedicated memory to support hardware security firmware [84]. The BMS enhanced by HSM can perform autonomous authenticity and integrity checks, for example, when a software update is to be installed, for secure in-vehicle communications through the CAN bus, and in case of extra-vehicle communications to the IoT and CBMS. Reference [84] also suggested a procedure for the determination of the ASILs by including the cybersecurity risks in the functional safety analysis. Accordingly, it pinpoints the importance of end-to-end (E2E) protection for the exchange of critical data to ensure an ASIL D requirement, e.g., for data that are linked to the braking signals, steering angle, battery pack safety, etc.
-
Encryption: Encryption refers to the process of encoding BMS/CBMS software data/information to prevent unauthorized access and/or data alternation [85]. Encryption can help ensure that sensitive battery/BMS data is kept confidential and that only authorized assets have access to the data. Internal communications, such as communication from slave boards to master BMS or vehicle CAN communication, as well as IoT communications from BMS to the CBMS and vice versa, can be effectively protected using cryptographic protocols such as TLS [81]. For example, end-to-end encryption based on NISTIR guidance on cryptography and key management has been suggested to assure the integrity and confidentiality of battery data [86,87]. Likewise, to protect against MitM cyberattacks, additional end-point security protocols (such as IEC 62351-7) and role-based access control (RBAC) based on IEC 62351-8 can be considered [88]. Regarding different battery data stored on CBMS, database encryption is an effective solution to prevent data stealth. Database encryption transfers different battery data (state data, link data, metadata, etc.) into cipher text which cannot be comprehended by unauthorized users (e.g., by attackers). Examples of database encryption methods are the hashing technique, SHA256 encryption, etc. [81]. In this regard, the National Renewable Energy Laboratory (NREL) also highlights the effectiveness of encryption in protecting both data-at-rest (data stored on BMS and/or CBMS) and data-in-flight (battery transactions real-time data) [58]. Despite being a powerful solution, encryption has some weaknesses. Encryption requires key management to encrypt and decrypt data or codes, and if the key is stolen, intercepted, or compromised, the data encryption can be broken. To ensure key security, Ref. [89] suggested a pluggable key management device with a key management protocol and integrated formal analysis to assure security compliance. It is also noteworthy that encryption protocols and algorithms are somehow susceptible to vulnerabilities such as side-channel attacks. Moreover, encryption is useless in the case of specific attack types against CBMS such as random delay attacks.
-
User authentication and access control [90,91]: User authentication provides an additional layer of security against unauthorized access to the battery, CBMS, and related data. Multifactor authentication or passwords can be used when accessing the battery database on the cloud, CAN bus through the OBD port, before performing maintenance, or when configuration/reconfiguration of the BMS or CBMS software is planned. Adopting ISO 15118 multimodal and multipass authentication processes was suggested in [92]. Likewise, in the case of adopting the MQTT protocol for IoT communications, Ref. [81] suggested that access to the broker should be restricted by deploying authentication keys on both sides including the clients and broker. In this context, Ref. [81] recommended using proper tools for checking the login history to track unauthorized access attempts.
| Potential Attack Paths | Impacts on CBMS | Countermeasures | |
|---|---|---|---|
|
|
|
|
| Potential cyberattacks against CBMSs | |||
| Confidentiality |
|
||
| Integrity |
|
||
| Attack Detection | |||
|
|||
| Availability |
|
||
This entry is adapted from the peer-reviewed paper 10.3390/batteries9070382
