1. Security Vulnerabilities in MGs
Cybersecurity vulnerabilities in MGs are similar to those found in large-scale energy grids. However, due to the unique characteristics of MGs, they require different attention. MGs are mainly based on RESs. Therefore, the devices used for energy generation, storage, and distribution are manufactured by different vendors and are not compatible with each other
[1][2]. This can lead to cybersecurity vulnerabilities in MGs as cyberattackers may exploit the weaknesses of these devices.
The vulnerabilities of MGs are generally caused by factors such as inadequate security measures, lack of software and hardware updates, weak authentication, incorrect configuration, faulty software coding, and improperly separated networks
[3]. Cybersecurity vulnerabilities allow a cyberattacker to take control of devices, gain unauthorized access to systems, install malware, and monitor network traffic. This can cause interruptions in the energy production and distribution processes of MGs and create security risks for individuals
[4].
Table 1 provides a brief description of the categories and explanations of significant vulnerabilities encountered in MGs.
Table 1. Some significant vulnerabilities encountered in MGs.
2. Threats to Microgrid Cybersecurity
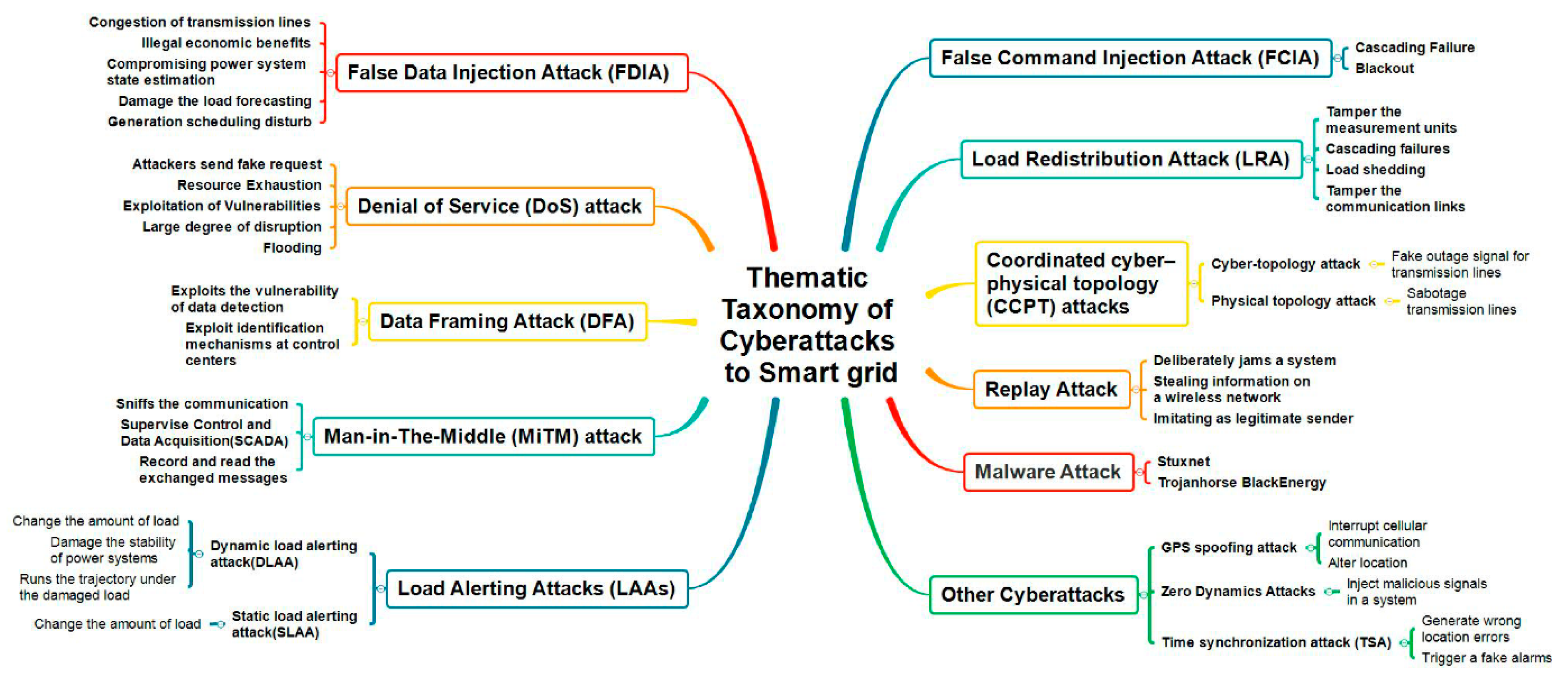
MGs and smart grids, as complex cyberphysical systems, are vulnerable to various types of cyberattacks that can cause severe disruptions to energy generation, distribution, and consumption. To better understand these risks, it is essential to develop a systematic taxonomy of cyberattacks on smart grids based on their themes and characteristics
[5][6]. Such a taxonomy can provide a useful framework for classifying and analyzing different types of cyberattacks, identifying common patterns and vulnerabilities, and designing effective countermeasures. A remarkable and up-to-date thematic taxonomy of cyberattacks to smart grids, which can also be considered for MGs, is presented by Ding et al., as illustrated in
Figure 1 [7].
Figure 1. A thematic taxonomy of cyberattacks to smart grids
[7].
As illustrated in
Figure 1, cyberattacks on smart and microgrids has mainly focused on various attack methods such as false data injection attacks, denial of service attacks, data framing attacks, man-in-the-middle attacks, load altering attacks, false command injection attacks, load redistribution attacks, coordinated cyberphysical topology attacks, and replay attacks. These attacks exploit different vulnerabilities in power grids and have varying intentions and strategies. Moreover, the integration of information systems into power physical systems has resulted in severe threats such as malware attacks
[7]. It is crucial to analyze and understand these cyberattacks on MGs to develop effective countermeasures against potential threats. Therefore, some of the most significant of attacks are outlined below:
False Data Injection Attack: False data injection (FDI) can have serious consequences by affecting the operation of MGs. FDI attacks cause incorrect processing or decision making in the system by providing misleading or erroneous data to the network users
[8][9]. This can lead to faulty load distribution, device failures, or system crashes. Typically, an attacker injects false data into network devices starting from a point where the attacker can access the network system. By using fake data, the attacker can deceive the network devices and cause them to perform incorrect operations. For example, an attacker can change traffic density data by sending false signals to a traffic sensor and create traffic flow in the wrong direction
[10]. False data injection attacks have been increasingly observed in recent years. To protect against these attacks, security vulnerabilities of microgrid systems need to be identified, and security measures need to be taken
[11][12]. Additionally, designing network devices for authentication and accuracy checks can reduce the impact of attacks.
Denial of Service (DoS): The cybersecurity infrastructure in MGs should be designed to ensure access to energy, related information, and communication structures. In this context, a DoS attack targets power availability by reliably and timely affecting access to microgrid services
[13][14]. Despite its simplicity, an effective DoS attack can cause significant disruption. A DoS attack can be carried out by overloading the device or channel with data, manipulating vulnerabilities or abnormalities in protocols and systems, or both. DoS attacks can also be generated by a large number of compromised information assets that have been turned into zombies, known as distributed denial of service (DDoS) attacks
[15][16]. Therefore, a DoS attack on a microgrid can be carried out against the accessibility of traditional power usage, preventing control over communication, computation, and information systems, endangering data integrity, and causing power outages. If the microgrid is connected to the internet, DoS attacks can cause significant power outages and have extremely harmful consequences. MGs contain a variety of measurement devices, such as smart meters, smart devices, data collectors, phase measurement units, remote terminal units, smart electronic devices, and programmable logic controllers (PLCs). These devices are sensitive to DoS attacks due to their use of internet standard protocols
[17]. For instance, PLCs, integral components of automation systems within microgrids, are responsible for controlling and monitoring various processes. However, their connection to the internet and utilization of standard protocols can introduce vulnerabilities. DoS attacks, for example, can disrupt the operation of PLCs by overwhelming them with a high volume of malicious requests, rendering them unresponsive or causing system malfunctions. It is crucial for microgrid operators and cybersecurity professionals to be aware of these vulnerabilities and implement robust security measures to mitigate potential risks. This may include implementing intrusion detection systems, access controls, secure network architectures, regular patching and updates, and ongoing monitoring and incident response protocols. By addressing these vulnerabilities, microgrids can enhance their resilience against cyberthreats and ensure the secure operation of their automation systems.
Data Framing Attacks: These are a type of cyberattack that targets communication networks. In this type of attack, the attackers attempt to deceive the devices in the network by sending fake messages that mimic the network traffic
[18][19]. These fake messages are used to distort or alter the data as they are transmitted between the devices in the network. Attackers may also send fake messages to cut off a data stream or to cause damage to a specific device. This type of attack is especially dangerous for many industrial protocols because these protocols are typically designed without security measures and use plain text for communication between devices in the network. Attackers can exploit the weak points in the communication algorithms of network devices by manipulating data through techniques such as modifying the values stored in the devices’ memory, sending fake messages, or using other methods to disrupt or disable devices
[20]. This type of attack can cause devices in the network to malfunction or even suffer physical damage
[21].
Man-in-the Middle Attacks: One of the most significant threats faced by MGs is the man-in-the-middle (MitM) attack. The MitM attack is a type of cyberattack where the attacker intercepts communication between two parties to steal or alter data
[22][23]. In the context of MGs, MitM attacks can cause significant disruptions to the energy supply chain, leading to power outages, equipment damage, and even safety hazards. The MitM attack in MGs typically involves an attacker gaining access to the communication network used to control and manage the grid’s various components. The attacker may use various methods to gain access, such as social engineering, phishing attacks, or exploiting vulnerabilities in the network infrastructure. Once the attacker gains access, they can intercept communication between the various components of the microgrid and manipulate data to their advantage
[24][25]. For instance, the attacker can intercept communication between the microgrid’s control system and the energy storage system and modify the power flow to create an overload, which can damage the equipment or cause a power outage. Similarly, the attacker can manipulate the data from the RESs to make them appear unreliable, which can cause the microgrid to switch to a more expensive and less sustainable energy source. MitM attacks in MGs can also pose a significant threat to the privacy and confidentiality of the energy data
[26]. For example, the attacker can intercept communication between the smart meters and the microgrid’s control system to gain access to the energy usage data of individual consumers. These data can be used for various purposes, such as identity theft or targeted advertising, leading to significant financial losses and privacy violations. Concludingly, the three main objectives of MiTM attacks are (1) to interrupt or modify measurements; (2) to alter smart meter data; and (3) to manipulate network traffic by the attacker. This attack technique relies on the Address Resolution Protocol (ARP) poisoning approach, and attack detection can be performed using packet evaluation techniques
[27].
Load Manipulation Attacks: These attacks aim to modify power usage of targeted loads or even to overload them. For instance, the method of load manipulation can be employed indirectly by publishing incorrect price information to customers in terms of demand response management techniques. Power loads must be protected to prevent overloading and to manage them cost-effectively
[28].
Malicious Command Injection Attack: In power grids, phase shifting transformers or phase shifters are used to control the flow of electricity. Phase shifters are used to prevent the accumulation of electrical density in transmission lines and to apply contract-based regulations. In an automatic power grid system, phase shifting commands are transmitted through the SCADA system. This situation can make the system vulnerable to cyberattacks in terms of both harmless and malicious commands being sent from the phase shifters. Malicious commands can cause serious damage, power outages, and disrupt cross-network interactions
[29].
Load Redistribution Attacks: These attacks are related to the distribution or routing of energy sources on a microgrid. This type of attack is carried out when a device with low security levels changes the flow of energy on the grid by sending fake data packets or using a predetermined strategy
[30][31]. Attackers can artificially increase energy consumption in a specific area of the grid, causing energy sources in that area to rapidly deplete. This can create a balancing issue across the entire grid, requiring other areas to be fed from different energy sources
[32]. Load redistribution attacks also allow individuals with access to energy sources to manipulate energy consumption by redirecting energy sources from one area to another. This can cause power outages in specific areas of the grid and harm electricity consumers in the affected region. The best way to counter these types of attacks is to implement appropriate mechanisms for controlling the distribution and routing of energy sources on the grid and monitoring them securely. Additionally, it is important to take appropriate security measures on each device to ensure the security of each component of the grid
[33].
Coordinated Cyberphysical Topology Attacks: Coordinated cyberphysical topology attacks (CCPT) are more dangerous for MGs than either physical topology attacks or cybertopology attacks alone
[34][35]. CCPT attacks are divided into two categories: physical topology attacks and cybertopology attacks. In a physical topology attack, the attacker cuts the transmission line, while in a cybertopology attack, the attacker deceives the control center, hides the outage signal in the cyberlayer, and creates a false outage signal for another transmission line
[36]. As a result, the most important goal of a coordinated topology attack is to overload the critical line by deceiving the control center into making incorrect dispatches
[37].
Replay Attack: A replay attack can be carried out by intercepting information in a communication network and then mimicking a legitimate sender by distributing the intercepted information to reproduce the original information
[38][39]. This type of attack relies on past data and makes it difficult for the control center to detect the attack. As a result, the attack can cause disruption in the power flow and lead to time delays at different frequencies. From the attacker’s point of view, a replay attack can intentionally disrupt the system and various processes completely
[40].
Malware Attacks: Malware is software designed to harm or disrupt computer systems, and it can be introduced into a microgrid’s system through email attachments, software updates, or infected USB drives. Once installed, malware can spread throughout the system, causing significant damage
[41][42]. Some types of malwares, such as ransomware, can encrypt the microgrid’s data and demand payment for their release, causing significant financial losses. Cyberattacks on microgrid systems can be carried out through the use of malicious software such as BlackEnergy, Stuxnet Trojan horses, or WannaCry ransomware. In December 2015, a cyberattack targeted the electricity grid in Ivano-Frankivsk, Ukraine, resulting in a power outage and directly affecting 80,000 people. It was determined that this cyberattack was created using phishing emails and the BlackEnergy Trojan horse
[43]. This attack method was observed to have the ability to delete certain types of data, damage hard disks, and control systems.
Insider Attacks: This could involve a rogue employee, contractor, or supplier who has access to the microgrid’s systems and deliberately causes harm
[44]. Such an attack could be motivated by financial gain, personal animosity, or ideological beliefs. Insider attacks can be challenging to detect, as the attacker may already have authorized access to the system.
Phishing Attacks: Phishing is another major threat to microgrid cybersecurity. Phishing is a type of social engineering attack that uses deceptive emails or other means to trick users into divulging sensitive information, such as passwords or other login credentials. Once attackers have this information, they can use it to gain unauthorized access to the microgrid system. To protect against phishing, microgrid operators should train employees to recognize and avoid phishing scams, and should implement multifactor authentication to prevent unauthorized access to critical systems
[44].
Ransomware Attacks: Ransomware is a type of malware that prevents users from accessing their own data or computer systems until a ransom is paid to the attacker
[45]. In recent years, ransomware has become a significant threat to the security of MGs. MGs are small-scale power grids that can operate independently or in conjunction with the main power grid. They typically use DERs such as solar panels and battery storage to generate and manage power. Ransomware attacks on MGs can cause significant disruptions to power supply and create safety hazards
[46][47], and they can take various forms, including locking access to control systems or preventing the delivery of electricity to customers. Attackers may also demand payment in cryptocurrency, making it difficult to track the flow of funds and apprehend the perpetrators. The consequences of a successful ransomware attack can be severe, with potential risks to human life and property. For example, an attacker could disrupt the supply of power to critical infrastructure, such as hospitals or emergency services, causing life-threatening situations. In addition, an attack on a microgrid could lead to a wider power outage affecting a larger population.
Advanced Persistent Threats: Advanced persistent threats (APTs) are a significant concern in the context of MGs as these critical infrastructures are vulnerable to cyberattacks due to their interconnected nature and the increased use of digital technologies in microgrid management systems
[48]. APTs are sophisticated and stealthy cyberattacks that are often orchestrated by state-sponsored actors, organized criminal groups, or hacker collectives
[49]. Unlike traditional cyberattacks that are aimed at exploiting vulnerabilities in software or hardware systems, APTs are designed to remain undetected for extended periods to collect sensitive data, steal intellectual property, or disrupt critical infrastructure. In the context of MGs, APTs can be devastating as they can compromise the integrity of the system, disrupt operations, and cause physical damage to the infrastructure
[50][51]. For example, an APT targeting the control system of a microgrid can lead to unauthorized access, data theft, and even physical damage to the equipment. Moreover, an APT can also be used to launch a ransomware attack, where the attacker encrypts the critical data and demands a ransom payment in exchange for the decryption key.
SQL Injection Attacks: These attacks can pose a significant threat to the cybersecurity of the system. MGs often use web applications and interfaces to monitor and control the system, and these interfaces are potential targets for SQL injection attacks. An SQL injection attack works by inserting malicious code into a web application’s input field, which is then executed by the database server
[52][53]. This code can be used to bypass authentication, retrieve sensitive data, or modify the contents of the database. In the context of MGs, a successful SQL injection attack could allow an attacker to gain control of the system, modify power flow, or even shut down the microgrid entirely
[54].
Zero-day Attacks: Zero-day exploits, also known as zero-day vulnerabilities, refer to previously unknown software vulnerabilities that hackers can exploit to launch attacks. These types of attacks are particularly concerning for MGs, as they can target critical infrastructure and cause significant damage to the system
[55][56]. Zero-day exploits are a type of cyberthreat that is difficult to defend against, as the system administrators may be unaware of the vulnerability and unable to apply a patch or update to fix it. They are a growing concern in the energy sector, and MGs are not immune to these types of attacks. In fact, as MGs become more prevalent, the likelihood of being targeted by zero-day exploits increases. This is because MGs often rely on outdated software and hardware, which can contain vulnerabilities that are not yet known to system administrators. Hackers can exploit these vulnerabilities to gain access to the microgrid system and launch attacks that can disrupt operations, cause damage to equipment, and potentially harm people
[56][57].
Physical Attacks: Physical attacks on MGs are also a significant threat to cybersecurity. These attacks could include vandalism, theft, or sabotage of the microgrid’s hardware or infrastructure
[58][59]. Physical attacks can be challenging to prevent, as they often require significant security measures and resources.
3. Strategies for Cybersecurity in MGs
MGs are small energy networks that usually provide electricity to a few consumers. These grids are important in terms of the use of RESs and energy efficiency. However, MGs are vulnerable to cyberattacks and can be manipulated by malicious actors who have access to the grid if cybersecurity measures are not taken.
Some of the crucial strategies that should be applied to ensure the security of MGs are listed below
[60][61]:
-
Encryption of communication channels: In MGs, communication between different devices is often carried out wirelessly. Therefore, encryption of communication channels is very important. Encrypting data traffic between wireless communication devices significantly reduces the risks of unauthorized access and data theft.
-
Access control: In MGs, communication between devices and systems often has an open structure, which can facilitate cyberattackers’ access to the system. Therefore, access control is important. Access control includes techniques such as authentication, authorization, and access control, and provides system access only to authenticated users and devices.
-
Device updates and patches: Devices in MGs, in addition to current software and hardware patches, should also be updated periodically to minimize cybersecurity vulnerabilities. Simultaneously performing these updates on all devices and systems helps make the system more secure.
-
Threat detection and response: Malware and other cyberthreats can spread quickly in MGs and cause serious damage. Therefore, an automatic threat detection and response system capable of detecting and monitoring threats and taking necessary measures should be established in MGs.
-
Network security: MGs can be protected with network security measures. Network security includes technologies such as firewalls, network monitoring systems, network access control, and similar measures, which help prevent malicious actors from accessing and damaging the network.
-
Identification and protection of weak points: Weak points in MGs can be a target for attackers. Therefore, identifying and protecting weak points is important in preventing attacks. This can include regular updates and patch installations, identifying and closing security vulnerabilities, encryption, and similar measures.
-
Personnel training: Personnel working in MGs should be trained on cybersecurity issues. This ensures that personnel are informed about secure practices and are knowledgeable about detecting and preventing cyberattacks.
-
Password management: Using strong and unique passwords is important in protecting MGs from cyberattacks. Passwords should be changed regularly and stored securely.
-
Emergency planning: MGs’ emergency plans should include contingency plans for a cyberattack or natural disaster. These plans should be regularly updated and tested to ensure their effectiveness in a crisis.
-
Physical security: Physical security is of great importance in MGs. Physical security involves the physical protection of devices, systems, and other hardware. Therefore, it is important to properly place devices, use mechanisms that ensure physical access control, and employ mechanisms that ensure the security of devices.
4. Vulnerability Assessment and Risk Analysis
Vulnerability assessment and risk analysis are two related but distinct processes that are often used in the field of cybersecurity to identify potential threats and vulnerabilities in computer systems, networks, and other digital assets.
Vulnerability assessment involves the systematic examination of a system or network to identify vulnerabilities that could be exploited by attackers. This can involve both automated and manual techniques, such as scanning for open ports, analyzing software configurations, and testing for known vulnerabilities in specific applications. Risk analysis, on the other hand, involves a more comprehensive examination of the potential impact of a security breach, including the likelihood of an attack occurring and the potential consequences for the organization. This can involve evaluating the value of assets that could be compromised, the cost of remediation, and the potential impact on reputation, financial stability, and legal liability
[62][63].
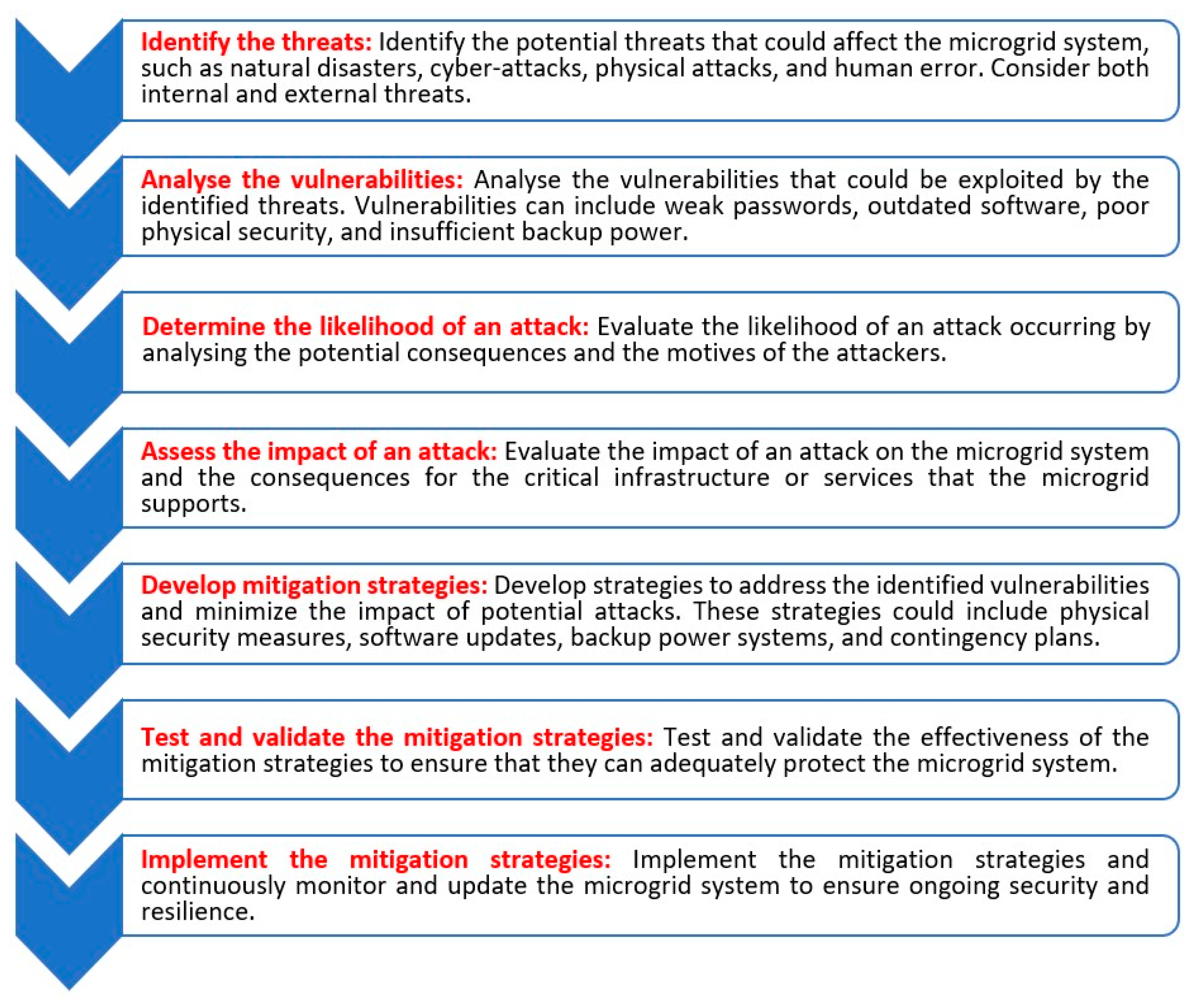
Performing a vulnerability assessment in a microgrid involves several important steps to ensure that the microgrid system is secure and resilient. This process includes identifying the assets and infrastructure that need to be assessed, identifying potential threats, analyzing vulnerabilities, evaluating the likelihood and impact of an attack, developing and implementing mitigation strategies, and continuously monitoring and updating the microgrid system to ensure ongoing security and resilience. By following these steps, a vulnerability assessment can identify potential threats and vulnerabilities, assess the impact of an attack, and develop and implement effective mitigation strategies to protect the microgrid system. Figure 2 illustrates some of the main and crucial steps to perform a vulnerability assessment in a microgrid.
Figure 2. Crucial steps to perform a vulnerability assessment in a microgrid.
In addition to vulnerability assessment, to ensure the safe and reliable operation of MGs, it is essential to perform a comprehensive risk analysis that identifies potential hazards, assesses their likelihood and impact, prioritizes risks, develops appropriate risk mitigation strategies, and monitors the effectiveness of the risk management process over time
[64][65]. As illustrated in
Figure 3, the main and crucial steps to perform a risk analysis in a microgrid includes hazard identification, likelihood assessment, impact assessment, risk prioritization, risk tolerance determination, evaluation of existing controls, development of risk mitigation strategies, implementation of risk mitigation measures, and monitoring and review. By following these steps, organizations can effectively manage risk in their MGs and ensure the continuity of critical services even in the face of unexpected events.
Figure 3. Crucial steps to perform a risk analysis in a microgrid.