The demand for clean and sustainable energy sources is increasing at a rapid pace, and microgrids (MGs) have emerged as a promising solution for achieving energy resilience, efficiency, and security. As a general definition, a microgrid is a localized power system that integrates renewable energy resources, energy storage systems, and loads to operate autonomously or in parallel with the main grid. As MGs continue to grow in popularity as a means of providing reliable and sustainable energy to communities and businesses, the issue of cybersecurity becomes increasingly important. With the use of digital technology and communication systems, MGs are vulnerable to cyberattacks that can compromise their operation and even cause physical damage.
- microgrids
- digitalization
- optimization
- cybersecurity
1. Security Vulnerabilities in MGs
| Vulnerability Type | Description | Potential Consequences |
|---|---|---|
| Attacks on field devices | Field devices are vulnerable due to limited memory and processing resources, which can be exploited by attackers. | Attackers can overwrite memory sections of field devices with incorrect values, leading to device crashes or malfunctions. |
| Backdoor or malware loaded onto command-and-control network | Malware/backdoors can be installed on the command-and-control network, providing attackers with covert access to devices or assets on the system. | Attackers can gain unauthorized access to the network and compromise the security of devices or assets. |
| Attacks on databases | Database attacks can impact system security and data collection from the field. | Attackers can update device values through the database, which may not be reflected in the human–machine interface (HMI), or affect the collection of data from the field. |
| Devices with few or no security features | Microgrid devices may lack basic security mechanisms, such as authentication or encryption. | Attackers can send control messages that disable grid devices, which are executed as there is no way to verify their validity. |
| Misconfigurations of assets | Default configurations, misconfigured assets, and using default passwords can undermine system security. | Assets that are not enabled to authenticate, or use default or hardcoded credentials, can compromise security. |
| Unsatisfactory cybersecurity procedures and training for personnel | Uneducated personnel can compromise network security by disregarding security policies and practices. | Personnel can unintentionally or intentionally disable security features or install new software that impacts the security profile of the information system. |
| Incorrect configured network | Networks that are not completely separated from the corporate network can become vulnerable to attackers. | An attacker can exploit a security vulnerability in the microgrid information system by sending a phishing email with a malicious attachment. |
| Incorrect or nonexistent patches | Incorrect or nonexistent patches can leave software and hardware vulnerable to attacks, compromising microgrid system security and reliability. | The patching process can create a risk for the system’s accessibility, affecting the security and reliability of the microgrid system. |
| Unsafe coding techniques | Inappropriate authentication, access control, and error checking can negatively impact system security. | An attacker can bypass authentication mechanisms that use device serial numbers or 16-bit authentication keys. |
| Failure to use microgrid-specific security technologies | The absence of a security technology aimed at detecting security vulnerabilities in MGs makes these systems vulnerable to attackers. | The system becomes vulnerable to attackers due to the absence of a security technology aimed at detecting security vulnerabilities in MGs. |
| Security vulnerabilities in microgrid-specific protocols | The communication protocols used in MGs are designed with little emphasis on security, making them more vulnerable to attacks. | Microgrid-specific protocols are more vulnerable to well-known attacks due to their lack of emphasis on security. |
| Unauthorized personnel access | Failure to monitor or restrict physical access to the microgrid network may result in unrestricted access to all assets in the network. | Failure to monitor or restrict physical access to the microgrid network. |
2. Threats to Microgrid Cybersecurity
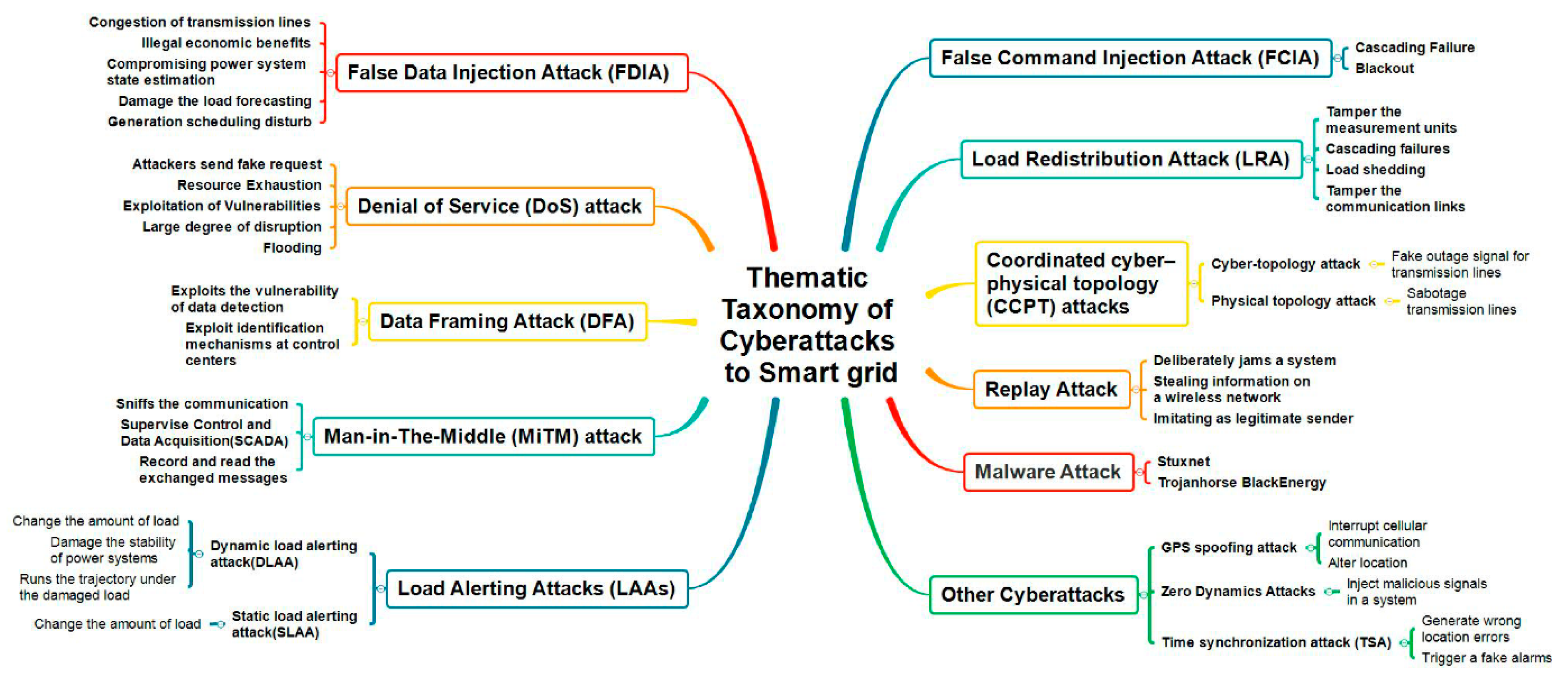
3. Strategies for Cybersecurity in MGs
-
Encryption of communication channels: In MGs, communication between different devices is often carried out wirelessly. Therefore, encryption of communication channels is very important. Encrypting data traffic between wireless communication devices significantly reduces the risks of unauthorized access and data theft.
-
Access control: In MGs, communication between devices and systems often has an open structure, which can facilitate cyberattackers’ access to the system. Therefore, access control is important. Access control includes techniques such as authentication, authorization, and access control, and provides system access only to authenticated users and devices.
-
Device updates and patches: Devices in MGs, in addition to current software and hardware patches, should also be updated periodically to minimize cybersecurity vulnerabilities. Simultaneously performing these updates on all devices and systems helps make the system more secure.
-
Threat detection and response: Malware and other cyberthreats can spread quickly in MGs and cause serious damage. Therefore, an automatic threat detection and response system capable of detecting and monitoring threats and taking necessary measures should be established in MGs.
-
Network security: MGs can be protected with network security measures. Network security includes technologies such as firewalls, network monitoring systems, network access control, and similar measures, which help prevent malicious actors from accessing and damaging the network.
-
Identification and protection of weak points: Weak points in MGs can be a target for attackers. Therefore, identifying and protecting weak points is important in preventing attacks. This can include regular updates and patch installations, identifying and closing security vulnerabilities, encryption, and similar measures.
-
Personnel training: Personnel working in MGs should be trained on cybersecurity issues. This ensures that personnel are informed about secure practices and are knowledgeable about detecting and preventing cyberattacks.
-
Password management: Using strong and unique passwords is important in protecting MGs from cyberattacks. Passwords should be changed regularly and stored securely.
-
Emergency planning: MGs’ emergency plans should include contingency plans for a cyberattack or natural disaster. These plans should be regularly updated and tested to ensure their effectiveness in a crisis.
-
Physical security: Physical security is of great importance in MGs. Physical security involves the physical protection of devices, systems, and other hardware. Therefore, it is important to properly place devices, use mechanisms that ensure physical access control, and employ mechanisms that ensure the security of devices.
4. Vulnerability Assessment and Risk Analysis
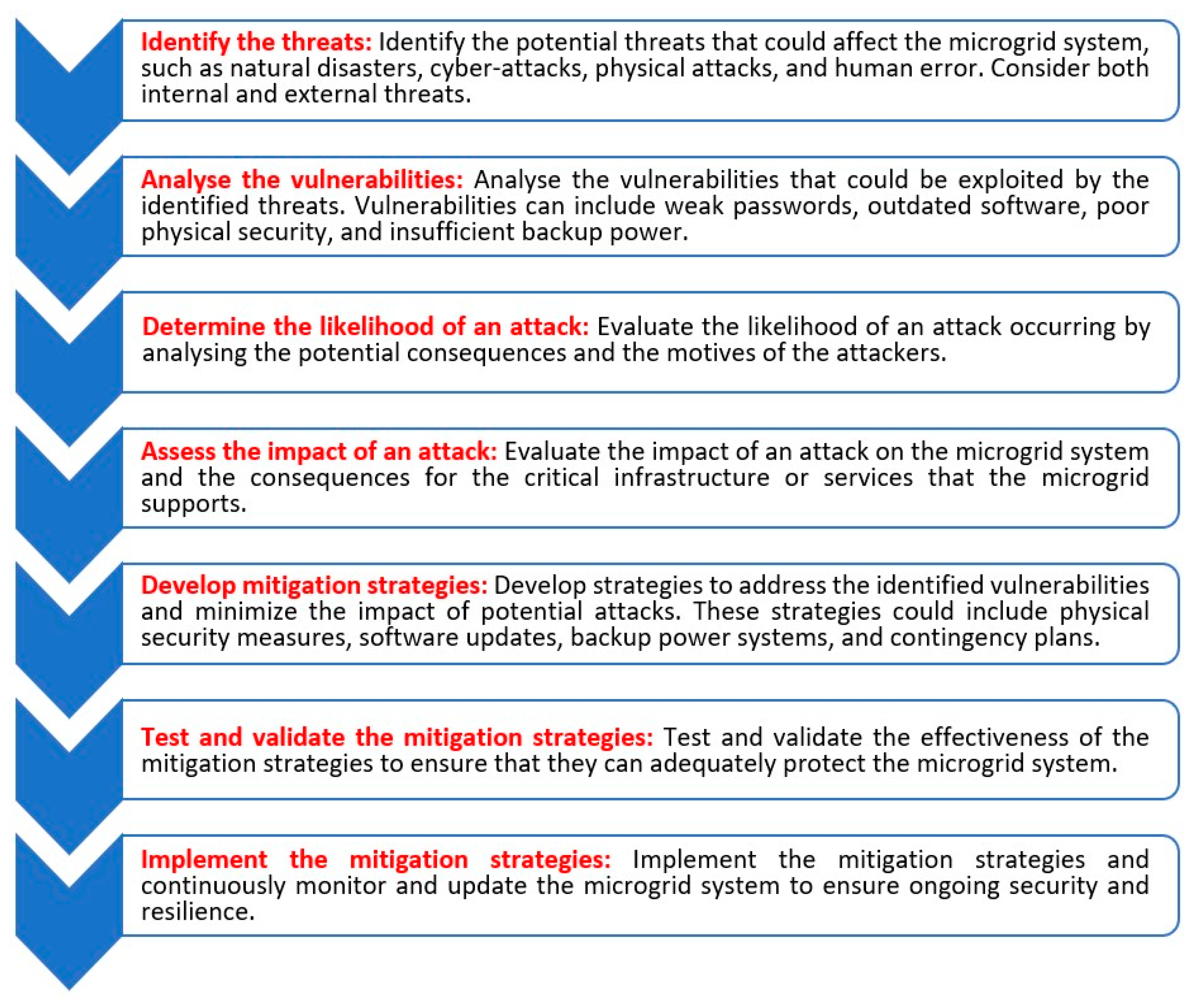

This entry is adapted from the peer-reviewed paper 10.3390/en16124590
References
- Dileep, G. A Survey on Smart Grid Technologies and Applications. Renew. Energy 2020, 146, 2589–2625.
- Kimani, K.; Oduol, V.; Langat, K. Cyber Security Challenges for IoT-Based Smart Grid Networks. Int. J. Crit. Infrastruct. Prot. 2019, 25, 36–49.
- Stouffer, K.; Pillitteri, V.; Lightman, S.; Abrams, M.; Hahn, A. Guide to Industrial Control Systems (ICS) Security; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015; p. NIST SP 800-82r2, Appendix C.
- Veitch, C.; Henry, J.; Richardson, B.; Hart, D. Microgrid Cyber Security Reference Architecture; Sandia National Lab.: Albuquerque, NM, USA, 2013; pp. SAND2013–5472, 1090210, 460305.
- Reda, H.T.; Anwar, A.; Mahmood, A. Comprehensive Survey and Taxonomies of False Data Injection Attacks in Smart Grids: Attack Models, Targets, and Impacts. Renew. Sustain. Energy Rev. 2022, 163, 112423.
- Reda, H.T.; Anwar, A.; Mahmood, A.N.; Tari, Z. A Taxonomy of Cyber Defence Strategies Against False Data Attacks in Smart Grids. ACM Comput. Surv. 2023.
- Ding, J.; Qammar, A.; Zhang, Z.; Karim, A.; Ning, H. Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions. Energies 2022, 15, 6799.
- Cao, G.; Gu, W.; Lou, G.; Sheng, W.; Liu, K. Distributed Synchronous Detection for False Data Injection Attack in Cyber-Physical Microgrids. Int. J. Electr. Power Energy Syst. 2022, 137, 107788.
- Giraldo, J.; Hariri, M.E.; Parvania, M. Decentralized Moving Target Defense for Microgrid Protection Against False-Data Injection Attacks. IEEE Trans. Smart Grid 2022, 13, 3700–3710.
- Koduru, S.S.; Machina, V.s.P.; Madichetty, S. Cyber-Attacks in Cyber Physical Microgrid Systems: A Comprehensive Review. Electr. Electron. Eng. 2023, 2023040691.
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C. False Data Injection Cyber-Attacks Detection for Multiple DC Microgrid Clusters. Appl. Energy 2022, 310, 118425.
- Barzegari, Y.; Zarei, J.; Razavi-Far, R.; Saif, M.; Palade, V. Resilient Consensus Control Design for DC Microgrids against False Data Injection Attacks Using a Distributed Bank of Sliding Mode Observers. Sensors 2022, 22, 2644.
- Hu, S.; Ge, X.; Chen, X.; Yue, D. Resilient Load Frequency Control of Islanded AC Microgrids Under Concurrent False Data Injection and Denial-of-Service Attacks. IEEE Trans. Smart Grid 2023, 14, 690–700.
- Chen, X.; Zhou, J.; Shi, M.; Chen, Y.; Wen, J. Distributed Resilient Control against Denial of Service Attacks in DC Microgrids with Constant Power Load. Renew. Sustain. Energy Rev. 2022, 153, 111792.
- Chen, X.; Hu, C.; Tian, E.; Peng, C. Event-Based Fuzzy Resilient Control of Nonlinear DC Microgrids under Denial-of-Service Attacks. ISA Trans. 2022, 127, 206–215.
- Jamali, M.; Baghaee, H.R.; Sadabadi, M.S.; Gharehpetian, G.B.; Anvari-Moghaddam, A. Distributed Cooperative Event-Triggered Control of Cyber-Physical AC Microgrids Subject to Denial-of-Service Attacks. IEEE Trans. Smart Grid 2023, 1.
- Kumar, V.; Mohanty, S.R. Chapter 1—Denial-of-Service Attack Resilient Control for Cyber Physical Microgrid System. In Microgrid Cyberphysical Systems; Subudhi, B., Ray, P.K., Eds.; Elsevier: Amsterdam, The Netherlands, 2022; pp. 1–27. ISBN 978-0-323-99910-6.
- Zuo, S.; Beg, O.A.; Lewis, F.L.; Davoudi, A. Resilient Networked AC Microgrids Under Unbounded Cyber Attacks. IEEE Trans. Smart Grid 2020, 11, 3785–3794.
- Zhuang, P.; Zamir, T.; Liang, H. Blockchain for Cybersecurity in Smart Grid: A Comprehensive Survey. IEEE Trans. Ind. Inform. 2021, 17, 3–19.
- Jiao, W.; Li, V.O.K. Support Vector Machine Detection of Data Framing Attack in Smart Grid. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–5.
- Ramakrishna, R.; Scaglione, A. Detection of False Data Injection Attack Using Graph Signal Processing for the Power Grid. In Proceedings of the 2019 IEEE Global Conference on Signal and Information Processing (GlobalSIP), Ottawa, ON, Canada, 11–14 November 2019; pp. 1–5.
- Ma, M.; Lahmadi, A.; Chrisment, I. Detecting a Stealthy Attack in Distributed Control for Microgrids Using Machine Learning Algorithms. In Proceedings of the 2020 IEEE Conference on Industrial Cyberphysical Systems (ICPS), Tampere, Finland, 10–12 June 2020; Volume 1, pp. 143–148.
- Karanfil, M.; Rebbah, D.E.; Ghafouri, M.; Kassouf, M.; Debbabi, M.; Hanna, A. Security Monitoring of the Microgrid Using IEC 62351-7 Network and System Management. In Proceedings of the 2022 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), New Orleans, LA, USA, 24–28 April 2022; pp. 1–5.
- Naderi, E.; Asrari, A. Experimental Validation of a Remedial Action via Hardware-in-the-Loop System Against Cyberattacks Targeting a Lab-Scale PV/Wind Microgrid. IEEE Trans. Smart Grid 2023, 1.
- Sahoo, S.; Dragičević, T.; Blaabjerg, F. Multilayer Resilience Paradigm Against Cyber Attacks in DC Microgrids. IEEE Trans. Power Electron. 2021, 36, 2522–2532.
- Fritz, J.J.; Sagisi, J.; James, J.; Leger, A.S.; King, K.; Duncan, K.J. Simulation of Man in the Middle Attack On Smart Grid Testbed. In Proceedings of the 2019 SoutheastCon, Huntsville, AL, USA, 11–14 April 2019; pp. 1–6.
- Wlazlo, P.; Sahu, A.; Mao, Z.; Huang, H.; Goulart, A.; Davis, K.; Zonouz, S. Man-in-the-Middle Attacks and Defence in a Power System Cyber-Physical Testbed. IET Cyber-Phys. Syst. Theory Appl. 2021, 6, 164–177.
- Amini, S.; Pasqualetti, F.; Mohsenian-Rad, H. Dynamic Load Altering Attacks Against Power System Stability: Attack Models and Protection Schemes. IEEE Trans. Smart Grid 2018, 9, 2862–2872.
- Chakrabarty, S.; Sikdar, B. Detection of Malicious Command Injection Attacks on Phase Shifter Control in Power Systems. IEEE Trans. Power Syst. 2021, 36, 271–280.
- Choeum, D.; Choi, D.-H. Vulnerability Assessment of Conservation Voltage Reduction to Load Redistribution Attack in Unbalanced Active Distribution Networks. IEEE Trans. Ind. Inform. 2021, 17, 473–483.
- Zhang, Z.J.; Bloch, M.; Saeedifard, M. Load Redistribution Attacks in Multi-Terminal DC Grids. In Proceedings of the 2022 IEEE Energy Conversion Congress and Exposition (ECCE), Detroit, MI, USA, 9–13 October 2022; pp. 1–7.
- Pinceti, A.; Sankar, L.; Kosut, O. Detection and Localization of Load Redistribution Attacks on Large-Scale Systems. J. Mod. Power Syst. Clean Energy 2022, 10, 361–370.
- Lei, J.; Gao, S.; Shi, J.; Wei, X.; Dong, M.; Wang, W.; Han, Z. A Reinforcement Learning Approach for Defending Against Multiscenario Load Redistribution Attacks. IEEE Trans. Smart Grid 2022, 13, 3711–3722.
- He, H.; Huang, S.; Liu, Y.; Zhang, T. A Tri-Level Optimization Model for Power Grid Defense with the Consideration of Post-Allocated DGs against Coordinated Cyber-Physical Attacks. Int. J. Electr. Power Energy Syst. 2021, 130, 106903.
- Poursmaeil, B.; Ravadanegh, S.N. Robust Defense Strategy Against Cyber Physical Attacks In Networked Microgrids. In Proceedings of the 2019 International Power System Conference (PSC), Tehran, Iran, 9–11 December 2019; pp. 709–715.
- Qin, C.; Zhong, C.; Sun, B.; Jin, X.; Zeng, Y. A Tri-Level Optimal Defense Method against Coordinated Cyber-Physical Attacks Considering Full Substation Topology. Appl. Energy 2023, 339, 120961.
- Zhang, J.; Sankar, L. Physical System Consequences of Unobservable State-and-Topology Cyber-Physical Attacks. IEEE Trans. Smart Grid 2016, 7, 2016–2025.
- Na, G.; Eun, Y. A Probing Signal-Based Replay Attack Detection Method Avoiding Control Performance Degradation. Int. J. Control Autom. Syst. 2022, 20, 3637–3649.
- Naha, A.; Teixeira, A.; Ahlén, A.; Dey, S. Sequential Detection of Replay Attacks. IEEE Trans. Autom. Control 2023, 68, 1941–1948.
- Abdelwahab, A.; Lucia, W.; Youssef, A. Set-Theoretic Control for Active Detection of Replay Attacks with Applications to Smart Grid. In Proceedings of the 2020 IEEE Conference on Control Technology and Applications (CCTA), Montreal, QC, Canada, 24–26 August 2020; pp. 1004–1009.
- Alsokhiry, F.; Annuk, A.; Kabanen, T.; Mohamed, M.A. A Malware Attack Enabled an Online Energy Strategy for Dynamic Wireless EVs within Transportation Systems. Mathematics 2022, 10, 4691.
- Xu, S.; Tu, H.; Xia, Y. Resilience Enhancement of Renewable Cyber–Physical Power System against Malware Attacks. Reliab. Eng. Syst. Saf. 2023, 229, 108830.
- BlackEnergy APT Attacks in Ukraine. Available online: https://www.kaspersky.com/resource-center/threats/blackenergy (accessed on 19 April 2023).
- Jamil, N.; Qassim, Q.S.; Bohani, F.A.; Mansor, M.; Ramachandaramurthy, V.K. Cybersecurity of Microgrid: State-of-the-Art Review and Possible Directions of Future Research. Appl. Sci. 2021, 11, 9812.
- Karanfil, M.; Rebbah, D.E.; Debbabi, M.; Kassouf, M.; Ghafouri, M.; Youssef, E.-N.S.; Hanna, A. Detection of Microgrid Cyberattacks Using Network and System Management. IEEE Trans. Smart Grid 2022, 1.
- Czekster, R.M.; Avritzer, A.; Menasché, D.S. Aging and Rejuvenation Models of Load Changing Attacks in Micro-Grids. In Proceedings of the 2021 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), Wuhan, China, 25–28 October 2021; pp. 17–24.
- Khalil, S.M.; Bahsi, H.; Dola, H.O.; Korõtko, T.; McLaughlin, K.; Kotkas, V. Threat Modeling of Cyber-Physical Systems—A Case Study of a Microgrid System. Comput. Secur. 2023, 124, 102950.
- Ning, B.; Xiao, L. Defense Against Advanced Persistent Threats in Smart Grids: A Reinforcement Learning Approach. In Proceedings of the 2021 40th Chinese Control Conference (CCC), Shanghai, China, 26–28 July 2021; pp. 8598–8603.
- Tian, W.; Du, M.; Ji, X.; Liu, G.; Dai, Y.; Han, Z. Honeypot Detection Strategy Against Advanced Persistent Threats in Industrial Internet of Things: A Prospect Theoretic Game. IEEE Internet Things J. 2021, 8, 17372–17381.
- Tian, W.; Ji, X.; Liu, W.; Liu, G.; Zhai, J.; Dai, Y.; Huang, S. Prospect Theoretic Study of Honeypot Defense Against Advanced Persistent Threats in Power Grid. IEEE Access 2020, 8, 64075–64085.
- Park, K.; Ahn, B.; Kim, J.; Won, D.; Noh, Y.; Choi, J.; Kim, T. An Advanced Persistent Threat (APT)-Style Cyberattack Testbed for Distributed Energy Resources (DER). In Proceedings of the 2021 IEEE Design Methodologies Conference (DMC), Bath, UK, 14–15 July 2021; pp. 1–5.
- Sheng, J. Research on SQL Injection Attack and Defense Technology of Power Dispatching Data Network: Based on Data Mining. Mob. Inf. Syst. 2022, 2022, e6207275.
- Gaggero, G.B.; Caviglia, R.; Armellin, A.; Rossi, M.; Girdinio, P.; Marchese, M. Detecting Cyberattacks on Electrical Storage Systems through Neural Network Based Anomaly Detection Algorithm. Sensors 2022, 22, 3933.
- Hasan, M.K.; Alkhalifah, A.; Islam, S.; Babiker, N.B.M.; Habib, A.K.M.A.; Aman, A.H.M.; Hossain, M.A. Blockchain Technology on Smart Grid, Energy Trading, and Big Data: Security Issues, Challenges, and Recommendations. Wirel. Commun. Mob. Comput. 2022, 2022, e9065768.
- Liu, M.; Zhao, C.; Zhang, Z.; Deng, R.; Cheng, P.; Chen, J. Converter-Based Moving Target Defense Against Deception Attacks in DC Microgrids. IEEE Trans. Smart Grid 2022, 13, 3984–3996.
- Takiddin, A.; Rath, S.; Ismail, M.; Sahoo, S. Data-Driven Detection of Stealth Cyber-Attacks in DC Microgrids. IEEE Syst. J. 2022, 16, 6097–6106.
- Salehghaffari, H.; Khodaparastan, M. Dynamic Attacks Against Inverter-Based Microgrids. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; pp. 1–5.
- Kawoosa, A.I.; Prashar, D. Cyber and Theft Attacks on Smart Electric Metering Systems: An Overview of Defenses. In Smart Electrical Grid System; CRC Press: Boca Raton, FL, USA, 2022; ISBN 978-1-00-324227-7.
- Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies 2022, 15, 6984.
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Reza Ahrabi, R. Cyber-Security of Smart Microgrids: A Survey. Energies 2021, 14, 27.
- Gunduz, M.Z.; Das, R. Cyber-Security on Smart Grid: Threats and Potential Solutions. Comput. Netw. 2020, 169, 107094.
- Luo, J.; Li, H.; Wang, S. A Quantitative Approach and Simplified Generic Transient Motor Startup Power Models for Microgrids Security Assessment. Sustain. Cities Soc. 2022, 83, 103998.
- Mishra, S.; Anderson, K.; Miller, B.; Boyer, K.; Warren, A. Microgrid Resilience: A Holistic Approach for Assessing Threats, Identifying Vulnerabilities, and Designing Corresponding Mitigation Strategies. Appl. Energy 2020, 264, 114726.
- Peng, H.; Su, M.; Li, S.; Li, C. Static Security Risk Assessment for Islanded Hybrid AC/DC Microgrid. IEEE Access 2019, 7, 37545–37554.
- Colorado, P.J.; Suppioni, V.P.; Filho, A.J.S.; Salles, M.B.C.; Grilo-Pavani, A.P. Security Assessment for the Islanding Transition of Microgrids. IEEE Access 2022, 10, 17189–17200.
