
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Inam Ullah | -- | 3890 | 2023-06-13 12:57:41 | | | |
| 2 | Lindsay Dong | + 3 word(s) | 3893 | 2023-06-15 02:46:50 | | | | |
| 3 | Lindsay Dong | Meta information modification | 3893 | 2023-06-16 08:01:13 | | |
Video Upload Options
The Internet of Things (IoT) is a well-known technology that has a significant impact on many areas, including connections, work, healthcare, and the economy. IoT has the potential to improve life in a variety of contexts, from smart cities to classrooms, by automating tasks, increasing output, and decreasing anxiety. Cyberattacks and threats, on the other hand, have a significant impact on intelligent IoT applications. Many traditional techniques for protecting the IoT are now ineffective due to new dangers and vulnerabilities. To keep their security procedures, IoT systems of the future will need artificial intelligence (AI)-efficient machine learning and deep learning. The capabilities of artificial intelligence, particularly machine and deep learning solutions, must be used if the next-generation IoT system is to have a continuously changing and up-to-date security system.
1. Introduction
2. Artificial Intelligence to Solve the IoT Security Challenges
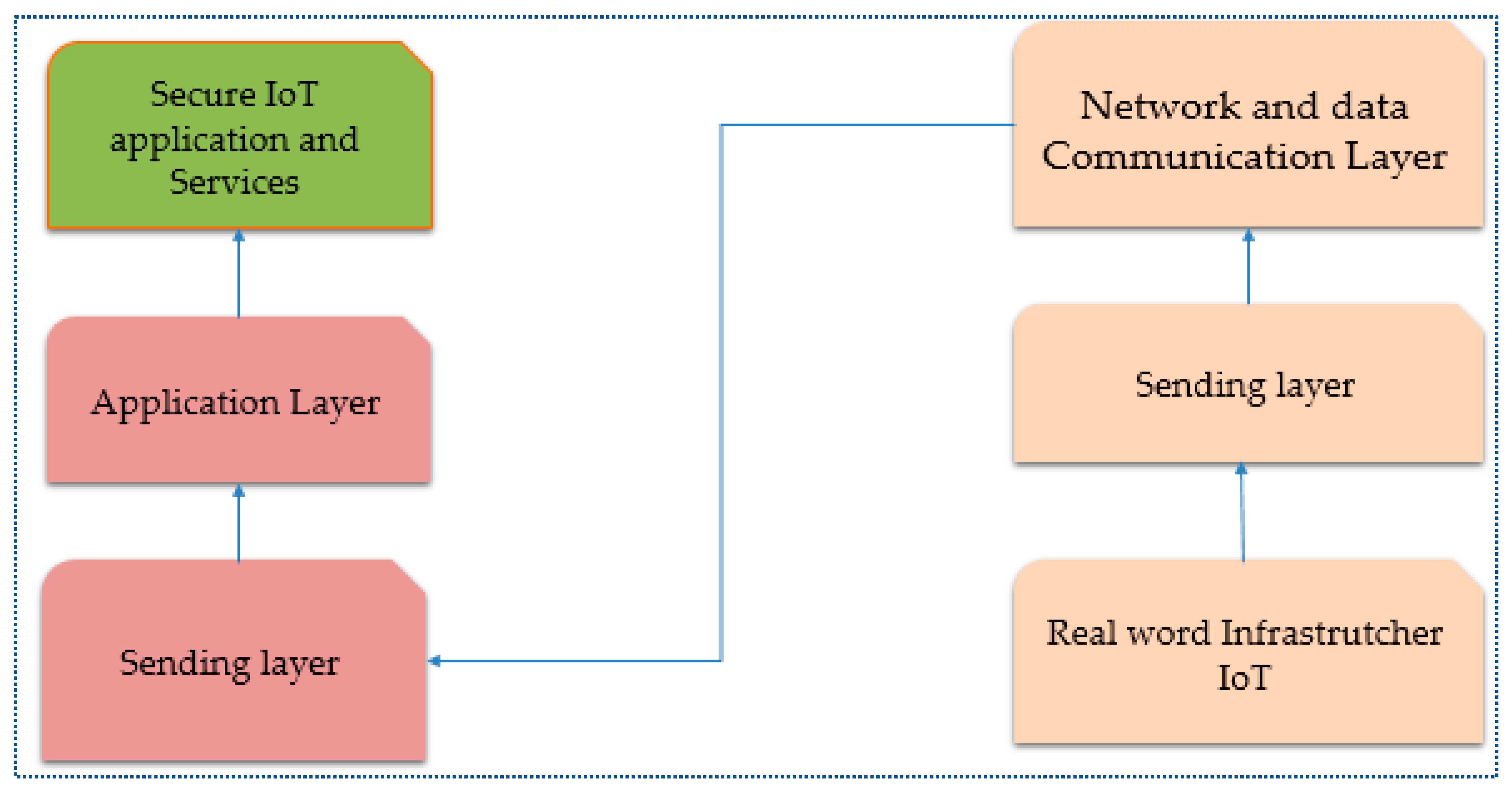
2.1. Security Issues in the Perception or Sensing Layer
2.1.1. Issues with Networking and Data Communications Layer Security
2.1.2. Security Issues in the Middleware or Support Layer
2.1.3. Application Layer
2.2. IoT Security Solutions Based on ML and DL
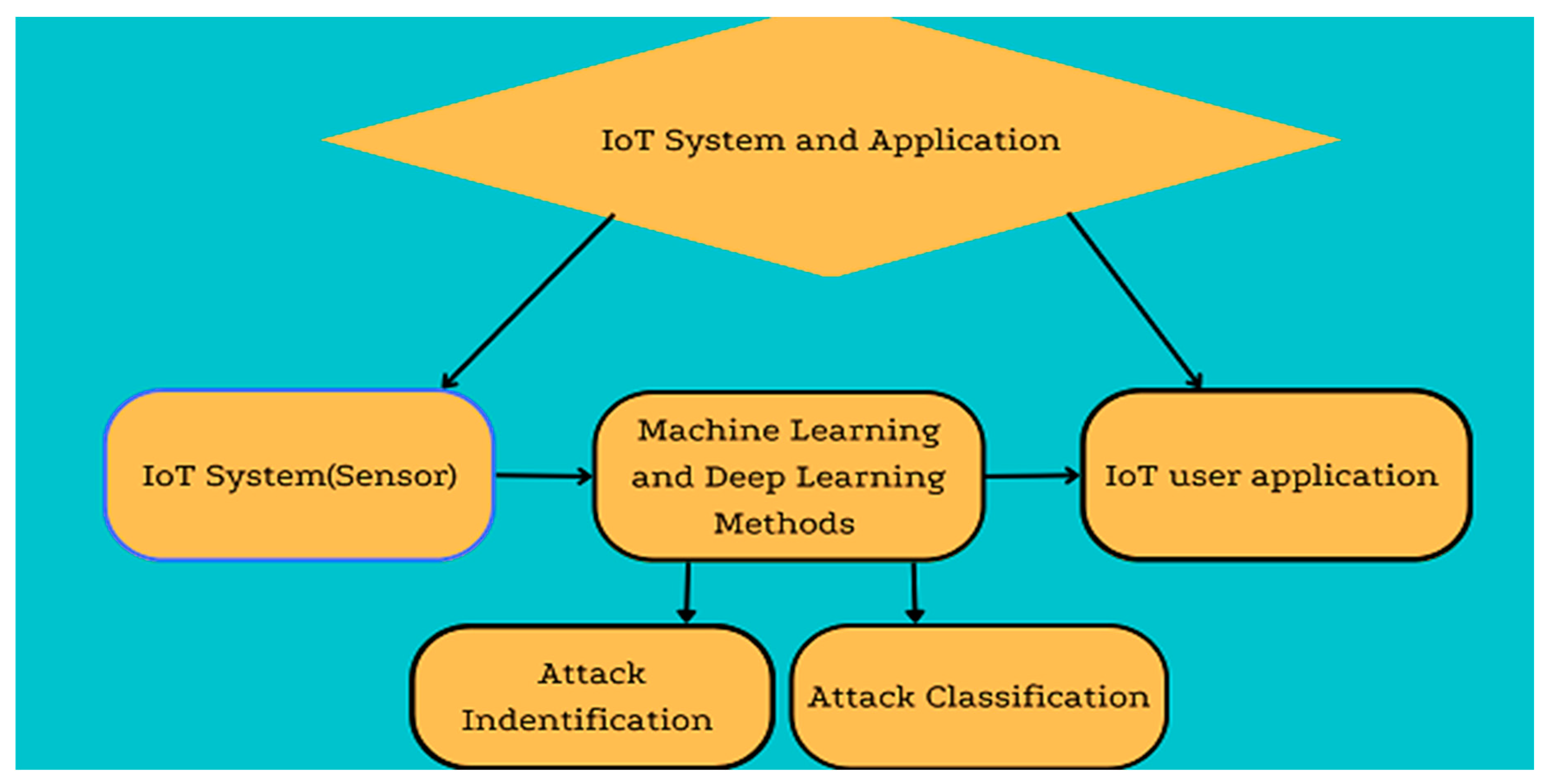
2.2.1. Classification and Regression Techniques
-
The SVM classification approach looks for unusual behavior in IoT devices and malware on Android to assure the dependability of IoT services [24].
-
Anomalies, denial-of-service assaults, IoT intrusions, and irregularities in smart cities are all detected using the random forest approach [25].
-
Two other methods for detecting abnormalities include a Naive-Bayes-based classification model and a linear-regression-based strategy for spotting malicious IoT malicious nodes [26].
- Any widely used R.T., such as linear, logistic, polynomial, and partial least-squares regression, can be used to build the quantitative security model. For instance, multiple regression analysis can create a correlation between human characteristics and how people desire to act in terms of cybersecurity [28].
2.2.2. Clustering Techniques
Clustering is a standard method of unsupervised learning used in machine learning to analyze IoT security data. It may group or cluster data points based on similarity or dissimilarity metrics of security data from IoT devices from various sources. As a result, clustering might make finding hidden patterns and structures in data easier, making it simpler to spot anomalies or attacks in the IoT. Various perspectives, such as partitioning, hierarchies, fuzzy theory, distribution, and grids, can be used to cluster data. Many well-known methods for classifying data include k-means, K-medoids, and the Gaussian mixture model [29].
2.2.3. Rule-Based Techniques
2.2.4. Optimization of Security Features and Principal Component Analysis
2.2.5. Multi-Layer Perceptron (MLP)
2.2.6. Recurrent Neural Network (RNN)
2.3. Research Issues and Directions
2.3.1. Poor Management
2.3.2. Naming and Identity Management
2.3.3. Trust Management and Policy
2.3.4. Big Data
2.3.5. Security
2.3.6. Storage
2.3.7. Authentication and Authorization
2.3.8. Secure Network
References
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743.
- Ślusarczyk, B. Industry 4.0: Are we ready? Pol. J. Manag. Stud. 2018, 17, 232–248.
- Sarker, I.H.; Kayes, A.S.M.; Badsha, S.; Alqahtani, H.; Watters, P.; Ng, A. Cybersecurity data science: An overview from machine learning perspective. J. Big Data 2020, 7, 41.
- Minerva, R.; Biru, A.; Rotondi, D. Towards a definition of the Internet of Things (IoT). IEEE Internet Initiat. 2015, 1, 1–86.
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The Effect of IoT New Features on Security and Privacy: New Threats, Existing Solutions, and Challenges Yet to Be Solved. IEEE Internet Things J. 2018, 6, 1606–1616.
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259.
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411.
- Asim, M.; Arif, M.; Rafiq, M. Applications of Internet of Things in university libraries of Pakistan: An empirical investigation. J. Acad. Libr. 2022, 48, 102613.
- Ma, Z.; Xiao, M.; Xiao, Y.; Pang, Z.; Poor, H.V.; Vucetic, B. High-Reliability and Low-Latency Wireless Communication for Internet of Things: Challenges, Fundamentals, and Enabling Technologies. IEEE Internet Things J. 2019, 6, 7946–7970.
- Albalawi, A.M.; Almaiah, M.A. Assessing and reviewing of cyber-security threats, attacks, mitigation techniques in IoT environment. J. Theor. Appl. Inf. Technol. 2022, 100, 2988–3011.
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Bashir, A.K. A survey of security and privacy issues in the Internet of Things from the layered context. Trans. Emerg. Telecommun. Technol. 2020, 33, e3935.
- Navya, P.; Rama, G.S.; Kumar, T.P.; Pasha, S.N.; Mahender, K. IoT technology: Architecture, stack, security risks, privacy risks and its applications. In Proceedings of AIP Conference Proceedings; AIP Publishing LLC.: College Park, MD, USA, 2022; p. 020062.
- Haque, A.K.M.B.; Bhushan, B.; Dhiman, G. Conceptualizing smart city applications: Requirements, architecture, security issues, and emerging trends. Expert Syst. 2021, 39, e12753.
- Zahran, S.; Elkadi, H.; Helm, W. Fog of Things Framework to Handle Data Streaming Heterogeneity on Internet of Things. In Proceedings of International Conference on Advanced Intelligent Systems and Informatics; Springer International Publishing: Cham, Switzerland, 2022; pp. 653–667.
- Rasheed, M.A.; Saleem, J.; Murtaza, H.; Tanweer, H.A.; Rasheed, M.A.; Ahmed, M. A Survey on Fog computing in IoT. VFAST Trans. Softw. Eng. 2022, 9, 4.
- Yassein, M.B.; Shatnawi, M.Q. Application layer protocols for the Internet of Things: A survey. In Proceedings of the 2016 International Conference on Engineering & MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016; pp. 1–4.
- Donta, P.K.; Srirama, S.N.; Amgoth, T.; Annavarapu, C.S.R. Survey on recent advances in IoT application layer protocols and machine learning scope for research directions. Digit. Commun. Netw. 2021, 8, 727–744.
- Kakkar, L.; Gupta, D.; Saxena, S.; Tanwar, S. IoT architectures and its security: A review. In Proceedings of the Second International Conference on Information Management and Machine Intelligence; Springer: Singapore, 2021; pp. 87–94.
- Sarker, I.H.; Khan, A.I.; Abushark, Y.B.; Alsolami, F. Internet of Things (IoT) Security Intelligence: A Comprehensive Overview, Machine Learning Solutions and Research Directions. Mob. Netw. Appl. 2022, 1–17.
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2020, 32, e4150.
- Sarker, I.H. Deep Learning: A Comprehensive Overview on Techniques, Taxonomy, Applications and Research Directions. SN Comput. Sci. 2021, 2, 420.
- Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, Security and Privacy in Machine Learning Based Internet of Things. J. Sens. Actuator Netw. 2022, 11, 38.
- Han, S.; Mannan, N.; Stein, D.C.; Pattipati, K.R.; Bollas, G.M. Classification and regression models of audio and vibration signals for machine state monitoring in precision machining systems. J. Manuf. Syst. 2021, 61, 45–53.
- Menter, Z.; Tee, W.Z.; Dave, R. Application of Machine Learning-Based Pattern Recognition in IoT Devices. In Proceedings of International Conference on Communication and Computational Technologies; Springer: Singapore, 2021; pp. 669–689.
- Meijin, L.; Zhiyang, F.; Junfeng, W.; Luyu, C.; Qi, Z.; Tao, Y.; Yinwei, W.; Jiaxuan, G. A Systematic Overview of Android Malware Detection. Appl. Artif. Intell. 2021, 36, 2007327.
- Nakip, M.; Gelenbe, E. Botnet attack detection with incremental online learning. In Proceedings of International ISCIS Security Workshop; Springer International Publishing: Cham, Switzerland, 2022; pp. 51–60.
- Ravikumar, D. Towards Enhancement of Machine Learning Techniques Using CSE-CIC-IDS2018 Cybersecurity Dataset; Rochester Institute of Technology: Rochester, NY, USA, 2021.
- Van der Schyff, K.; Flowerday, S. Mediating effects of information security awareness. Comput. Secur. 2021, 106, 102313.
- Sarker, I.H. Machine Learning for Intelligent Data Analysis and Automation in Cybersecurity: Current and Future Prospects. Ann. Data Sci. 2022, 1–26.
- Kallitsis, M.; Prajapati, R.; Honavar, V.; Wu, D.; Yen, J. Detecting and Interpreting Changes in Scanning Behavior in Large Network Telescopes. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3611–3625.
- Masum, M.H.R. IT-Security Challenges for IoT Infrastructures; Frankfurt University of Applied Sciences: Frankfurt am Main, Germany, 2022.
- Gordaliza, P.M. Computer-Aided Assessment of Tuberculosis with Radiological Imaging: From Rule-Based Methods to Deep Learning. Ph.D. Thesis, Universidad Carlos III de Madrid, Madrid, Spain, 2022.
- Júnior, E.C.; Costa, W.L.; Portela, A.L.C.; Rocha, L.S.; Gomes, R.L.; Andrade, R.M.C. Detecting Attacks and Locating Malicious Devices Using Unmanned Air Vehicles and Machine Learning. J. Internet Serv. Appl. 2022, 13, 11–20.
- Edemacu, K.; Kim, J.W. Multi-Party Privacy-Preserving Logistic Regression with Poor Quality Data Filtering for IoT Contributors. Electronics 2021, 10, 2049.
- Elghamrawy, S.M.; Lotfy, M.O.; Elawady, Y.H. An Intrusion Detection Model Based on Deep Learning and Multi-Layer Perceptron in the Internet of Things (IoT) Network. In International Conference on Advanced Machine Learning Technologies and Applications; Springer: Berlin/Heidelberg, Germany, 2022; pp. 34–46.
- Uhricek, D.; Hynek, K.; Cejka, T.; Kolar, D. BOTA: Explainable IoT Malware Detection in Large Networks; IEEE: New York, NY, USA, 2022; p. 1.
- Madhu, B.; Chari, M.V.G.; Vankdothu, R.; Silivery, A.K.; Aerranagula, V. Intrusion detection models for IOT networks via deep learning approaches. Meas. Sens. 2022, 100641.
- Gopal, S.B.; Poongodi, C.; Nanthiya, D.; Kirubakaran, T.; Logeshwar, D.; Saravanan, B.K. Autoencoder based Architecture for Mitigating Phishing URL attack in the Internet of Things (IoT) Using Deep Neural Networks. In 2022 6th International Conference on Devices, Circuits and Systems (ICDCS); IEEE: New York, NY, USA, 2022; pp. 427–431.
- Bhattacharya, S.; Ghorai, S.; Khan, A.K. Systematic Study of Detection Mechanism for Network Intrusion in Cloud, Fog, and Internet of Things Using Deep Learning. In Human-Centric Smart Computing; Springer: Berlin/Heidelberg, Germany, 2023; pp. 31–43.
- Yang, X.; Peng, G.; Zhang, D.; Lv, Y. An Enhanced Intrusion Detection System for IoT Networks Based on Deep Learning and Knowledge Graph. Secur. Commun. Netw. 2022, 2022, 4748528.
- Kumar, K.D.; Venkata Rathnam, T.; Venkata Ramana, R.; Sudhakara, M.; Poluru, R.K. Towards the Integration of Blockchain and IoT for Security Challenges in IoT. 2019. Available online: https://www.igi-global.com/chapter/towards-the-integration-of-blockchain-and-iot-for-security-challenges-in-iot/310448 (accessed on 31 December 2022).
- Thavamani, S.; Mahesh, D.; Sinthuja, U.; Manoharan, G. Crucial attacks in internet of things via artificial intelligence techniques: The security survey. In AIP Conference Proceedings; AIP Publishing LLC.: College Park, MD, USA, 2022.
- Khan, R.; Yang, Q.; Ullah, I.; Rehman, A.U.; Bin Tufail, A.; Noor, A.; Rehman, A.; Cengiz, K. 3D convolutional neural networks based automatic modulation classification in the presence of channel noise. IET Commun. 2021, 16, 497–509.
- Abideen, Z.U.; Mazhar, T.; Razzaq, A.; Haq, I.; Ullah, I.; Alasmary, H.; Mohamed, H.G. Analysis of Enrollment Criteria in Secondary Schools Using Machine Learning and Data Mining Approach. Electronics 2023, 12, 694.
- Khan, W.U.; Imtiaz, N.; Ullah, I. Joint optimization of NOMA-enabled backscatter communications for beyond 5G IoT networks. Internet Technol. Lett. 2020, 4, e265.
- Esmalifalak, M.; Liu, L.; Nguyen, N.; Zheng, R.; Han, Z. Detecting Stealthy False Data Injection Using Machine Learning in Smart Grid. IEEE Syst. J. 2017, 11, 1644–1652.
- Pourghebleh, B.; Wakil, K.; Navimipour, N.J. A Comprehensive Study on the Trust Management Techniques in the Internet of Things. IEEE Internet Things J. 2019, 6, 9326–9337.
- Hajjaji, Y.; Boulila, W.; Farah, I.R.; Romdhani, I.; Hussain, A. Big data and IoT-based applications in smart environments: A systematic review. Comput. Sci. Rev. 2021, 39, 100318.
- Stergiou, C.; Psannis, K.E.; Gupta, B.B.; Ishibashi, Y. Security, privacy & efficiency of sustainable Cloud Computing for Big Data & IoT. Sustain. Comput. Inform. Syst. 2018, 19, 174–184.
- Chui, K.T.; Liu, R.W.; Lytras, M.D.; Zhao, M. Big data and IoT solution for patient behaviour monitoring. Behav. Inf. Technol. 2019, 38, 940–949.
- Mkrttchian, V.; Gamidullaeva, L.; Finogeev, A.; Chernyshenko, S.; Chernyshenko, V.; Amirov, D.; Potapova, I. Big data and Internet of Things (IoT) technologies’ influence on higher education: Current state and future prospects. Int. J. Web-Based Learn. Teach. Technol. (IJWLTT) 2021, 16, 137–157.
- Khalil, H.; Rahman, S.U.; Ullah, I.; Khan, I.; Alghadhban, A.J.; Al-Adhaileh, M.H.; Ali, G.; ElAffendi, M. A UAV-Swarm-Communication Model Using a Machine-Learning Approach for Search-and-Rescue Applications. Drones 2022, 6, 372.
- Dehghantanha, A.; Choo, K.-K.R. Handbook of Big Data and IoT Security; Springer: Berlin/Heidelberg, Germany, 2019.
- Dwivedi, S.K.; Roy, P.; Karda, C.; Agrawal, S.; Amin, R. Blockchain-Based Internet of Things and Industrial IoT: A Comprehensive Survey. Secur. Commun. Netw. 2021, 2021, 7142048.





