The Internet of Things (IoT) is a well-known technology that has a significant impact on many areas, including connections, work, healthcare, and the economy. IoT has the potential to improve life in a variety of contexts, from smart cities to classrooms, by automating tasks, increasing output, and decreasing anxiety. Cyberattacks and threats, on the other hand, have a significant impact on intelligent IoT applications. Many traditional techniques for protecting the IoT are now ineffective due to new dangers and vulnerabilities. To keep their security procedures, IoT systems of the future will need artificial intelligence (AI)-efficient machine learning and deep learning. The capabilities of artificial intelligence, particularly machine and deep learning solutions, must be used if the next-generation IoT system is to have a continuously changing and up-to-date security system.
- internet of things
- cyberattacks
- anomalies
- deep learning
- machine learning
1. Introduction
2. Artificial Intelligence to Solve the IoT Security Challenges
2.1. Security Issues in the Perception or Sensing Layer
A conventional IoT design consists of three layers: the application layer, the network layer, and the perception layer [83][10]. However, the support or middleware layer between the network and application layers becomes more important as the significance of data processing and intelligent decision making rises. Multiple layers, including a network layer and a support layer, may be present in IoT systems. Cloud computing has been used as the underlying support layer in numerous studies of IoT systems. Various sensors and other devices make up the perception layer, sometimes called the sensing layer. This layer’s storage, processing, memory, and communication capabilities are limited. The main methods this layer secures in the IoT network are node authentication, weak encryption, and access control [84][11]. Attacks and crimes against the perceiving layer’s privacy are too common in the real world. One approach to conduct this is to take control of a node. Malicious code usage, data injection, replay assaults, and side-channel attacks are other techniques. For example, if an attacker takes over a node, it will stop sending valid network data and may even stop using the IoT security program. It is possible that the IoT application will not operate as planned if it receives terrible data or is compromised by malicious code injection. A technique called eavesdropping, also called sniffing or snooping, allows an attacker to intercept and look through data being exchanged between two devices [85][12].2.1.1. Issues with Networking and Data Communications Layer Security
The main goals of this layer are compatibility, privacy, and secrecy. At this layer, it is expected that criminal activities, including phishing, distributed denial-of-service attacks, attacks on data transit, routing attacks, identity authentication, and encryption, will occur [87][13]. This layer of the IoT is especially vulnerable to phishing attacks, which aim to obtain sensitive information such as passwords and login credentials. When an attacker or unauthorized user gains access to the IoT network while IoT apps gather and transfer sensitive data, this is characterized as an access attack, also known as a continuous advanced threat.2.1.2. Security Issues in the Middleware or Support Layer
Distributed computing solutions have been used to replace centralized cloud environments in a variety of cases, with good results in terms of performance and response time. All sent data should now be checked for accuracy, concision, and secrecy. When someone inside a network purposefully alters or steals data or information, this is known as a malicious inside attack [89][14]. By inserting malicious SQL queries into the code, SQL injection attacks are used to steal data from user services in the real world. When damage to one virtual machine spreads to another, this is a virtualization attack. With the help of cloud malware injection, a hacker can take over a cloud service, install malicious code, or even create a fake virtual machine. There could be significant consequences if attacks are so powerful that cloud infrastructure is incredibly frustrated [90][15].2.1.3. Application Layer
Defining and maintaining IoT applications, including their interactions with specific clients, fall under the scope of the application layer. One way to use IoT services is through a user interface. A computer, a smartphone, or any other Internet-enabled smart device could serve as an interface. The data that the middleware layer process is used by the application layer [91][16]. This holds for a wide range of application categories, including applications for smart homes, smart cities, industry, construction, and health. The security needs of an application may change depending on how it functions. When sending information on climate change forecasts as opposed to when conducting online banking, it is acceptable to expect a better level of security. The application layer must address various security challenges, such as attacks on access control, malicious code, programming, data leaks, service interruptions, application vulnerabilities, and software flaws [92][17]. Attacks that interrupt service, commonly referred to as “Distributed Denial of Service (DoS)” attacks, stop users from using IoT apps by sending a flood of requests to servers or networks. Threat actors could use sniffer software to monitor data being transmitted by IoT apps. Attacks that gain unauthorized access can seriously harm a system quickly by preventing users from using IoT-related services and wiping data [93][18]. Each layer of an IoT system may be vulnerable to different security flaws and attacks, as was already mentioned. Furthermore, there is a severe risk of unknown vulnerabilities. One must conduct a thorough investigation to find these hacks. Understanding artificial intelligence, especially machine learning and deep learning architectures and techniques, is an effective way to safeguard the system regarding IoT security. Figure 81 shows the layers and function of IoT architecture.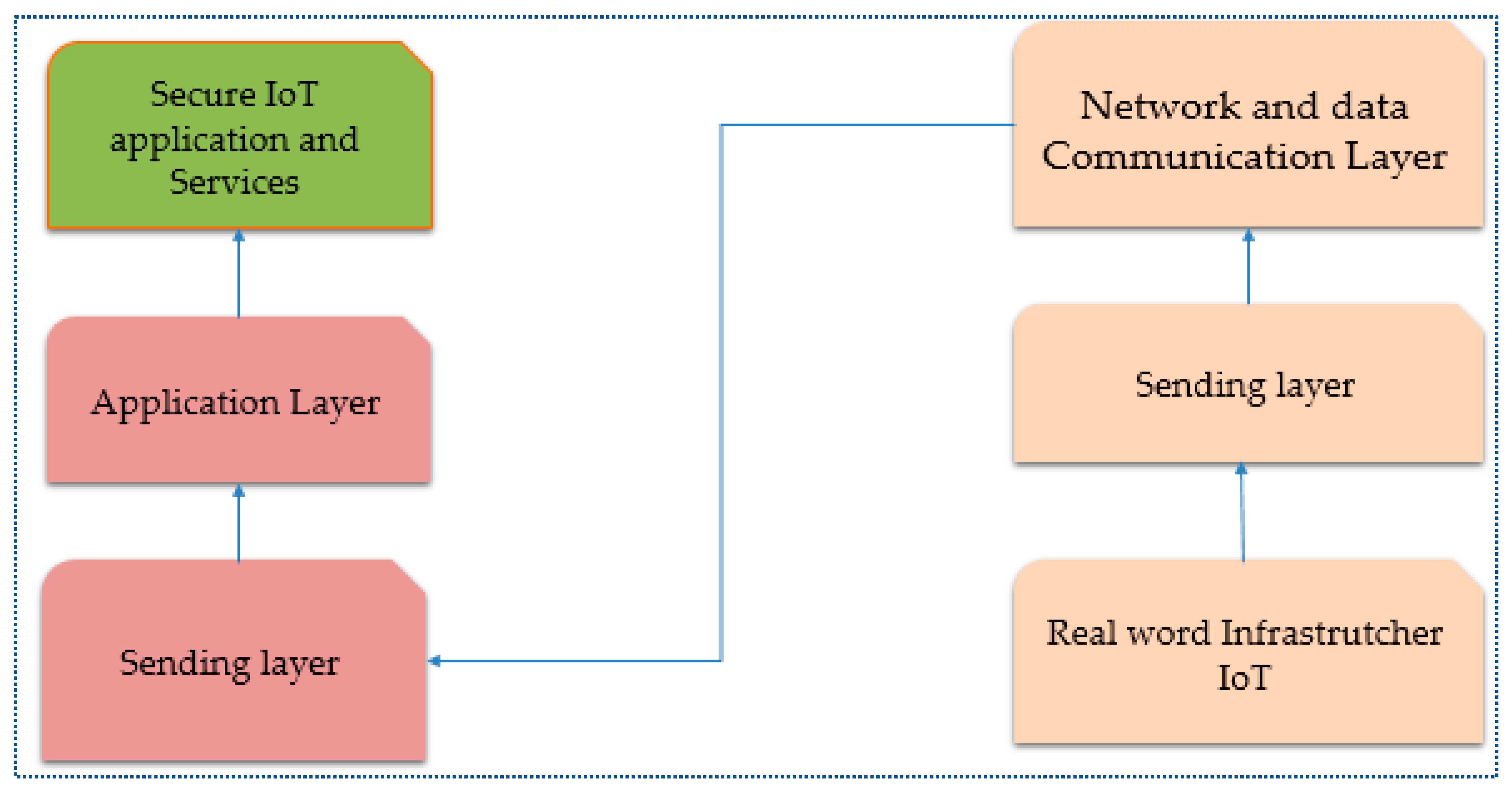
2.2. IoT Security Solutions Based on ML and DL
2.2. IoT Security Solutions Based on ML and DL
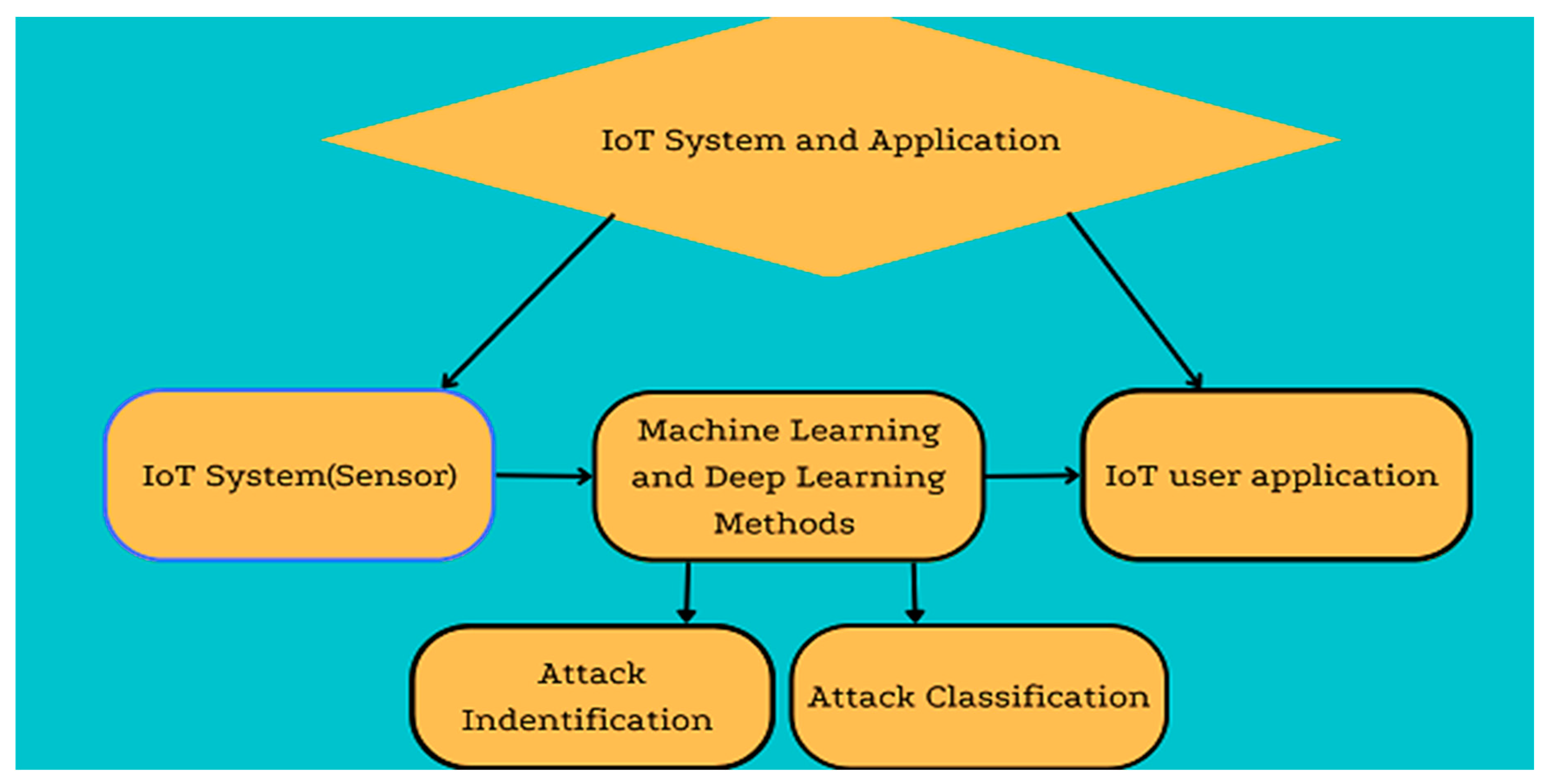
2.2.1. Classification and Regression Techniques
- Any widely used R.T., such as linear, logistic, polynomial, and partial least-squares regression, can be used to build the quantitative security model. For instance, multiple regression analysis can create a correlation between human characteristics and how people desire to act in terms of cybersecurity [28].
2.2.2. Clustering Techniques
-
Any widely used R.T., such as linear, logistic, polynomial, and partial least-squares regression, can be used to build the quantitative security model. For instance, multiple regression analysis can create a correlation between human characteristics and how people desire to act in terms of cybersecurity [110].
Clustering is a standard method of unsupervised learning used in machine learning to analyze IoT security data. It may group or cluster data points based on similarity or dissimilarity metrics of security data from IoT devices from various sources. As a result, clustering might make finding hidden patterns and structures in data easier, making it simpler to spot anomalies or attacks in the IoT. Various perspectives, such as partitioning, hierarchies, fuzzy theory, distribution, and grids, can be used to cluster data. Many well-known methods for classifying data include k-means, K-medoids, and the Gaussian mixture model [29].
2.2.3. Rule-Based Techniques
Older patterns are less likely to stand out and aid in the identification or prediction of IoT security issues than newer unfriendly behavior patterns. Selectivity analysis, which examines current practices, may be more beneficial in some cases than conventional data analysis. Another critical goal is to develop a security model for IoT devices that is based on how recently they have been used. Innovative, portable IoT device solutions that take new data trends into account are required as part of the learning-based research on IoT security [30]. By creating various links and patterns based on support and confidence values, rule-based procedures are easy to use and complicate the model. The problem might be lessened with a robust association model. A rule-learning technique that can be used to find trustworthy, non-redundant links between ideas is shown in a earlier work [31]. Policy rules in a plan define which network usage is allowed and which is not. Even cyberattacks with no known vulnerabilities can be stopped by security policy monitoring filters and protections based on rules [32].2.2.2. Clustering Techniques
2.2.4. Optimization of Security Features and Principal Component Analysis
Clustering is a standard method of unsupervised learning used in machine learning to analyze IoT security data. It may group or cluster data points based on similarity or dissimilarity metrics of security data from IoT devices from various sources. As a result, clustering might make finding hidden patterns and structures in data easier, making it simpler to spot anomalies or attacks in the IoT. Various perspectives, such as partitioning, hierarchies, fuzzy theory, distribution, and grids, can be used to cluster data. Many well-known methods for classifying data include k-means, K-medoids, and the Gaussian mixture model [111].
2.2.3. Rule-Based Techniques
Older patterns are less likely to stand out and aid in the identification or prediction of IoT security issues than newer unfriendly behavior patterns. Selectivity analysis, which examines current practices, may be more beneficial in some cases than conventional data analysis. Another critical goal is to develop a security model for IoT devices that is based on how recently they have been used. Innovative, portable IoT device solutions that take new data trends into account are required as part of our learning-based research on IoT security [114]. By creating various links and patterns based on support and confidence values, rule-based procedures are easy to use and complicate the model. The problem might be lessened with a robust association model. A rule-learning technique that can be used to find trustworthy, non-redundant links between ideas is shown in our earlier work [115]. Policy rules in a plan define which network usage is allowed and which is not. Even cyberattacks with no known vulnerabilities can be stopped by security policy monitoring filters and protections based on rules [116].2.2.4. Optimization of Security Features and Principal Component Analysis
In the current cyber threat environment, the development and optimization of security features are significant barriers to the success of an ML-based IoT security solution. Security characteristics and IoT data have a direct impact on ML-based security models, necessitating the use of a data-dimensionality-reduction technique. “Feature engineering” is the process of establishing and changing security features or variables so that machine-learning-based security models work properly. Today’s IoT security datasets may contain unused or irrelevant data, making simulation of cyberattacks and other challenges difficult [101]. The forecasting accuracy of a security model can be harmed by extreme variation, overfitting, expensive processing, and time-consuming model setup [93]. A high-dimensional dataset with many security attributes evaluated according to how important or relevant they are may make it easier to create an IoT security model [102]. Existing approaches include the correlation coefficient, the chi-squared test, and analysis of variance. Techniques for embedding information include regularization, Lasso, Ridge, Elastic Net, and tree-based feature importance [84].2.2.5. Multi-Layer Perceptron (MLP)
In the current cyber threat environment, the development and optimization of security features are significant barriers to the success of an ML-based IoT security solution. Security characteristics and IoT data have a direct impact on ML-based security models, necessitating the use of a data-dimensionality-reduction technique. “Feature engineering” is the process of establishing and changing security features or variables so that machine-learning-based security models work properly. Today’s IoT security datasets may contain unused or irrelevant data, making simulation of cyberattacks and other challenges difficult [33]. The forecasting accuracy of a security model can be harmed by extreme variation, overfitting, expensive processing, and time-consuming model setup [18]. A high-dimensional dataset with many security attributes evaluated according to how important or relevant they are may make it easier to create an IoT security model [34]. Existing approaches include the correlation coefficient, the chi-squared test, and analysis of variance. Techniques for embedding information include regularization, Lasso, Ridge, Elastic Net, and tree-based feature importance [11].Deep learning usually uses the multi-layer MLP, FFAN. The input layer, the hidden output layers, and the actual output layer are the three layers that make up the traditional M.L.P. design. An AI network links each node in a layer to a specific value in the layer below it. In the end, this number is associated with the layer below it. As the model is being built, MLP employs backpropagation to adjust the internal weight values [117][35]. This M.L.P. network is used to analyze the NSL-KDD dataset’s malware, explain the IoT parameters, detect malicious traffic coming from IoT devices, and create a model for intrusion detection [118][36]. The idea divides network data into secure data and unsecure data.2.2.5. Multi-Layer Perceptron (MLP)
2.2.6. Recurrent Neural Network (RNN)
Another variety of artificial neural networks is the recurrent neural network. A directed graph representing time is constructed from the connections between the nodes. In the R.N.N. model, neural feed-forward networks are used. It looks at its internal state, or memory, to determine how long different input sequences last. IoT security, natural language processing, and speech recognition can all benefit from the RNN model’s capabilities to manage sequential data effectively [119][37]. IoT devices that are connected provide a lot of sequential data, including information that changes over time and network traffic flows. Recurrent connections in neural networks can uncover potential defense vulnerabilities when a threat’s communication patterns change over time. This is because it has a powerful model for predicting time series because of its long short-term Memory, which allows it to remember what it has been told in the past. The detection and prevention of malware, spoofing, and computer virus attacks across a wide range of IoT devices can be made using a variety of deep learning models and hybrid network models [121][38]. One type of deep learning model that could be used to protect IoT devices is a DBN-based security model [122][39]. The authors looked at multiple approaches to in-depth learning.2.3. Research Issues and Directions
As a result, through current and future research and development, weit addresses the issues raised in this section and attempt to identify the best strategies for protecting IoT networks and devices. As a result, determining the best learning strategy for a specific IoT security scenario can be time consuming. This is conducted so that the results of various learning algorithms can differ depending on the quality of the input [84][11]. The model’s efficacy, precision, and labor requirements may be jeopardized if the incorrect learning method is used. Additionally, redundant IoT security data could lead to the gathering of irrelevant data and inaccurate conclusions. Machine learning or deep learning security models may not perform as well, be less accurate, or even be completely ineffective if the IoT data are incomplete in some way, such as by not being representative, being of poor quality, having irrelevant features, or being too small for training [134][40]. Here are a few possible future paths for study on IoT security: Because of the way the IoT works, gathering security information can be difficult. A dynamic feature of the IoT known as heterogeneity was briefly discussed. It enables the routine collection of massive amounts of data from various sources. Data collection for IoT security is difficult. When working with IoT data, it is critical to understand the data collection process [62][41]. Statistics that are inaccurate or incomplete, outliers, and other flaws may jeopardize the security of the aging process or insufficient IoT devices [122][39]. The machine learning or deep learning methodology of IoT security has a significant impact on data quality and training availability, which has a significant impact on the IoT security model. IoT environments generate a lot of security data, which are hard to manage and clean up. Learning algorithms must be improved, or new data preparation techniques must be devised for them to be helpful in IoT security [135][42]. An effective IoT security solution must include the constraints or capabilities of IoT systems and devices. A device’s ability to store, compute, process, make decisions, and communicate must therefore be balanced with security. Therefore, choosing the best machine learning or deep learning algorithms requires extensive research [136][43].42.3.1. Poor Management
Systems based on the IoT are having trouble because of poor management. The problem is that most of the time, software engineers try to figure out how to extract useful data from sensors [138][44]. They do not care how data are gathered, just that it is. It is easier for attackers to hack a system and steal sensitive user data when there is no guarantee. Developers must start concentrating on data acquisition as a result [139][45].42.3.2. Naming and Identity Management
To communicate with other components of a network, each component needs to have its own identity. Therefore, a technique for dynamically identifying each network node with a special identification must exist [140][46]. When the IoT first started, IPv4 was used to give each networked device a special identifier. Because the number of Internet of Things devices is increasing, IPv6 is used to give each one a distinct name.2.3.3. Trust Management and Policy
The idea of trust is important and complicated. It is also necessary to have scalability, dependability, strength, and availability. It goes above taking safety procedures. IoT apps ask their users for sensitive information with their permission. Therefore, a privacy guarantee is necessary. User data are protected and cannot be accessed without permission. Academics have suggested a range of strategies for improving both trust and privacy in scholarly writings. These strategies for protecting trust and privacy in IoT applications have been ineffective. These issues are currently at the forefront of research on the Internet of Things as a result [141][47].2.3.4. Big Data
Currently, billions of devices are connected to the web, forming what is known as the IoT. Huge volumes of information are being generated by these devices. IoT struggles with the transmission and processing of massive datasets. Therefore, such a system is essential in order to solve the problem of big data [142][48].2.3.5. Security
Information security implementation in the IoT is challenging. Users communicate private data to complete tasks. There are various possible opponents for user privacy. Therefore, security measures should be implemented to safeguard user data and discourage unauthorized access [143][49].2.3.6. Storage
IoT devices must also be secure to use. Sensors keep an eye on the surroundings and send the information they gather to computers. Because there is no encounter measurement, the security of data storage devices cannot be guaranteed. As a result, there needs to be a way to stop unauthorized access to or monitoring of sensitive data [144][50].2.3.7. Authentication and Authorization
User IDs can be verified using several different techniques. The most common approach is to use a login and password, but there are other options as well, such as an access card, retina scan, voice recognition, or fingerprints. Authorization can also be obtained through access control. It is a method of protecting a system by only allowing those who need access to use it. The system has become complex because it consists of so many nodes and components. The traditional methods of authentication and permission have failed in large-scale networks. Although concerns with authentication and authorization have been researched, they still need to be fixed. To solve these challenges, such an approach is necessary [145][51].2.3.8. Secure Network
Man-in-the-middle and denial-of-service attacks are only two examples of the multiple ways the transport layer of a network can be used. An attack that prevents user’s access to the targeted system, device, or network resource is known as a denial-of-service attack [146][52]. A cyberattack known as “man-in-the-middle” occurs when an attacker pretends to be a third party and transmits and detects messages between two objectives who believe they are speaking directly to one another. Therefore, a set of protections must be put in place to guarantee the security of the network layer [147][53]. Therefore, it is challenging to create new, lightweight algorithms or procedures for IoT devices without first weighing the advantages and disadvantages of current teaching techniques [148][54].
References
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743.
- Ślusarczyk, B. Industry 4.0: Are we ready? Pol. J. Manag. Stud. 2018, 17, 232–248.
- Sarker, I.H.; Kayes, A.S.M.; Badsha, S.; Alqahtani, H.; Watters, P.; Ng, A. Cybersecurity data science: An overview from machine learning perspective. J. Big Data 2020, 7, 41.
- Minerva, R.; Biru, A.; Rotondi, D. Towards a definition of the Internet of Things (IoT). IEEE Internet Initiat. 2015, 1, 1–86.
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The Effect of IoT New Features on Security and Privacy: New Threats, Existing Solutions, and Challenges Yet to Be Solved. IEEE Internet Things J. 2018, 6, 1606–1616.
- Li, S.; Xu, L.D.; Zhao, S. The internet of things: A survey. Inf. Syst. Front. 2015, 17, 243–259.
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411.
- Asim, M.; Arif, M.; Rafiq, M. Applications of Internet of Things in university libraries of Pakistan: An empirical investigation. J. Acad. Libr. 2022, 48, 102613.
- Ma, Z.; Xiao, M.; Xiao, Y.; Pang, Z.; Poor, H.V.; Vucetic, B. High-Reliability and Low-Latency Wireless Communication for Internet of Things: Challenges, Fundamentals, and Enabling Technologies. IEEE Internet Things J. 2019, 6, 7946–7970.
- Albalawi, A.M.; Almaiah, M.A. Assessing and reviewing of cyber-security threats, attacks, mitigation techniques in IoT environment. J. Theor. Appl. Inf. Technol. 2022, 100, 2988–3011.
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Bashir, A.K. A survey of security and privacy issues in the Internet of Things from the layered context. Trans. Emerg. Telecommun. Technol. 2020, 33, e3935.
- Navya, P.; Rama, G.S.; Kumar, T.P.; Pasha, S.N.; Mahender, K. IoT technology: Architecture, stack, security risks, privacy risks and its applications. In Proceedings of AIP Conference Proceedings; AIP Publishing LLC.: College Park, MD, USA, 2022; p. 020062.
- Haque, A.K.M.B.; Bhushan, B.; Dhiman, G. Conceptualizing smart city applications: Requirements, architecture, security issues, and emerging trends. Expert Syst. 2021, 39, e12753.
- Zahran, S.; Elkadi, H.; Helm, W. Fog of Things Framework to Handle Data Streaming Heterogeneity on Internet of Things. In Proceedings of International Conference on Advanced Intelligent Systems and Informatics; Springer International Publishing: Cham, Switzerland, 2022; pp. 653–667.
- Rasheed, M.A.; Saleem, J.; Murtaza, H.; Tanweer, H.A.; Rasheed, M.A.; Ahmed, M. A Survey on Fog computing in IoT. VFAST Trans. Softw. Eng. 2022, 9, 4.
- Yassein, M.B.; Shatnawi, M.Q. Application layer protocols for the Internet of Things: A survey. In Proceedings of the 2016 International Conference on Engineering & MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016; pp. 1–4.
- Donta, P.K.; Srirama, S.N.; Amgoth, T.; Annavarapu, C.S.R. Survey on recent advances in IoT application layer protocols and machine learning scope for research directions. Digit. Commun. Netw. 2021, 8, 727–744.
- Kakkar, L.; Gupta, D.; Saxena, S.; Tanwar, S. IoT architectures and its security: A review. In Proceedings of the Second International Conference on Information Management and Machine Intelligence; Springer: Singapore, 2021; pp. 87–94.
- Sarker, I.H.; Khan, A.I.; Abushark, Y.B.; Alsolami, F. Internet of Things (IoT) Security Intelligence: A Comprehensive Overview, Machine Learning Solutions and Research Directions. Mob. Netw. Appl. 2022, 1–17.
- Ahmad, Z.; Khan, A.S.; Shiang, C.W.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2020, 32, e4150.
- Sarker, I.H. Deep Learning: A Comprehensive Overview on Techniques, Taxonomy, Applications and Research Directions. SN Comput. Sci. 2021, 2, 420.
- Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, Security and Privacy in Machine Learning Based Internet of Things. J. Sens. Actuator Netw. 2022, 11, 38.
- Han, S.; Mannan, N.; Stein, D.C.; Pattipati, K.R.; Bollas, G.M. Classification and regression models of audio and vibration signals for machine state monitoring in precision machining systems. J. Manuf. Syst. 2021, 61, 45–53.
- Menter, Z.; Tee, W.Z.; Dave, R. Application of Machine Learning-Based Pattern Recognition in IoT Devices. In Proceedings of International Conference on Communication and Computational Technologies; Springer: Singapore, 2021; pp. 669–689.
- Meijin, L.; Zhiyang, F.; Junfeng, W.; Luyu, C.; Qi, Z.; Tao, Y.; Yinwei, W.; Jiaxuan, G. A Systematic Overview of Android Malware Detection. Appl. Artif. Intell. 2021, 36, 2007327.
- Nakip, M.; Gelenbe, E. Botnet attack detection with incremental online learning. In Proceedings of International ISCIS Security Workshop; Springer International Publishing: Cham, Switzerland, 2022; pp. 51–60.
- Ravikumar, D. Towards Enhancement of Machine Learning Techniques Using CSE-CIC-IDS2018 Cybersecurity Dataset; Rochester Institute of Technology: Rochester, NY, USA, 2021.
- Van der Schyff, K.; Flowerday, S. Mediating effects of information security awareness. Comput. Secur. 2021, 106, 102313.
- Sarker, I.H. Machine Learning for Intelligent Data Analysis and Automation in Cybersecurity: Current and Future Prospects. Ann. Data Sci. 2022, 1–26.
- Kallitsis, M.; Prajapati, R.; Honavar, V.; Wu, D.; Yen, J. Detecting and Interpreting Changes in Scanning Behavior in Large Network Telescopes. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3611–3625.
- Masum, M.H.R. IT-Security Challenges for IoT Infrastructures; Frankfurt University of Applied Sciences: Frankfurt am Main, Germany, 2022.
- Gordaliza, P.M. Computer-Aided Assessment of Tuberculosis with Radiological Imaging: From Rule-Based Methods to Deep Learning. Ph.D. Thesis, Universidad Carlos III de Madrid, Madrid, Spain, 2022.
- Júnior, E.C.; Costa, W.L.; Portela, A.L.C.; Rocha, L.S.; Gomes, R.L.; Andrade, R.M.C. Detecting Attacks and Locating Malicious Devices Using Unmanned Air Vehicles and Machine Learning. J. Internet Serv. Appl. 2022, 13, 11–20.
- Edemacu, K.; Kim, J.W. Multi-Party Privacy-Preserving Logistic Regression with Poor Quality Data Filtering for IoT Contributors. Electronics 2021, 10, 2049.
- Elghamrawy, S.M.; Lotfy, M.O.; Elawady, Y.H. An Intrusion Detection Model Based on Deep Learning and Multi-Layer Perceptron in the Internet of Things (IoT) Network. In International Conference on Advanced Machine Learning Technologies and Applications; Springer: Berlin/Heidelberg, Germany, 2022; pp. 34–46.
- Uhricek, D.; Hynek, K.; Cejka, T.; Kolar, D. BOTA: Explainable IoT Malware Detection in Large Networks; IEEE: New York, NY, USA, 2022; p. 1.
- Madhu, B.; Chari, M.V.G.; Vankdothu, R.; Silivery, A.K.; Aerranagula, V. Intrusion detection models for IOT networks via deep learning approaches. Meas. Sens. 2022, 100641.
- Gopal, S.B.; Poongodi, C.; Nanthiya, D.; Kirubakaran, T.; Logeshwar, D.; Saravanan, B.K. Autoencoder based Architecture for Mitigating Phishing URL attack in the Internet of Things (IoT) Using Deep Neural Networks. In 2022 6th International Conference on Devices, Circuits and Systems (ICDCS); IEEE: New York, NY, USA, 2022; pp. 427–431.
- Bhattacharya, S.; Ghorai, S.; Khan, A.K. Systematic Study of Detection Mechanism for Network Intrusion in Cloud, Fog, and Internet of Things Using Deep Learning. In Human-Centric Smart Computing; Springer: Berlin/Heidelberg, Germany, 2023; pp. 31–43.
- Yang, X.; Peng, G.; Zhang, D.; Lv, Y. An Enhanced Intrusion Detection System for IoT Networks Based on Deep Learning and Knowledge Graph. Secur. Commun. Netw. 2022, 2022, 4748528.
- Kumar, K.D.; Venkata Rathnam, T.; Venkata Ramana, R.; Sudhakara, M.; Poluru, R.K. Towards the Integration of Blockchain and IoT for Security Challenges in IoT. 2019. Available online: https://www.igi-global.com/chapter/towards-the-integration-of-blockchain-and-iot-for-security-challenges-in-iot/310448 (accessed on 31 December 2022).
- Thavamani, S.; Mahesh, D.; Sinthuja, U.; Manoharan, G. Crucial attacks in internet of things via artificial intelligence techniques: The security survey. In AIP Conference Proceedings; AIP Publishing LLC.: College Park, MD, USA, 2022.
- Khan, R.; Yang, Q.; Ullah, I.; Rehman, A.U.; Bin Tufail, A.; Noor, A.; Rehman, A.; Cengiz, K. 3D convolutional neural networks based automatic modulation classification in the presence of channel noise. IET Commun. 2021, 16, 497–509.
- Abideen, Z.U.; Mazhar, T.; Razzaq, A.; Haq, I.; Ullah, I.; Alasmary, H.; Mohamed, H.G. Analysis of Enrollment Criteria in Secondary Schools Using Machine Learning and Data Mining Approach. Electronics 2023, 12, 694.
- Khan, W.U.; Imtiaz, N.; Ullah, I. Joint optimization of NOMA-enabled backscatter communications for beyond 5G IoT networks. Internet Technol. Lett. 2020, 4, e265.
- Esmalifalak, M.; Liu, L.; Nguyen, N.; Zheng, R.; Han, Z. Detecting Stealthy False Data Injection Using Machine Learning in Smart Grid. IEEE Syst. J. 2017, 11, 1644–1652.
- Pourghebleh, B.; Wakil, K.; Navimipour, N.J. A Comprehensive Study on the Trust Management Techniques in the Internet of Things. IEEE Internet Things J. 2019, 6, 9326–9337.
- Hajjaji, Y.; Boulila, W.; Farah, I.R.; Romdhani, I.; Hussain, A. Big data and IoT-based applications in smart environments: A systematic review. Comput. Sci. Rev. 2021, 39, 100318.
- Stergiou, C.; Psannis, K.E.; Gupta, B.B.; Ishibashi, Y. Security, privacy & efficiency of sustainable Cloud Computing for Big Data & IoT. Sustain. Comput. Inform. Syst. 2018, 19, 174–184.
- Chui, K.T.; Liu, R.W.; Lytras, M.D.; Zhao, M. Big data and IoT solution for patient behaviour monitoring. Behav. Inf. Technol. 2019, 38, 940–949.
- Mkrttchian, V.; Gamidullaeva, L.; Finogeev, A.; Chernyshenko, S.; Chernyshenko, V.; Amirov, D.; Potapova, I. Big data and Internet of Things (IoT) technologies’ influence on higher education: Current state and future prospects. Int. J. Web-Based Learn. Teach. Technol. (IJWLTT) 2021, 16, 137–157.
- Khalil, H.; Rahman, S.U.; Ullah, I.; Khan, I.; Alghadhban, A.J.; Al-Adhaileh, M.H.; Ali, G.; ElAffendi, M. A UAV-Swarm-Communication Model Using a Machine-Learning Approach for Search-and-Rescue Applications. Drones 2022, 6, 372.
- Dehghantanha, A.; Choo, K.-K.R. Handbook of Big Data and IoT Security; Springer: Berlin/Heidelberg, Germany, 2019.
- Dwivedi, S.K.; Roy, P.; Karda, C.; Agrawal, S.; Amin, R. Blockchain-Based Internet of Things and Industrial IoT: A Comprehensive Survey. Secur. Commun. Netw. 2021, 2021, 7142048.
