
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Xianfeng Zhang | -- | 1370 | 2022-09-22 11:42:36 | | | |
| 2 | Vivi Li | -5 word(s) | 1365 | 2022-09-23 02:45:51 | | |
Video Upload Options
Early detection of people’s suspicious behaviors can aid in the prevention of crimes and make the community safer. Existing methods are mostly focused on identifying abnormal behaviors from video surveillance that are based on computer vision, which are more suitable for detecting ongoing behaviors. Due to advances in positioning technology and the increasing number of cameras, smart mobile terminals, and WLAN networks, large amounts of fine-grained personal trajectory data are collected. Such a large number of trajectories provide people with an unprecedented opportunity to automatically discover helpful knowledge, such as identifying suspicious movements and unusual activities. Therefore, crimes can be prevented if people’s suspicious behaviors can be automatically detected by mining the semantic information that is hidden in the trajectory data.
1. Introduction
2. Detection of Abnormal Trajectories Based on Outlier Detection
3. Abnormal Behavior Detection Based on Trajectory Analysis
A total of 215 incidents of access to important areas, 130 loitering incidents, 136 incidents of aimlessly wandering, 104 frequent short stops, 592 unusual visit locations, 229 unusual routes, 220 unusual visit times, and 1 crowd gathering behavior were detected in the TucityLife dataset, the accuracies of detecting the access to important areas, loitering, aimlessly wandering, frequent short stops, and crowd gathering were verified; the results are listed in Table 1. History-based suspicious behaviors must be analyzed using long-term historical information, which are easily mislabeled in an activity log; therefore, the unusual visit location and visit time were not checked for accuracy. The accuracy of detecting the unusual routes was verified by manually comparing the regular route clusters with the unusual route; the precision is shown in Table 1. The recall rate of all the six suspicious behaviors is 93.5%, and the precision is 87.6%; the recall and precision of the individual categories are relatively high. Comparative experiments (Figure. 1) show that researchers' method outperforms the compared methods in detecting all three suspicious behaviors. By analyzing the detected results, researchers found that the compared method cannot effectively identify discontinuous loitering behaviors in detecting loitering, such as leaving briefly. In the detection of aimlessly wandering and unusual route behaviors, the comparison methods were more sensitive to the noise. The results show that the proposed method could detect suspicious behaviors hidden in the massive trajectory data, providing decision support for the early detection of safety incidents. Identifying the possible offenders and potential target places in advance will play an essential role in urban safety management
Table 1. Accuracies of the detection algorithms for the suspicious behaviors
|
Type of suspicious behaviors |
Number of logged behaviors |
Number of detected behaviors |
Number of correctly detected behaviors |
Recall |
Precision |
F1-score |
|
Access to important areas |
215 |
215 |
205 |
0.953 |
0.953 |
0.953 |
|
Loitering |
123 |
130 |
118 |
0.959 |
0.908 |
0.933 |
|
Aimlessly wandering |
120 |
136 |
106 |
0.883 |
0.779 |
0.828 |
|
Frequent short stops |
93 |
104 |
86 |
0.925 |
0.827 |
|
|
Unusual route |
- |
229 |
198 |
- |
0.865 |
- |
|
Crowd gathering |
1 |
1 |
1 |
1.000 |
1.000 |
1.000 |
|
Total |
- |
815 |
714 |
0.935 |
0.876 |
0.905 |
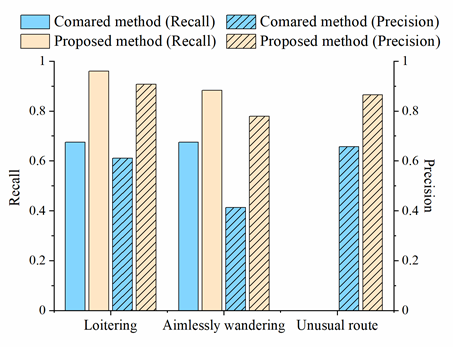
Figure 1. Comparison of the accuracy of different methods in suspicious behavior detection
References
- Kalaiselvi Geetha, M.; Arunnehru, J.; Geetha, A. Early recognition of suspicious activity for crime prevention. In Computer Vision: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2018; pp. 2139–2165.
- Bartoli, G.; Fantacci, R.; Gei, F.; Marabissi, D.; Micciullo, L. A novel emergency management platform for smart public safety: A Novel Emergency Management Platform. Int. J. Commun. Syst. 2015, 28, 928–943.
- Meijer, A.; Wessels, M. Predictive Policing: Review of Benefits and Drawbacks. Int. J. Public Adm. 2019, 42, 1031–1039.
- GNR Safe Residence Program. Available online: https://www.safecommunitiesportugal.com/regional/algarve/gnr-safe-residence-program/ (accessed on 4 July 2022).
- Capital Watch: What Is Suspicious Behavior? Available online: https://mpdc.dc.gov/whatssuspicious (accessed on 4 July 2022).
- Pareek, P.; Thakkar, A. A survey on video-based Human Action Recognition: Recent updates, datasets, challenges, and applications. Artif. Intell. Rev. 2020, 54, 2259–2322.
- Chen, Z.; Cai, H.; Zhang, Y.; Wu, C.; Mu, M.; Li, Z.; Sotelo, M.A. A novel sparse representation model for pedestrian abnormal trajectory understanding. Expert Syst. Appl. 2019, 138, 112753.
- Clarke, R.V.; Cornish, D.B. Modeling Offenders’ Decisions: A Framework for Research and Policy. Crime Justice 1985, 6, 147–185.
- Cohen, L.E.; Felson, M. Social Change and Crime Rate Trends: A Routine Activity Approach. Am. Sociol. Rev. 1979, 44, 588–608.
- Wortley, R. Situational precipitators of crime. In Environmental Criminology and Crime Analysis; Routledge: London, UK, 2016; pp. 81–105.
- Vandeviver, C.; Neirynck, E.; Bernasco, W. The foraging perspective in criminology: A review of research literature. Eur. J. Criminol 2021, 1–27.
- Bernasco, W.; Johnson, S.D.; Ruiter, S. Learning where to offend: Effects of past on future burglary locations. Appl. Geogr. 2015, 60, 120–129.
- McCue, C. Data Mining and Predictive Analysis: Intelligence Gathering and Crime Analysis, 2nd ed.; Butterworth-Heinemann: Oxford, UK, 2015.
- Yan, Z.; Chakraborty, D.; Parent, C.; Spaccapietra, S.; Aberer, K. Semantic trajectories: Mobility data computation and annotation. ACM Trans. Intell. Syst. Technol. (TIST) 2013, 4, 49.
- Mazimpaka, J.D.; Timpf, S. Trajectory data mining: A review of methods and applications. J. Spat. Inf. Sci. 2016, 13, 61–99.
- Shen, M.; Liu, D.-R.; Shann, S.-H. Outlier detection from vehicle trajectories to discover roaming events. Inf. Sci. 2015, 294, 242–254.
- Wu, H.; Tang, X.; Wang, Z.; Wang, N. Uncovering abnormal behavior patterns from mobility trajectories. Sensors 2021, 21, 3520.
- Belhadi, A.; Djenouri, Y.; Lin, J.C.-W. Comparative Study on Trajectory Outlier Detection Algorithms. In Proceedings of the 2019 International Conference on Data Mining Workshops (ICDMW), Beijing, China, 8–11 November 2019; pp. 415–423.
- Yao, D.; Zhang, C.; Zhu, Z.; Huang, J.; Bi, J. Trajectory clustering via deep representation learning. In Proceedings of the 2017 International Joint Conference on Neural Networks (IJCNN), Anchorage, AK, USA, 14–19 May 2017; pp. 3880–3887.
- Wang, Y.; Qin, K.; Chen, Y.; Zhao, P. Detecting anomalous trajectories and behavior patterns using hierarchical clustering from Taxi GPS Data. ISPRS Int. J. Geo-Inf. 2018, 7, 25.
- Shaikh, S.A.; Kitagawa, H. Efficient distance-based outlier detection on uncertain datasets of Gaussian distribution. World Wide Web 2013, 17, 511–538.
- Shi, H.; Xu, X.; Fan, Y.; Zhang, C.; Peng, Y. An Auto Encoder Network Based Method for Abnormal behavior detection. In Proceedings of the ACM International Conference Proceeding Series, Yokohama, Japan, 16–18 January 2021; pp. 243–251.
- Ahmed, U.; Srivastava, G.; Djenouri, Y.; Lin, J.C.-W. Knowledge graph based trajectory outlier detection in sustainable smart cities. Sustain. Cities Soc. 2022, 78, 103580.
- Pang, G.; Shen, C.; Cao, L.; Hengel, A.V.D. Deep Learning for Anomaly Detection: A Review. ACM Comput. Surv. 2021, 54, 38.




