Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Farhan Amin | -- | 1401 | 2022-06-25 04:12:53 | | | |
| 2 | Conner Chen | -150 word(s) | 1251 | 2022-06-27 04:50:27 | | | | |
| 3 | Conner Chen | Meta information modification | 1251 | 2022-07-04 11:01:49 | | | | |
| 4 | Conner Chen | -1 word(s) | 1250 | 2022-07-04 11:04:21 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Ali, A.; Mateen, A.; Hanan, A.; Amin, F. Advanced Security Framework for Internet of Things. Encyclopedia. Available online: https://encyclopedia.pub/entry/24469 (accessed on 07 February 2026).
Ali A, Mateen A, Hanan A, Amin F. Advanced Security Framework for Internet of Things. Encyclopedia. Available at: https://encyclopedia.pub/entry/24469. Accessed February 07, 2026.
Ali, Abid, Abdul Mateen, Abdul Hanan, Farhan Amin. "Advanced Security Framework for Internet of Things" Encyclopedia, https://encyclopedia.pub/entry/24469 (accessed February 07, 2026).
Ali, A., Mateen, A., Hanan, A., & Amin, F. (2022, June 25). Advanced Security Framework for Internet of Things. In Encyclopedia. https://encyclopedia.pub/entry/24469
Ali, Abid, et al. "Advanced Security Framework for Internet of Things." Encyclopedia. Web. 25 June, 2022.
Copy Citation
Due to the massive accessibility and interconnection of IoT devices, systems are at risk of being exploited by hackers. Therefore, there is a need to find an advanced security framework that covers data security, data confidentiality, and data integrity issues.
Internet of Things
data availability
1. Introduction
The twenty-first century is known as the era of interconnectivity and wireless communication where the world has witnessed some major technological revolutions in computer networking. The term Internet of Things (IoT) was coined by Kevin Ashton in 1999 [1]. The IoT provides a way of connectivity of things to things. The “thing” refers to all the things around us that are connected to the network. For example, the household appliances at home that are connected to the internet. IoT technology is used to share information and generate useful information between “things”. It can operate without human intervention. The IoT concept is illustrated in Figure 1.
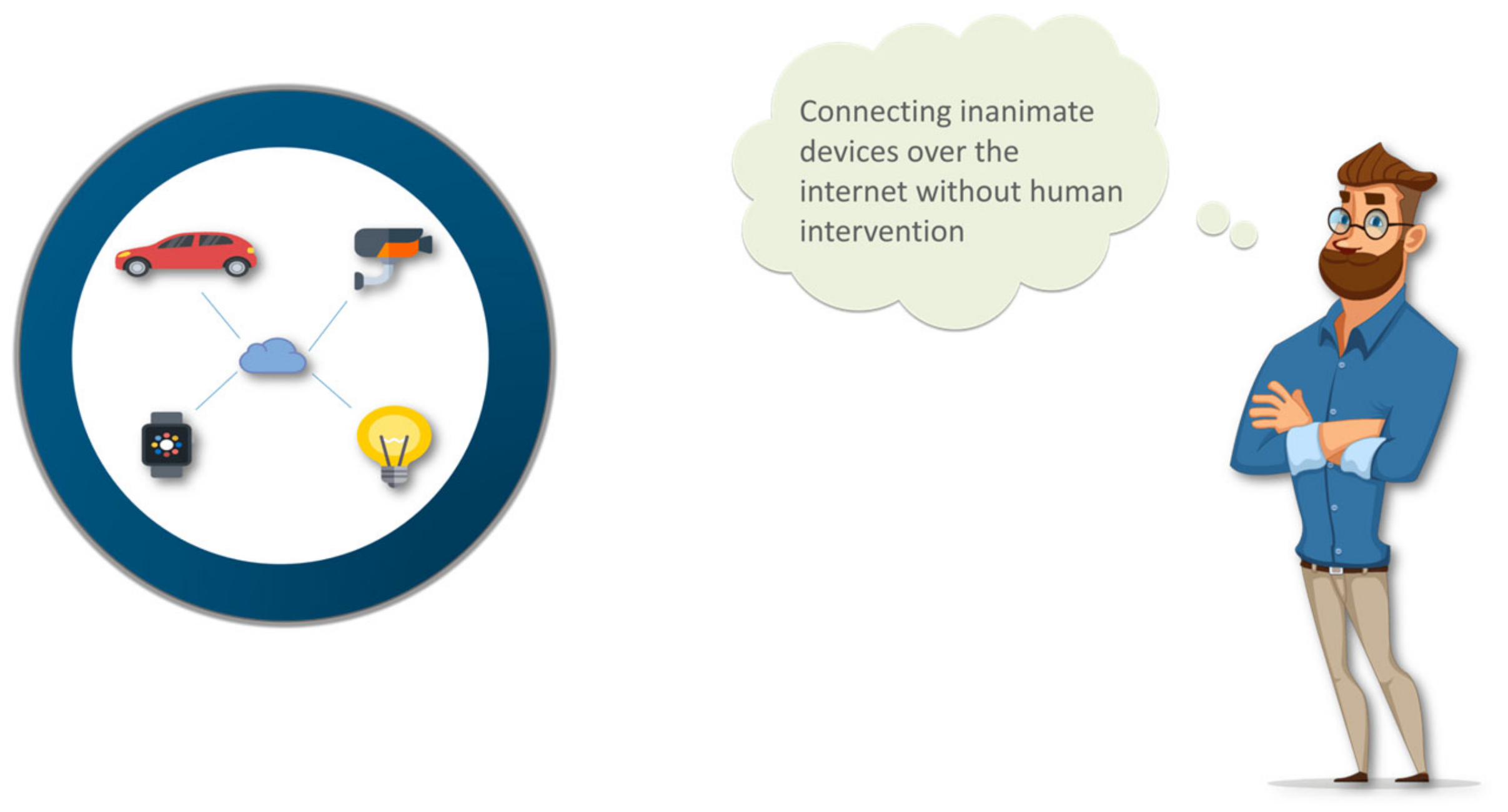
Figure 1. The concept of the Internet of Things.
In this Figure, the things are connected without human intervention. The traditional role of human command has been overpowered by the analytical capability of the IoT. Mobile phones, actuators, transceivers, protocol stacks, and microcontrollers have been developed to provide a firm connection and communication through the IoT. The data are collected and transmitted back to these devices with certain commands. The automated actions are made based on these suggested commands. The concepts of the IoT have been updated to improve the current Internet infrastructure to advanced network infrastructure, and have brought a technological revolution to the IT industry. The concept of the IoT suggests some interconnection between devices that include the facility of device autonomy, contextual awareness, sensing capability, and so on. To implement the IoT platform, many technologies and sensors, such as radiofrequency identifiers and networks of wireless sensors, are being used nowadays. However, in a conventional Internet protocol (IP), the security mechanisms need to be extended and modified to support IoT applications. The current IoT architecture is usually divided into three layers: the perception layer, the network layer, and the application layer. Figure 2 illustrates this architecture. The other forms are four-layer, five-layer, and seven-layer architecture, etc. However, using the three-layer architecture for illustration. The interaction of the sensors, actuators, and edge devices is the key part of this layer. The perception layer is used to identify the objects, perceive objects, collect information, and automatic control. This layer contains different types of control modules and collecting devices, such as the sound sensors, the temperature and pressure sensors, vibration sensors, etc., as shown in Figure 2. The perception layer is further divided into two parts: the perception node (controllers and sensors, etc.) and the perception network (transportation communication network) [2]. The use of the perception layer is to control data and data acquisition, while the perception network sends control instructions to the controller. The perception layers include implantable medical devices (IMDs), Global Positioning Systems (GPS), implantable medical devices (IMDs), Radio Frequency Identification (RFI), etc. The identification of abnormal sensor nodes is the one of security issues. It occurs when the node is attacked physically (e.g., destroyed or disabled). In general, these nodes are also known as faulty nodes. To ensure the standards of service, it is necessary to detect the fault codes and overcome the causes of lower standard services [3][4]. Another security concern of the perception layer is the key management mechanism and cryptography algorithms. For node authentication, public keys have been considered convenient. It is better to secure the entire network without any management protocol of complicated keys and to have large scalability [5]. According to [6], the most promising candidates for wireless sensor networks are three low-power public key encryption algorithms, namely, Rabin’s Scheme, Ntru Encrypt, and the Elliptic Curve Cryptography. The network layer mainly realizes the transmission of information, routing (deciding the way of information transmission), and control (how to control the transmission of information). It is divided into two parts; one part is the communication technology and the other is the communication protocol of the Internet of Things. Communication technology is responsible for physically linking things with things to enable them to communicate. The communication protocol is responsible for establishing communication rules [7]. The application layer provides users with professional services and functional data processing and storage [8]. It has the support of the cloud and servers for the storage of data in the network. Our study is more focused on the aspect of data security in the IoT. The key data security aspects are given below:
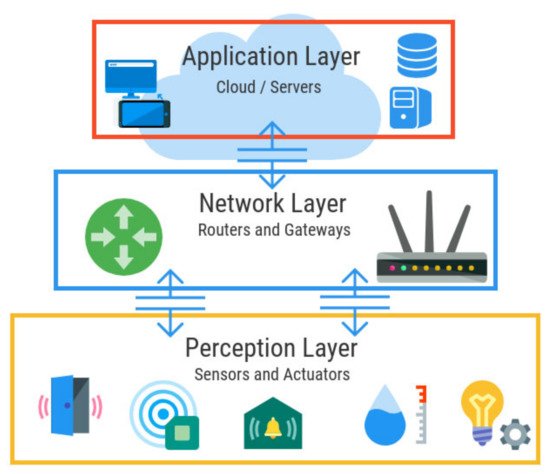
Figure 2. A three-tier IoT.
2. Data Security in IoT
Currently, data security and privacy protection should be adopted equally to offer robust data security. Accessing and securing data by a static approach has become unacceptable because it fails to address the scalable data security IoT [5]. The security support is not always maintained. Consumer knowledge of IoT security is weak: security incidents can be difficult to detect or to resolve for usage [9].
3. Data Integrity in the IoT
Data integrity is necessary for up-to-date and accurate data. It is very important to store data by any person or organization for integrity [10]. It is significant that data integrity in the IoT is measured, as data need to be secure and every transaction of data needs to be secure. Defining the integrity of data is easy but it is hard to ensure.
4. Data Confidentiality in the IoT
To keep data private in the public domain is called ‘data privacy’. Data privacy terms can be applied to any organization or a person. Data are always limited and related to any person’s life and existence [11]. He or she can keep the data private or public. An organization can also keep its data private, such as for financial statement reports or business plans. If there is no framework available for establishing personal privacy, then the privacy of any individual is very limited [12][13]. Data security and data privacy are used in many situations in the same context, but there is a distinct difference; data security is broadly thought to be about protection and saving your data from other unknown persons, whereas data privacy is to control where your data are collected, shared, and used for which, and for what, purpose.
5. Data Validity in the IoT
Data validity ensures that IoT services are practically available. If these services are unavailable, total progress can be decreased; it will also facilitate and provide help to hackers and attackers who are working in different smart industries, smart cities, and smart home etc. [6]. With the development of connected objects, users entrust part of their privacy to improve their environment and make their living environment more efficient and safer. There are risks to the person and his data; for example, a hacked surveillance camera lets you know if the owner is away or not from their home; a smart electricity meter: the meter can quickly become a spy if you are not careful [14].
6. Current IoT Security Framework
- It consists of sensors, actuators, and other embedded systems [15].
- Fog set of connections: A class of exchange ideas, technologies, and protocols by several IoT policies with the prerequisite to expand and enforce an entire confidence policy [16].
- Core Complex: It provides a set of connection center platforms and IoT devices. The issues at this time are individuals confronted with conventional fundamental networks [17]. The measureless number of endpoints act together and get by to create a considerable precautions burden. Thus, based on the suggestions made in previous research papers, the current study proposes a security framework for the IoT in terms of data confidentiality, availability, and integrity.
References
- Amin, F.; Abbasi, R.; Rehman, A.; Choi, G.S. An Advanced Algorithm for Higher Network Navigation in Social Internet of Things Using Small-World Networks. Sensors 2019, 19, 2007.
- Qian, Y.; Jiang, Y.; Chen, J.; Zhang, Y.; Song, J.; Zhou, M.; Pustišek, M. Towards decentralized IoT security enhancement: A blockchain approach. Comput. Electr. Eng. 2018, 72, 266–273.
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Futur. Gener. Comput. Syst. 2019, 100, 144–164.
- Amin, F.; Choi, G.S. Hotspots Analysis Using Cyber-Physical-Social System for a Smart City. IEEE Access 2020, 8, 122197–122209.
- Kumar, N.M.; Mallick, P.K. The Internet of Things: Insights into the building blocks, component interactions, and architecture layers. Procedia Comput. Sci. 2018, 132, 117–119.
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Security and Privacy in the Medical Internet of Things: A Review. Secur. Commun. Netw. 2018, 2018, 5978636.
- Jose, D.V.; Vijyalakshmi, A. An Overview of Security in Internet of Things. Procedia Comput. Sci. 2018, 143, 744–748.
- Yang, A.; Li, Y.; Kong, F.; Wang, G.; Chen, E. Security Control Redundancy Allocation Technology and Security Keys Based on Internet of Things. IEEE Access 2018, 6, 50187–50196.
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q. Internet-of-Things security and vulnerabilities: Taxonomy, challenges, and practice. J. Hardw. Syst. Secur. 2018, 2, 97–110.
- Javaid, U.; Aman, M.N.; Sikdar, B. Blockpro: Blockchain based data provenance and integrity for secure IoT environments. In Proceedings of the ACM Blocksys 2018, New York, NY, USA, 4 November 2018; pp. 13–18.
- El-Hajj, M.; Chamoun, M.; Fadlallah, A.; Serhrouchni, A. Analysis of authentication techniques in Internet of Things (IoT). In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–13.
- Huang, Q.; Yang, Y.; Wang, L. Secure Data Access Control with Ciphertext Update and Computation Outsourcing in Fog Computing for Internet of Things. IEEE Access 2017, 5, 12941–12950.
- Sahmim, S.; Gharsellaoui, H. Privacy and security in internet-based computing: Cloud computing, internet of things, cloud of things: A review. Procedia Comput. Sci. 2017, 112, 1516–1522.
- Meddeb, M.; Dhraief, A.; Belghith, A.; Monteil, T.; Drira, K.; Alahmadi, S. Cache Freshness in Named Data Networking for the Internet of Things. Comput. J. 2018, 61, 1496–1511.
- Angin, P.; Mert, M.B.; Mete, O.; Ramazanli, A.; Sarica, K.; Gungoren, B. A Blockchain-Based Decentralized Security Architecture for IoT. In Proceedings of the International Conference on Internet of Things, Seattle, WA, USA, 25–30 June 2018.
- Aman, M.N.; Sikdar, B.; Chua, K.C.; Ali, A. Low Power Data Integrity in IoT Systems. IEEE Internet Things J. 2018, 5, 3102–3113.
- Amin, F.; Choi, G.S. Advanced Service Search Model for Higher Network Navigation Using Small World Networks. IEEE Access 2021, 9, 70584–70595.
More
Information
Subjects:
Computer Science, Software Engineering
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.5K
Entry Collection:
Remote Sensing Data Fusion
Revisions:
4 times
(View History)
Update Date:
04 Jul 2022
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




