A FANET is a hybrid model of VANET (vehicular ad hoc networks) and a mobile ad-hoc network (MANET). In FANETs, UAVs are the network nodes, and the peer-to-peer communication model is used in communication. FANETs, MANETs, and VANETs have many similar properties. However, there are also some significant variances. These characteristics make FANETs incredibly fast-moving and capable of coping with various 3D environments. The FANET’s changing structure and hostile surroundings make networking and communication difficult
[1][2]. While in the air, the nodes have a clear line of sight and are pretty far apart. UAVs have limited resources (batteries, processing power, and bandwidth), which also hampers UAVs working efficiency. UAVs need to devise a communication system with minimal routing overhead, high throughput, and little processing complexity to make the most reliable working model
[2]. Researchers can see that communication in an ad-hoc network can be accomplished via various methods. There are three main types of routing: proactive, reactive, and cluster-based. Routes to other nodes in the network are preserved in routing tables in proactive routing. Each time a message is exchanged, a new routing table is created. Researchers can see a FANETS network in
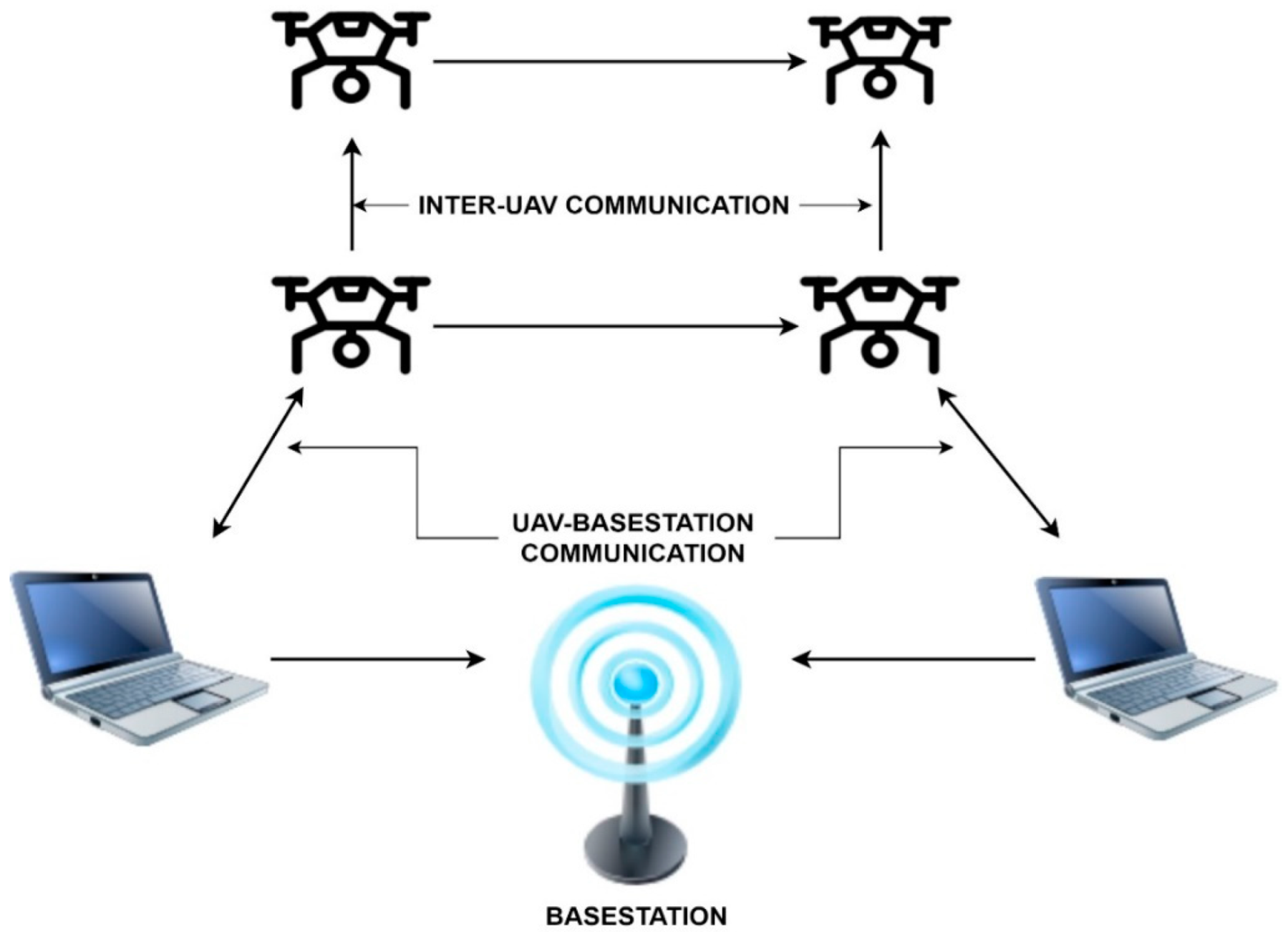
Figure 1 used for monitoring and searching applications.
On the other hand, reactive routing protocols do not keep track of the routing table. Every time a node needs to communicate data, it searches for a new route. It helps to find a new path once the present one is disrupted
[2][3]. When nodes constantly move around, maintaining the current routing table or finding a new way is a substantial communication overhead. Network throughput is cut down, extra delays are brought in, and the limited battery power of the UAV is wasted as a result of these communication overheads
[4]. There is a solution to the problem of limited resources in FANETS, which is clustering. Clustering is a method for grouping nodes based on their geographic location. It contributes to the network’s scalability, efficiency, and throughput
[4][5] as the UAVs’ energy consumption will be reduced due to the minimal routing overhead. There is a cost associated with clustering, although it is substantially lower than the cost of the other approaches. When a network is clustered, it is broken down into several distinct groups or clusters
[6][7]. There is a leader or “cluster head” (CH) for each cluster, which is in charge of communication between clusters and inside clusters, as seen in
Figure 1. CH serves as a first-hop node that takes the message to its final destination to facilitate routing
[8].
Cluster creation and maintenance consume some of the computational network radio resources. In the early stages of cluster development, nodes communicate information about their immediate area, including node ID, location, residual energy, etc. are computed. Control messages are used to provide this information to other nodes. As a result, a portion of the network’s radio resources is dedicated to clustering
[8]. A CH is elected in each cluster during network clustering, where nodes can execute calculations to organize neighboring nodes into clusters. The development of clusters and the selection of CHs are critical to the stability of the cluster structure
[6][7]. It is possible to alter the design of a cluster by repositioning cluster members (CMs). It is imperative that each CH regularly broadcasts its presence to its CMs and that each CM responds with its current status so that any changes to the cluster structure may be tracked. The radio resources of the network are also used for this cluster maintenance signaling. Overhead for cluster creation and maintenance is defined as transposing of control messages. In addition to using radio resources (such as channel bandwidth), this overhead is also a drain on the UAVs’ energy. A clustering model’s performance is evaluated using several parameters, including the cluster’s lifespan and building time
[4][9]. As the cluster’s life span increases, the model’s ability to save money and time increases. Clustering algorithms significantly impact a network’s performance, and to ensure the cluster’s long-term viability, the CHs must be carefully chosen. Networks may be divided into clusters using artificial intelligence algorithms
[10]. The fundamental downside of these strategies is their high computing complexity, which prevents them from providing the best outcomes. They take too long to get to the best possible work
[7]. Clustering in FANETs cannot be carried out using costly approaches due to the dynamic nature of the environment and the low processing capability of UAVs. UAV energy usage is also heavily influenced by transmission power options. Transmission power and energy use go hand in hand. SNs will use more energy if researchers choose a transmission power of either high or low
[4]. Transmission power should not be as high as possible while not as low as possible to minimize energy wastage.
Evolutionary algorithms (EA) are based on the theory of biological evolution. EA includes genetic algorithms/programming, evolutionary techniques, and learning classifier systems. When other strategies fail, evolutionary algorithms can provide a viable alternative. Evolutionary approaches are frequently accepted when faced with issues that seem impossible
[8][11] to solve. Even if EA is computationally costly, a near-optimal solution to an unsolved case is acceptable. Node clustering using evolutionary algorithms may be carried out well in FANETS and VANETS systems. To identify a solution to the problem, an environment will be created that allows for the evolution of viable solutions
[12]. It is feasible to find the best possible solution for the issues related to building environments through these biological algorithms. Nodes are aggregated, and their geographic locations are shared to tackle the scalability problem. Load balancing ensures that resources are effectively used in each cluster. One of the best clustering methods is the moth flame optimizer, which provides the ideal number of clusters. Insects that resemble butterflies are called moths and currently, there are about 16,000 moth species known to science. The larvae of moths, as with those of other insects, develop into cocoons as they mature. Moths fly at night and use the moonlight to find their way around
[13]. An intelligent moth flame optimization-based clustering for FANET was developed to reduce energy consumption and expand the coverage area of SNs. Researchers proposes EECP-MFO, which employs a moth flame and a variation of the K-Means Density clustering method to choose CHs for usage in a distributed computing environment. K-Means Density is utilized in conjunction with the MFO algorithm for the first selection of centroids/CH. The original K-Means Density algorithm only considers one parameter, namely the degree of the neighborhood
[13]. However, the EECP-MFO algorithm considers two additional factors, namely the energy level and the distance between the neighbors, to select the ideal CH. EECP-MFO extends the lifetime of a cluster while simultaneously reducing its energy usag
[14][15][16]. It also saves energy by efficiently choosing the transmission power of nodes according to operational needs, reducing the network load
[16][17][18][19]. In terms of cluster construction time, cluster longevity, the chance of success
[20][21][22][23][24], and energy consumption, EECP-MFO beats the ant colony optimizatio
[17][20], PSO-particle swarm optimization
[18], and grey wolf optimization-based clustering models
[14][25].
2. FANETS
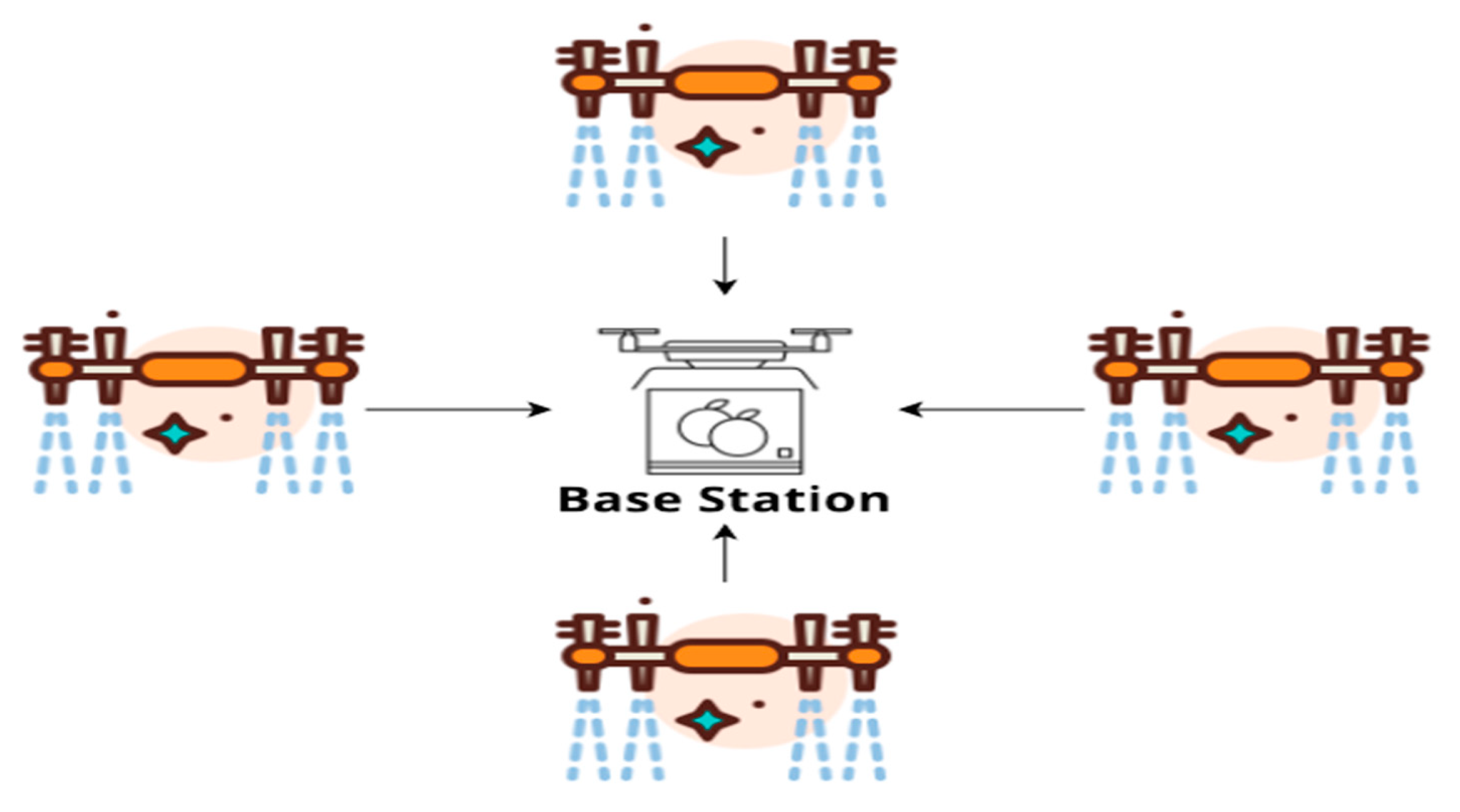
An unmanned aerial system (UAS) comprises small unmanned aerial vehicles (UAVs) that are small in size, flexible, and quick to deploy, as seen in Figure 2.
Figure 2. FANETS structure.
When a single UAV is employed, a star topology network is present where the UAV is at the center. A ground node can indirectly connect with other ground nodes via the UAV
[19][20]. On the other hand, single UAV systems have specific complex challenges in peer-to-peer communication
[26], such as decreasing interference, improving transmission range, and transmitting more data to multiple UAV systems
[27] .
The use of high gain directional antennas, rather than omnidirectional antennas, can be found as one of the possible solutions to these issues
[21]. If the UAV or a sensor/hardware fails in a single UAV system, the UAV should return to its home base to be repaired or replaced
[5]. The fault tolerance of a multi-UAV system is increased since other UAVs may share duties among themselves, which raises the overall fault tolerance of the system. It is feasible to take advantage of the capabilities of other UAVs while working with a heterogeneous UAV cluster
[22] . FANET is also considered a component of the VANET network. Due to the excellent mobility of nodes in FANETs networks, conventional routing methods are also not practical in FANETs and do not offer sufficient throughput
[19][20][21]. FANET topologies change significantly more often than MANETs or vehicle ad hoc networks, which is typical
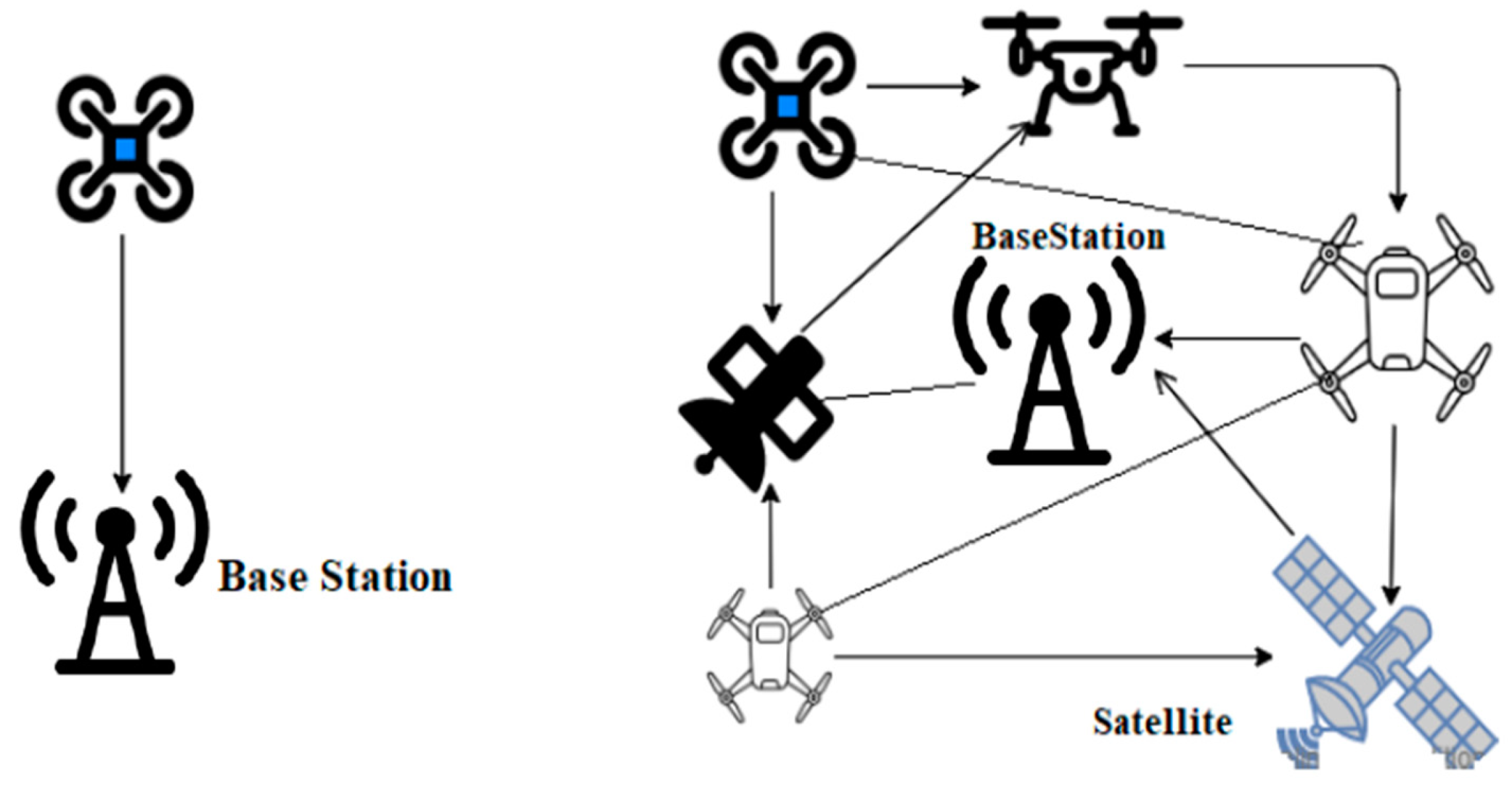
[15]. FANETs, which are not only applicable for multi-UAV systems but can also be formed by single-UAV systems, according to the specification seen in
Figure 3.
Figure 3. Types of FANETs network.
3. What Links Make FANETs, Different from MANETs, and VANETs?
The IEEE 802.11a network technology is today’s essential network technology for constructing FANETs. Mesh ad hoc networks utilize the 802.11s wireless networking standard
[14]. When two UAVs interact, this is called Single Hop Communication. Alternatively, a Multi-Hop Communication channel may be created across the other UAVs in UAV-to-UAV communication, as seen in
Figure 3.
Fixed infrastructure, such as a satellite or a ground station, is used in the case of FANETS-to-FANETS Communication, in which UAVs connect with improved infrastructure. FANET may be a more advanced version of MANET and VANET
[15]. However, there are several distinctions between FANET and the existing ad hoc networks, including the following: FANET nodes have far greater mobility than MANET or VANET nodes. FANET nodes fly in the air, in contrast to the traditional MANET and VANET nodes, representing walking men and vehicles.
-
Due to the high mobility of FANET nodes, the network’s topology changes more frequently than the network itself
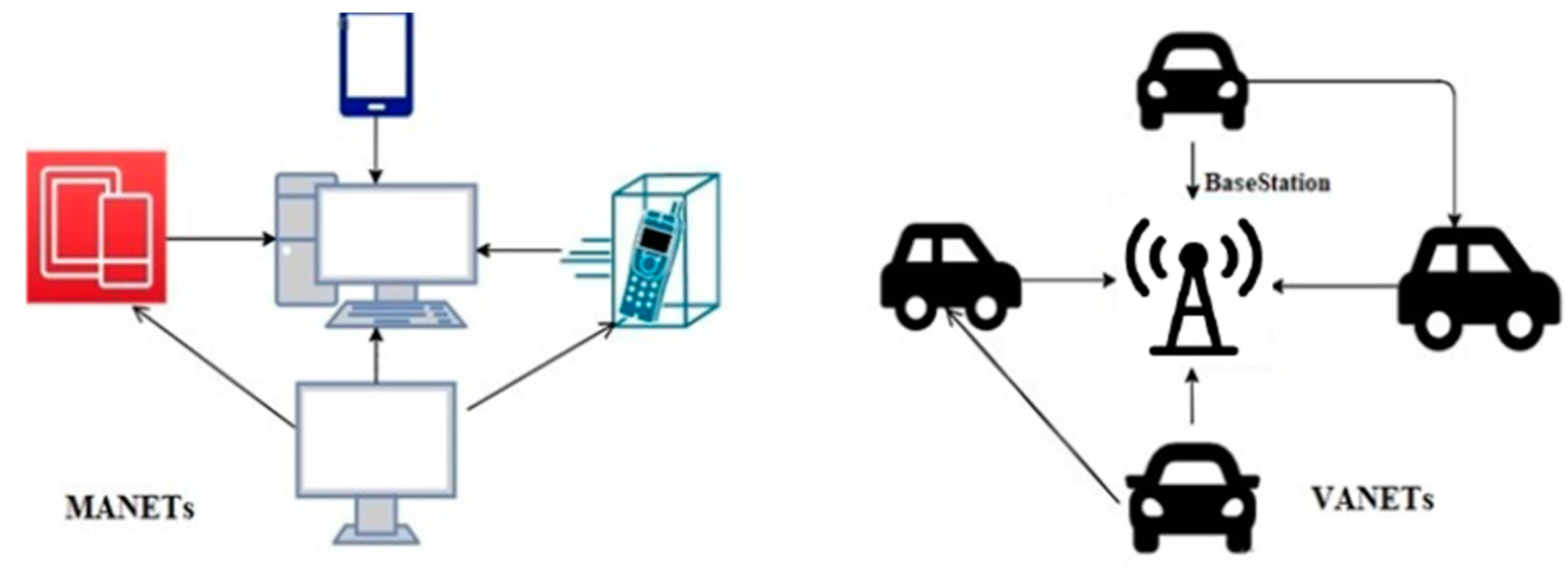
[16][19][23]. A typical MANET or VANET network topology is shown in
Figure 4.
-
There are now many ad hoc networks striving to connect. For example, Wireless sensor networks make extensive use of these technologies for gathering and transmitting data about the surrounding environment
[24]. Peer-to-peer and broadcast traffic must be allowed simultaneously for FANET to work effectively.
-
The Distances between FANET and FANETS nodes are much longer than the distances between the two networks
[12][13][24]. Unmanned aerial vehicles (UAVs) need a more extended communication range than either MANETs or VANETs if they are to be linked together. Consequently, radio links, hardware circuits, and physical layer behaviour are all impacted.
-
Multi-UAV systems may contain various types of sensors, each of which may need a separate data transmission strategy
[19].
Figure 4. MANETS and VANETS network structure.
4. What’s the Roles of Bioinspired Algorithms in FANETs?
A clustering method comprises virtual sets, which are represented by clusters. Each cluster consists of cluster nodes (CN) or cluster members, each contributing to the selection or suggestion of a CH
[15]. A CH’s neighbors’ nodes within the CH’s transmission range are considered cluster members. In theory, any cluster node can be nominated as the cluster head. However, some characteristics may be more critical for a CH than others
[20][21]. These characteristics are considered when selecting a CH. Using the example, an SN with an additional 5G connection is preferred to become a CH than all nodes that do not have this characteristic
[21][22][23][24]. The transmission range of the nodes controls the size of a cluster and, as a result, the outcome varies from cluster to cluster
[22].
The term “optimization” refers to improving performance by efficiently using specific limited resources that exist. During the previous several years, the difficulties associated with solving specific issues have increased, resulting in the need for novel optimization strategies to handle a problem efficiently. The methods were theoretically modelled before developing heuristic optimization algorithms to get the desired results. The most common drawback with mathematical optimization approaches is that local optima tend to become stuck in place
[21][22][25][26]. This makes them exceedingly ineffective in resolving real-world problems due to their behaviors. Population-based algorithms, based on randomization, include two critical steps for obtaining improved results: solution development (finding the optimal answer) and exploration (finding alternate solutions). The MFO method is an innovative nature-inspired optimization technique that may be used to address challenging optimization issues. Transverse orientation mimics the movement of moths in nature
[22]. The proposed algorithm uses moths and flames techniques, by which it generates efficient solutions.
Moreover, it has been proven that this algorithm can outperform other meta-heuristic optimization techniques in terms of performance. It takes its inspiration from transverse orientation, which is the term used to describe the maritime strategy of moths
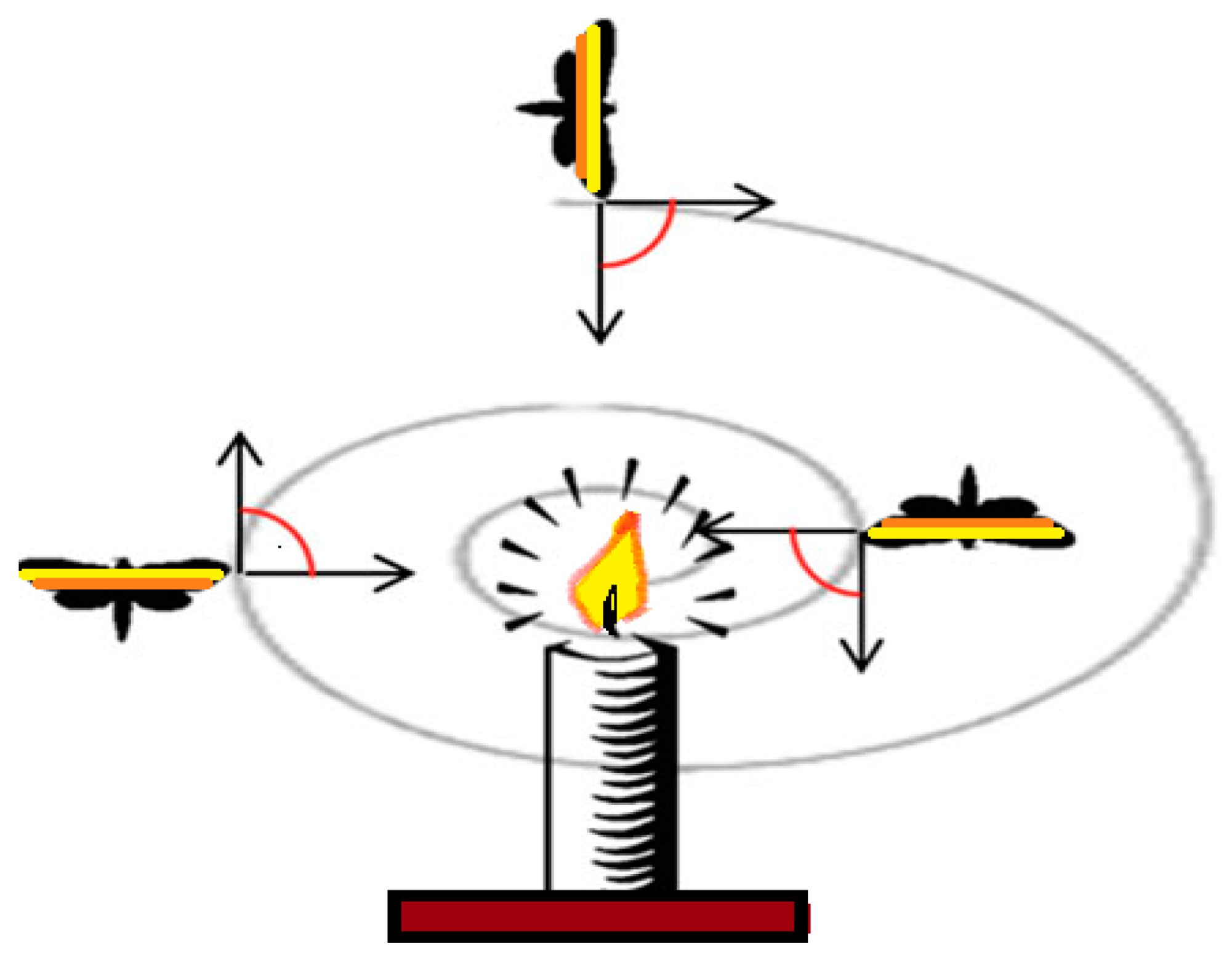
[20]. Keeping a steady angle concerning the moon’s movement allows a moth to hover, as seen in
Figure 5. This method is quite effective in drifting over long distances with a straight track. Quite the opposite, artificial lighting can occasionally fool moths
[27]. As a result, in comparison to the moon, a manufactured light is very close. While maintaining an equivalent viewpoint to the light, a moth may begin to travel in a spiral route with the light source, which can be disastrous for it
[7][8][11]. This technique has many advantages, but two stand out.
Figure 5. Spiral flying path.
First and foremost, MFO avoids the problem of local optima stagnation
[12]. However, some other optimization methods, such as the genetic algorithm (GA)
[7][8][9][10], continue to suffer from this problem. Second, MFO offers tremendous potential for exploitation and exploration, enabling it to outperform other processes in the long run.
However, even though FANETs are part of ad-hoc networks, they cannot use the same MANET and VANET clustering methods due to their unique characteristics. Instead, new techniques need to be made, or existing practices need to be changed to consider the unique features of a UAV network. UAVs were grouped into clusters, each of which had a specified number of UAVs and one of which was designated as a CH as by Bilal et al.
[7]. Neighboring UAVs start by exchanging information about their node’s specifications. Node information messages include a “zone ID” field that categorizes each UAV in a particular cluster. Each node keeps a database of connection quality information in the cluster, including information about its neighbors’ distance, SNR, and latency. LEACH was developed to ensure balanced energy use and improve WSN efficiency by dividing the network into numerous clusters and rotating the CHs. LEACH is a MAC protocol based on TDMA, the first hierarchical routing protocol to use clustering. LEACH is a routing system based on clustering, where nodes form different clusters. Every cluster has a CH node that gathers data from cluster members and transmits it to the sink. The LEACH protocol
[28] is divided into turns, each of which has two primary stages: setup and data transmission. The setup stage comprises selecting CHs, clustering, and creating the TDMA schedule for data transmission, which is carried out in the data transmission stage. LEACH-C picks CHs based on node residual energy and generates clusters accordingly in the network. As the name implies, LEACH-C
[29] employs a centralized technique to choose the best candidate for CH from nominated nodes. Initially, sensor nodes report their remaining energy and position to the sink. The sink computes the average energy of nodes using this data. Then it chooses which nodes will be CHs. Thus, nodes with more leftover energy than average will be chosen as CHs in this round. The rest, however, remains a simple node. Centralization improves CH distribution and selection and the number of communications between nodes and sinks, which improves the network life-cycle. Like LEACH, LEACH-C transfers data to the sink in a single hop, reducing CH lifespan. The number of CHs varies from turn to turn in the LEACH technique, but in the LEACH-C approach, it is fixed.
CBLADSR (cluster-based location aided dynamic source routing) is a new routing technique suggested by Shi et al.
[8]. Using three parameters, CBLADSR selects the CHs. A CH will be chosen among cluster members with a low-speed ratio, a high energy level, and several neighbor nodes. Each node in the cluster has a neighbor table, which keeps track of all of the other nodes in the group. To communicate between clusters, CBLADSR employs short and long-range transmissions. As part of their research, Zang and Zang
[11] came up with an algorithm for mobility prediction. Each node keeps track of its one-hop neighbors in a neighbor table. The neighbor table also contains the probability of how long a node will remain in its table. A dictionary tree structure is used to calculate the probability. This neighbor node’s probability and time determine when the link will end. Neighboring nodes’ LET probabilities and degrees are used to create a weight for each node. A CH will be chosen from among the nodes based on the node’s weight
[10][11][12][13].
Clustering in ad-hoc networks has also been performed using artificial intelligence approaches such as ant colony optimization (ACO)
[17][20], particle swarm optimization (PSO)
[13][18], and grey wolf optimization (GWO)
[14]. Numerous options are generated by using these methods. Nodes that potentially serve as CHs are included in each solution. The future orientation of ad-hoc networks was also examined by Bilal et al.
[15] and Rizwan et al.
[16]. In addition, these ideas are based on the nodes’ mobility. Peer et al.
[23] discussed the routing method using the fuzziness in wireless multi-hop networks. Nadeem et al.
[19] came up with a way to choose a CH by a recommendation system that takes information from many different datasets and suggests an optimal CH node. As a result of this research, Adil et al.
[20] developed a clustering technique based on the ACO (CACONET). ACO employs the social behavior of ants to find some food or a solution to a shared problem
[17]. Another ACO-based algorithm called ACONET
[20] has also been used as a clustering technique but has the same problem as
[19][20][23]. GWOCNETs
[25] simulate the grey wolf’s leadership hierarchy and hunting strategy. Alpha, beta, delta, and omega are the four varieties of grey wolves. The alpha wolf is the most powerful in a pack and serves as the pack’s leader. The rest of the group follows their lead to keep up with the alpha, beta, and delta wolves. Each wolf will be considered as a solution to the optimization issues. As an alpha solution, it is considered the best one. CAVDO
[22] utilized the dragon fly algorithm’s feature extraction to resolve the problem of clustering and selecting the best CH. The fundamental drawback of artificial intelligence approaches is that they require a large amount of computer power, even though they generate better outcomes. It takes a long time for them to get to an ideal solution. A vast number of random selections and random population sizes slow down the convergence of these methods. Due to the high mobility of UAVs, artificial intelligence approaches take too long to generate a correct result. Hence, they cannot be employed alone for a changing network architecture due to their low processing capacity.