
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Abdul Razaque | + 1387 word(s) | 1387 | 2021-11-18 07:29:09 | | | |
| 2 | Lindsay Dong | + 124 word(s) | 1511 | 2021-12-13 03:55:56 | | | | |
| 3 | Lindsay Dong | Meta information modification | 1511 | 2022-03-28 08:05:36 | | |
Video Upload Options
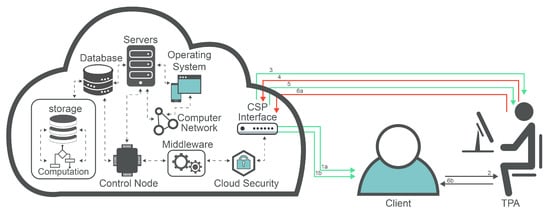
Cloud computing has become a prominent technology due to its important utility service; this service concentrates on outsourcing data to organizations and individual consumers. Cloud computing has considerably changed the manner in which individuals or organizations store, retrieve, and organize their personal information. Despite the manifest development in cloud computing, there are still some concerns regarding the level of security and issues related to adopting cloud computing that prevent users from fully trusting this useful technology.
1. Introduction
-
The private cloud is usually utilized by a limited number of users capable of accessing highly confidential data.
-
The public cloud is commonly employed for hosting sensitive data, in which data integrity is repeatedly mutable.
-
The hybrid cloud combines two or more delivery models. This model can be applicable to cloud users who would like to retain their most crucial data on-premises while storing their fundamental data on the cloud. The combined delivery models can be private-, public-, or community-based models; however, a standardized technology can be utilized to bound the data. The hybrid cloud improves security and lowers the price. However, the high management complexity is the major drawback.
-
The community cloud can be considered as a type of public cloud in which various cloud clients share a specific infrastructure with a community that engages with one another on an identical interest.
2. Vulnerabilities, and Potential Threats
2.1. TPA-Based Cloud Vulnerabilities
-
Loss of control;
-
Lack of trust (mechanisms).
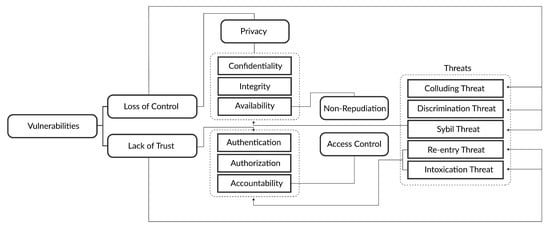
2.1.1. Loss of Control
When clients/users lose their authority over their resources stored on the servers of the cloud service provider (CSP), a loss of control occurs [10]. A deficiency in authentication and authorization placed by the service providers contributes to bigger security risks and concerns. Most of the cloud services providers do not provide data encryption for the data at rest. As a result, the data cannot be safeguarded if a data breach occurs at the cloud service provider side [11].
Let us consider the server in the CSP and clients that use the services . We take the security requirements to impose on the server. Thus, the risk can be referred to as for and that has a security requirements for the clients. We let , for be the probability that the server loses the control to meet the security requirements. The loss of control be determined as:
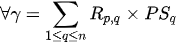
2.1.2. Lack of Trust (Mechanisms)
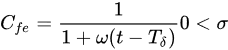
-
Privileged user access;
-
Regulatory compliance;
-
Data location;
-
Data segregation;
-
Recovery;
-
Investigative support;
-
Long-term viability.
2.2. TPA-Based Cloud Threats
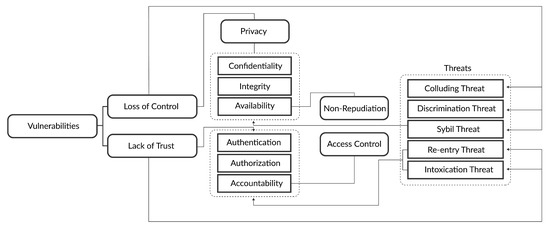
2.2.1. Collusion Threats
-
Self-promoting: malicious cloud clients falsely promote a specific cloud service provider by recording remarkable positive feedback;
-
Slandering: malicious cloud clients defame a specific cloud service provider by sending remarkable negative feedback;
-
Occasional collusion feedback attack: this kind of attack occurs when a remarkable negative or positive feedback is occasionally entered by malicious cloud clients.
2.2.2. Sybil Threats
-
Self-promoting: this is also known as a ballot-stuffing attack. In this attack, significant positive feedback is added by malicious cloud clients to promote a specific cloud service provider;
-
Slandering: another name of this attack is bad-mouthing. This attack is launched by malicious cloud clients to defame a specific cloud service provider using significant negative ratings.
-
Occasional Sybil feedback attack: in this attack, significant amounts of negative or positive feedback are entered occasionally by malicious cloud client to either promote or defame a specific cloud service provider.
2.2.3. ON OFF Threat or Intoxication Threat
2.2.4. Discrimination Threat
2.2.5. Newcomer or Reentry Threat
References
- Razaque, A.; Jararweh, Y.; Alotaibi, B.; Alotaibi, M.; Hariri, S.; Almiani, M. Energy-efficient and secure mobile fog-based cloud for the Internet of Things. Future Gener. Comput. Syst. 2021, 127, 1–13.
- Huang, H.; Sun, X.; Xiao, F.; Zhu, P.; Wang, W. Blockchain-based eHealth system for auditable EHRs manipulation in cloud environments. J. Parallel Distrib. Comput. 2021, 148, 46–57.
- Ibrahim, F.A.; Hemayed, E.E. Trusted cloud computing architectures for infrastructure as a service: Survey and systematic literature review. Comput. Secur. 2019, 82, 196–226.
- Razaque, A.; Vennapusa, N.R.; Soni, N.; Janapati, G.S. Task scheduling in cloud computing. In Proceedings of the Systems, Applications and Technology Conference (LISAT) 2016 IEEE Long Island, Farmingdale, NY, USA, 29 April 2016; pp. 1–5.
- Arwa, M.; Hamdan, M.; Khan, S.; Abdelaziz, A.; Babiker, S.F.; Imran, M.; Marsono, M.N. Software-defined networks for resource allocation in cloud computing: A survey. Comput. Netw. 2021, 195, 108151.
- Yeh, T.; Chen, Y. Improving the hybrid cloud performance through disk activity-aware data access. Simul. Model. Pract. Theory 2021, 109, 102296.
- Razaque, A.; Li, Y.; Liu, Q.; Khan, M.J.; Doulat, A.; Almiani, M.; Alflahat, A. Enhanced Risk Minimization Framework for Cloud Computing Environment. In Proceedings of the 2018 IEEE/ACS 15th International Conference on Computer Systems and Applications (AICCSA), Aqaba, Jordan, 28 October–1 November 2018; pp. 1–7.
- Kalluri, R.K.; Guru, C.V. An effective analytics of third party auditing and Trust architectures for integrity in cloud environment. Mater. Today Proc. 2021, 79, 69–76.
- Perez-Botero, D.; Szefer, J.; Lee, R.B. Characterizing hypervisor vulnerabilities in cloud computing servers. In Proceedings of the ACM 2013 International Workshop on Security in Cloud Computing, Dresden, Germany, 9–12 December 2013; pp. 3–10.
- Razaque, A.; Amsaad, F.; Hariri, S.; Almasri, M.; Rizvi, S.S.; Frej, M.B.H. Enhanced grey risk assessment model for support of cloud service provider. IEEE Access 2020, 8, 80812–80826.
- Razaque, A.; Nadimpalli, S.S.V.; Vommina, S.; Atukuri, D.K.; Reddy, D.N.; Anne, P.; Vegi, D.; Malllapu, V.S. Secure data sharing in multi-clouds. In Proceedings of the IEEE 2016 International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016; pp. 1909–1913.
- Dunne, N.J.; Brennan, N.M.; Kirwan, C.E. Impression management and Big Four auditors: Scrutiny at a public inquiry. Account. Organ. Soc. 2021, 88, 101170.




