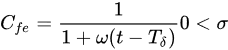Cloud computing has become a prominent technology due to its important utility service; this service concentrates on outsourcing data to organizations and individual consumers. Cloud computing has considerably changed the manner in which individuals or organizations store, retrieve, and organize their personal information. Despite the manifest development in cloud computing, there are still some concerns regarding the level of security and issues related to adopting cloud computing that prevent users from fully trusting this useful technology.
1. Introduction
Cloud computing is considered as a utility-driven paradigm derived from a “pay as you use” concept responsible for enabling consumers to remotely share technology-based resources instead of possessing these resources locally [
1,
2].
Cloud computing transports a reliable, custom-made information technology (IT) perimeter for cloud users with an ensured quality of service. In cloud computing, services are afforded from the cloud clients’ points of view and are presented as IT-related skills, reachable with no in-depth familiarity of the used technologies and with a titular coordinating effort [
3,
4].
The cloud as a concept can be defined as the “storing of data anywhere and accessing it anytime”. Cloud clients who have appropriate permissions can access the stored data. For more information about the cloud characteristics, readers can refer to [
5]. Four diverse types of delivery models are supported in cloud computing: private cloud, public cloud, hybrid cloud, and community cloud [
6,
7].
-
The private cloud is usually utilized by a limited number of users capable of accessing highly confidential data.
-
The public cloud is commonly employed for hosting sensitive data, in which data integrity is repeatedly mutable.
-
The hybrid cloud combines two or more delivery models. This model can be applicable to cloud users who would like to retain their most crucial data on-premises while storing their fundamental data on the cloud. The combined delivery models can be private-, public-, or community-based models; however, a standardized technology can be utilized to bound the data. The hybrid cloud improves security and lowers the price. However, the high management complexity is the major drawback.
-
The community cloud can be considered as a type of public cloud in which various cloud clients share a specific infrastructure with a community that engages with one another on an identical interest.
Cloud computing merges various technologies and procedures to preserve cloud client’s data. Thus, there are competitions between cloud service providers to provide the latest security mechanisms. Notwithstanding, several security-wise ambiguities still exist which make many organizations reluctant to fully utilize cloud computing [
8].
In cloud computing, data security, privacy, and safety are fundamental measures which establish the trust level between the cloud clients and cloud providers. Cloud computing is broadly employed in diverse fields such as economy, social, finance, educational institutions, and government offices. Therefore, users store confidential information on the cloud and retrieve it at their convenience. Prior to developing and designing cloud computing, privacy and security requirements have to be exhaustively explored. Individuals and organizations are still distrustful due to the existing security vulnerabilities that threaten cloud computing. In fact, cloud computing lacks explicit security and privacy protection regulations.
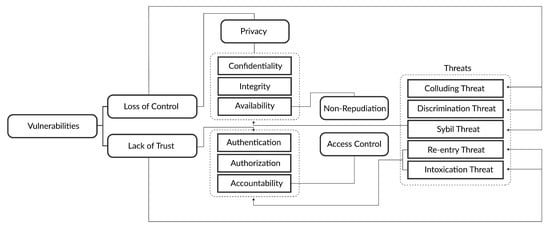
4. Vulnerabilities, and Potential Threats
4.1. TPA-Based Cloud Vulnerabilities
Encrypting data on the cloud is necessary while avoiding considerable processing overhead. Many organizations are leaning towards cloud-based IT solutions because of the multiple benefits that cloud computing affords. Nevertheless, before making use of cloud computing, cloud clients should be aware of potential vulnerabilities (
Figure 2) that might mutate cloud clients’ hopes of increasing scalability and decreasing coordination cost into a misery of misuse and data breaches [
23]. Therefore, the security issues associated with cloud adoption should be considered. The most common vulnerabilities effecting TPAs are given as follows:
Figure 2. Security requirements, vulnerabilities, and threats.
4.1.1. Loss of Control
When clients/users lose their authority over their resources stored on the servers of the cloud service provider (CSP), a loss of control occurs [24]. A deficiency in authentication and authorization placed by the service providers contributes to bigger security risks and concerns. Most of the cloud services providers do not provide data encryption for the data at rest. As a result, the data cannot be safeguarded if a data breach occurs at the cloud service provider side [25].

4.1.2. Lack of Trust (Mechanisms)
Trust is one of the important aspects for maintaining quality. Trust is faith or confidence in the cloud services delivered by the CSP [
26]. Trust permits the clients to use the service in the cloud without any panic.
To reinforce the confidence of the clients, it is necessary to build trust among clients, TPA, and CSP. The problem is a lack of trust for data storage on the servers of the clouds for clients. Furthermore, most organizations store their private and sensitive information on cloud servers. If a CSP reliably provides the services, then there is the possibility that a TPA might play a role as a malicious adversary when auditing the services. There is the possibility that the TPA might share the private and sensitive data to other unknown parties to harm the legitimate owners of the data. Thus, there is a need to build a trust model to deal with the lack of trust of the clients. The trust model based on time factor is considered as feedback. If the feedback is older, it is considered to be of a lower weight, whereas newer feedback is counted as having a higher weight. Thus, the feedback of the client can be determined as:
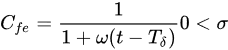
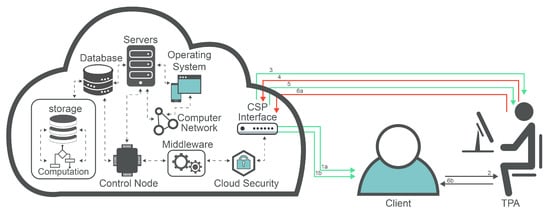
TPA takes the responsibility to evaluate and authenticate the client while maintaining privacy preservation depicted in Figure 3. This is carried out because the actions taken by the TPA could be malicious for the client and CSP.
Figure 3. Evaluation and authentication of the client through CPS.
Cloud clients should be aware of the following seven issues.
-
Privileged user access;
-
Regulatory compliance;
-
Data location;
-
Data segregation;
-
Recovery;
-
Investigative support;
-
Long-term viability.
4.2. TPA-Based Cloud Threats
Several security requirements are violated because of the diverse attacks that target cloud computing as depicted in Figure 2.
4.2.1. Collusion Threats
This type of threat consist of a form of attack known as collusive malicious feedback that is created by malicious cloud clients who misuse feedbacks to tamper with trust model outcomes. Collusion attacks exist in three forms:
-
Self-promoting: malicious cloud clients falsely promote a specific cloud service provider by recording remarkable positive feedback;
-
Slandering: malicious cloud clients defame a specific cloud service provider by sending remarkable negative feedback;
-
Occasional collusion feedback attack: this kind of attack occurs when a remarkable negative or positive feedback is occasionally entered by malicious cloud clients.
4.2.2. Sybil Threats
This type of attack is launched by malicious cloud clients utilizing several identities to tamper with test outcomes. Various counterfeit ratings are generated by malicious cloud clients utilizing low product value in which products are purchased in short time. This type of attack can be categorized as:
-
Self-promoting: this is also known as a ballot-stuffing attack. In this attack, significant positive feedback is added by malicious cloud clients to promote a specific cloud service provider;
-
Slandering: another name of this attack is bad-mouthing. This attack is launched by malicious cloud clients to defame a specific cloud service provider using significant negative ratings.
-
Occasional Sybil feedback attack: in this attack, significant amounts of negative or positive feedback are entered occasionally by malicious cloud client to either promote or defame a specific cloud service provider.
4.2.3. ON OFF Threat or Intoxication Threat
Malicious cloud clients adjust their behaviors either to act as harmful or harmless users. More specifically, the cloud client initially performs ordinarily until gaining trust, then the client begins to misbehave. Regrettably, this type of misbehavior is hard to detect. This deficiency is derived from peer-to-peer network and is known as the dynamic personality of peers. This attack can be resolved using a forgetting factor approach.
4.2.4. Discrimination Threat
Discrimination attacks occur when distinct qualities of services are afforded from cloud service providers to cloud clients. This attack jeopardizes cloud service providers’ trust because various ratings are provided by clients as a result of this attack. Mitigating or preventing this attack is a difficult task to accomplish.
4.2.5. Newcomer or Reentry Threat
This attack is carried out by a previous client who has been terminated due to unethical behavior and who reenters the domain with a new identification. Reentry or newcomer attack can be mitigated/prevented by contrasting credential records utilizing the client location and then using the location as a unique ID.
This entry is adapted from the peer-reviewed paper 10.3390/electronics10212721