
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Sumaira Johar | + 2331 word(s) | 2331 | 2021-07-22 05:55:28 | | | |
| 2 | Lindsay Dong | -5 word(s) | 2326 | 2021-08-27 03:14:05 | | | | |
| 3 | Arjun Remadevi Somanathan | + 3 word(s) | 2329 | 2021-12-09 09:36:45 | | |
Video Upload Options
Blockchain being a leading technology in the 21st century is revolutionizing each sector of life. Services are being provided and upgraded using its salient features and fruitful characteristics. Businesses are being enhanced by using this technology. Countries are shifting towards digital currencies i.e., an initial application of blockchain application. It omits the need of central authority by its distributed ledger functionality. This distributed ledger is achieved by using a consensus mechanism in blockchain. A consensus algorithm plays a core role in the implementation of blockchain. Any application implementing blockchain uses consensus algorithms to achieve its desired task.
1. Introduction
2. Types of Blockchain
-
Public/Permissionless Blockchains for example Bitcoin and Ethereum etc.
-
Private/Permissioned Blockchains for example Hyperledger and R3 Corda etc.
-
Hybrid Blockchains for example Dragonchain etc.
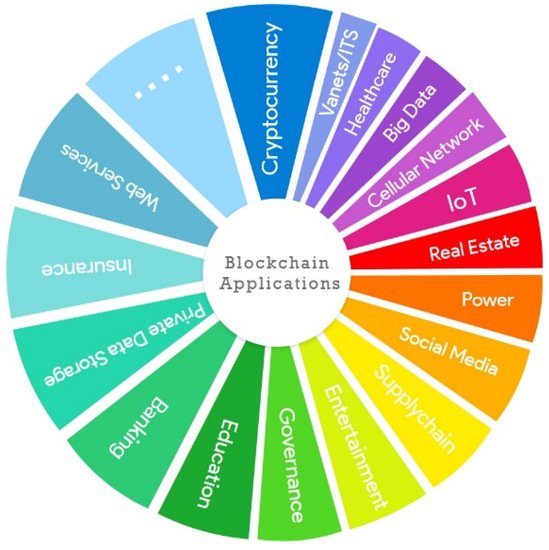
3. Applications of Blockchain
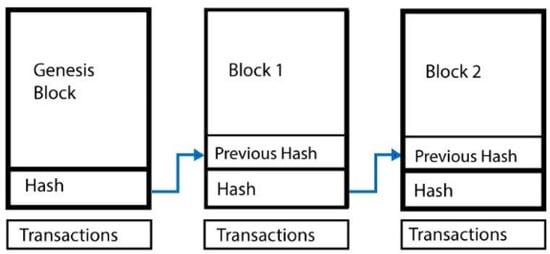
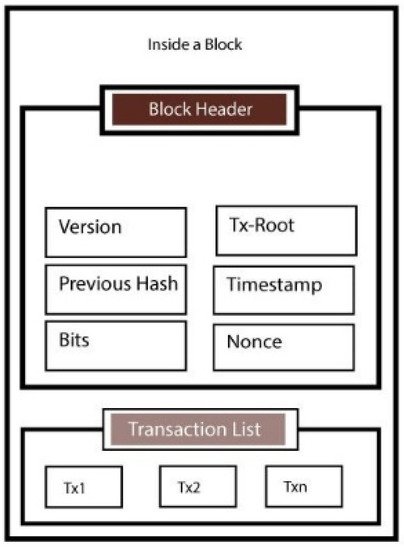
4. Blockchain’s Architecture
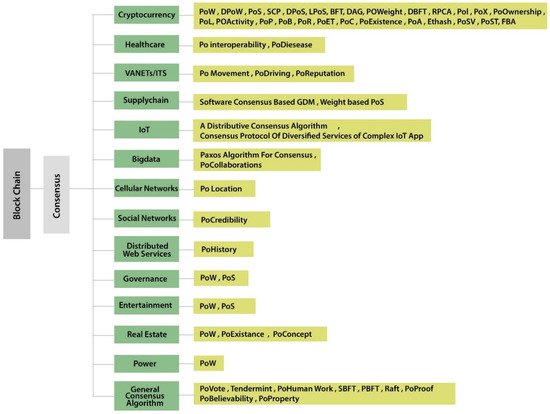
5. Consensus Algorithms
6. Development Platforms
| Comparison Parameters | Ethereum | Cosmos | Cardano | EOS | Bitcoin | Hyperledger | Corda |
|---|---|---|---|---|---|---|---|
| Token | ETH | ATOM | ADA | EOS | Bitcoin | n/a | SDK |
| Public/Private | Public | Public/Private | Public | Public/Private | Public | Public/Private | Private |
| Programming Languages | Solidity | Java, C++, Python, Go | Haskell | JavaScript, Python, Ruby | Golang | Java, Golang, Node | Kotlin, Java |
| Consensus Algorithms | Proof of Work (Currently used), Proof of Stake (In Future) | Tendermint (Byzantine Fault-Tolerant, Proof of Stake) | Proof of Stack | Delegated Proof of Stack | Proof of Work | Practical Byzantine Fault Tolerance | Pluggable Consensus |
| Transactions Per Second | 25 | 10,000 | n/a | Millions (theoretically) | 1/3 to 1/7 | More than 1000 | Between 15 and 1678 TPS |
| Transaction Size | 1 MB | 250 bytes | n/a | n/a | 1 MB | Changeable (depending on framework) | Maximum size in bytes |
| Open Source | True | True | True | True | True | True | True |
| Pros | Anyone can write smart contract and anyone can view that contract | Works like a hub for blockchains, based on Tendermint | Scalability, Sidechain which reduces the risk of hacks. | Parallel processing, low latency, free usage (claimed not proven). | Safe and secure, High token value. | Don’t use cryptocurrency so it is ideal for business networks. | Designed specifically for financial applications |
| Cons | Scalability issue, 25 transactions per second is very slow | Complex technology may have compatibility issues with the latest technologies and new blockchains | Maintaining a side chain is complicated and it will require its own miners. | Never actually free, not fully decentralized, the free transaction fee are imposed on everyone who has EOS. | Very slow, not ideal for programming while there are other faster technologies. | There are a lot of frameworks to choose from and they all have different requirements to implement and setup. | Partially decentralized, not much suitable for IoT resource constrained networks |
7. Blockchain Challenges
Although blockchain has improved a lot of applications and has a fault-tolerant peer-to-peer network blockchain always comes up with its vulnerabilities. We discuss the possible attacks on a blockchain ledger.
7.1. Denial of Service (DoS) Attacks
7.2. Sybil Attacks
7.3. Eclipse Attacks
7.4. Routing Attacks
7.5. The 51% Attacks
7.6. Double Spending
7.7. Alternative History Attacks
7.8. Race Attacks
7.9. Finney Attack
8. Blockchain Research Issues
8.1. Blockchain-Based Research Issues in Healthcare
8.2. Blockchain-Based Research Issues/Future Work in Intelligent Transportation System (ITS) and Internet of Things (IoT)
8.3. Blockhain Research Issues/Future Work in Real Estate
9. Future Work
References
- Velde, F. Bitcoin: A Primer; Essays on Issues the Federal Reserve Bank of Chicago Dec; Federal Reserve Bank of Chicago: Chicago, IL, USA, 2013.
- Shoker, A. Sustainable blockchain through proof of exercise. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; pp. 1–9.
- Brito, J.; Castillo, A. Bitcoin: A Primer for Policymakers; Mercatus Center at George Mason University: Fairfax, VA, USA, 2013.
- Sun, J.; Yan, J.; Zhang, K.Z. Blockchain-based sharing services: What blockchain technology can contribute to smart cities. Financ. Innov. 2016, 2, 26.
- Basden, J.; Cottrell, M. How utilities are using blockchain to modernize the grid. Harv. Bus. Rev. 2017, 23, 1–8.
- Syed, T.A.; Alzahrani, A.; Jan, S.; Siddiqui, M.S.; Nadeem, A.; Alghamdi, T. A comparative analysis of blockchain architecture and its applications: Problems and recommendations. IEEE Access 2019, 7, 176838–176869.
- Wang, W.; Hoang, D.T.; Hu, P.; Xiong, Z.; Niyato, D.; Wang, P.; Wen, Y.; Kim, D.I. A survey on consensus mechanisms and mining strategy management in blockchain networks. IEEE Access 2019, 7, 22328–22370.
- Lucas, B.; Páez, R.V. Consensus Algorithm for a Private Blockchain. In Proceedings of the 2019 IEEE 9th International Conference on Electronics Information and Emergency Communication (ICEIEC), Beijing, China, 12–14 July 2019; pp. 264–271.
- Dinh, T.T.A.; Liu, R.; Zhang, M.; Chen, G.; Ooi, B.C.; Wang, J. Untangling blockchain: A data processing view of blockchain systems. IEEE Trans. Knowl. Data Eng. 2018, 30, 1366–1385.
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853.
- Sayeed, S.; Marco-Gisbert, H. Assessing blockchain consensus and security mechanisms against the 51% attack. Appl. Sci. 2019, 9, 1788.
- Wüst, K.; Gervais, A. Ethereum Eclipse Attacks; Technical Report; ETH: Zurich, Germany, 2016.
- Nayak, K.; Kumar, S.; Miller, A.; Shi, E. Stubborn mining: Generalizing selfish mining and combining with an eclipse attack. In Proceedings of the 2016 IEEE European Symposium on Security and Privacy (EuroS&P), Saarbruecken, Germany, 21–24 March 2016; pp. 305–320.
- Sahay, R.; Geethakumari, G.; Mitra, B. A novel blockchain based framework to secure IoT-LLNs against routing attacks. Computing 2020, 102, 2445–2470.
- Saad, M.; Cook, V.; Nguyen, L.; Thai, M.T.; Mohaisen, A. Partitioning attacks on bitcoin: Colliding space, time, and logic. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 1175–1187.
- Natoli, C.; Gramoli, V. The blockchain anomaly. In Proceedings of the 2016 IEEE 15th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 31 October–2 November 2016; pp. 310–317.
- Pilkington, M. Blockchain Technology: Principles and Applications. In Research Handbook on Digital Transformations; Edward Elgar Publishing: Cheltenham, UK, 2016; Available online: https://www.elgaronline.com/ (accessed on 16 May 2021).
- Lee, H.; Shin, M.; Kim, K.S.; Kang, Y.; Kim, J. Recipient-oriented transaction for preventing double spending attacks in private blockchain. In Proceedings of the 2018 15th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Hong Kong, China, 11–13 June 2018; pp. 1–2.
- Rosenfeld, M. Analysis of hashrate-based double spending. arXiv 2014, arXiv:1402.2009.
- Pérez-Solà, C.; Delgado-Segura, S.; Navarro-Arribas, G.; Herrera-Joancomartí, J. Double-spending prevention for bitcoin zero-confirmation transactions. Int. J. Inf. Secur. 2019, 18, 451–463.
- Malik, A.; Gautam, S.; Abidin, S.; Bhushan, B. Blockchain Technology-Future of IoT: Including Structure, Limitations and Various Possible Attacks. In Proceedings of the 2019 2nd International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), Kannur, India, 5–6 July 2019; Volume 1, pp. 1100–1104.
- Mechkaroska, D.; Dimitrova, V.; Popovska-Mitrovikj, A. Analysis of the possibilities for improvement of BlockChain technology. In Proceedings of the 2018 26th Telecommunications Forum (TELFOR) IEEE, Belgrade, Serbia, 20–21 November 2018; pp. 1–4.
- Morganti, G.; Schiavone, E.; Bondavalli, A. Risk Assessment of Blockchain Technology. In Proceedings of the 2018 Eighth Latin-American Symposium on Dependable Computing (LADC), Belgrade, Serbia, 20–21 November 2018; pp. 87–96.
- Alkhalifah, A.; Ng, A.; Kayes, A.; Chowdhury, J.; Alazab, M.; Watters, P.A. A taxonomy of blockchain threats and vulnerabilities. In Blockchain for Cybersecurity and Privacy; CRC Press: Boca Raton, FL, USA, 2020; pp. 3–28.
- Dasgupta, D.; Shrein, J.M.; Gupta, K.D. A survey of blockchain from security perspective. J. Bank. Financ. Technol. 2019, 3, 1–17.
- Alizadeh, M.; Andersson, K.; Schelén, O. A Survey of Secure Internet of Things in Relation to Blockchain. J. Internet Serv. Inf. Secur. 2020, 3, 47–75.
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the attack surface of blockchain: A systematic overview. arXiv 2019, arXiv:1904.03487.
- Kaushik, A.; Choudhary, A.; Ektare, C.; Thomas, D.; Akram, S. Blockchain—Literature survey. In Proceedings of the 2017 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 19–20 May 2017; pp. 2145–2148.
- Vokerla, R.R.; Shanmugam, B.; Azam, S.; Karim, A.; De Boer, F.; Jonkman, M.; Faisal, F. An Overview of Blockchain Applications and Attacks. In Proceedings of the 2019 International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–6.
- McGhin, T.; Choo, K.K.R.; Liu, C.Z.; He, D. Blockchain in healthcare applications: Research challenges and opportunities. J. Netw. Comput. Appl. 2019, 135, 62–75.
- Lunardi, R.C.; Michelin, R.A.; Neu, C.V.; Nunes, H.C.; Zorzo, A.F.; Kanhere, S.S. Impact of consensus on appendable-block blockchain for IoT. In Proceedings of the 16th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Houston, TX, USA, 12–14 November 2019; pp. 228–237.
- Zhang, L.; Peng, M.; Wang, W.; Su, Y.; Cui, S.; Kim, S. Secure and Efficient Data Storage and Sharing Scheme Based on Double Blockchain. CMC Comput. Mater. Contin. 2021, 66, 499–515.
- Ali, Q.E.; Ahmad, N.; Malik, A.H.; Ali, G.; Rehman, W.U. Issues, challenges, and research opportunities in intelligent transport system for security and privacy. Appl. Sci. 2018, 8, 1964.
- Ali, Q.E.; Ahmad, N.; Malik, A.H.; Rehman, W.U.; Din, A.U.; Ali, G. ASPA: Advanced Strong Pseudonym based Authentication in Intelligent Transport System. PLoS ONE 2019, 14, e0221213.
- Taleb, T.; Sakhaee, E.; Jamalipour, A.; Hashimoto, K.; Kato, N.; Nemoto, Y. A stable routing protocol to support ITS services in VANET networks. IEEE Trans. Veh. Technol. 2007, 56, 3337–3347.
- Taleb, T.; Ochi, M.; Jamalipour, A.; Kato, N.; Nemoto, Y. An efficient vehicle-heading based routing protocol for VANET networks. In Proceedings of the IEEE Wireless Communications and Networking Conference, 2006, WCNC 2006, Las Vegas, NV, USA, 3–6 April 2006; Volume 4, pp. 2199–2204.
- Qi, W.; Landfeldt, B.; Song, Q.; Guo, L.; Jamalipour, A. Traffic differentiated clustering routing in DSRC and C-V2X hybrid vehicular networks. IEEE Trans. Veh. Technol. 2020, 69, 7723–7734.
- Alghamdi, N.S.; Khan, M.A. Energy-Efficient and Blockchain-Enabled Model for Internet of Things (IoT) in Smart Cities. CMC Comput. Mater. Contin. 2021, 66, 2509–2524.
- Alamri, M.; Jhanjhi, N.; Humayun, M. Blockchain for Internet of Things (IoT) Research Issues Challenges & Future Directions: A Review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 244–258.
- Gauhar, A.; Ahmad, N.; Cao, Y.; Khan, S.; Cruickshank, H.; Qazi, E.A.; Ali, A. xDBAuth: Blockchain based cross domain authentication and authorization framework for Internet of Things. IEEE Access 2020, 8, 58800–58816.
- Ahmad, I.; Alqarni, M.A.; Almazroi, A.A.; Alam, L. Real Estate Management via a Decentralized Blockchain Platform. CMC Comput. Mater. Contin. 2021, 66, 1813–1822.
- Li, M.; Shen, L.; Huang, G.Q. Blockchain-enabled workflow operating system for logistics resources sharing in E-commerce logistics real estate service. Comput. Ind. Eng. 2019, 135, 950–969.
- R. Arjun; K. R. Suprabha; Innovation and Challenges of Blockchain in Banking: A Scientometric View. International Journal of Interactive Multimedia and Artificial Intelligence 2020, 6, 7-14, 10.9781/ijimai.2020.03.004.





