Electronic voting (e-voting) is an electronic system that allows users to make a collaborative decision or vote for candidates in an election. It handles the registration of voters, input of vote, vote casting, vote encryption, the transmission of the ballot to the server, vote storing, vote counting, and tabulation of the election result.
1. Introduction
The e-voting system can be used in various applications such as punched cards, smart cards, direct-recording e-voting systems (DRE), optical scan systems, and computers connected to the Internet. The e-voting system offers more accurate election results, faster result tabulation, minimises human errors, more convenience towards disabled or handicapped people, and self-tallying election results [1]. However, according to Peng [2] and Oo and Aung [3], e-voting faces challenges of scalability for large-scale elections, security challenges, unpredictable malfunctions of servers, and others. Some people feel uncomfortable adopting e-voting systems due to voter privacy as voter identity might be disclosed. The most important security properties to preserve as mentioned by Peng [2] and Sebé et al. [4] are the privacy of the voter, fairness, receipt-freeness, coercion-resistance, individual verifiability, universal verifiability, robustness, double-voting prevention, etc. Thus, many researchers have proposed schemes to enhance the security of e-voting systems and put e-voting systems in practice. In this paper, we focus on conventional approaches which cover mix-net-based e-voting, homomorphic e-voting, and blind signature-based e-voting, and latest developments which cover blockchain-based e-voting, post-quantum e-voting, and hybrid e-voting. We aim to draw a bigger picture of past and present e-voting scheme developments to provide readers with an overview of various e-voting approaches, in terms of their structure, advantages, and disadvantages. We then aim to provide a comprehensive review of each e-voting approach in terms of its security properties, underlying tools, distinctive features, and weaknesses. We also discuss some critical practical considerations in the design of e-voting systems. Finally, we conclude our analysis with some potential future research directions.
The mix-net-based e-voting scheme breaks the correlation between the voters and their votes with the shuffling process using the mix-server. Homomorphic e-voting scheme allows the authority to sum all ballots without decrypting them. Blind signature-based e-voting allows the authority to authorise the voter without revealing any information on the ballot by employing a blind signature as the underlying building block. The underlying homomorphic encryption scheme and blind signature scheme are instances of asymmetric cryptographic primitive. Meanwhile, blockchain-based e-voting schemes are immutable, distributed, and do not rely on trusted third parties, therefore minimising potential malicious activities. Post-quantum e-voting schemes are designed to be secure against quantum attacks. A hybrid scheme refers to the scheme that is constructed by integrating two or more approaches.
1.1. Entities in e-Voting System
A generic e-voting scheme involves the following entities:
Voter: Individuals who are eligible to vote for candidates.
Candidate: Nominees seeking to be considered in the election.
Registrar: Registrars are responsible for authenticating the voters.
Authority: Persons in charge of conducting the election.
Auditor: Authorised persons to verify and review election results.
Adversary: Malicious individuals attempt to corrupt elections. There are two main types of adversaries, external and internal [
5]. External adversaries, also known as coercers, actively coerce voters to vote in certain ways, whereas internal adversaries attempt to breach the system and corrupt voter privacy and authority.
1.2. Structure of e-Voting System
The structure of e-voting systems consists of three phases [
6], namely, pre-voting, pre-voting, and post-voting. The processes in the pre-voting phase include the nomination of candidates, computation of the list of candidates, registration of voters, and computation of the list of eligible voters. Eligible voters cast their ballots during the voting phase. The post-voting phase mainly deals with the counting of votes and announcing the election results.
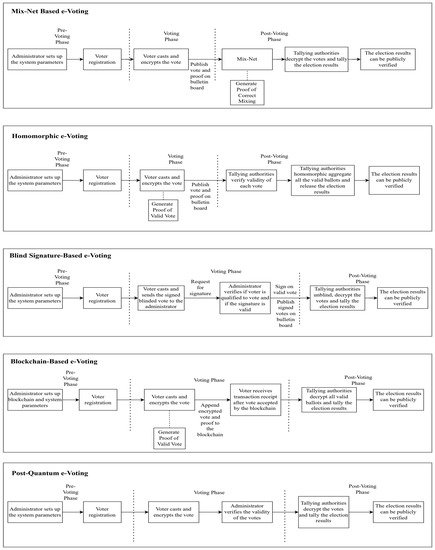
Figure 1 shows the general structure of mix-net-based e-voting, homomorphic e-voting, blind signature-based e-voting, blockchain-based e-voting, and post-quantum e-voting in the pre-voting phase, voting phase, and post-voting phase.
Figure 1. General structure of various e-voting approaches.
1.3. Advantages and Disadvantages of Various e-Voting Approaches
The summary presented in
Table 1 are compiled from the works of [
2,
4,
7,
8,
9,
10,
11,
12,
13,
14].
Table 1. Advantages and disadvantages of various e-voting approaches.
| Approach |
Advantages |
Disadvantages |
| Mix-net-Based e-Voting |
-
Provides unlinkability between voters and their votes
-
The computation cost is lower than the homomorphic tallying e-voting scheme
-
Supports write-in ballots
|
-
Difficult to implement on large-scale elections due to its complexity
-
Large amount of computation power is required for the mix server to prove the correctness of mixing
-
Vulnerable to DDOS attack
|
| Homomorphic e-Voting |
-
Suitable for small-scale elections, efficient in the open phase
-
Do not require decrypting of the encrypted votes to tally the election result. Thus, voter privacy is achieved
|
-
Requires intensive zero knowledge proof to prove the validity of votes (high communication cost)
-
High computation cost for the vote verification
-
This is not suitable for multi-candidate elections because the ballot must contain proof of a possible choice in the election; therefore, the encryption cost is high when there is a large range of preference
|
| Blind Signature-Based e-Voting |
-
Simple, flexible, universally verifiable, and efficient
-
Intensive zero knowledge proof is not required
-
Guarantees anonymity
-
Supports write-in ballots
-
Most efficient in the tallying phase
-
Does not require high communication cost for the intensive phase
|
-
Requires an anonymous channel where it suffers from complex computation and might be impractical to implement in the real world
-
Blind factor can serve as a voting receipt
-
Receipt-free blind signature e-voting requires physical assumption, e.g., an untappable channel that is impractical to implement over internet
-
Most of the proposed schemes required certificate authority to distribute key pairs to the voter and it is costly to maintain
|
| Blockchain-Based e-Voting |
-
The votes stored in the blockchain are immutable
-
Allows the election results to be generated instantly
-
Offers transparency while guaranteeing privacy
-
Able to withstand a DOS attack
|
|
| Post-Quantum e-Voting |
|
-
Larger key size than public key algorithms, thus requires more storage space
-
Large sizes of data for signature and key establishment to be transmitted over communication channels, thus limits the speed of transmission and vulnerable to unforeseen quantum attacks
|
As observed from the comparison analysis in Table 1, it is worth mentioning that hybrid schemes are more practical and efficient than other approaches. A hybrid scheme refers to the scheme that is constructed by integrating two or more approaches. A hybrid scheme inherits the advantages and security properties of combined cryptographic tools and eliminates the weaknesses of cryptographic tools individually. However, the use of these e-voting approaches varies depending on the application to which they are applied [15]. Therefore, different e-voting approaches may be suited for different applications.
The mix-net-based e-voting scheme breaks the correlation between the voters and their votes with the shuffling process using the mix-server. Homomorphic e-voting scheme allows the authority to sum all ballots without decrypting them. Blind signature-based e-voting allows the authority to authorise the voter without revealing any information on the ballot by employing a blind signature as the underlying building block. The underlying homomorphic encryption scheme and blind signature scheme are instances of asymmetric cryptographic primitive. Meanwhile, blockchain-based e-voting schemes are immutable, distributed, and do not rely on trusted third parties, therefore minimising potential malicious activities. Post-quantum e-voting schemes are designed to be secure against quantum attacks. A hybrid scheme refers to the scheme that is constructed by integrating two or more approaches.
2. Practical Considerations in e-Voting
According to the technical report presented by National Academies of Sciences, Engineering, and Medicine in 2018 [
131], e-voting is a cybersecurity issue that has many factors to be considered before it can be implemented in real-world applications. Cybersecurity is a continuous challenge because adversaries constantly implement new techniques to breach system defences. e-Voting systems connected to the Internet are the most vulnerable to attack via wireless or physical access and during data transmission. All e-voting schemes, including voting at polling stations and remote e-voting, are vulnerable to the following attacks.
-
Denial-of-service (DoS) attacks. The main goal of DoS attacks is to slow down computer systems and to the extent that it affects the casting of votes, tallying of votes, and the auditing process.
-
Malware attacks. Malicious software that can disrupt the casting of votes and the auditing process, and alter or destroy stored ballots.
-
Malicious individuals or servers break into the system to retrieve administrator-level sensitive data such as voters’ credentials.
The following are some of the factors that affect an adversary’s ability to breach the system.
-
If the system is designed properly.
-
If the system is configured and updated accordingly.
-
If the system is operated and managed accordingly.
-
Resources and skills of potential attackers.
We do not have the technology to offer a secure method to support e-voting at present. The Internet is unsuitable for transmitting ballots, and currently, there is no realistic mechanism to fully secure the casting of votes and tabulation of election results from cyberattacks. In addition, there are no technical mechanisms to guarantee that a computer system can generate accurate results, and each layer of the computer system is not modified. Furthermore, e-voting schemes that deploy emails are more vulnerable than other forms of e-voting because the emails do not utilise a secure channel. Moreover, not all vendors follow the best practices in developing, maintaining, and operating e-voting systems. Therefore, to achieve strong defenses against cyber threats, it is necessary to deploy state-of-the-art technologies and practices and expand new cybersecurity knowledge.
3. Potential Research Directions
Many current studies rely on strong assumptions, such as perfect random oracles, honest registrars, and honest bulletin boards. Most of the schemes suffer from high computational costs, thus it is desirable to consider developing more lightweight systems that can still satisfy the necessary security properties.
Post-quantum e-voting is still in its initial stages and has not been fully developed. Further research is expected to improve the current results and implement it in a fully practical scenario. Post-quantum e-voting has drawn great attention in recent years to design a system that can resist quantum adversaries. Chillotti et al. [
151] first proposed an LWE-based e-voting scheme. The bulletin board in the proposed scheme has an additional function that is required to check whether the ballot is generated correctly before the ballot is cast with an additional secret key. Their proposed scheme relies on the honest bulletin board, which leads to an open problem if the proposed scheme is secure against dishonest bulletin boards and can be improved to be more practical. The scheme proposed by Dong and Yang [
12] can be further extended to explore whether the proposed e-voting scheme is secure in quantum computing environments, such as cavity quantum electrodynamics. Rønne et al. [
153] employed a fully homomorphic encryption scheme in linear time in the Juels et al. [
43]’s coercion-resistance e-voting scheme. The proposed scheme was not supported by a formal security proof to prove that the modified Juels et al. [
43] scheme can be secure against classical adversaries.
Meanwhile, further research is expected to analyse, study, and improve the scalability of blockchain-based e-voting systems, such as the implementation of blockchain-based e-voting in large-scale elections, as the current blockchain-based e-voting systems are only implemented in boardroom and small organisation elections [
128]. Further research is also expected to improve the computational cost, reduce delays, and high bandwidth. According to Liu and Wang [
129], the coercion-resistance property is difficult to fulfill owing to the transparency property of the blockchain. Thus, future research could be carried out to balance the properties of transparency and coercion-resistance.
Additionally, it would be interesting to study blockchain-based e-voting using post-quantum algorithms that can resist quantum attacks [
136,
164]. According to Fernández-Caramés and Fraga-Lamas [
165], the challenges of post-quantum blockchain include the key size required for post-quantum cryptosystems which is larger than that required for public-key cryptosystems, typically between 128 and 4096 bits. Moreover, some post-quantum schemes restrict the number of messages that can be signed by using a single key for security reasons. Consequently, continuous generation of new keys is required, which leads to high computational resource consumption and slacking of certain blockchain processes.Therefore, further research is required to balance the efficiency of blockchain and key generation and key size issues. Esgin et al. [
164] suggested that their proposed post-quantum blockchain scheme can be implemented in privacy preserving applications such as e-voting systems. Gao et al. [
136] constructed their scheme with code-based cryptography proposed by McEliece [
166], which has not been broken so far, to be secure against quantum attacks.
From the latest works on various e-voting schemes, we observed that the current research trend for e-voting schemes has been diverted towards blockchain technology and post-quantum cryptography. In mix-net-based e-voting, Pinilla [
29], Boyen et al. [
154], Rønne et al. [
153] migrated mix-net-based e-voting to post-quantum cryptography. On the other hand, Gong et al. [
135] and Chaieb and Yousfi [
137] integrated mix-net with blockchain technology. In homomorphic e-voting, recent studies on post-quantum homomorphic e-voting schemes have been conducted by Aziz et al. [
152] and Liao [
155]. Some studies have proposed homomorphic e-voting with lattice-based cryptography and fully homomorphic encryption because fully homomorphic encryption and lattice-based cryptography are new research directions. In blind signature-based e-voting, recent studies by Liu and Wang [
129], Cruz and Kaji [
112], and Zhou et al. [
138] integrated blind signature-based e-voting with blockchain technology. Kaim et al. [
158] proposed a blind signature-based e-voting scheme that can resist quantum attacks.
It is also interesting to find out the possibility of performing generic transformation from e-voting to e-cash and e-voting to e-cheque, as conjectured by Kho and Heng [
167]. They showed that e-cash and e-cheque have high similarities with e-voting in terms of their structure and security properties.
This entry is adapted from the peer-reviewed paper 10.3390/sym14050858