As the 全球导航卫星系统(Global Navigation Satellite System (GNSS) is widely used in all walks of life, the signal structure of satellite navigation is open, and the vulnerability to spoofing attacks is also becoming increasingly prominent, which will seriously affect the credibility of navigation, positioning, and timing (PNT) services. Satellite navigation signal authentication technology is an emerging technical means of improving civil signal anti-spoofing on the satellite navigation system side, and it is also an important development direction and research focus of the GNSS. NSS)广泛应用于各行各业,卫星导航信号结构开放,对欺骗攻击的脆弱性也日益突出,这将严重影响导航、定位和授时(PNT)服务的可信度。卫星导航信号认证技术是卫星导航系统侧提高民用信号反欺骗能力的新兴技术手段,也是GNSS的重要发展方向和研究重点。
- satellite navigation
- Beidou navigation satellite system
- credible navigation
1. Introduction简介
2. Principles and Technical Architecture of the Satellite Navigation Signal Authentication二、卫星导航信号认证原理与技术架构
Satellite navigation signal authentication uses cryptographic methods to improve the anti-spoofing of civil 卫星导航信号认证采用密码学方法,提高民用GNSS signals and provides users with more credible PNT services. First of all, this section introduces the principle of satellite navigation signal authentication. Then, it describes the technical architecture of navigation signal authentication based on space segment, ground section and user segment, Finally, it analyzes the new capabilities brought by satellite navigation signal authentication, as well as the advantages and limitations in anti-spoofing.信号的反欺骗能力,为用户提供更可信的PNT服务。本节首先介绍卫星导航信号认证的原理。然后,介绍了基于空间段、地面段和用户段的导航信号认证技术架构,最后分析了卫星导航信号认证带来的新功能,以及反欺骗的优势和局限性。2.1. Principles
2.1. 原则
卫星导航信号认证技术旨在为卫星导航信号添加加密认证标记,防止卫星导航信号受到GNSS欺骗攻击。它是一种新的GNSS反欺骗技术,结合了信息安全和导航信号设计。发送方(导航卫星)使用密码技术生成“认证符号”,该符号嵌入现有卫星导航信号中并广播给用户。接收器(GNSS用户终端)验证“认证符号”,以确认接收到的导航信号是否来自在轨真实卫星,以及导航信息是否被伪造或篡改[21]。卫星导航信号认证技术具有以下特点:Satellite navigation signal authentication technology aims to add encrypted authentication marks to satellite navigation signals to prevent satellite navigation signals from GNSS spoofing attacks. It is a new GNSS anti-spoofing technology that combines information security and navigation signal design. The sender (navigation satellite) uses cryptography technology to generate an "authentication symbol", which is embedded in the existing satellite navigation signal and broadcast to users. The receiver (GNSS user terminal) verifies the "authentication symbol" to confirm whether the received navigation signal is from a real satellite in orbit, and whether the navigation message has been forged or tampered with [17]. Satellite navigation signal authentication technology has the following characteristics:
1) One-way broadcast.
- (1)
-
单向广播。
The satellite navigation signal uses the navigation satellite broadcast signal to provide PNT services for terrestrial users, and its signal characteristics have the characteristics of one-way broadcast. Therefore, satellite navigation signal authentication technology should be based on the broadcast system authentication framework.
2) Signal disclosure transmission.
卫星导航信号利用导航卫星广播信号为地面用户提供PNT服务,其信号特性具有单向广播的特点。因此,卫星导航信号认证技术应基于广播系统认证框架。Satellite navigation signals use the public signal structure to broadcast signals, and their signal authentication needs to have the characteristics of public signal transmission.
- (2)
-
信号泄露传输。
3) Compatible with existing signal structure.
卫星导航信号采用公共信号结构广播信号,其信号认证需要具有公共信号传输的特点。The authentication of satellite navigation signals will not affect existing GNSS services, so its authentication signal design should be compatible with existing signal structure.
- (3)
-
与现有信号结构兼容。
2.1.1. Satellite Navigation Signal Authentication Type2.1.1. 卫星导航信号认证类型
Satellite navigation signals include the carrier, pseudocodes, and message. The newly added authentication mark can be added to the navigation message [18] and spreading spectrum codes [19]. Figure 1 shows the generation of the navigation message including authentication message and the spreading spectrum code including authentication code. Therefore, the satellite navigation signal authentication type is divided into Navigation Message Authentication (NMA) and Spreading Code Authentication (SCA) [20].
卫星导航信号包括载波、伪码和消息。新添加的认证标记可以添加到导航消息[22]和扩频码[23]中。图1示出了包括认证消息和扩频码在内的认证码的导航消息的生成。因此,卫星导航信号认证类型分为导航消息认证(NMA)和扩码认证(SCA)[24]。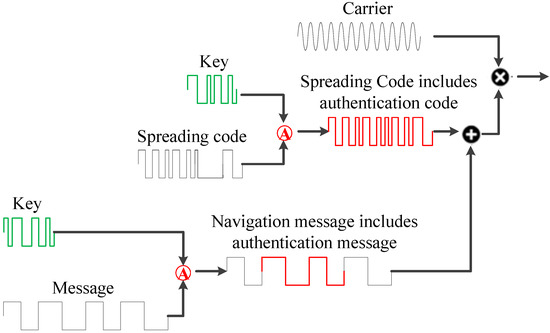 Figure 图1. Satellite Navigation Signal Authentication.卫星导航信号认证。
Figure 图1. Satellite Navigation Signal Authentication.卫星导航信号认证。1) NMA
NMA uses message bit-level authentication to realize navigation source authentication. Its advantage is that the modification of the existing signal system is small and the signal modulation method is not changed. It’s just to upgrade the software of the user receiver. The engineering realization cost is small. The Galileo E1 OSNMA structure is shown as Figure 2. Galileo reserved a 40-bit message in the early ICD, and the ICD announced in 2021 clarified that the 40-bit message is the navigation authentication message [21].
- (1)
-
国家海洋管理局
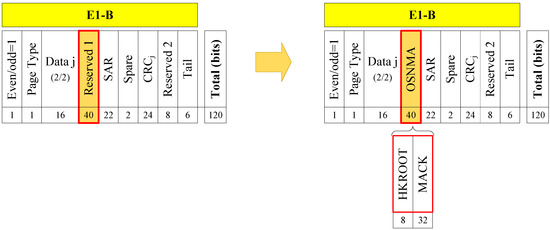
Figure 图2. GALILEO NMA message structure [21].
2) SCA
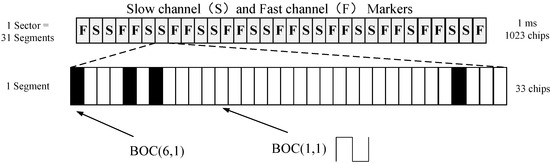
SCA adopts the characteristics of unpredictable authentication spreading chips, and implements authentication processing in the power domain, which can provide spoofing protection in the pseudorange domain. The typical SCA is the CHIMERA signal, as shown in the Figure 3. Based on the TMBOC (Time-Multiplexed Binary Offset Carrier) signal, the 1 ms sector is divided into 31 segments via a combination of time division and time hopping, and different authentication channel (fast channel and slow channel) are assigned for each segment. The authentication codes are randomly replaced for 29 BOC(1,1) in each segment of 33 chips, and the four BOC(6,1) chips are never modified [22].
伽利略NMA报文结构[25]。- (2)
-
爱生雅, Key1, …, Keyi−1, Keyi. The advantage is that when the key is not received or not received at a certain moment, the key can be obtained via the key hash of the subsequent epoch. Then, according to the key Keyi and the navigation message Mi at the current moment, the Hash-based Message Authentication Code (HMAC) algorithm is used to generate the message authentication code MACi. The GNSS system broadcasts the navigation message Mi, the message authentication code MACi, and the Keyi−1 of the previous epoch to the user; that is, the symmetric key used to generate the MAC is sent after the broadcast MAC is delayed by δ time. The user receives the GNSS message Mi for storage and the delayed symmetric key Keyi, then generates delay MAC′i′, and compares it with the MACi of the GNSS broadcast. If the two are consistent, the authentication is passed. Key chain generation and the key usage of TESLA are shown in Figure 5 below.Table 1.Comparison of NMA and SCA.
Type Indicators Receiver Processing Feature NMA [21][25] Galileo-OSNMA
Time Between Authentication: 10 sMessage bit authentication using Message Authentication Code (MAC) The project implementation is less difficult, the security level is not as good as SCA, and it can be processed in real time at the terminal. Compared with the ECDSA algorithm, TESLA has a lower computational load and communication load, and is suitable for satellite navigation systems with limited message bandwidth. TESLA’s one-way keychain generation and transmission improve the stability of authentication services. ECDSA has a variety of international standards, and the implementation process is simple, but ECDSA occupies more data bits. The comparison between TESLA and the digital signature is shown in Table 2.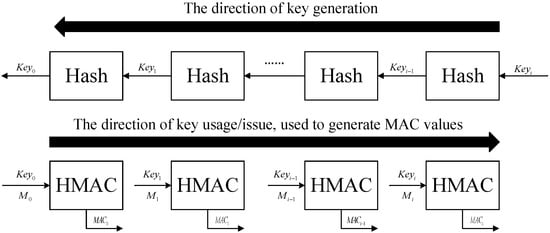 Figure 5.Key chain generation and key usage of TESLA.Table 2.Comparison of TESLA and ECDSA.
Figure 5.Key chain generation and key usage of TESLA.Table 2.Comparison of TESLA and ECDSA.Protocol Cryptographic Algorithm Calculated Amount Authentication Information Truncation Key Distribution Requirements Key Length under the Same Security Level TESLA
[25]][28[26]SCA [22][26] NTS3-CHIMERA
Time Between Authentication for slow channel: 180 s
Time Between Authentication for fast channel: 1.5 s or 6 sPower Domain Authentication Using Sampled Data for Spreading Code Correlation Processing The pseudorange can be authenticated. The authentication requires data caching, and the project implementation is costly. 2.1.2. Satellite Navigation Message Authentication Type
The navigation message authentication protocol includes Digital Signatures (DS) and the Timed Efficient Stream Loss-Tolerant Authentication (TESLA). Digital signatures are implemented based on asymmetric cryptography (also known as public key cryptography). The sender uses the private key to sign the message, and the receiver uses the public key to verify the signature of the message [23][27]. Digital signatures commonly use the Elliptic Curve Digital Signature Algorithm (ECDSA), which has the characteristics of high security and complex algorithm strength. In addition, European scholars proposed EC Schnorr’s digital signature algorithm [24][18]. The digital signature schematic is shown in Figure 4 below.The TESLA protocol is a broadcast authentication protocol that can be applied to satellite navigation broadcast signals with limited bandwidth [25][26][28,29]. The TESLA protocol, designed by Perring et al., is an MAC-based broadcast authentication protocol [27][28][30,31]. The protocol uses a symmetric cryptography method, and the key is to use the delayed key release to ensure the security of the broadcast key. The TESLA protocol generates a set of keychains through the hash function. The generation order of the keychain is Keyi, Keyi−1, …, Key1, Key0, while the keychain system uses Key0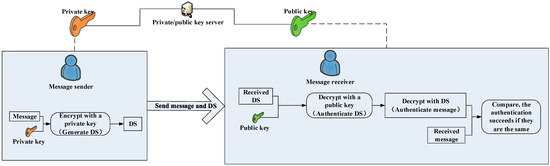 Figure 4.Digital Signature Schematic.
Figure 4.Digital Signature Schematic.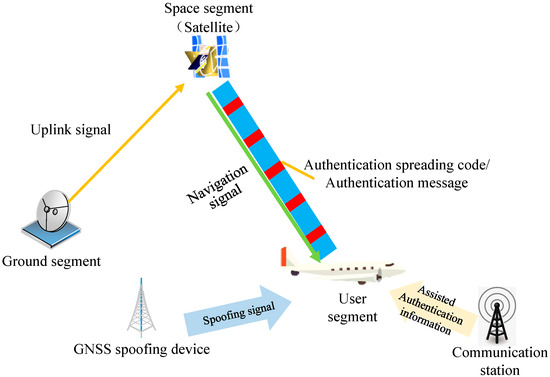 Figure 6.Satellite navigation signal authentication architecture.
Figure 6.Satellite navigation signal authentication architecture.2.3. Incremental Capability
Navigation signal authentication technology will bring a new service to the GNSS, which neither improves the accuracy nor augments the integrity and continuity, just focuses on improving the anti-spoofing capability of GNSS civil signals to provide users with more credible PNT services. Signal authentication is a system-side anti-spoof technology which can resist generative spoofing. The orange part in Figure 7 represents the incremental capability.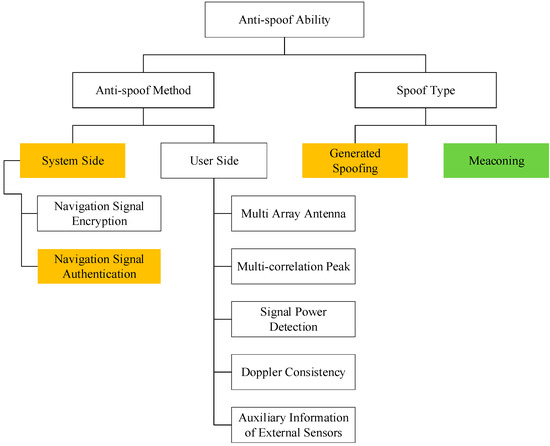 Figure 7.Ability of satellite navigation signal authentication technology.
Figure 7.Ability of satellite navigation signal authentication technology.- (1)
-
Anti-spoofing methodTable 3.Comparison of common anti-spoofing algorithms.
2.2. Technical Architecture
The satellite navigation system consists of the space segment, ground segment, and user segment. Based on the existing satellite navigation system, the satellite navigation signal authentication will be extended to the space segment, the ground segment, the user terminal, and the network auxiliary segment. The space segment adds the authentication spreading code/authentication messages to the broadcast downlink satellite navigation signal, the user segment authenticates the received satellite navigation signal, and the network auxiliary segment uses the communication base station (terrestrial communication/satellite communication) to provide network auxiliary authentication information. If there is a GNSS spoofing signal in the actual environment, the user segment can identify whether the current signal is a spoofing signal through the authentication of the message/spreading spectrum code. The architecture of the satellite navigation signal authentication is shown in Figure 6.It is difficult for spoofed attackers to predict the authentication message/spreading code High DOA detection based on multi-array antennas [7][8][7,8] The spoofing signal is generally emitted from a single transmitting antenna, and its satellites come from the same direction, while the real satellites of the signal come from different directions High High/Medium Multiple correlation peaks [31][32][33,34] The superposition of the spoofed signal and the real signal will bring multiple correlation peaks, and it will also cause distortion of the correlation peaks Medium Signal power [33][35[34],36] The spoofing signal has more power, and the signal power changes during the spoofing implementation Medium Doppler consistency [35][36][37,38] It is difficult for spoofing signals to keep the carrier Doppler shift consistent with the pseudocode Doppler shift Medium Auxiliary information of external sensors [4][5][4,5] Spoofing signals cannot deceive sensors such as inertial navigation, chip-scale atomic clocks, and lidar High - (2)
-
Anti-spoofing capabilityGenerated spoofing means that the attacker generates a spoofing signal with the exact same structure as the real GNSS signal [37][39], which utilizes the known vulnerabilities of the civilian signal ICD to generate a false GNSS spoofing signal and broadcast it to the target receiver. The prerequisite for satellite navigation signal authentication is that the spoofing attacker cannot break the cryptographic algorithm, so that the authentication message/spreading code cannot be forged. Therefore, satellite navigation signal authentication can solve the generative spoofing attack to civilian users. Meaconing means that the attacker receives the navigation signal [38][40], performing proper delay and power amplification on the real GNSS signal, and then broadcasts the meaconing signal to the target receiver. The meaconing does not change the message and spreading code, so the satellite navigation signal authentication effect is not good for this method. In addition to the above two common spoofing methods, Security Code Estimation and Replay (SCER) [39][41] has also been proposed in recent years. This method is to receive the real signal and estimate the encrypted or authenticated message in real time as much as possible. Then, the encrypted or authenticated message in the signal is reassembled and sent. SCER predicts the authentication message based on the security code estimation method, which is effective for security codes with a low symbol rate (navigation message), but less effective for security codes with a high symbol rate (spreading code).
Spoofing NMA SCA Generated spoofing Primary generated spoofing (low-cost software radio or commercial signal simulator) High High Intermediate generated spoofing (receive GNSS signal first and then generate spoofing signal) High High SCER Low Advanced generated spoofing (multiple intermediate generative spoofing) High/Medium High Meaconing Simple meaconing (same delay for each satellite channel) Low Low Multichannel meaconing (the delay of each satellite channel is inconsistent) Low Low