Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Adnan Shahid Khan and Version 2 by Catherine Yang.
There are continued advances in the internet and communication fields regarding the deployment of 5G-based applications. It is expected that by 2030, 6G applications will emerge as a continued evolution of the mobile network. Blockchain technology is one of the leading supporting technologies predicted to provide a secure and unique network to 6G-enabled devices, transactions, and applications. It is anticipated that the 6G mobile networks will be virtualized, have cloud-based systems, and aim to be the foundation for the Internet of Everything.
- 6G cellular network
- blockchain technology
- multifactor authentication technique
1. 6G Cellular Network
1.1. Concept and Development
With the research community involved in discussing possibilities and opportunities that may be opened up with the materialization of 6G technology, most countries in the world are still caught up in the deployment of the 5G technology. However, it is hypothesized by most researchers that 5G and Beyond 5G (B5G) technologies, once fully deployed, will be capable of enabling the Internet of Everything (IoE) to truly take off [1][2][23,24], leading to justifying the massive demands for 6G. The sixth generation of wireless technology (6G) will focus on communication between connected machines, i.e., thing-to-thing connection instead of people-to-people links in 1G-4G and people-to-thing communication as in the focus of 5G, as represented in Figure 12.
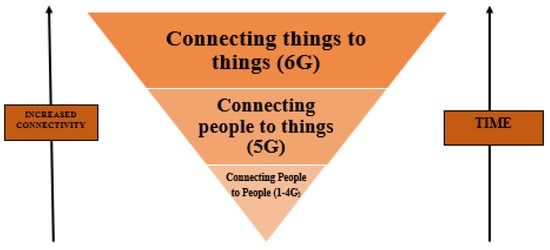
Figure 12.
Evolution of Internet.
In the past, a new wireless communication standard emerged after around a decade, and given this trend, it is expected that we would be witnessing 6G around 2030 [3][4][5][25,26,27]. As more and more users are connecting to the internet and using a large number of devices connected to the Internet, big changes and challenges are coming up for internet research. The research communities are already looking towards solutions to the challenges posed by 5G mobile communication. It is expected that many of these challenges will be addressed by the time 6G materializes [6][7][20,28].
1.2. Security Needs
While 6G applications and communication technologies will be powerful and a revolution, there will be many specific vulnerabilities [6][20]. Communication, access control, malicious behavior, authentication, and encryption-related issues will be faced in these applications (see Figure 23 below). It can be seen in the figure that 6G will support autonomous systems powered by A.I. and ML, multi-sensory X.R. applications built upon molecular communication technology, the THz technology, and the quantum communication technology and distributed ledger technologies that will be mainly developed using blockchains, etc. A.I. technologies and multi-sensory X.R. applications will be susceptible to issues with malicious behavior, encryption, and communication due to heavy data transmissions; however, the blockchains and DLT will be relatively safe as they already implement techniques of multistep or multifactor authentication.
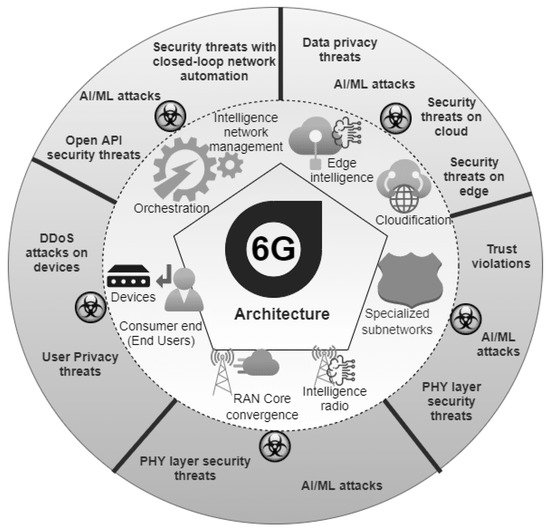
Figure 23.
Security and Privacy issues in 6G networks.
2. Blockchain Technology
2.1. What Is Blockchain Technology?
Blockchain technology can be claimed to be the most-hyped innovation of the 21st century that was designed to support bitcoin but now powers many business applications and is hyped to be the leading technology for the support of 6G technologies [8][9][10][22,58,59]. Advancements in blockchains are still young and hold the promise of a bright future [11][12][13][60,61,62]. The blockchains can be defined as a digital ledger of transactions (DLT), a database that can store encrypted transaction data in chronological order and chain the data together in the form of blocks [14][15][63,64]. Blockchain is used to define a structure of data that can be described as an ordered arrangement of blocks, where each of the blocks contains a small list of transactions and each of the blocks is chained together [16][17][18][65,66,67]. Through these chains, each component of the data can be traced to its source; however, the blockchains cannot be altered, deleted, or replaced without invalidation of the hash chain [16][65]. Blockchain technology has extensive applications in payment systems and other digital financial or Fintech solutions. Thus, this technology requires strict authentication protocol for managing the safety of the users and transactions [19][20][15,32].
2.2. How does Blockchain Work?
This technology, therefore, enables safe transactions between individuals without the fear of government, bank, or other third-party software snooping and stealing the data [21][22][68,69]. Figure 35 maps out roughly how a blockchain works; first, an individual node in a peer network requests a transaction, which is then broadcasted to a P2P network of nodes that authenticates it by verification technique and combines it to other transactions to form an encrypted block of data which is added to an existing blockchain [23][24][70,71]. Blockchains can be considered, therefore, as a promising and revolutionary technology for future developments of applications in the 6G network era as it can help in reducing the risks, stamps out frauds, and brings multilayer transparency in any transactions between two nodes in a scalable way, opening up a myriad of application scope and uses.
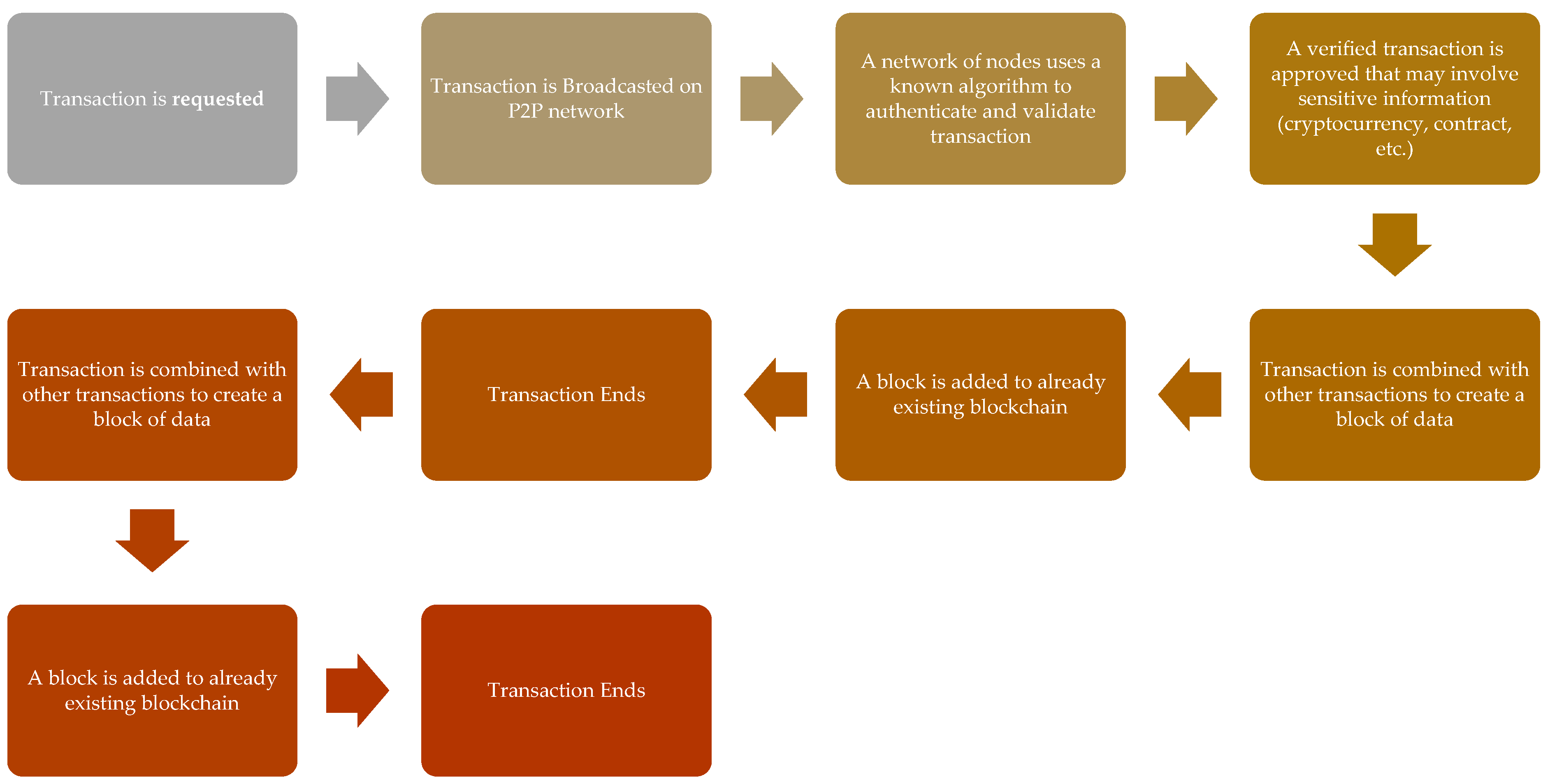
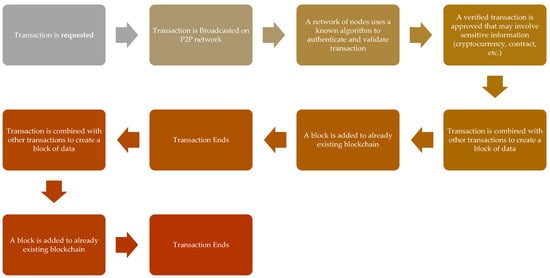
Figure 35. Blockchain Working.
Blockchain Working.
2.3. Benefits of Blockchain
Blockchains are gaining rapid fame due to the importance of record-keeping and storage of transactions and their crucial status for various kinds of businesses [25][26][27][72,73,74]. Blockchains allow efficient processing and faster transactions, saving both time and money [28][29][75,76]. Blockchain technology uses a highly secure digital signature feature to ensure that transactions are fraud-free [30][77]. Blockchains enable decentralized transactions and ensure smoother, safer, and faster transactions as they are carried out with a mutual consensus of users [31][32][78,79]. Moreover, these systems enable systematic actions, events, and payments. Transactions using blockchains are immutable, i.e., they cannot be changed, edited, or altered in any way after being recorded once [33][80]. Hence, in addition to speed and security, blockchains also enable the establishment of trust between users and parties in a transaction [34][35][36][81,82,83].
3. Recent Exploration of MFA Applications and Blockchain Authentication
Blockchain authentication refers to the system developed for increasing the security for the users and it verifies the users and connects it to the resources found on the technologies of digital currency, digital payments, transactions, and cryptocurrencies. The blockchain mainly uses the PKC, public-key cryptography, for the encryption of wallets and also the other places or links of the blockchain where the work of value has been stored. Thus, the authentication requirements for the blockchain increase similarities between the technology itself and the measures taken for securing it [37][16]. Multifactor authentication is referred to as a process of verification of users through at least two authentication factors [38][29]. The users can make use of an additional password, flash drive, special software, some particular files, and a flash drive containing important software. The MFA works in such a way that all layers of the verification need to be cleared, i.e., the user needs to provide proof of identity through OTPs, passwords, etc. Although this method is not preferred by most internet applications due to their security risks, blockchain applications use private keys for the identification of users [39][84].
There are different methods and techniques for ensuring the safety of the private key. Most of the time, there is a trade-off between security and usability. One of the methods proposes the security key be placed in a device without the addition of extra security [40][85]. However, anyone can access the unprotected device and obtain the keys. Users may use the encryptions on these devices as they need to enable them themselves. Digital wallets are commonly used for storage and access to blockchains [41][42][43][44][45][86,87,88,89,90]. They work by encrypting the security key/s by setting up a password. However, the security and key recovery are all challenges as there are numerous attacks on the passwords and security layers applied on the wallets [40][85]. Another method used for increasing security is using passwords to derive a combination of keys for accessing the information on the blockchains. When following this method, the private key needs to be unlocked so that previously defined passwords can be accessed during the creation of the key. This method is also prone to some disadvantages; one of the main disadvantages is that the user will be unable to change the password. Some devices possess computing capabilities that may be used with blockchain. Although these devices do not possess or support storage and they require zero understanding of the mechanism, it is highly susceptible to malware attacks [46][91].
Shin et al. [47][92] proposed a multifactor authentication procedure for WSNs in recent network applications that act in real-time but is found to be vulnerable to the collision of users and desynchronization attacks. Ni et al. [48][93] presented a service for authentication mechanism for 5G enabled IoT networks using key agreement mechanism by use of an anonymous key. However, after rigorous testing, it was revealed to be a single-level authentication, despite using a complex public key cryptosystem and a single authentication method is not suitable for 5G multiservice systems [49][94]. A robust MFA protocol was proposed by Huang et al. [50][95] for systems that use fragile communications based on two standalone schemes for authentication; however, these systems are not comprehensible, making them vulnerable to access attacks. Luo et al. [51][96] presented a flexible 3-factor authentication mechanism for various applications based on 5G multiservice systems. In this system, four different kinds of schemes can be provided for a user to ensure identity authentication and safety. The technique was slightly costly in terms of time efficiency. These issues are addressed by Luo et al. [52][97], who presented a Service-Based Architecture for 5G multiservice systems that build upon the work of Luo et al. [51][96] and uses an adaptable and decomposable 3-factor authentication system that can be applied simultaneously to ensure efficiency and speed. The tests on this system showed that it could provide an ideal efficiency in terms of transparency of action, security, and speed. However, further testing and real-time application are required. Wong et al. [53][98] also presented a 3-factor authentication scheme to ensure a high-security environment for communicating parties and integrates biometrics, password, and smart card authentication into a single system. Multiple server technologies are used to ensure that performance is quick and transparent. However, the technique still poses a communication cost.
There is limited research on the integration of multifactor analysis in blockchain-based applications. However, some papers were reviewed that can be valuable to indicate the benefits of these integrations. Antonio et al. [20][32] presented a multifactor analysis named 2FA for WordPress pages by using Hydro Raindrop multifactor authentication technology. In this paper, the researcher summarized the use of a blockchain-based two-factor authentication solution by a page on WordPress that contributes to securing user information. The study is not experimental, however, and the entire proposal is based on other theoretical and practical evidence. Overall, it suggested that the use of a decentralized technique provided by the integration of blockchain can enable multifactor and transparent user authentication, strengthening the security of information and the assets of individuals. Several studies also indicate the use of blockchain-based authentication procedures for autonomous vehicles [54][55][56][99,100,101]. In the study by Feng et al. [57][10], Blockchain-assisted privacy-preserving authentication system (BPAS) is presented to secure the data generated by vehicular ad hoc networks. This technique was proposed for ensuring accuracy as well as trust in the systems. However, there was a lack of support for batch verification in this papentryr that could provide an optimized verification in the form of blocks of data and hence reduce load on the resource consumption. Kebande et al. [19][15] also proposed an MFA based on Blockchain technology that proposed the use of an embedded Digital Signature (MFBC_eDS) that was found to be a suitable technique for countering the adversarial attacks on the Internet of vehicles in the past. Alharbi et al. [58][8] proposed a framework for authentication based on Blockchain technology as they claimed it could add more security to the authentication process. In this framework, the one-time password (OTP) is encrypted and sent to the application/website to complete the authentication process. This system was claimed to be safer than SMS-based authentication mechanisms, but it was less efficient in terms of time efficiency. Wu et al. [59][11] proposed an out-of-band 2factor authentication mechanism for IoT devices by use of blockchain to enable flexible, secure, and reliable authentication [60][61][62][63][64][102,103,104,105,106]. The overheads of blockchain use, however, were high. Table 14 summarizes all the studies related to MFA and Blockchain.
Table 14.
Summary of Reviewed MFA and Blockchain Technology Papers.
| Study |
|---|
| Technologies Mentioned | Advantage/Contribution | Disadvantage/Gap | |||
|---|---|---|---|---|---|
| MFA | BC | 3/4/5G | |||
| [95] | ✓ | ✓ | A robust and effective system for fragile communications between two nodes. | Vulnerable to access attacks. | |
| [93] | ✓ | The authentication mechanism for 5G enabled IoT networks in the form of a service. | Not an MFA-based technique. | ||
| [96] | ✓ | ✓ | The flexible 3-factor authentication mechanism for various kinds of applications that are based on 5G multiservice systems. | Costly in terms of time efficiency. | |
| [92] | ✓ | ✓ | Provides a multifactor authentication procedure for WSNs in recent network applications and may be extendible to future network advancements such as 6G. | Vulnerable to the collision of users and desynchronization attacks. | |
| [98] | ✓ | ✓ | Multiple server technologies are used to ensure that performance is quick and transparent. | Technique still poses a communication cost as it integrates biometrics, password, and smart card authentication. | |
| [97] | ✓ | ✓ | An adaptable and decomposable 3-factor authentication system that can be applied simultaneously to ensure efficiency and speed. | Further testing and real-time application are required. | |
| [32] | ✓ | ✓ | ✓ | Hydro Raindrop multifactor authentication technology to conduct 2FA for WordPress. | Not experimental in nature. |
| [10] | ✓ | ✓ | ✓ | BPAS for ensuring accuracy as well as trust in the systems. | A lack of support for batch verification for an optimized verification in form of blocks of data and hence reduce the load on the resource consumption. |
| [15] | ✓ | ✓ | ✓ | Embedded Digital Signature-based MFA suitable technique for countering the adversarial attacks. | Overheads are high. |
| [8] | ✓ | ✓ | ✓ | More security to the authentication process as compared to SMS-based authentication protocols. | This system was claimed to be safer than SMS-based authentication mechanisms, but it was less efficient in terms of time efficiency. |
| [11] | ✓ | ✓ | ✓ | Flexible, secure, and reliable authentication. | The overheads of blockchain use, however, were high. |
| Study | Technologies Mentioned | Advantage/Contribution | Disadvantage/Gap | ||
|---|---|---|---|---|---|
| MFA | BC | 3/4/5G | |||
| [50] | ✓ | ✓ | A robust and effective system for fragile communications between two nodes. | Vulnerable to access attacks. | |
| [48] | ✓ | The authentication mechanism for 5G enabled IoT networks in the form of a service. | Not an MFA-based technique. | ||
| [51] | ✓ | ✓ | The flexible 3-factor authentication mechanism for various kinds of applications that are based on 5G multiservice systems. | Costly in terms of time efficiency. | |
| [47] | ✓ | ✓ | Provides a multifactor authentication procedure for WSNs in recent network applications and may be extendible to future network advancements such as 6G. | Vulnerable to the collision of users and desynchronization attacks. | |
| [53] | ✓ | ✓ | Multiple server technologies are used to ensure that performance is quick and transparent. | Technique still poses a communication cost as it integrates biometrics, password, and smart card authentication. | |
| [52] | ✓ | ✓ | An adaptable and decomposable 3-factor authentication system that can be applied simultaneously to ensure efficiency and speed. | Further testing and real-time application are required. | |
| [20] | ✓ | ✓ | ✓ | Hydro Raindrop multifactor authentication technology to conduct 2FA for WordPress. | Not experimental in nature. |
| [57] | ✓ | ✓ | ✓ | BPAS for ensuring accuracy as well as trust in the systems. | A lack of support for batch verification for an optimized verification in form of blocks of data and hence reduce the load on the resource consumption. |
| [19] | ✓ | ✓ | ✓ | Embedded Digital Signature-based MFA suitable technique for countering the adversarial attacks. | Overheads are high. |
| [58] | ✓ | ✓ | ✓ | More security to the authentication process as compared to SMS-based authentication protocols. | This system was claimed to be safer than SMS-based authentication mechanisms, but it was less efficient in terms of time efficiency. |
| [59] | ✓ | ✓ | ✓ | Flexible, secure, and reliable authentication. | The overheads of blockchain use, however, were high. |
