
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Thorsten Reimann | + 2904 word(s) | 2904 | 2021-05-18 08:15:59 | | | |
| 2 | Peter Tang | Meta information modification | 2904 | 2021-05-19 11:35:19 | | | | |
| 3 | Thorsten Reimann | Meta information modification | 2904 | 2021-05-19 14:58:50 | | | | |
| 4 | Peter Tang | Meta information modification | 2904 | 2021-05-20 03:06:04 | | |
Video Upload Options
A microgrid is an independent power system that can be connected to the grid or operated in an islanded mode. This single grid entity is widely used for furthering access to energy and ensuring reliable energy supply.
1. Introduction
2. Microgrid and Benchmarking
2.1. Microgrid Objectives and Functions
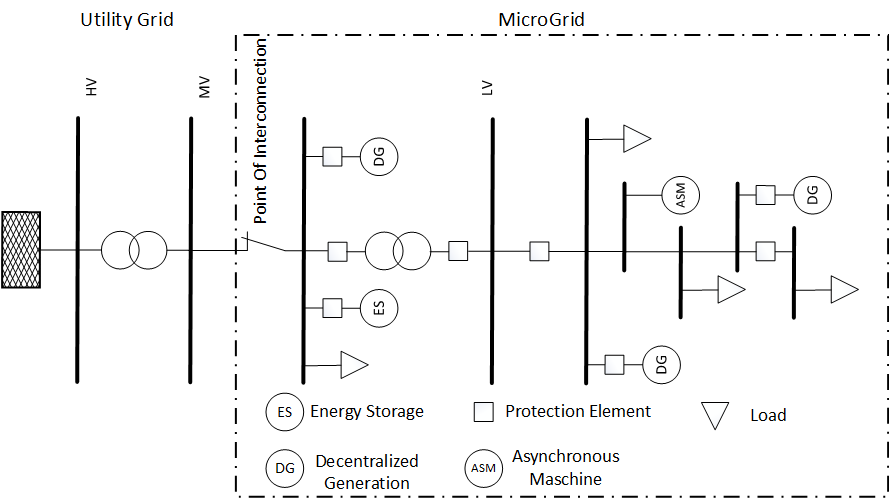
2.2. Standards and Technical Specifications
|
Abbreviation |
Title |
Date of Issue |
|---|---|---|
|
Standard |
||
|
IEEE 1547.4 |
IEEE Guide for Design, Operation, and Integration of Distributed Resource Island Systems with Electric Power Systems |
07-2011 |
|
IEEE 2030 |
IEEE Guide for Smart Grid Interoperability of Energy Technology and Information Technology Operation with the Electric Power System (EPS), End-Use Applications, and Loads |
09-2011 |
|
IEEE 2030.2 |
IEEE Guide for the Interoperability of Energy Storage Systems Integrated with the Electric Power Infrastructure |
03-2015 |
|
IEEE 2030.3 |
IEEE Standard Test Procedures for Electric Energy Storage Equipment and Systems for Electric Power Systems Applications |
06-2016 |
|
IEEE 2030.7 |
IEEE Standard for the Specification of Microgrid Controllers |
12-2017 |
|
IEEE 2030.8 |
IEEE Standard for the Testing of Microgrid Controllers |
06-2018 |
|
IEEE 2030.9 |
IEEE Recommended Practice for the Planning and Design of the Microgrid |
03-2019 |
|
IEC 62898-1 |
Microgrids—Part 1: Guidelines for microgrid projects planning and specification |
05-2017 |
|
IEC 62898-2 |
Microgrids—Part 2: Guidelines for operation |
09-2018 |
|
IEC 62898-3-1 |
Microgrids—Part 3-1: Technical requirements— Protection and dynamic control |
09-2020 |
|
IEC 62898-3-2 |
Microgrids—Part 3-2: Technical requirements— Energy management systems |
Expected in 12-2022 |
|
IEC 62898-3-3 |
Microgrids—Part 3-3: Technical requirements— Self-regulation of dispatchable loads |
Expected in 12-2021 |
|
DIN EN 50160 |
Voltage characteristics of electricity supplied by public electricity networks |
11-2020 |
|
Grid codes for interoperability with the electrical power system/grid |
||
|
Commission Regulation (EU) 2016/631 |
Establishing a network code on requirements for grid connection of generators |
04-2016 |
|
Directives |
||
|
Directive 2009/72/EC |
Common rules for the internal market in electricity and repealing Directive 2003/54/EC |
07-2019 |
|
FERC Order 888 |
The Federal Energy Regulatory Commission’s Open Access Rule |
1996 |
|
IT-SiG 2.0 |
Draft of a second law to promote the security of information technology systems (title translated from German) |
05-2020 |
|
BSI-KritisV |
Decree on the regulation of critical infrastructures according to the BSI-Act (title translated from German) |
04-2016 |
|
NISRIR 7628 |
Guidelines for Smart Grid Cybersecurity |
07-2014 |
2.3. Microgrid Test-Beds
|
Application (Location) |
Name (Organization) |
Voltage Level |
Rated Power (kW) |
Specific Test |
Site Available |
|---|---|---|---|---|---|
|
Mixed, AC (Canada, Senneterre) |
Boralex planned islanding (Hydro Quebec) |
25 kV |
8750 |
Transient response, outage solution |
− |
|
Test system, AC (US, Wisconsin—Madison) |
UW microgrid (University of Wisconsin—Madison) |
<1 kV |
− |
Investigation controls diesel generators |
yes |
|
Residential, AC (The Netherland, Bronsbergen) |
Bronsbergen Holiday Park (CONTINUON) |
<1 kV |
315 |
Central control |
− |
|
Residential, AC (US, Columbus, OH) |
CERTS testbed (CERTS) |
<1 kV |
173 |
Power quality optimization and energy management |
yes |
|
Test microgrid, DC (Italy, -) |
CESI RICERCA DER test microgrid (CESI) |
<1 kV |
251 |
Local and supervisory control with fast transients |
yes |
|
Residential, AC (Greece, Kythnos Island) |
Kythnos island microgrid (CRES) |
<1 kV |
102 |
Islanded |
yes |
|
Residential and small business, AC (Germany, Kassel) |
SysTec LV smart grid and MV hybrid system test bench (IEE) |
<1 kV/20 kV |
120/500 |
Islanding switches Local und supervisory control |
− |
|
Test system, AC (UK, Manchester) |
Microgrid/flywheel energy storage laboratory prototype (University of Manchester) |
<1 kV |
42 |
Intelligent control |
− |
|
Test system, AC (Japan, Gunma) |
Test network at Akagi (CRIEPI) |
6.6 kV |
1775 |
Algorithms for day-ahead planning |
yes |
|
Rural grid, AC (Japan, Kyotango) |
Kyoto eco-energy project (NEDO) |
MV |
450 |
Internet-based communication for DER |
− |
|
Residential, AC (-) |
CIGRE low voltage distribution benchmark system (CIGRE) |
<1 kV |
99 |
Control options for DER |
− |
|
Mixed loads, AC (-) |
IEC microgrid benchmark (IEC) |
25 kV |
16,200 |
Setting of optimal protection systems |
− |
3. Assessment Criteria for Microgrid Operation and Control
3.1. Microgrid Reliability
3.2. Use of Distributed Local Resources
-
Demand-side management (DSM);
-
Dispatch optimization (DO);
-
Forecasting module (FM).
3.3. Cybersecurity
References
- Sophie Marchand; Cristian Monsalve; Thorsten Reimann; Wolfram Heckmann; Jakob Ungerland; Hagen Lauer; Stephan Ruhe; Christoph Krauß; Microgrid Systems: Towards a Technical Performance Assessment Frame. Energies 2021, 14, 2161, 10.3390/en14082161.
- Marnay, C.; Chatzivasileiadis, S.; Abbey, C.; Iravani, R.; Joos, G.; Lombardi, P.; Mancarella, P.; von Appen, J. Microgrid Evolution Roadmap. In Proceedings of the Smart Electric Distribution Systems and Technologies (EDST), 2015 International Symposium on IEEE, Vienna, Austria, 8–11 September 2015; pp. 139–144.
- Oleinikova, I.; Hillberg, E. Micro vs MEGA: Trends Influencing the Development of the Power System. May 2020. Available online: (accessed on 1 March 2021).
- Ackeby, S.; Tjäder, J.; Bastholm, C. The role and interaction of microgrids and centralized grids in developing modern power systems. Cigrée Electricity Supply to Africa and Developing Economies: Challenges and Opportunities. In Proceedings of the 8th Southern Africa Regional Conference, Cape Town, South Africa, 14–17 November 2017.
- IEEE 2030.7-2017. IEEE Standard for the Specification of Microgrid Controllers; IEEE Std: Piscataway, NJ, USA, 2018.
- U.S. Department of Energy, Office of Electricity Delivery and Energy Reliability Smart Grid R&D Program. DOE Microgrid Workshop Report; U.S. Department of Energy: Washington, DC, USA, 2011; pp. 1–32.
- 60050-617. Amendment 2—International Electrotechnical Vocabulary (IEV)—Part 617: Organization/Market of Electricity. 2017. Volume 01.040.29. Available online: (accessed on 1 March 2021).
- Olivares, D.E.; Mehrizi-Sani, A.; Etemadi, A.H.; Cañizares, C.A.; Iravani, R.; Kazerani, M.; Hajimiragha, A.H.; Gomis-Bellmunt, O.; Saeedifard, M.; Palma-Behnke, R.; et al. Trends in microgrid control. IEEE Trans. Smart Grid 2014, 5, 1905–1919.
- Soshinskaya, M.; Crijns-Graus, W.H.J.; Guerrero, J.M.; Vasquez, J.C. Microgrids: Experiences, barriers and success factors. Renew. Sustain. Energy Rev. 2014, 40, 659–672.
- Basso, T.; Hambrick, J.; DeBlasio, D. Update and review of IEEE P2030 Smart Grid Interoperability and IEEE 1547 interconnection standards. In Proceedings of the Innovative Smart Grid Technologies (ISGT), Washigton, DC, USA, 16–20 January 2012; pp. 1–7.
- Papathanassiou, S.; Hatziargyriou, N.; Strunz, K. A benchmark low voltage microgrid network; Technol. impacts Dev. Oper. Performances. In Proceedings of the CIGRE Symposium: Power Systems with Dispersed Generation, Athens, Greece, 13–16 April 2005; pp. 1–8.
- Lidula, N.W.A.; Rajapakse, A.D. Microgrids research: A review of experimental microgrids and test systems. Renew. Sustain. Energy Rev. 2011, 15, 186–202.
- Naily, N.E.; Saad, S.M.; El Misslati, M.M.; Mohamed, F.A. Optimal Protection Coordination for IEC Microgrid Benchmark Using Water Cycle Algorithm. In Proceedings of the 10th International Renewable Energy Congress (IREC), Sousse, Tunisia, 26–28 March 2019; pp. 1–6.
- Bidram, A.; Davoudi, A. Hierarchical structure of microgrids control system. IEEE Trans. Smart Grid 2012, 3, 1963–1976.
- Shayeghi, H.; Shahryari, E.; Moradzadeh, M.; Siano, P. A survey on microgrid energy management considering flexible energy sources. Energies 2019, 12, 2156.
- Meyabadi, A.F.; Deihimi, M.H. A review of demand-side management: Reconsidering theoretical framework. Renew. Sustain. Energy Rev. 2017, 80, 367–379.
- Gandhi, O.; Rodriguez-Gallegos, C.D.; Srinivasan, D. Review of optimization of power dispatch in renewable energy system. In Proceedings of the IEEE PES Innovative Smart Grid Technolologies, Melbourne, VIC, Austalia, 28 November–1 December 2016; pp. 250–257.
- Sobri, S.; Koohi-Kamali, S.; Rahim, N.A. Solar photovoltaic generation forecasting methods: A review. Energy Convers. Manag. 2018, 156, 459–497.
- Fallah, S.N.; Deo, R.C.; Shojafar, M.; Conti, M.; Shamshirband, S. Computational intelligence approaches for energy load forecasting in smart energy management grids: State of the art, future challenges, and research directions. Energies 2018, 11, 596.
- Jiang, L.; Hu, G. A Review on Short-Term Electricity Price Forecasting Techniques for Energy Markets. In Proceedings of the 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2018; pp. 937–944.
- Li, Z.; Shahidehpour, M.; Aminifar, F. Cybersecurity in Distributed Power Systems. Proc. IEEE 2017, 105, 1367–1388.
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J. Survey of intrusion detection systems: Techniques, datasets and challenges. Cybersecurity 2019, 2, 384.
- Kummerow, A.; Rösch, D.; Monsalve, C.; Nicolai, S.; Bretschneider, P. Challenges and opportunities for phasor data based event detection in transmission control centers under cyber security constraints. In Proceedings of the IEEE Milan PowerTech, Milano, Italy, 23–27 June 2019; pp. 3–8.
- Khurana, H.; Hadley, M.; Lu, N.; Frincke, D.A. Smart-grid security issues. IEEE Secur. Priv. 2010, 8, 81–85.
- Ryan, M.D. Cloud computing security: The scientific challenge, and a survey of solutions. J. Syst. Softw. 2013, 86, 2263–2268.
- Metke, A.R.; Ekl, R.L. Security Technology for Smart Grid Networks. IEEE Trans. Smart Grid 2010, 1, 99–107.
- Kuntze, N.; Rudolph, C.; Bente, I.; Vieweg, J.; von Helden, J. Interoperable device identification in smart-grid environments. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–28 July 2011; pp. 1–7.
- Lauer, H.; Salehi, A.; Rudolph, C.; Nepal, S. User-centered attestation for layered and decentralized systems. In Proceedings of the Workshop on Decentralized IoT Security and Standards (DISS), San Diego, CA, USA, 18 February 2018.
- Rehmani, M.H.; Davy, A.; Jennings, B.; Assi, C. Software Defined Networks-Based Smart Grid Communication: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2019, 21, 2637–2670.
- McGraw, G. Software security. IEEE Secur. Priv. 2004, 2, 80–83.
- Klein, G.; Elphinstone, K.; Heiser, G.; Andronick, J.; Cock, D.; Derrin, P.; Elkaduwe, D.; Engelhardt, K.; Kolanski, R.; Norrish, M.; et al. seL4: Formal verification of an OS kernel. In Proceedings of the ACM SIGOPS 22nd Symposium on Operating Systems Principles; Big Sky, MT, USA, 11–14 October 2009, pp. 207–220.
- Godefroid, P.; Levin, M.Y.; Molnar, D. SAGE: Whitebox Fuzzing for Security Testing; ACM: New York, NY, USA, 2012; Volume 55.





