
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Gabriel Souto Fischer | -- | 1041 | 2024-02-28 03:07:55 | | | |
| 2 | Catherine Yang | -8 word(s) | 1033 | 2024-02-28 03:57:09 | | | | |
| 3 | Catherine Yang | Meta information modification | 1033 | 2024-02-28 03:57:37 | | |
Video Upload Options
RFID Technology is an automatic identification technology, which works through radio signals, retrieving and storing data remotely. It is used in hundreds, or perhaps even thousands, of applications with the aim of collecting data about objects in order to identify ways to solve everyday problems.
1. RFID technology
There are several devices and approaches capable of bringing the Internet of Things paradigm into the real world. Among them we can mention Radio Frequency Identification Technology, commonly known by the acronym RFID, which is a wireless identification technology[1] that allows locate physical objects and connect them to the virtual world[2].
According to Pereira[3], RFID Technology is an automatic identification technology, which works through radio signals, retrieving and storing data remotely. According to Landt[4] regardless of whether we want it or not, RFID technology is an integral part of our lives. It is used in hundreds, or perhaps even thousands, of applications with the aim of collecting data about objects in order to identify ways to solve everyday problems. In recent years, the technology has emerged from obscurity into the main applications, allowing remote identification, unlike barcode identification technology that only allows identification in front of a beam of light, and in addition, while the barcode stores just one type of information, Tags support, in addition to identification, a variety of additional information, which can range from the name of the manufacturer, and types of products, to environmental factors such as, for example, temperature[4]. For an RFID system to work, some components are necessary, among which we can mention the three main ones: Tags RFID (Transponder), the RFID Reader (Transceiver), and the Middleware (Figure 1).
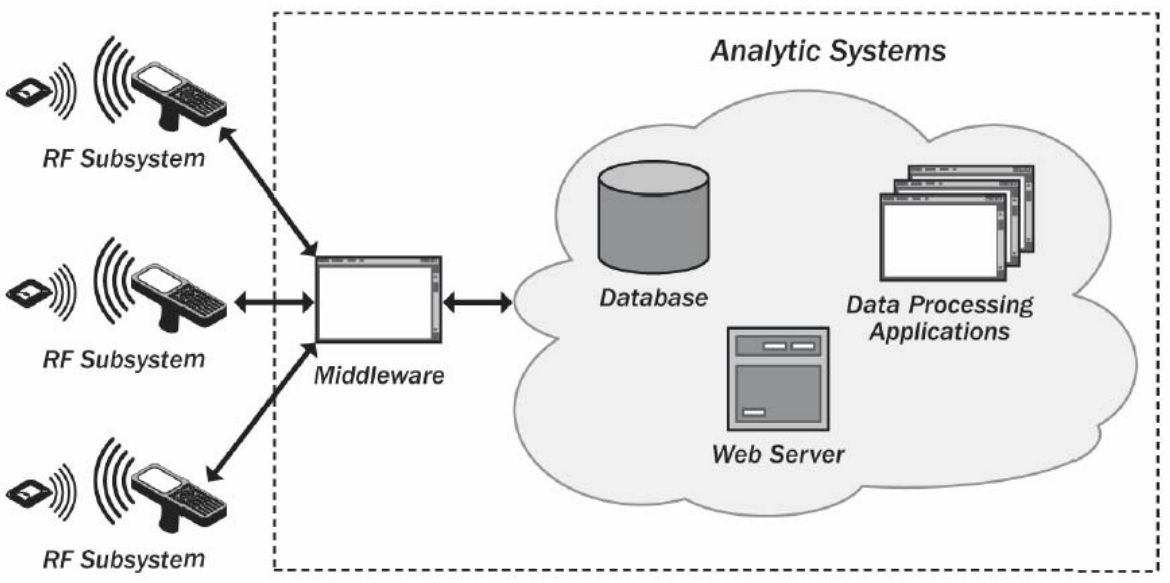
Figure 1. RFID system' components.
2. Tag RFID
Tags are small physical circuits that aim to attach logical data to a physical object. Each tag has its own mechanism for storing data and a way of sending it, so we can say that they have at least three parts: an antenna, a semiconductor chip connected to this antenna and some form of encapsulation[4]. In addition to the characteristics presented, tags can also have various forms, from common rectangular cards (plastic or paper), to circular cards, stickers or even in the form of injectables. They can also have various dimensions[5]. Additionally, there are many other not-so-common features, such as the ability for your content to be re-recorded, or to be deactivated or activated remotely[3]. They can be divided into two main groups: active tags and passive tags. In addition to these, there are also Semi-Active and Semi-Passive Tags.
Passive tags (Figure 2) are those that do not have their own energy sources, being powered directly by the reader[6]. They are only activated when they are within range of a reader, and the energy received is used to power the internal circuit, returning the information contained in the tag to the device. So for the tags to work, it is not enough for them to be within reach of a reader, but also for the reader to be able to provide enough power to power the tag so that it can establish communication with the device[3].
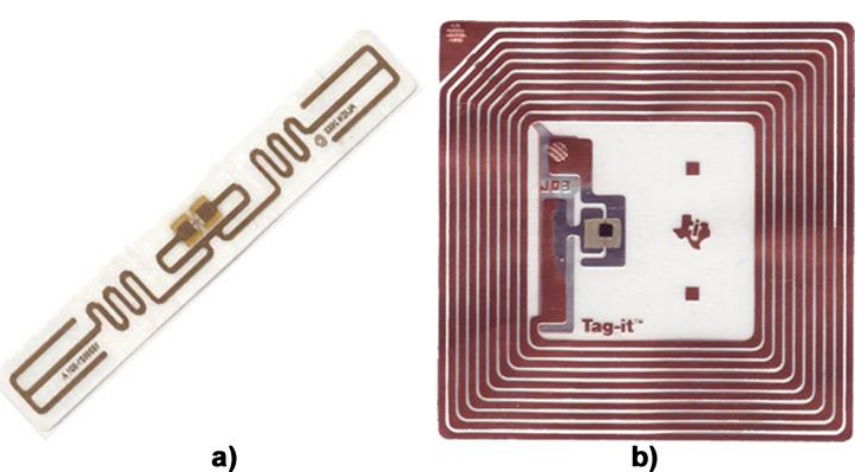
Figure 2. a) Passive Tag UHF; b) Printed circuit of a passive tag.
Active tags (Figure 3) are those that require their own energy source, generally an integrated battery, or an infrastructure that provides external energy[4], allowing tags perform writing and reading operations remotely[7]. Unlike passive tags, they do not depend on the reader to be powered, making the range greater as the received signal does not need to be so strong as to generate energy[3]. Therefore, they can not only communicate over greater distances, but also respond to weaker signals[8].

Figure 3. Active tag.
Semi-Active Tags are nothing more than active tags that remain deactivated until they receive a signal from the reader to activate them. Just like active tags, they have a greater reach compared to passive tags. The big advantage of this model is that the battery can have a longer lifespan, since the tag does not remain active all the time. However, they have the major disadvantage of activation time, which may be unacceptable depending on the application[8]
Semi-Passive Tags have their own energy source to power the internal circuit, but not to produce return signals[8] Thus, the range of action is increased since the energy absorbed by the antenna is used only for communication with the reader[3]
3. Reader
A Reader (Transceiver) is the device that allows communication, interpretation and reading of data contained in RFID tags that are within the range of its antenna. Coverage can vary from a few centimeters to several meters, depending on the type of tag and frequency used for communication[3]. We can divide readers into three groups: fixed, mobile and handheld. Fixed readers (Figure 4) are those mounted on fixed structures, generally fixed to walls.

Figure 4. Fixed reader.
Mobile readers are those mounted on mobile equipment, generally used in the trade of goods, such as forklifts and pallet trucks. And Handheld are the readers used by operators who read tags (Figure 5)

Figure 5. Motorola MC9190-Z Handheld reader.
4. Middleware
According to Pereira[3], Middleware is the fundamental element for any implementation of RFID systems and must have some essential characteristics:
- Data filtering and aggregation: The middleware must receive all data received by readers and send only the data they really need to applications, filtering and eliminating unnecessary data.
- Data distribution: The middleware must be responsible for delivering the data captured by the readers to the correct applications. In a system composed of several applications, each of them must receive only the interesting data for its own processing.
- Reading and writing: The middleware must be able to read the information contained in tags and, if they allow and are interesting for the application, write new data to tags.
- Reader management: The middleware must have the ability to manage the various equipment present in the system.
- Security: middleware must be prepared to collect information from tags in a protected manner, filtering the data to prevent possible attacks on the system.
- Performance and Scalability: The middleware must take into account the current needs of the system, and be prepared for the needs foreseen for the future and the expected developments in technology.
References
- RYU, W.; KWON, J.; HONG, B. Generation of RFID Test Datasets Using RSN Tool.Personal Ubiquitous Comput., London, UK, UK, v. 17, n. 7, p. 1409–1419, Oct. 2013.
- PEDRAZA, G.; GARCÍA, I.; DEBBABI, B. An RFID Architecture Based on anEvent-oriented Component Model. In: FOURTH ACM INTERNATIONAL CONFERENCEON DISTRIBUTED EVENT-BASED SYSTEMS, 2010, New York, NY, USA.Proceedings. . . ACM, 2010. p. 87–88. (DEBS ’10).
- PEREIRA, C. L. A. Dispositivos de Identificação. 2012. 127 p. Master Thesis (Mestrado emSistemas e Tecnologias de Informação para as Organizações). — Instituto Politecnido deViseu, Escola Superior de Tecnologia e Gestão de Viseu, Portugal, 2012
- LANDT, J. The history of RFID. IEEE Potentials, New York, NY, USA, v. 24, n. 4, p. 8–11,Oct. 2005.
- NEIVA, J. P. B. Localização e Orientação Indoor com recurso à Tecnologia RFID. 2012.78 p. Master Thesis (Mestrado Integrado em Engenharia Electrotecnica e de Computadores) —Faculdade de Engenharia da Universidade de Porto, Portugal, 2012.
- HOANG, B.; CAUDILL, A. RFID. IEEE Emerging Technology portal, USA, 2012.
- BERNARDO, C. G. A tecnologia RFID e os benefícios da etiqueta inteligente para osnegócios. Revista Eletrônica Unibero de Iniciação Científica, São Paulo, SP, Brasil, 2004
- MOREIRA, P. A. T. GESTÃO DE CONTROLO DE ACESSOS. 2008. 241 p. Master Thesis(Mestrado Integrado em Engenharia Electrotecnica e de Computadores) — Faculdade deEngenharia da Universidade de Porto, Portugal, 2008





