You're using an outdated browser. Please upgrade to a modern browser for the best experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Adnan M. Abu-Mahfouz | -- | 8609 | 2024-02-15 17:16:12 | | | |
| 2 | Sirius Huang | Meta information modification | 8609 | 2024-02-17 02:07:31 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Musonda, S.K.; Ndiaye, M.; Libati, H.M.; Abu-Mahfouz, A.M. IoT Communication in Mining Environments. Encyclopedia. Available online: https://encyclopedia.pub/entry/55075 (accessed on 26 December 2025).
Musonda SK, Ndiaye M, Libati HM, Abu-Mahfouz AM. IoT Communication in Mining Environments. Encyclopedia. Available at: https://encyclopedia.pub/entry/55075. Accessed December 26, 2025.
Musonda, Sonile K., Musa Ndiaye, Hastings M. Libati, Adnan M. Abu-Mahfouz. "IoT Communication in Mining Environments" Encyclopedia, https://encyclopedia.pub/entry/55075 (accessed December 26, 2025).
Musonda, S.K., Ndiaye, M., Libati, H.M., & Abu-Mahfouz, A.M. (2024, February 15). IoT Communication in Mining Environments. In Encyclopedia. https://encyclopedia.pub/entry/55075
Musonda, Sonile K., et al. "IoT Communication in Mining Environments." Encyclopedia. Web. 15 February, 2024.
Copy Citation
While a robust and reliable communication network for monitoring the mining environment in a timely manner to take care of people, the planet Earth and profits is key, the mining environment is very challenging in terms of achieving reliable wireless transmission.
reliability
LoRaWAN
mining environment
Internet of Things (IoT) communication
mission-critical
telemetry and alarms
1. Introduction
IoT-based monitoring systems employing advanced sensing, communication systems and information systems are needed in mining to specifically deal with health and safety, environmental issues, earth crust monitoring, transportation management, gas detection, fire prevention and detection, conveyor belt monitoring, water hazards and quality and miner tracking [1]. There is particularly a need for reliable wireless underground communication techniques for the IoT to address incidents and escalate rescue operations [1][2]. However, wireless communication is very difficult in underground mines because of irregular, confined shapes and rough environments. The following sections will look at technologies being implemented for the IoT in mines and their applications, strengths, weaknesses and records of reliability. The technologies covered are classified as licensed and unlicensed; long-range, medium-range and short-range; and cellular and non-cellular, as shown in Figure 1.
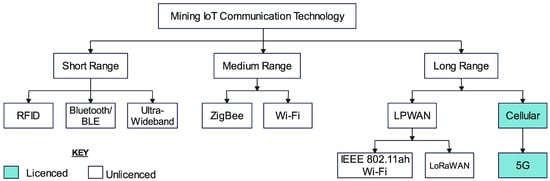
Figure 1. Classification of mining IoT technologies.
2. Radio-Frequency Identification (RFID)
RFID, also known as wireless identification, uses radio frequencies (RFs) to read data stored in a contactless tag, making it useful for identifying items. It is an improvement of barcode technology meant to address its limitations; thus, it has a high recognition rate, is not affected by the direction of access and can read or modify multiple pieces of information simultaneously. RFID is classified according to the frequency band used: low-frequency RFID (30–500 kHz), high-frequency RFID (10–15 MHz) and ultra-high-frequency (UHF)/microwave RFID (850–950 MHz, 2.4–3.5 GHz and 5.8 GHz) [3][4]. It has different strengths and weaknesses depending on the band used.
2.1. Application in Mining
RFID is actively used in mines for localisation and tracking applications [2]. Specific applications include efficient equipment operation and worker safety, where receivers are placed at mine entrances and major workshops and RFID tags are installed on mine equipment and workers’ hard hats. RFID is also used to manage logistics in mines, vehicle operations and worker time and attendance. For applications that involve the location of workers, RFID tags are embedded in lamp batteries. RFID is also used in reduction furnaces to automate the process and establish a systematic quality control system.
2.2. Strengths and Weaknesses
Low-frequency RFID has the advantages of short recognition distance, relatively slow recognition speed, low performance degradation and low price. High-frequency RFID can recognise multiple tags, while microwave RFID has an excellent recognition rate even at long distances. Data on tags are more secure because they are hidden from plain sight and are represented by digital signals. Data can also be encrypted such that only specialised equipment can read the data. It is also important to note that there are three types of RFID tags in terms of power supply: passive, semi-passive and active. Passive tags do not have an internal power source but rely on the power provided by the RFID reader. Passive tags thus have the advantage of an unlimited lifespan due to not being dependant on an internal power source.
On the other hand, interception is still possible since data are transmitted as digital signals. Additionally, microwave RFID in particular is greatly affected by environmental conditions, such as moisture and physical obstructions, which can limit the system as readers can have problems scanning through metallic and conductive objects. Compared to other wireless technologies and standards, such as ultra-wideband, Bluetooth and Zigbee, RFID is considerably inferior due to technological limitations [5].
2.3. Record of Reliability
With regard to the record of reliability of RFID, high-frequency RFID has high reliability for transmitted data, and ultra-high-frequency RFID in particular is reliable for capturing data with fast-moving objects, such as dump trucks. In addition, tags can be read away from the line of sight and can also track items in real time to provide important information about their location and status. The advantage of the passive tags stated above adds to the reliability of the system in terms of both unlimited lifespan and security because the tag can only be read if powered by a related reader. Studies and systems implemented in mining indicate that RFID is both accurate and reliable [4]. In relation to the IoT, however, RFID is used for data perception; therefore, it is equivalent to a sensor or end node. This places a limitation on it in that it depends entirely on other network technologies to transmit the data read to servers or cloud databases, as well as monitoring devices. The required distance between the RFID tag and reader is short: practically, 10 m for UHF RFID [4] and 100 m for microwave RFID [3].
3. Bluetooth/Bluetooth Low Energy (BLE)
Bluetooth is a short-range wireless technology standard that connects mobile devices for information exchange. It wirelessly exchanges data using ultra-high-frequency radio waves in an unlicensed (free-to-use) industrial, scientific and medical (ISM) frequency band specifically from 2.4 GHz to 2.485 GHz. Recently, measures have been introduced to improve transmission speed from the typical 720 kbps and to reduce energy consumption. For instance, version 4 of the standard enables periodic transmission of Bluetooth signals with a low-energy protocol. In addition, Bluetooth beacons can be used to identify indoor locations and detect environmental changes in various fields. Version 4.2, released in 2014, improves the ability to respond to the IoT due to the addition of an Internet protocol support profile (IPSP) to the standard. The latest version (5.0) improves the slow transmission speed of the low-energy protocol and adds the slot availability mask (SAM) function to block interference between IoT devices in advance, while versions 3.0 and 4.0 support 25 Mbps [3][6]. BLE (version 4 and higher) consumes less energy than standard Bluetooth (versions 1 to 3) because it was developed for applications that require only periodic data and not continuous streaming of data; thus, it remains in sleep constantly except when a connection is initiated [7].
3.1. Application in Mining
In mining, Bluetooth is used for localisation and tracking [2]. Investigational tests have also been undertaken to enable application of Bluetooth in underground intra-mine location-tracking systems, measuring the travel time of transport trucks using smartphones by means of Bluetooth beacon signals and employing a smartphone application that uses Bluetooth beacons to track and visualise objects in three dimensions (3D). Figure 2 is a block diagram of a Bluetooth position-sensing device and alert system to help miners move away from dangerous zones. It is worth noting that Bluetooth was less useful in the mining field in the past due to communication distance and transmission speed limitations, but due to continuous improvements, it is expected to have effective future applications in mining [3].
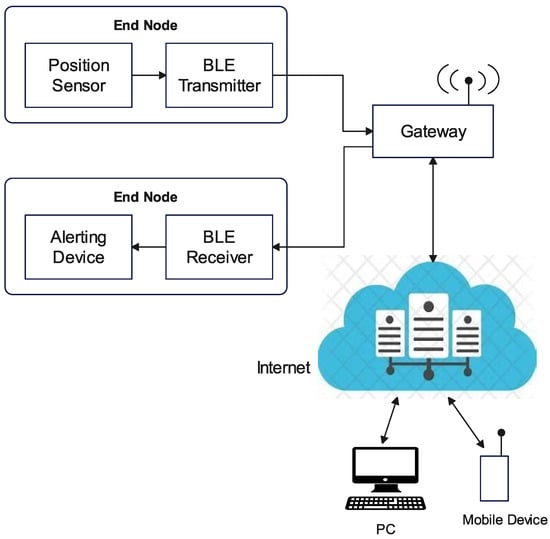
Figure 2. Block diagram of Bluetooth miner alert system.
3.2. Strengths and Weaknesses
Bluetooth makes it possible to wirelessly connect or pair devices to create a WPAN, enable wireless Internet connectivity and wireless synchronisation and conveniently exchange files without the trouble of using cables or hardware interfacing technology. The technology has extensive availability and accessibility in that most laptops and mobile devices (smartphones and tablet computers) have inbuilt Bluetooth hardware, and personal computers (PCs) that do not have the required hardware component can communicate with Bluetooth-enabled devices using a Bluetooth adapter. Additionally, the technology has seemingly become a standard feature of modern computers (laptops and mobile devices) as these include wireless speakers and headphones, and such devices, together with microphones, mice, etc., can be obtained at a reasonable cost. It is also considerably easy and convenient to use, since devices with built-in Bluetooth radios can easily be paired, and there is no need to install additional software or drivers to establish communication between devices enabled with the technology and no rigorous setup process. In addition, it is relatively energy-efficient, particularly for the BLE standard, the ultra-low-power requirement of which makes it ideal for small devices and wearable technologies that need minimal battery lifespan and a small form factor [6][8]. Standard Bluetooth can consume up to a maximum of 1 watt of power, while BLE consumes between 0.01 and 0.5 watts; thus, some BLE devises use 100 times less power [9].
Despite the outlined strengths, Bluetooth/BLE has limited operational range. The range depends on the class of radio used; thus, enabled devices can only establish and maintain communication as long as they are within the range limit. Class-one radios range from 20 to 30 m for commercial use and up to 100 m for industrial use cases, while class-two radios have a more limited range of up to 10 m and class three less than 10 m. With regard to energy consumption, however, Bluetooth can be energy-inefficient in real-world applications as it can significantly drain the battery life of a device, particularly if it remains turned on. In addition, for mobile devices that use their battery for different software processes and keep the hardware components running, a Bluetooth radio increases the power requirement of the device. Energy efficiency is also dependent on the specific class of the radio, with class-one radios being more power-intensive and requiring 100 milliwatts (mW) due to their comparatively longer range relative to classes two and three, which transmit at 2.5 mW and 1 mW [10]. Bluetooth has a slower data transmission rate compared to other hardware interfacing technologies, such as Wi-Fi Direct at 250 Mbps, USB 3.0 (wired) at 5 Gbps and at 40 Gbps. There are also security vulnerabilities as Bluetooth can be susceptible to denial-of-service attacks, eavesdropping, man-in-the-middle attacks, message modification and resource misappropriation. Although a standard has been implemented, there are still compatibility and functionality issues as a result of factors such as the version of Bluetooth used, drivers and profiles, etc. It is noteworthy that the low-energy (LE) technology of Bluetooth 4.0 is not compatible with other classic versions; hence, devices equipped with Bluetooth 4.0 that only have the LE technology component will not work with devices equipped with Bluetooth 2.0, and BLE will not work with classic Bluetooth. Upgradability is also a challenge for devices such as headsets or smartphones. Lastly, it has limited connection in the latest version (5.0), only supporting up to seven devices [6][8]. However, mesh topology can be used to expand the network, although the challenge with using this topology is that it may not be suitable for real-time communication due to connection establishment procedures that introduce delay [11].
3.3. Record of Reliability
Although a Bluetooth network supports fewer devices, the network forms a piconet and groups of piconets can be interconnected to form a scatternet [8], thus making it possible to considerably expand the network. However, a larger mesh network cannot be created to support long-distance communication [12]. Bluetooth can easily be updated and does not have interoperability issues as devices from different vendors can connect [8]. BLE is often viewed as the optimal technology for IoT applications because of two main reasons: low power consumption and the type of data exchanged [13]. BLE is optimised to transmit a small amount of data. This works well for IoT devices like sensors that just need to transfer state data. It is also accurate for indoor location-tracking applications [7]. Standard Bluetooth can transfer data in different formats, such as text, videos, pictures, etc., and the latest version (5.0) offers better speed than older versions [8]; thus, it could be suitable for future IoT applications. The latest Bluetooth technology uses the frequency-hopping spread spectrum (FH-SS), which protects data. FH-SS provides superior resistance to interference and multipath effects and also performs well in harsh environments. Additionally, spread spectrum modulation has high spectral efficiency and is heavily resistant to noise and malicious jamming [14]. Bluetooth technology is also reliable due to its long battery lifespan of about 5–10 years resulting from low power consumption, with the latest version using only a tenth of the power of the classic version. BLE has lower latency than classic Bluetooth, typically 6 milliseconds (ms) while that of the classic (standard) version is 100 ms [9]. Version 5.0 has greater reliability than the previous versions [8].
4. Zigbee
Zigbee is defined by the Institute of Electrical and Electronics Engineers (IEEE) 802.15.4 standard and is used to configure wireless personal area networks (WPANs) using small, low-power digital radios. It is relatively simpler and cheaper compared to Bluetooth or Wi-Fi and can be used to deploy a large number of devices in a wide area. It enables a wide range of communication using a mesh network and is suitable for applications requiring low transfer speeds, long battery life and security [3]. It operates in the 2.4 GHz band in most jurisdictions worldwide, though some devices use 784 MHz in China, 868 MHz in Europe and 915 MHz in the United States of America and Australia. It is a short-range wireless technology with typical transmission ranges of 10 to 100 m depending on power output and environmental characteristics. It supports low data rates ranging from 20 kbps (868 MHz) to 250 kbps (2.4 GHz), making it suitable for intermittent data transmission from a sensor or input device. It also relies on the carrier sense multiple access with collision avoidance protocol [15][16]. It is worth noting that the IEEE 802.15.4e standard has been released to enhance the original standard by introducing five different MAC behaviour modes, among which are time-slotted channel hopping (TSCH), deterministic and synchronous multichannel extension (DSME) and low-latency deterministic networks (LLDNs). These modes have features that improve the performance of Zigbee and its suitability for industrial communications [17].
4.1. Application in Mining
Zigbee is applied in conjunction with various sensors underground. For instance, it is used to detect environmental information related to gas concentrations, temperature and humidity in underground coal mines. A robot based on network communication using Zigbee can be employed to achieve this. Zigbee technology is also used to sound safety alarms. Gas-concentration, temperature and humidity sensors are placed on helmets, and Zigbee is used to transmit sensed data to systems on the ground so as to manage workers’ conditions. Sensors mounted on UAVs are also used to sense the underground mine environment and acquire location information with network communication performed using Zigbee [3]. It is also used for localisation and tracking [2].
4.2. Strengths and Weaknesses
Zigbee technology has strong node support and can support 6500 nodes. The nodes also act as intermediary devices, which helps in increasing the range and makes it easier to expand the network. It is suitable for devices with low power since it does not require much bandwidth; thus, devices such as object tags and sensors can be battery-operated. It is an alternative to Wi-Fi and Bluetooth, with the advantages of being a simpler and less expensive technology [18]. Although Zigbee is a short-range technology with typical ranges of 10 to 100 m, this can be extended by arranging the devices to form a mesh network. The structure of the technology is very flexible, and it has an easy installation process. The network is easy to maintain as this can even be achieved with the help of a remote control. In addition, the technology can be monitored and controlled easily. Across the network, loads are evenly distributed [18][19]. Figure 3 shows elements of a Zigbee mesh network.
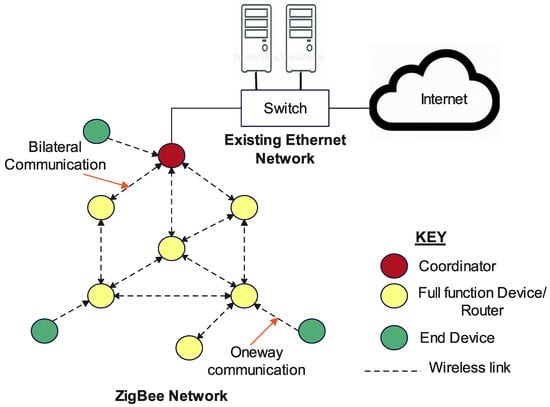
Figure 3. Elements of a Zigbee mesh network.
Zigbee technology is, however, only suitable for indoor applications and cannot be used for outdoor wireless communication systems due to its short coverage range. In instances where sensed data in an underground mine environment have to be monitored from the surface control room or remotely, Zigbee has range limitations; therefore, it has been integrated with cellular technologies to enable it to cover long distances [12][20]. The technology is prone to network interference due to overcrowding and channel noise since it uses the 2.4 GHz band, which is also used by Bluetooth, cordless phones, microwave ovens and other wireless devices. Another notable weakness is that it has a low transmission rate, lower than Bluetooth and Wi-Fi, and as such is not suitable for transmitting data at high speed. It still has compatibility issues with mainstream devices like smartphones, tablets, computers and laptops. It is not as secure as Wi-Fi, and its susceptibility to interference presents a security issue in that interference can cause loss of network service, theft of data from nodes and theft of entire nodes. Implementation of the technology can be expensive due to the size and range of the network being determined by the number of nodes, which entails that more nodes are required to cover a greater range. Other factors affecting cost are the availability of compatible products and devices and, depending on the use case, the level of complexity of the network. Lastly, better alternatives to standard wireless technologies are available, such as Z-Wave, which has a more extended range and better reliability and stability as it operates in the 908 MHz band [18][19].
4.3. Record of Reliability
The mesh topology used in Zigbee networks enhances the reliability of the network in that it forms a peer-to-peer network of nodes that allows a sensor (source) node to be out of range in relation to the collection (sink) node as long as other sensor nodes are in close proximity that can relay the data [12]. Additionally, mesh topology makes the network reliable because it improves the throughput, packet delivery rate (PDR) and security, thus enabling Zigbee nodes to create an underground wireless network that is more secure and delivers higher quality of service [21]. This also enables the network to expand and considerably increases its range. The transmitted signals are able to penetrate walls, making the technology not only useful for indoor but also mining environments. End nodes in this network do not just sense the environment but also have the capability to serve as coordinators and perform routing functions, and this provides better stability compared to using a single router, as is the case with Wi-Fi or Bluetooth [20][21]. The strengths listed above—namely, long battery life, low power consumption, ease of maintenance and even distribution of load—also make the technology reliable. The Zigbee network is an autonomous wireless sensor network (WSN); thus, to enable IoT and cloud services, it can be integrated with other communication technologies, such as Wi-Fi, Ethernet and the Global System for Mobile Communications (GSM). This adds positive notes to the technology in terms of reliability in that it can be IoT-based and it is possible to integrate other communication technologies, thus further increasing its range. However, this also brings a challenge because riding on GSM, for instance, to transmit data to remote locations or to enable IoT attracts charges from the cellular operators, thus increasing the cost. In addition, communication reliability is compromised since both quality of service and network availability depend on the prevailing conditions of the GSM network [12]. In terms of network capacity, there is also a limitation because Zigbee can connect up to 255 devices within a maximum of 100 m [15]. Zigbee networks do not support mobility, hence presenting a challenge when using them for miner safety in that if the miner moves out of range, there is no communication [20]. Added to this, as noted in relation to the weaknesses, is that it is prone to interference, hence compromising its communication reliability.
5. Wireless Fidelity (Wi-Fi)
Wi-Fi is a family of technologies defined by the IEEE 802.11 standard for short- to long-range wireless communication and is commonly used for closed or indoor environments. It uses 2.4 GHz and 5 GHz in the ISM band. In addition to IEEE 802.11, there are also the 802.11a/b/e/g/h/i/k/n/p/r/s/ac/ad/ax and 802.11be standards, which cover short- to medium-range communication. IEEE 802.11ac has additional features that make it possible to improve performance and speed and better manage interference by means of channel bonding, multiple-input and multiple-output (MIMO) and denser modulation. New generations of Wi-Fi allow nodes to operate at very high data rates of up to 7 Gbps for 802.11ad and 9.6 Gbps for 802.11ax. IEEE 802.11ax is enhanced further to include features that improve network capacity and delay, while IEEE 802.11ah Wi-Fi, which operates in the 900 MHz license-exempt band, is a low-data-rate and low-energy solution designed for IoT applications that can cover up to 1 km with 200 mW default power transmission at a minimum data rate of 100 kbps [15][22][23]. IEEE 802.11p, which provides 10 MHz bandwidth and a data transmission rate of up to 27 Mbps, supports intelligent transport systems for vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communication within a range of 1000 m. IEEE 802.11s is a mesh local area networking standard meant to increase Wi-Fi coverage through the use of a master AP to provide wireless backhaul to extenders, while 802.11be, also known as Wi-Fi 7, takes advantage of the large bandwidth available in the 6 GHz band to significantly reduce latency and enhance reliability. Wi-Fi 7 provides the standard with which the next generation Wi-Fi will be built [24][25].
5.1. Application in Mining
Wi-Fi—particularly the IEEE 802.11ax standard, also known as Wi-Fi 6—is used for underground mine coverage involving long distance roadways. It is also used for multi-function communication systems, dispatch communication and safety monitoring in coal mine tunnels. Additional applications include location tracking in underground mines to accurately locate mining personnel and determine their distribution and operating conditions in real time. Of course, in this case Wi-Fi acts as the core network for the sensors in the network. In open-pit mines, Wi-Fi technology is used for automated ticketing and tracking systems for monitoring surface-mine hauling operations [23][26][27][28][29]. The situation on the ground in the copper mining industry in Zambia is that Wi-Fi has been deployed in some underground mines to support sensing and monitoring, voice communication and surveillance systems.
5.2. Strengths and Weaknesses
Wi-Fi can be used in complex terrain in underground mines where optical fibre cannot reach easily and has the additional advantage that it does not depend on line-of-sight communication. It can also easily reach the blind spots in existing mobile network coverage. For underground communication, Wi-Fi 6 is better than 5G because it covers longer distances, thus providing wide network coverage, and has lower power consumption. It also has fast communication speed, with a typical downlink speed being 9.6 Gbps. For underground coal mines in particular, it meets the requirements of full wireless coverage. It is possible to cover a distance of 1.4 km through wireless signal stretching with four access points in the most difficult parts of the coal mine (i.e., the mining roadway, return air roadway and long-distance transportation roadway) [23][27]. This technology can be implemented underground using different topologies, such as linear (with redundancy appropriately provided), ring and mesh topologies, as illustrated in Figure 4 and Figure 5. IEEE 802.11p, released in 2010, is able to support high mobility requirements, has a longer range of up to 1 km and uses the less interference-prone ISM band of 5.9 GHz. Compared to Zigbee and Bluetooth, Wi-Fi has much lower latency and longer range.
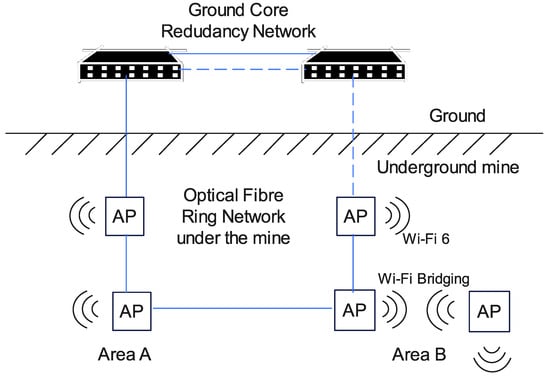
Figure 4. Wi-Fi ring network for underground communication [23].
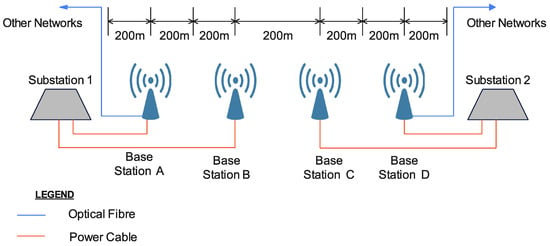
Figure 5. Wi-Fi linear network for long-distance underground roadway [23].
One of the notable challenges with Wi-Fi is that it cannot stand alone as a network since it does not have its own backbone but has to “lean on” a wired network, such as Ethernet. Wi-Fi 6 is still classified as a short-range technology because practically, with one access point at 2.4 GHz, it is only possible to cover 200–300 m [23]. Although mesh networking can be adopted for underground communication, multi-hop transmission throughputs decline while average delays increase with increased hops [28]. Despite the range being extended and delay decreased for Wi-Fi, power consumption is still high and the number of devices supported is still low (typically 250), except for 802.11ah, which is able to provide connectivity to thousands of devices within a radius of 1 km [15][22].
5.3. Record of Reliability
Wi-Fi 6 uses orthogonal frequency-division multiple access (OFDMA), which helps improve network delay and communication efficiency: communication delay is typically 10 ms. It uses transmit beam-forming technology to improve network capacity. It also has a dual-frequency signal output of 2.4 GHz and 5 GHz and the base station automatically adjusts the user frequency band through an internal control circuit to ensure communication quality and reliability. The 2.4 GHz signal has strong signal diffraction, anti-interference properties and a long transmission distance [23]. The wireless routers for Wi-Fi 6 consume 9 to 12 watts and depend on an external power source [23]; this does not meet the power requirements of the IoT. Additionally, according to the advantages stated above, Wi-Fi is reliable because it can be integrated with technologies such as Zigbee and Bluetooth. Applying a Wi-Fi mesh underground gives the technology higher flexibility and greater reliability in applications than WLAN and WSN, and it may be a preferred mine emergency communication system in the future. However, reliability factors such as throughput and delay are affected with increased hops [28]. With regard to the IoT, IEEE 802.11ah Wi-Fi is suitable for outdoor environments but unsuitable for remote and underground environments, and it has been highlighted as the most reliable long-range communication technology alongside LoRa/LoRaWAN in farming, where the IIoT is applied outdoors [22]. Thus, 802.11ah may be a suitable candidate for long-range surface IoT mining technologies. It also has features that enhance its communication reliability similarly to 802.11ac, such as OFDMA, downlink multi-user multiple-input and multiple-output (DL-MU-MIMO) and efficient modulation and coding schemes [15]. It is worth noting that one of the current IoT requirements is low data rates, and Wi-Fi notably supports high data rates, which makes it a promising technology for future IoT systems.
6. Ultra-Wideband (UWB)
UWB entails transmitting across a wide range of radio bandwidths from 500 MHz to several GHz. It is a short-range radio technology enabling high-bandwidth communication at very low energy levels and covers a large portion of the radio spectrum. The technology, previously known as “pulse radio”, has been with us since 1901 and has mostly been used in military communication applications. Currently, it is defined by IEEE 802.15.4a/z. The transmitter sends billions of pulses over a wide-spectrum frequency range while the receiver converts the pulses into data by identifying a recognisable pulse sequence delivered by the transmitter [30]. Therefore, UWB wireless communication technology is a carrier-free communication technology that does not use carriers but short energy pulse sequences, expanding the pulses to a frequency range through orthogonal frequency modulation or direct sequencing [31]. The frequency range for UWB is 3.1 to 10.5 GHz in the unlicensed band with a bandwidth of 500 MHz or more and data rate of up to 27 Mbps. In trials undertaken in an underground coal mine, the communication range between the transmitter and receiver was 28 m [30]. UWB has an added portion in the physical layer used to send and receive data packets specified as IEEE 802.15.4z. This serves as a critical extension not available in other technologies that allows for security techniques, such as cryptography and random number generation, to deter attackers from accessing the UWB communication [32]. Two modes of transmission are supported: ultra-short pulses in the picosecond range, which are also known as impulse radios, and subdividing the total UWB bandwidth into a set of broadband orthogonal frequency-division multiplexed channels. The first mode is cost-effective at the expense of degrading the signal-to-noise ratio and does not need the use of carriers, which makes the transmission less complex with simpler transceivers. The second mode uses the spectrum more efficiently and has better performance and data throughput at the expense of increased complexity and power consumption. The choice between the two modes of transmission depends on the application.
6.1. Application in Mining
UWB technology is used to estimate and track position in underground mines. Recently, new UWB modules for positioning and collision avoidance for human safety in non-explosive areas have been developed for use in underground mining operations. UWB technology is as an excellent and cost-effective technology that can be used for tracking and tracing people and machines in underground situations. To be specific, it is widely used in underground equipment positioning and information transmission in coal mines. In the future, UWB technology may be applied in self-driving vehicles underground or autonomous robots where line of sight is a necessary component for safe implementation [30][31][33].
6.2. Strengths and Weaknesses
UWB technology provides a high data rate and robust communication in dense multipath environments, as well as high performance and good positioning effects in non-visual environments [31][34]. Tests conducted in underground mine environments have shown that UWB communication does not experience signal interference from other networks, such as local WLAN or radio communication systems. It is also used concurrently in smartphones along with other technologies, such as Bluetooth, WLAN and the Global Positioning System (GPS), without any interference problems. Compared with Wi-Fi, Bluetooth, Zigbee and RFID, UWB has the advantages of low power consumption, high measurement accuracy and strong robustness in relation to multipath effects and non-line-of-sight environments [30][31][33]. An additional useful property of UWB is that it is permitted to use low carrier frequencies, where signals can easily pass through obstacles.
UWB depends on line of sight for accuracy, and the best range can experience loss of signal where there is no direct line of sight. Tests described in [30] for communication with sensors on moving targets show that UWB is only accurate for single-sensor location and tracking. Results obtained in multiple moving scenarios were not precise due to mutual shielding (shadowing) of sensors in the observed area.
6.3. Record of Reliability
As far as the record of reliability is concerned, UWB has the ability to transmit pulses at a rate of one per two nanoseconds, which contributes to its real-time precision. It is accurate and reliable for data transfer, positioning and tracking of employees. It also enables fast and reliable data transmission across small distances between 10 and 200 m. With regard to energy consumption, UWB can carry a huge amount of data using very little power: between 9 and 22 milliwatts [30][33]. When UWB employs time-of-flight techniques for positioning, reliability is enhanced and the performance is better because the signal can cover a large bandwidth, which provides a high resolution, hence resolving multipath effects and giving robust performance in indoor environments [33]. While ultrasonic and optical cameras fail to collect data in underground roadways of coal mines characterised by dust, water mist, significant impacts from noise and low light illumination, UWB has good positioning effects and works in these environments. Also noteworthy is that UWB is immune to interference since it has a significantly different spectrum [31][35]. Additionally, the low spectral density of UWB signals makes it less susceptible to the in-band interference of narrowband signals, as well as making it very secure since signals are difficult to detect [36]. The location accuracy of UWB is 10 cm and this is better than that of Bluetooth and Wi-Fi, which is around 150 cm. Therefore, UWB is preferred for applications requiring lower latency, better energy efficiency and accurate positioning, while Wi-Fi is preferred for high-data-rate communications. In addition, in the future, UWB could prove more successful than Bluetooth because of its superior speed, low cost, low power requirements, more secure transmission, superior location discovery and device ranging [32]. In the IoT, UWB is used for perception and, partly, transmission. UWB end nodes are used as sensors and actuators. Sensed data are transmitted wirelessly over short distances to a UWB receiver, which relies on other wireless or wired technologies to enable Internet connection and cloud services. This places a limitation on the UWB network but at the same time implies that it can be integrated with other technologies to increase its communication range and enable use with the IoT as illustrated in Figure 6.
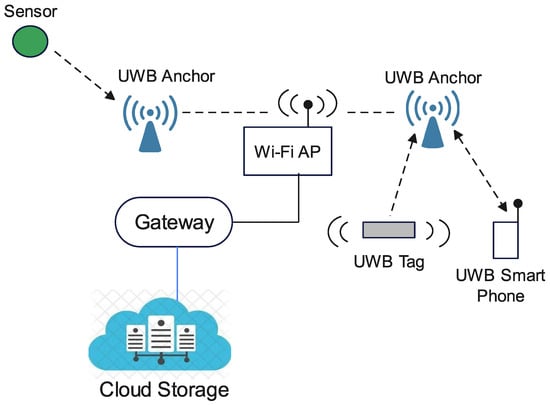
Figure 6. Enabling use of the IoT with an ultra-wideband network.
7. Fifth-Generation Cellular Technology (5G)
5G was set up by the industry consortium known as the 3GPP and is a new global wireless standard following the 1G, 2G, 3G and 4G networks. The 1G mobile network was for analogue voice signals, 2G was for digital voice signals, 3G combines digital voice signals and mobile data and 4G supports broadband mobile data; all of these have brought into 5G, which is designed to provide more connectivity and faster connection speeds. Like its predecessors, service area is divided into small geographical areas called cells but 5G uses higher frequency bands. The air interface defined by the 3GPP for 5G is known as New Radio (NR) and the specification is divided into two frequency bands: frequency range (FR) 1 (below 6 GHz) and FR 2 (24–54 GHz). FR 1 is also known as sub-6: it has a maximum channel of 100 MHz and the band widely used is 3.3–4.2 GHz. FR 2 has a minimum channel bandwidth of 50 MHz and maximum of 400 MHz, with two-channel aggregation supported in 3GPP release 15. Signals in this frequency range with wavelengths between 4 and 12 mm are called millimetre waves (mmwaves). 5G is much faster than 4G and 3G; for instance, the average speeds of 5G, 4G+ and 3G are 130–240 Mbps, 42 Mbps and 8 Mbps, respectively, while the maximum speeds are 1–10 Gbps (theoretical) for 5G and 300 Mbps in the case of 4G+. 5G utilises MIMO antennae to boost signals and capacity across the wireless network, supporting 1000 more devices per metre than 4G [37][38].
7.1. Application in Mining
Demonstration mines in China have successfully deployed 5G systems, and 5G-based mine IoT applications, such as unmanned driving, intelligent video, unmanned work surfaces, industrial control and intelligent robot inspection, have been or should soon be successfully implemented [39]. Despite the fact that the private 5G network is still in its infancy, China Mobile, Yangquan Coal Group and Huawei successfully built China’s lowest underground network at Xinyuan Coal Mine in Shanxi province. This private 5G network is located deep underground at 534 m and has an upload speed greater than 1 Gbps. It has enabled the launch of a 5G smart coal mine and three 5G-enabled unmanned applications involving the inspection of electromechanical chambers, operations on the coal face and comprehensive mechanised coal mine operations. This has benefited the mine in that it is possible to lower labour intensity and improve the security of workers [25]. Figure 7 shows the 5G deployment architectural diagram for an underground coal mine.
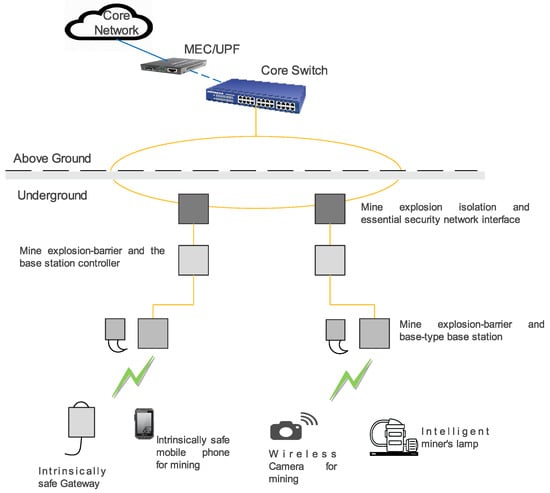
Figure 7. 5G deployment architectural diagram for an underground coal mine [40].
7.2. Strengths and Weaknesses
5G technology operates on a higher frequency band, which means that it has a wide channel bandwidth and supports a high number of devices per square kilometre and high speed. Compared with older techniques, 5G communication provides higher speed, greater capacity and lower latency, and when employed for the IoT, it allows the interconnection of diversified sensors in one framework. On the ground or surface, 5G has a superior communication range, offering multi-channel data return over long distances of up to 100 km [22][41]. Compared with 4G communication, the working power and RF energy of the 5G base station greatly improves its application underground, as the general requirement for transmission equipment underground is that the RF threshold power is less than or equal to 6 watts, thus making 5G safe underground. 5G supports ultra-reliable low-latency communication (URLLC) and massive machine-type communication (mMTC), making it suitable for safe production business scenarios involving the IoT in mines. It is also worth mentioning that, for industrial applications such as mining, it is possible to deploy private 5G networks exclusively designed for a single organisation. These share the advantages of public 5G networks and also simplify challenges such as interference management, as well as further reducing transmission delay, since the core network can be deployed locally [25][39].
The drawback of 5G is that it is not economically viable to deploy public 5G networks in remote locations; thus, it is unavailable in these locations where most mines exist. It also has high power consumption and requires complex devices (that is, base stations and end devices) since it is designed to process complex waveforms, such as voice and high-data services. In addition, it is not suitable for energy-constrained IoT devices and relies on long-term evolution machine-type communication (LTE-M) and narrowband IoT (NB-IoT) to support mMTC [22]. In coal mines, to be specific, there are challenges in achieving full wireless coverage with 5G because its wireless signal distance underground is short due to the signal being high-frequency with high diffraction loss; hence, it fails to meet the transmission demands of irregular roadways and to provide network coverage for the whole roadway [23]. Mine 5G suffers from multifactorial interference; for instance, in the mining roadway, the strong electrical equipment induces an alternating magnetic field at turn on and turn off that disrupts the normal operation of the base station and terminal of the mine 5G systems. Additionally, signal propagation is blocked by large-scale mechanical equipment, such as trains, scrapers and shearers, resulting in reflection scattering, phase mismatch and waveform distortion, which weakens the 5G signal. Underground substation equipment with coupling circuits, such as high-voltage distribution boxes, power boxes and relays, generates electromagnetic interference that interferes with 5G signals and affects the accuracy of signal transmission [39]. It also has an insufficient uplink rate; hence, studies are being conducted to improve its rate and communication reliability in underground mines [40][42].
7.3. Record of Reliability
5G is most suitable and reliable where precision is required and large amounts of real-time data need to be transmitted and processed [22]. 5G URLLC in particular has specific features in both the radio interface and the network architecture to enable shorter latency and high reliability. The strengths highlighted above—namely, high speed, high capacity and low latency—enable the technology to satisfy the requirements of IoT communications; specifically, high-quality data transmission with real-time monitoring. It is also suitable for surveillance systems with high-definition cameras, as these require high bandwidth. This makes 5G good for future IoT systems as it is a potential technology that can realise the interconnection of all “things”. In addition, private 5G, Wi-Fi 6 and Wi-Fi 7 networks are expected to coexist and complement each other, hence adding to the reliability of 5G [41]. Existing 5G anti-interference schemes follow the 3D model of the overground environment and are mainly based on MIMO technology and smart antennae, with MIMO technology improving system performance and increasing processing flexibility. MIMO technology has two basic elements: multiplexing and diversity. Multiplexing increases the system’s capacity by transmitting data along multiple independent paths, while diversity involves transmitting the same data along multiple independent paths to resist channel fading and improve transmission reliability. Smart antennae improve mobile communication quality by directing the wireless electromagnetic wave signals in the effective direction to reach the user and also solve problems in the mobile communication environment such as Rayleigh fading, multi-user interference and delay spread. To meet the radio frequency power specification in mines of less than or equal to 6 W, plate-shaped directional antennae with gain of 8 dBi are generally used in mine 5G base stations, which seriously restricts the application of massive MIMO and smart antenna technology in underground explosive environments. Two objectives for 5G that would make it possible to leverage URLLC are mMTC and critical machine-type communication (cMTC), with mMTC having been developed for the IoT. However, mMTC in 5G is fulfilled using LTE-M and NB-IoT, and there are no other dedicated solutions specified for 5G IoT. Although 5G meets the power requirements in underground mines, the expected performance for underground application scenarios has not been fully achieved due to the waste of bandwidth and resources [22][40]. In addition, spurs and crosstalk in the frequency domain are considered to be the greatest culprits leading to instability and inaccuracy, which in their effects influence the reliability of 5G signals [39].
8. LoRa and LoRaWAN
LoRaWAN is a wireless LPWAN technology and an open standard managed by the LoRa Alliance that defines the datalink layer of a wireless communication solution based on LoRa radios in the physical layer. LoRa is a modulation technology created by SemTech to standardise LPWANs based on the chirp spread spectrum technique and enables long-range datalinks, thus providing long-range communication at up to 5 km (urban) and 15 km (rural). In simpler terms, LoRaWAN is a wide-area network (WAN) based on LoRa, which is deployed in a star topology (star of stars) and is suitable for applications that require long-range or in-building communication among a large number of devices that have low power requirements and collect small amounts of data. LoRaWAN has two tiers, wireless links for connecting end nodes and a base station (gateway) and backend servers where network management and user applications are executed [43][44]. It operates in the unlicensed ISM band and uses fixed bandwidths of 125, 250 or 500 kHz. The ISM bands used for LoRa transmission are 863 to 870 MHz (Europe), 902 to 928 MHz (North America) and 470 to 510 MHz (China). It uses six orthogonal spreading factors (SFs) from 7 to 12, which enable adaptive optimisation of an end node’s power level and data rate. End nodes closer to the gateway use low spreading factors while those far away use high spreading factors to transmit data. The high spreading factor provides increased gain and higher reception sensitivity at the expense of data rate.
8.1. Application in Mining
LoRaWAN is yet to be deployed in mining. A few studies have been conducted to determine how it can best be implemented in the harsh mining environment. Some of the applications that have been attempted are smart monitoring of workers and machinery in the underground mine environment and smart data transmission of underground localisation traffic to an above-the-surface control room. Furthermore, at the EGAT Mae Mao coal mine in Lampang, Thailand, a prototype was tested that integrated LoRa with NB-IoT as an alternative communication channel for the IoT [2][45][46].
8.2. Strengths and Weaknesses
LoRaWAN has excellent characteristics, such as ultra-low power consumption, an extensive communication range, deep penetration capabilities, an adaptive rate of data transmission and high immunity to interference due to chirp spread spectrum modulation, which makes the technology promising for mine environments [2][44]. The extensive communication range makes it possible to achieve deep indoor coverage in multi-floor buildings and also entails a reduction in the number of gateways deployed on the field for covering wide areas, which lowers both the initial and maintenance costs. LoRa end nodes have a long battery life of up to 10 years, and LoRa also supports geolocation and firmware updates over-the-air for applications and LoRaWAN stacks. The other positive aspect of LoRaWAN is that it is unlicensed and non-cellular but also available from mobile network service providers around the world.
The main drawback is the Aloha MAC protocol used, which may not meet the needs of some of the mission-critical communications that are present in mining environments, especially when a large number of devices use the same channel frequently to transfer data [2]. Additionally, it requires subscription with a single vendor (SemTech), is not suitable for video surveillance due to low data rates and has no handover mechanism for mobile devices. Although the adaptive data rate (ADR) mechanism can save power in LoRaWAN end nodes, distant nodes use more battery power since the spreading factor is high and time on air is longer [44].
8.3. Record of Reliability
LoRa end nodes are stand-alone or autonomous since they are battery-powered and devices are manufactured in such a way that they can ensure safe transport of packets over a private or public network and deliver encrypted data to the cloud. Additionally, LoRa end nodes can send data to multiple gateways within range as there is no fixed association, which reduces the packet error rate and the probability of reception is high. The LoRa modulation based on the chirp spread spectrum (CSS) adds to the reliability of the technology in that the timing and frequency offsets between the transmitter and receiver are the same, which reduces the complexity of the receiver, and also the frequency bandwidth of the chirp is the same as the spectral bandwidth of the data signal. In addition, since spreading factors are orthogonal, signals modulated with different spreading factors can be transmitted on the same frequency channel at the same time without interfering with each other. LoRa signals are thus robust and resistant to in-band and out-of-band interference and immune to multipath effects and fading. LoRaWAN is also capable of supporting data communications from devices that are mobile since there is no need for a tight-tolerance reference clock [44]. The ADR mechanism makes it possible for each node’s SF to be adjusted to select the highest practical data rate while maintaining an acceptable signal-to-noise ratio (SNR) and at the same time enables the gateways to be capable of serving over one million nodes; otherwise, only 120 nodes per gateway would be supported without ADR [14]. The beauty of a LoRa network is that it is possible to set up an autonomous, private and locally administered network. A mining company, for instance, can deploy LoRa end nodes for monitoring various parameters, which will then transmit to gateways that may be connected via Wi-Fi or hardwired Ethernet to the local area network where the network server, join server and application server can be placed. This makes the network more secure as there is no need to go through public infrastructure to connect to the servers. On the other hand, the servers can be housed in the ’cloud’ and traffic from the gateways can be transmitted using Wi-Fi, Ethernet or cellular connection to the Internet, hence enabling IoT for LoRaWAN [44]. The authors of [14] demonstrate LPWAN’s suitability for use cases such as meter reading, SCADA/infrastructure control, transport, logistics, retail, environmental monitoring, wildlife monitoring, smart buildings, agriculture, smart street lighting and health, defence and military applications and bring out the fact that in practice LoRaWAN is often used as it is not restricted by regional availability, which adds to its reliability. In addition, they also state that, among other LPWANs, LoRaWAN has a sufficiently high data rate for real-time communication and it is also suitable for signal-hostile or hazardous environments. LoRaWAN is only capable of carrying low-data-rate sensor data; however, its future reliability can still be guaranteed by the strength highlighted above that it is available from mobile service providers around the world and may be complemented by the high-bit-rate mobile networks.
Table 2 presents a comparative summary of the properties of mining IoT technologies, while Table 3 gives a summary of their main strengths, weaknesses and records of reliability.
Table 2. A comparative summary of the main properties of the mining IoT communication systems.
| Technology | TX Power | Range | TX Speed | Frequency Bands | Sensitivity | Power Consumption | Applications |
|---|---|---|---|---|---|---|---|
| RFID | 30–33 dB | 10–100 m | 10–640 kbps | 30–500 kHz, 10–15 MHz, 850–950 MHz, 2.4–3.5 GHz, 5.8 GHz | Reader: −84 to −92 dBm, tag: −30 to −92 dBm | Typically: 13–26 mW, maximum: 1 W | Localisation and tracking systems, plant automation, quality control |
| Bluetooth/BLE | −20 to +20 dBm | 0–100 m | Typically: 720 kbps, versions 3 and 4: 25 Mbps | 2.4–2.485 GHz | −70 to −82 dBm | Classic: 100 mW, 2.5 mW and 1 mW, BLE: 0.01–0.5 W | Localisation and tracking for transport trucks, miner sensing and alerting |
| Zigbee | 12.3 dBm | 10–100 m | 20–250 kbps | 784 MHz, 868 MHz, 915 MHz, 2.4 GHz | −97 to −101 dBm | Classic: 10–100 mW | Environmental sensing, monitoring and alerting |
| Wi-Fi | 23–36 dBm | 0–1000 m | 160 kbps, 27 Mbps, 7 Gbps, 9.6 Gbps | 900 MHz, 2.4 GHz, 5 GHz, 6 GHz | −40 to −80 dBm | 9–12 W | Long-distance underground roadway communication, safety monitoring, location tracking, automatic ticketing and tracking, voice and surveillance communication |
| UWB | Emitter power spectral density: −41.3 to −75 dBm/MHz | 10–200 m | Up to 27 Mbps | 3.1–10.5 GHz | −73 to −80.8 dBm | 9–22 mW | Position tracking and estimation, information transmission |
| 5G | Up to 6 W (mining) | Up to 100 km | - | 3.3–4.2 GHz, 24–54 GHz | - | 1000 W to 20 KW (dependant on number of bands used) | Unmanned driving and work surfaces, industrial control, intelligent robot inspection |
| LoRa/LoRaWAN | 10–30 dBm | Urban: 5 km, rural: 15 km | 0.3–50 kbps | 470–510 MHz, 863–870 MHz, 902–928 MHz | 25 mW | −137 to −150 dBm | Yet to be deployed |
Table 3. Summary of strengths, weaknesses and records of reliability of mining IoT communication systems.
| Mining IoT Technology | Strengths | Weaknesses | Record of Reliability |
|---|---|---|---|
| RFID | Short recognition distance, low performance degradation and low price, data secure and hidden from plain sight, long lifespan of passive tags | Affected by environmental conditions (i.e., moisture and physical obstructions), inferior due to technological limitations | Capturing data for fast-moving objects, non-line-of-sight data reading, real-time tracking, data perception only, short-range technology |
| Bluetooth/BLE | Convenient wireless data sharing between paired devices, technology extensively available and accessible, cost of devices reasonable, easy and convenient to use, BLE relatively energy-efficient | Range of up to 100 m, energy-inefficient in real-time applications and drains battery if left on, slower data transmission rate, security vulnerabilities, BLE not compatible with other classic versions, low node capacity | No interoperability issues and optimal for IoT, accurate for indoor location tracking, resistant to interference and multipath effects when using FH-SS, good performance for harsh environments (i.e., mining), low power consumption results in long battery lifespan of 5–10 years, BLE has low latency |
| Zigbee | High node support at 6500 nodes, network easily expandable—end nodes can play intermediary roles, simple and less expensive than Wi-Fi and Bluetooth, flexible structure, easy installation process and easy maintenance, load evenly distributed across network | Suitable for indoor applications only, short range—depends on cellular coverage for off-site monitoring; prone to network interference and channel noise and not very secure, lower transmission rate than Bluetooth and Wi-Fi, compatibility issues with computers, laptops and smartphones | Mesh topology enhances reliability of network access, range, throughput, packet delivery rate and security; high signal penetration ability, thus suitable for mining; better stability than Wi-Fi since end nodes also act as coordinators and perform routing functions; reliable due to long battery life, low power consumption, ease of maintenance and even distribution of load; prone to interference and does not support mobility; relies on Wi-Fi, Ethernet or cellular technologies to support IoT; connecting to cellular increases cost and compromises quality and network availability |
| Wi-Fi | Suitable for complex terrain underground, not dependant on line of sight, Wi-Fi 6 better than 5G underground, fast communication speed of 9.6 Gbps, implemented with different topologies underground (i.e., ring, linear and mesh), lower latency and longer range than Bluetooth and Zigbee | Relies on Ethernet as backbone; high power consumption and low capacity in terms of number of devices supported; practically, with one access point at 2.4 GHz, the range is short, within 200–300 m | OFDM used improves network delay and communication efficiency, dual-frequency adjustment between 2.4 GHz and 5 GHz for communication quality and reliability, integrable with Zigbee and Bluetooth, IEEE802.11ah suitable for outdoor environments and as reliable as LoRaWAN but with shorter range |
| Ultra-wide band | High data rates and robust communication; high performance and good positioning in non-visual environments; not interfered with by other wireless networks; low power consumption, high measurement accuracy and strong robustness to multipath effects and non-line-of-sight environments compared to RFID, Bluetooth, Zigbee and Wi-Fi; use of low carrier frequency enables penetration through obstacles | For better accuracy, relies on line of sight; accurate for single sensor locating and tracking where mobility is demanded | Excellent real-time precision; accurate and reliable for data transfer, positioning and tracking of employees; fast and reliable data transmission up to 200 m; low power consumption even with huge amounts of data (9–22 mW); TOF technique enhances reliability and performance in multipath environments and indoors; can collect data in dusty, misty, noisy and low-illumination environments; uses pulse transmission and hence immune to interference and very secure; location accuracy better than Bluetooth and Wi-Fi; IoT applications require other wired and wireless technologies for Internet and cloud services |
| 5G | High channel bandwidth, higher capacity in terms of devices per square kilometre, high-speed and ultra-low latency communication, long range of up to 100 km on the ground and safe for underground communication, private 5G network deployment exclusively for single organisations | Unavailable in remote locations where mines exist, high power consumption, devices are more complex, not suitable for energy- constrained IoT devices, coverage distance is short underground, accuracy of signal transmission is affected by multifactorial interference underground |
Reliable where precision is required and large amounts of real-time data are transmitted, URLLC enables low latency and high reliability, satisfies requirements for IoT communications involving high-quality data transmission monitored in real time, suitable for surveillance systems, can coexist with Wi-Fi 6 and Wi-Fi 7, transmission reliability and channel capacity enhanced by MIMO and smart antenna technology, communication reliability is affected in underground explosive environments, still relies on LTE-M and NB-IoT to support IoT |
| LoRaWAN | Unlicensed and non-cellular but available from mobile network providers, end-node battery life of up to 10 years, uses fewer gateways, ultra-low power consumption, long range, adaptive rate of data transmission, strong immunity to interference spectrum | Aloha MAC protocol can cause data collisions and increase delay, requires subscription with a single vendor, unsuitable for video surveillance due to low data rates, distant nodes using high SFs may use more battery power and time on air | Encrypts data to the cloud and hence secure; diversity in transmission reduces packet error rate and increases probability of reception; robust against interference, multipath effects and fading due to CSS; ADR enables support for high capacity; autonomous networks supported; among the most reliable LPWANs; not restricted by regional availability; sufficient data rate for real-time communications, thus promising for mines |
References
- Salam, A.; Salam, A. Internet of things for sustainable mining. In Internet of Things for Sustainable Community Development: Wireless Communications, Sensing, and Systems; Springer: Berlin/Heidelberg, Germany, 2020; pp. 243–271.
- Nessa, A.; Hussain, F.; Fernando, X. Adaptive latency reduction in lora for mission critical communications in mines. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Virtual Conference, 29 June–1 July 2020; pp. 1–7.
- Kim, S.M. Review of internet of things and open-source hardware technologies use in the mining industry. J. Korean Soc. Miner. Energy Resour. Eng. 2019, 56, 447–456.
- Chieochan, O.; SaoKaew, A.; Boonchieng, E. An integrated system of applying the use of Internet of Things, RFID and cloud computing: A case study of logistic management of Electricity Generation Authority of Thailand (EGAT) Mae Mao Lignite Coal Mining, Lampang, Thailand. In Proceedings of the 2017 9th International Conference on Knowledge and Smart Technology (KST), Chonburi, Thailand, 1–4 February 2017; pp. 156–161.
- Lewis, D. RFID: Advantages and Disadvantages — Konsyse. Konsyse. 2023. Available online: https://www.konsyse.com/articles/rfid-advantages-and-disadvantages (accessed on 6 February 2023).
- Ivankov, A. Advantages and Disadvantages of Bluetooth-Profolus. Profolus. 2019. Available online: https://www.profolus.com/topics/advantages-and-disadvantages-of-bluetooth (accessed on 22 February 2023).
- Consani, P. Classic Bluetooth vs. Bluetooth Low Energy (BLE). IoT Lab-TERTIUM Cloud Blog. 2020. Available online: https://iotlab.tertiumcloud.com/2020/08/19/classic-bluetooth-vs-bluetooth-low-energy-ble (accessed on 22 February 2023).
- 17 Pros and Cons of Using Bluetooth. 2023. Available online: https://ecomputertips.com/pros-and-cons-of-using-bluetooth (accessed on 26 October 2023).
- Nesbo, E. What Is BLE (Bluetooth Low Energy) and How Does It Work? 2021. Available online: https://www.makeuseof.com/what-is-ble-bluetooth-low-energy (accessed on 26 October 2023).
- Bray, J.; Senese, B.; McNutt, G.; Munday, B.; Kammer, D. BlueTooth Application Developer’s Guide; Syngress Publishing: Rockland, MA, USA, 2001.
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734.
- Deokar, S.; Wakode, J. Coal mine safety monitoring and alerting system. Int. Res. J. Eng. Technol. 2017, 4, 2146–2149.
- Afaneh, M. Bluetooth Low Energy (BLE): A Complete Guide. Novel Bits. 2023. Available online: https://novelbits.io/bluetooth-low-energy-ble-complete-guide (accessed on 22 February 2023).
- Buurman, B.; Kamruzzaman, J.; Karmakar, G.; Islam, S. Low-power wide-area networks: Design goals, architecture, suitability to use cases and research challenges. IEEE Access 2020, 8, 17179–17220.
- Qadir, Q.M.; Rashid, T.A.; Al-Salihi, N.K.; Ismael, B.; Kist, A.A.; Zhang, Z. Low power wide area networks: A survey of enabling technologies, applications and interoperability needs. IEEE Access 2018, 6, 77454–77473.
- Rosencrance, L. Zigbee. IoT Agenda. 2017. Available online: https://www.techtarget.com/iotagenda/definition/ZigBee (accessed on 28 February 2023).
- Vitturi, S.; Zunino, C.; Sauter, T. Industrial communication systems and their future challenges: Next-generation Ethernet, IIoT, and 5G. Proc. IEEE 2019, 107, 944–961.
- Zigbee Technology Advantages and Disadvantages|ZigBee Technology Architecture and Its Applications. 2022. Available online: https://www.aplustopper.com/zigbee-technology-advantages-and-disadvantages (accessed on 26 October 2023).
- Davies, M. Zigbee Technology: Advantages and Disadvantages. 2023. Available online: https://www.konsyse.com/articles/zigbee-technology-advantages-and-disadvantages (accessed on 28 October 2023).
- Ansari, A.; Shaikh, K.; Kadu, P.; Rishikesh, N. IOT based coal mine safety monitoring and alerting system. Int. J. Sci. Res. Sci. Eng. Technol. 2021, 8, 404–410.
- Moridi, M.A.; Kawamura, Y.; Sharifzadeh, M.; Chanda, E.K.; Wagner, M.; Okawa, H. Performance analysis of ZigBee network topologies for underground space monitoring and communication systems. Tunn. Undergr. Space Technol. 2018, 71, 201–209.
- Islam, N.; Rashid, M.M.; Pasandideh, F.; Ray, B.; Moore, S.; Kadel, R. A review of applications and communication technologies for internet of things (Iot) and unmanned aerial vehicle (uav) based sustainable smart farming. Sustainability 2021, 13, 1821.
- Min, C.; Jinhao, Z. The application of WiFi 6 technology in underground mine. In Proceedings of the IOP Conference Series: Earth and Environmental Science; IOP Publishing: Bristol, UK, 2021; Volume 687, p. 012153.
- Wang, Y.; Duan, X.; Tian, D.; Lu, G.; Yu, H. Throughput and Delay Limits of 802.11 p and its Influence on Highway Capacity. Procedia-Soc. Behav. Sci. 2013, 96, 2096–2104.
- Wen, M.; Li, Q.; Kim, K.J.; López-Pérez, D.; Dobre, O.A.; Poor, H.V.; Popovski, P.; Tsiftsis, T.A. Private 5G networks: Concepts, architectures, and research landscape. IEEE J. Sel. Top. Signal Process. 2021, 16, 7–25.
- Tao, P.; Xiaoyang, L. Hybrid wireless communication system using ZigBee and WiFi technology in the coalmine tunnels. In Proceedings of the 2011 Third International Conference on Measuring Technology and Mechatronics Automation, Shanghai, China, 6–7 January 2011; Volume 2, pp. 340–343.
- Zhang, Y.; Li, L.; Zhang, Y. Research and design of location tracking system used in underground mine based on WiFi technology. In Proceedings of the 2009 International Forum on Computer Science-Technology and Applications, Chongqing, China, 25–27 December 2009; Volume 3, pp. 417–419.
- Song, W.; Wang, F.; Dai, J. A Emergency Communication System based on WMN in underground mine. In Proceedings of the 2010 International Conference on Computer Application and System Modeling (ICCASM 2010), Taiyuan, China, 22–24 October 2010; Volume 4, pp. V4–V624.
- Dagsa, L.M.; Demetillo, A.T.; Balamad, A.D.B.; Sajonia, E.; Amper, G.L.; Virtudazo, M.C.O. Development of an Automated Ticketing and Tracking System for the Monitoring of Surface Mine Hauling Operations. Eng. Technol. Appl. Sci. Res. 2022, 12, 8500–8505.
- Wisiak, K.; Jakić, M.; Hartlieb, P. Application of ultra-wide band sensors in mining. Sensors 2022, 23, 300.
- Yuan, X.; Bi, Y.; Hao, M.; Ji, Q.; Liu, Z.; Bao, J. Research on Location Estimation for Coal Tunnel Vehicle Based on Ultra-Wide Band Equipment. Energies 2022, 15, 8524.
- Yang, L.; Giannakis, G. Ultra-wideband communications: An idea whose time has come. IEEE Signal Process. Mag. 2004, 21, 26–54.
- Kianfar, A.E.; Uth, F.; Baltes, R.; Clausen, E. Development of a robust ultra-wideband module for underground positioning and collision avoidance. Mining, Metall. Explor. 2020, 37, 1821–1825.
- Abou El-Nasr, M.; Shaban, H. Low-power and reliable communications for UWB-based wireless monitoring sensor networks in underground mine tunnels. Int. J. Distrib. Sens. Netw. 2015, 11, 456460.
- Obeidat, H.; Shuaieb, W.; Obeidat, O.; Abd-Alhameed, R. A review of indoor localization techniques and wireless technologies. Wirel. Pers. Commun. 2021, 119, 289–327.
- Bakr, D.M. Introduction to Ultra-Wideband (UWB) Technology. All About Circuits. 2020. Available online: https://www.allaboutcircuits.com/technical-articles/introduction-to-ultra-wideband-uwb-technology (accessed on 27 April 2023).
- What Is 5G Technology and How Does It Work? 2023. Available online: https://www.twi-global.com/technical-knowledge/faqs/What-is-5G (accessed on 26 October 2023).
- What Is 5G|Everything You Need to Know about 5G|5G FAQ|Qualcomm. 2023. Available online: https://www.qualcomm.com/5g/what-is-5g (accessed on 26 October 2023).
- Zhang, L.; Yang, W.; Fang, W.; Jiang, Y.; Zhao, Q. Periodic Monitoring and Filtering Suppression of Signal Interference in Mine 5G Communication. Appl. Sci. 2022, 12, 7689.
- Zhang, L.; Yang, W.; Hao, B.; Yang, Z.; Zhao, Q. Edge computing resource allocation method for mining 5G communication system. IEEE Access 2023, 11, 49730–49737.
- Li, Z.; Fang, L.; Sun, X.; Peng, W. 5G IoT-based geohazard monitoring and early warning system and its application. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 1–16.
- Zhao, Q.; Yang, W.; Zhang, L. Energy-efficient resource allocation for NOMA-based heterogeneous 5G mine internet of things. IEEE Access 2022, 10, 67437–67450.
- Sisinni, E.; Ferrari, P.; Carvalho, D.F.; Rinaldi, S.; Marco, P.; Flammini, A.; Depari, A. LoRaWAN range extender for industrial IoT. IEEE Trans. Ind. Inform. 2019, 16, 5607–5616.
- LoRa and LoRaWAN: Technical overview|DEVELOPER PORTAL. 2023. Available online: https://lora-developers.semtech.com/documentation/tech-papers-and-guides/lora-and-lorawan (accessed on 25 October 2023).
- RayChowdhury, A.; Pramanik, A.; Roy, G.C. New approach for localization and smart data transmission inside underground mine environment. SN Appl. Sci. 2021, 3, 604.
- Boonchieng, E.; Saokaew, A.; Chieochan, O. The prototype of the integration between low cost single private lora gateway and public ais nb-iot. J. Internet Technol. 2019, 20, 1313–1322.
More
Information
Subjects:
Engineering, Electrical & Electronic
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.9K
Revisions:
2 times
(View History)
Update Date:
17 Feb 2024
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




