
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Valeriy Ivanov | -- | 3846 | 2024-01-28 16:21:41 | | | |
| 2 | Lindsay Dong | + 3 word(s) | 3849 | 2024-01-29 03:07:35 | | |
Video Upload Options
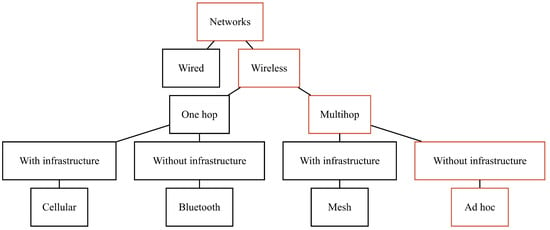
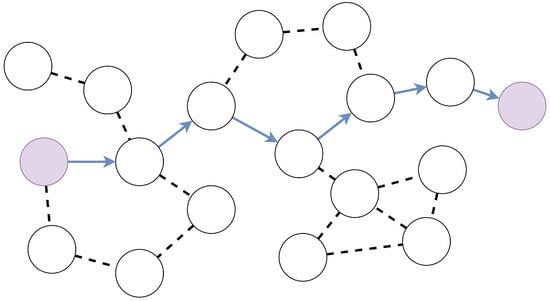
The Open systems interconnection (OSI)model used to be a common network model for years. In the case of ad hoc networks with dynamic topology and difficult radio communications conditions, gradual departure is happening from the classical kind of OSI network model with a clear delineation of layers (physical, channel, network, transport, application) to the cross-layer approach. The layers of the network model in ad hoc networks strongly influence each other. Thus, the cross-layer approach can improve the performance of an ad hoc network by jointly developing protocols using interaction and collaborative optimization of multiple layers. The existing cross-layer methods classification is too complicated because it is based on the whole manifold of network model layer combinations, regardless of their importance.
1. Introduction
-
Self-organization. Nodes are organized into networks and manage the network independently and in a distributed manner without centralized intervention. Each node acts as both the user and router [1].
-
Peer network. Nodes of ad hoc networks are equal and perform the same functions [1].
-
Limited resources. Ad hoc networks usually consist of portable devices with low computing power, memory, and battery charge [1].
-
Limited constantly changing capacity of radio lines. Radio lines are susceptible to interference from neighboring nodes, noise from outside, multipath fading, and the Doppler effect [4].
-
Shared channel resource. The lack of dedicated channel resources (the contention of nodes over channel resources) leads to interference and packet collisions, which reduces network bandwidth [4].
-
Vulnerability to attacks. In classical networks, all data from a single subnet passes through one powerful firewall, and an attack from outside the network is directed only to the firewall. In the ad hoc network, each node is equally vulnerable to attacks from outside [5].
-
Large amount of service data for routing. It is necessary because of ad hoc network dynamic topology to send more (than static networks) service information about the lines state, etc., to find network routes [4].
-
Frequent network fragmentation. Network mobility can cause the ad hoc network to be divided into isolated subnets [4].
-
Complexity of providing QoS. The poorly predictable instability of radio lines, interference of nodes, frequent route breaks, and delay in finding a new route all make the task of providing QoS in ad hoc networks very difficult [4].
-
Military use. It is difficult to deploy a cellular network in a warzone, but an ad hoc network can be deployed almost instantly.
-
Rescue and search operations. In the event of a disaster, the local infrastructure is destroyed, and in the case of search operations in sparsely populated areas, the infrastructure initially does not exist. The rapid deployment of an ad hoc network allows immediate rescue and search operations.
-
Distributed file sharing. During a meeting, such as a conference, one can quickly deploy a network to share files and presentations.
-
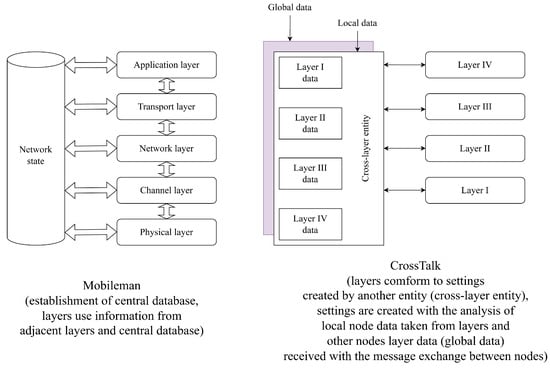
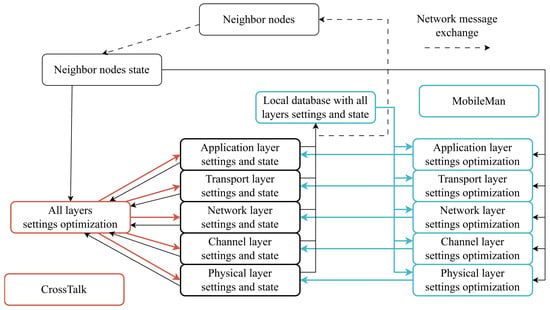
Provision of information. Adjacent and disconnected layers share information through interfaces or by using a common database.
-
Layer integration. Layer separation disappears, and all layers except maybe the application layer are merged into one.
-
Cross-layer method parameter selection. One of the fundamental questions of cross-layer methods is the choice of layer parameters on the basis of which decisions about network operation are made. It is very important to consider the physical layer parameters, but it is also important to consider the application layer parameters. For example, the received signal strength indicator (RSSI) is a good indicator of signal power, but this parameter does not take into account noise and interference. The noise level is taken into account in the signal-to-noise ratio (SNR), but interference is also not included. The signal-to-interference + noise ratio (SINR) parameter is much more useful because it simultaneously takes into account the signal strength and noise. With the SNR [28], one can estimate the proximity of the nodes (i.e., the nodes are within each other’s radio connection). Queue occupancy information is available at the channel layer. In addition to the above parameters, parameters that provide information about data flows are also used. As shown in [29][30], another approach is to use composite parameters obtained by combining many other parameters.
-
Layer interdependency and the complexity of independent development. As shown in [31], cross-layer protocol design is nothing more than an OSI violation in which interlinked layers interact. The modification and improvement of a highly interconnected system is difficult. However, achieving modularity is one of the most difficult tasks in developing cross-layer methods.
-
Overly complex interaction between layers. The flow of information between the different layers creates unforeseen relationships between layers, reducing the efficiency of the entire system. Therefore, it is necessary to choose the interaction between layers very carefully.
2. Cross-Layer Methods for Ad Hoc Networks
-
Line throughput. Line throughput is the volume of successfully delivered data through the line per unit of time.
-
Energy consumption. The less the node energy spent per successful information transmission, the more battery life, and the greater the longevity of network connectivity.
-
Line packet error rate. Line packet error rate is inversely proportional to line throughput with regard to the line bandwidth, which is the line transmission rate.
-
Line latency. Line latency is the sum of multiple delays: queueing delay, propagation delay, transmission delay, etc.
-
Route throughput. Route throughput is the minimal throughput of lines inside the route.
-
Route packet error rate. Route packet error rate is the complimentary of the lines inside route probabilities of successful packet delivery multiplication.
-
Route stability. Route stability is how long all lines in the route remain existing and within the desired range of parameters.
-
Route latency. Route latency is the sum of line latencies inside the route.
-
Interference. Interference is the simultaneous transmission of multiple nodes when the total power of other nodes transmitted, except the sender, corrupts the received packets. Low interference is not harmful. High interference causes packet collisions.
-
Data overhead. The volume of service data. The more, for example, the routing protocol sends route request packets, the lower the throughput.
2.1. One Layer
2.1.1. Physical Layer
Zorzi et al. [41] consider the problems of the development of the channel layer protocol for ad hoc networks with nodes with multiple antenna elements with MIMO technology. Network nodes are capable of forming directional antenna patterns, interference rejection, and MIMO space-time coding of signals. For single omnidirectional antennas, nodes send a transmission request packet, and the target node responds with a permission packet. All other nodes that have accepted the permission and request packet cease to use the radio channel for the time required to transfer the packet between the two nodes. If the receiving node can use a radio channel, the node allows the packet to receive. In the case of multiple antennas with independent transceivers, the node can receive multiple packets at the same time under sufficient spatial separation of senders; when transmitting packets, it can beamform in a way that reduces interference. As a result, requests for transmission packets are advisory in nature and are used to assess the needs of data streams. Therefore, the authors conclude that the interaction of physical and channel layers is necessary.
2.1.2. Channel Layer
-
Channel layer (resource reservation)
-
Channel layer (random access)
-
Channel layer (cooperative transmission)
2.1.3. Network Layer
-
Network layer (routing metrics)
-
Network layer (routing protocols)
2.1.4. Transport Layer
2.1.5. Application Layer
-
Application layer (overlay network)
2.2. Multiple Layers
2.2.1. External Entity Multiple Layers Control and Optimization
-
External entity multiple layers control and optimization (fuzzy logic)
-
External entity multiple layers control and optimization (dual decomposition)
2.2.2. Independent Layers and Information Sharing
3. Conclusions
References
- Raza, N.; Umar Aftab, M.; Qasim Akbar, M.; Ashraf, O.; Irfan, M. Mobile ad-hoc networks applications and its challenges. Commun. Netw. 2016, 8, 131–136.
- Kirubasri, G.; Maheswari, U.; Venkatesh, R. A survey on hierarchical cluster based routing protocols for wireless multimedia sensor networks. J. Converg. Inf. Technol. 2014, 9, 19.
- Sennan, S.; Somula, R.; Luhach, A.K.; Deverajan, G.G.; Alnumay, W.; Jhanjhi, N.; Ghosh, U.; Sharma, P. Energy efficient optimal parent selection based routing protocol for Internet of Things using firefly optimization algorithm. Trans. Emerg. Telecommun. Technol. 2021, 32, e4171.
- Zemrane, H.; Baddi, Y.; Hasbi, A. Mobile adhoc networks for intelligent transportation system: Comparative analysis of the routing protocols. Procedia Comput. Sci. 2019, 160, 758–765.
- Pandey, M.A. Introduction to mobile ad hoc network. Int. J. Sci. Res. Publ. 2015, 5, 1–6.
- Goldsmith, A.; Wicker, S. Design challenges for energy-constrained ad hoc wireless networks. IEEE Wirel. Commun. 2002, 9, 8–27.
- Alshbatat, A.I.; Dong, L. Cross layer design for mobile ad-hoc unmanned aerial vehicle communication networks. In Proceedings of the 2010 International Conference on Networking, Sensing and Control (ICNSC), Chicago, IL, USA, 10–12 April 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 331–336.
- Gawas, M.A.; Govekar, S. State-of-art and open issues of cross-layer design and QOS routing in internet of vehicles. Wirel. Pers. Commun. 2021, 116, 2261–2297.
- Cruz, R.L.; Santhanam, A.V. Optimal link scheduling and power control in cdma multihop wireless networks. In Proceedings of the Global Telecommunications Conference, 2002, GLOBECOM’02, Taipei, Taiwan, 17–21 November 2002; IEEE: Piscataway, NJ, USA, 2002; Volume 1, pp. 52–56.
- Merz, R.; Widmer, J.; Le Boudec, J.Y.; Radunović, B. A joint PHY/MAC architecture for low-radiated power TH-UWB wireless ad hoc networks. Wirel. Commun. Mob. Comput. 2005, 5, 567–580.
- Toumpis, S.; Goldsmith, A.J. Capacity regions for wireless ad hoc networks. IEEE Trans. Wirel. Commun. 2003, 2, 736–748.
- Neely, M.; Modiano, E.; Rohrs, C. Dynamic power allocation and routing for time varying wireless networks. In Proceedings of the IEEE INFOCOM 2003. Twenty-Second Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE Cat. No.03CH37428), San Francisco, CA, USA, 30 March–3 April 2003; Volume 1, pp. 745–755.
- Zorba, N.; Skianis, C.; Verikoukis, C. Cross Layer Designs in WLAN Systems; Troubador Publishing Limited: Market Harborough, UK, 2011.
- Zuo, J.; Dong, C.; Ng, S.X.; Yang, L.L.; Hanzo, L. Cross-layer aided energy-efficient routing design for ad hoc networks. IEEE Commun. Surv. Tutorials 2015, 17, 1214–1238.
- Arafat, M.Y.; Poudel, S.; Moh, S. Medium access control protocols for flying ad hoc networks: A review. IEEE Sens. J. 2020, 21, 4097–4121.
- Labiod, M.A.; Gharbi, M.; Coudoux, F.X.; Corlay, P.; Doghmane, N. Cross-layer scheme for low latency multiple description video streaming over Vehicular Ad-hoc NETworks (VANETs). AEU-Int. J. Electron. Commun. 2019, 104, 23–34.
- Amponis, G.; Lagkas, T.; Sarigiannidis, P.; Vitsas, V.; Fouliras, P.; Wan, S. A survey on FANET routing from a cross-layer design perspective. J. Syst. Archit. 2021, 120, 102281.
- Ahlswede, R.; Cai, N.; Li, S.Y.; Yeung, R.W. Network information flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216.
- Fu, F.; van der Schaar, M. A new systematic framework for autonomous cross-layer optimization. IEEE Trans. Veh. Technol. 2008, 58, 1887–1903.
- Conti, M.; Giordano, S.; Maselli, G.; Turi, G. Mobileman: Mobile metropolitan ad hoc networks. In Proceedings of the IFIP International Conference on Personal Wireless Communications, Venice, Italy, 23–25 September 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 169–174.
- Winter, R.; Schiller, J.H.; Nikaein, N.; Bonnet, C. Crosstalk: Cross-layer decision support based on global knowledge. IEEE Commun. Mag. 2006, 44, 93–99.
- Jurdak, R. Wireless Ad Hoc and Sensor Networks: A Cross-Layer Design Perspective; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2007.
- Awang, A.; Husain, K.; Kamel, N.; Aissa, S. Routing in vehicular ad-hoc networks: A survey on single-and cross-layer design techniques, and perspectives. IEEE Access 2017, 5, 9497–9517.
- Fu, B.; Xiao, Y.; Deng, H.; Zeng, H. A survey of cross-layer designs in wireless networks. IEEE Commun. Surv. Tutorials 2013, 16, 110–126.
- Aktas, I.; Alizai, M.H.; Schmidt, F.; Wirtz, H.; Wehrle, K. Harnessing cross-layer-design. Hoc Netw. 2014, 13, 444–461.
- Edirisinghe, R.; Zaslavsky, A. Cross-layer contextual interactions in wireless networks. IEEE Commun. Surv. Tutorials 2013, 16, 1114–1134.
- Kawadia, V.; Kumar, P.R. A cautionary perspective on cross-layer design. IEEE Wirel. Commun. 2005, 12, 3–11.
- Singh, J.P.; Bambos, N.; Srinivasan, B.; Clawin, D. Cross-layer multi-hop wireless routing for inter-vehicle communication. In Proceedings of the 2nd International Conference on Testbeds and Research Infrastructures for the Development of Networks and Communities, 2006. TRIDENTCOM 2006, Barcelona, Spain, 1–3 March 2006; IEEE: Piscataway, NJ, USA, 2006; p. 10.
- Katsaros, K.; Dianati, M.; Tafazolli, R.; Kernchen, R. CLWPR—A novel cross-layer optimized position based routing protocol for VANETs. In Proceedings of the 2011 IEEE Vehicular Networking Conference (VNC), Amsterdam, The Netherlands, 14–16 November 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 139–146.
- Chen, Y.; Xiang, Z.; Jian, W.; Jiang, W. A cross-layer AOMDV routing protocol for V2V communication in urban VANET. In Proceedings of the 2009 Fifth International Conference on Mobile Ad-Hoc and Sensor Networks, Wuyi, China, 14–16 December 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 353–359.
- Srivastava, V.; Motani, M. Cross-layer design: A survey and the road ahead. IEEE Commun. Mag. 2005, 43, 112–119.
- Ren, X.; Zhang, J. Review of the Cross-Layer Design in Wireless Ad Hoc and Sensor Networks. In Proceedings of the 2010 International Conference on Computational Intelligence and Software Engineering, Wuhan, China, 10–12 December 2010; IEEE: Piscataway, NJ, USA, 2010.
- Jarupan, B.; Ekici, E. A survey of cross-layer design for VANETs. Hoc Netw. 2011, 9, 966–983.
- Singhal, C.; Rajesh, A. Review on cross-layer design for cognitive ad-hoc and sensor network. IET Commun. 2020, 14, 897–909.
- Trivedi, H.; Veeraraghavan, P.; Loke, S.; Desai, A.; Singh, J. Routing mechanisms and cross-layer design for Vehicular Ad Hoc Networks: A survey. In Proceedings of the 2011 IEEE Symposium on Computers & Informatics, Banff, AB, USA, 18–20 August 2011; IEEE: Piscataway, NJ, USA, 2011.
- Mantzouratos, S.; Gardikis, G.; Koumaras, H.; Kourtis, A. Survey of cross-layer proposals for video streaming over Mobile Ad hoc Networks (MANETs). In Proceedings of the 2012 International Conference on Telecommunications and Multimedia (TEMU), Crete, Greece, 30 July–1 August 2012; IEEE: Piscataway, NJ, USA, 2012.
- Goswami, C.; Sultanah, P. A Study on Cross-Layer TCP Performance in Wireless Ad Hoc Network. In International Conference on Intelligent Data Communication Technologies and Internet of Things (ICICI) 2018; Springer International Publishing: Coimbatore, India, 2018; pp. 56–70.
- DARPA IAMANET Developed Scalable and Secure Mobile Ad Hoc Networks (MANETS) to Support an Entire Battalion—International Defense Security & Technology. 2024. Available online: https://idstch.com/military/mobile-ad-hoc-networks-manets-essential-for-network-centric-warfare-and-disaster-management/ (accessed on 12 January 2024).
- Connected and Automated Mobility. 2024. Available online: https://digital-strategy.ec.europa.eu/en/policies/connected-and-automated-mobility/ (accessed on 12 January 2024).
- Frąckiewicz, M. The Potential of Mesh Networks for Africa’s Connectivity. 2023. Available online: https://ts2.pl/en/the-potential-of-mesh-networks-for-africas-connectivity (accessed on 12 January 2024).
- Zorzi, M.; Zeidler, J.; Anderson, A.; Rao, B.; Proakis, J.; Swindlehurst, A.; Jensen, M.; Krishnamurthy, S. Cross-layer issues in MAC protocol design for MIMO ad hoc networks. IEEE Wirel. Commun. 2006, 13, 62–76.
- Mansoor, N.; Islam, A.K.M.M.; Zareei, M.; Vargas-Rosales, C. RARE: A Spectrum Aware Cross-Layer MAC Protocol for Cognitive Radio Ad-Hoc Networks. IEEE Access 2018, 6, 22210–22227.
- Park, M.; Andrews, J.; Nettles, S. Wireless channel-aware ad hoc cross-layer protocol with multiroute path selection diversity. In Proceedings of the 2003 IEEE 58th Vehicular Technology Conference, VTC 2003-Fall (IEEE Cat. No.03CH37484), Orlando, FL, USA, 6–9 October 2003; IEEE: Piscataway, NJ, USA, 2003.
- Canales, M.; Gállego, J.R.; Hernández-Solana, Á.; Valdovinos, A. QoS provision in mobile ad hoc networks with an adaptive cross-layer architecture. Wirel. Netw. 2008, 15, 1165–1187.
- Yu, X. Improving TCP performance over mobile ad hoc networks by exploiting cross-layer information awareness. In Proceedings of the 10th Annual International Conference on Mobile Computing and Networking, Philadelphia, PA, USA, 26 September–1 October 2004; ACM: New York, NY, USA, 2004.
- Beylot, A.L.; Dhaou, R.; Gauthier, V.; Becker, M. Cross-Layer Simulation and Optimization for Mobile Ad-Hoc Networks. In IFIP International Federation for Information Processing; Springer: Greer, SC, USA, 2005; pp. 13–22.
- Xia, X.; Ren, Q.; Liang, Q. Cross-layer design for mobile ad hoc networks: Energy, throughput and delay-aware approach. In Proceedings of the IEEE Wireless Communications and Networking Conference, 2006. WCNC 2006, Las Vegas, NV, USA, 3–6 April 2006; IEEE: Piscataway, NJ, USA, 2006.
- Yuen, W.H.; no Lee, H.; Andersen, T. A simple and effective cross layer networking system for mobile ad hoc networks. In Proceedings of the 13th IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, Lisbon, Portugal, 18 September 2002; IEEE: Piscataway, NJ, USA, 2002.
- Wu, Y.; Chou, P.A.; Zhang, Q.; Jain, K.; Zhu, W.; Kung, S.Y. Network planning in wireless ad hoc networks: A cross-layer approach. IEEE J. Sel. Areas Commun. 2005, 23, 136–150.




