Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Adnan Akhunzada | -- | 992 | 2024-01-28 05:57:25 | | | |
| 2 | Jessie Wu | + 17 word(s) | 1009 | 2024-01-29 02:13:11 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Saeed, K.; Khalil, W.; Al-Shamayleh, A.S.; Ahmad, I.; Akhunzada, A.; Alharethi, S.Z.; Gani, A. Threshold-Optimized Depth-Based Routing Protocol. Encyclopedia. Available online: https://encyclopedia.pub/entry/54442 (accessed on 07 February 2026).
Saeed K, Khalil W, Al-Shamayleh AS, Ahmad I, Akhunzada A, Alharethi SZ, et al. Threshold-Optimized Depth-Based Routing Protocol. Encyclopedia. Available at: https://encyclopedia.pub/entry/54442. Accessed February 07, 2026.
Saeed, Khalid, Wajeeha Khalil, Ahmad Sami Al-Shamayleh, Iftikhar Ahmad, Adnan Akhunzada, Salman Z. Alharethi, Abdullah Gani. "Threshold-Optimized Depth-Based Routing Protocol" Encyclopedia, https://encyclopedia.pub/entry/54442 (accessed February 07, 2026).
Saeed, K., Khalil, W., Al-Shamayleh, A.S., Ahmad, I., Akhunzada, A., Alharethi, S.Z., & Gani, A. (2024, January 28). Threshold-Optimized Depth-Based Routing Protocol. In Encyclopedia. https://encyclopedia.pub/entry/54442
Saeed, Khalid, et al. "Threshold-Optimized Depth-Based Routing Protocol." Encyclopedia. Web. 28 January, 2024.
Copy Citation
The exponentially growing concern of cyber-attacks on extremely dense underwater sensor networks (UWSNs) and the evolution of UWSNs digital threat landscape has brought novel research challenges and issues.
security attack
active attack
routing attack
attacker nodes
malicious nodes
1. Introduction
Over the past ten years, interest in underwater wireless sensor networks (UWSNs) has grown significantly [1]. Due to the seas and water that cover it, the earth is known as the “blue planet” in the solar system [2]. Since the oceans cover more than 70% of our world [3][4], UWSNs are extremely important and an important research area [5]. Exploration underwater has increased significantly in the recent past [6]. UWSNs are made up of sensor nodes, and these nodes exchange data and communicate [7]. These sensor nodes have limited battery capacity [8]. In UWSNs, the sensor nodes also communicate with one another to determine the optimum path based on a set of criteria. The data are transmitted using the best route possible from the bottom of the sea to the surface level of the water, and then further [9][10][11][12]. UWSNs have the potential to explore hidden underwater resources. Additionally, they have enhanced capacity for both prediction and observation of the oceans [13]. Other significant UWSNs endeavors include ocean resource exploration, underwater information exchange, monitoring, and disaster avoidance [9][10][11][12][14][15]. Due to the constrained context of UWSNs, they are very different from conventional WSNs. Furthermore, compared to the context of WSNs, the issues faced by UWSNs are very different [16]. The major challenge in WSNs environment is the smaller battery power capacity of the nodes [17]. Some important research contributions in ad-hoc and sensor networks include improving fault tolerance [18], detection of faulty nodes in WSNs [19][20], reliable data transfer protocol for WSNs [21] and routing approach in IoT [22].
Due to a variety of factors, communication in the UWSNs context is difficult and unpredictable [23]. Due to absorption, high-level attenuation, and dispersion, radio waves in UWSNs are not effective. The atmosphere of UWSNs is suitable for the transfer of data via acoustic communication [24]. The range of frequencies that can be used for acoustic waves is limited, which affects their applicability in underwater communication [25]. In contrast to radio communication, where the speed of transmission is the same as the speed of light, the speed of propagation for acoustic communication is slower, i.e., five times slower than radio waves. The end-to-end and propagation delay in acoustic communication in UWSNs is greater due to the slower propagation speed of 1500 m/s. The usable bandwidth for audio communication is under 100 kHz. While most sensors in UWSNs are stationary, they can still move at a speed of 1 to 3 m/sec [16][26][27][28][29]. Figure 1 shows the UWSNs architecture. The sensor nodes deployed in UWSNs environment are labeled as sensor node A, B …. O and these nodes communicate under the water via acoustic waves.
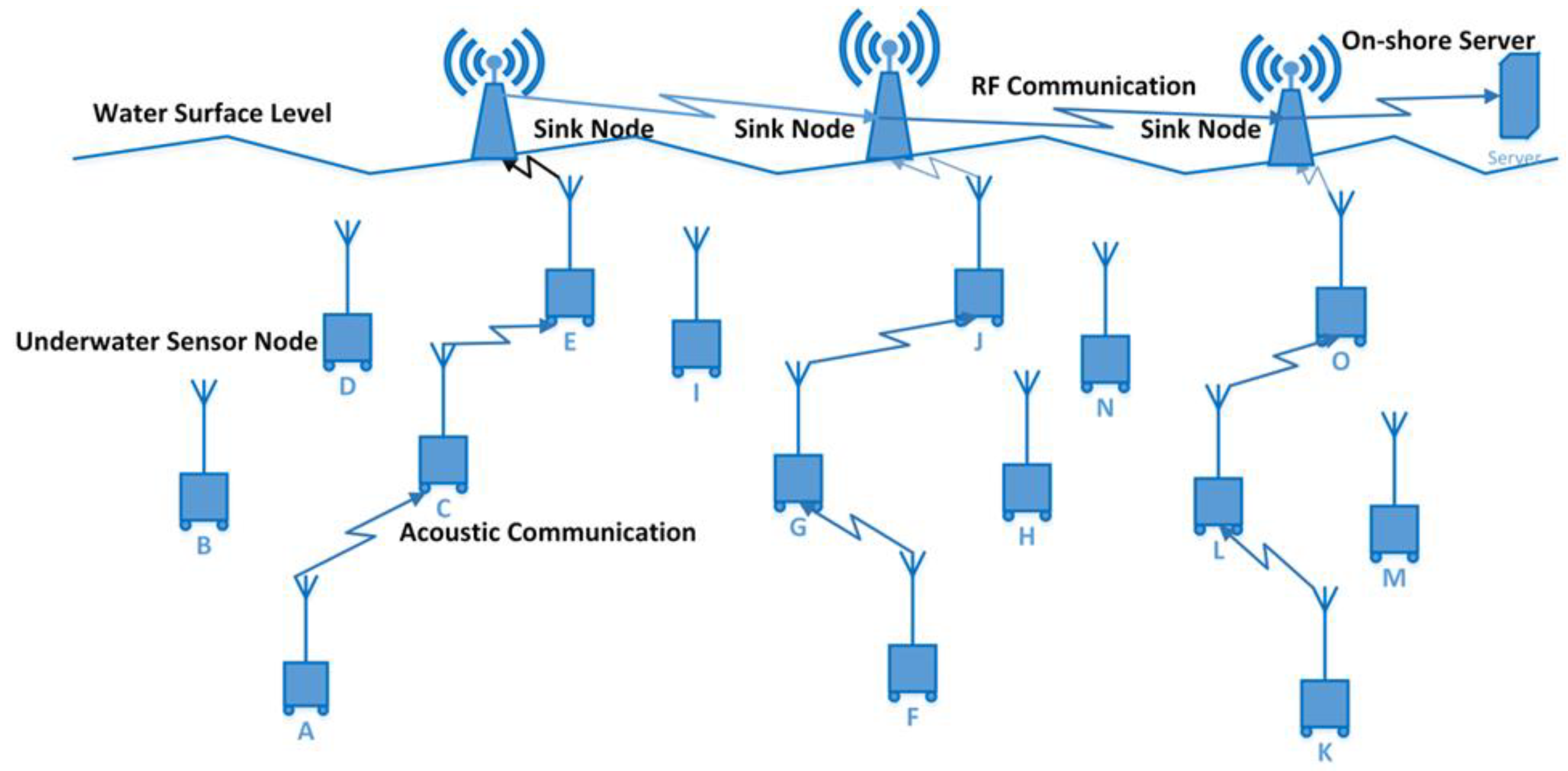
Figure 1. UWSNs Architecture.
2. Adaptive Mobility of Courier Nodes in Threshold-optimized Depth-based Routing Protocol
The AMCTD protocol for UWSNs environments addresses the issues of short periods of stability, rapid energy consumption by nodes with low depth, and slow throughput during these unstable periods. By leveraging courier nodes to optimize movement under the network’s sparse conditions, AMCTD promotes global load balancing. The protocol enables efficient consumption of energy by the sensor nodes in the UWSNs environment. Figure 2a,b show the AMCTD flowchart and data transmission, respectively.
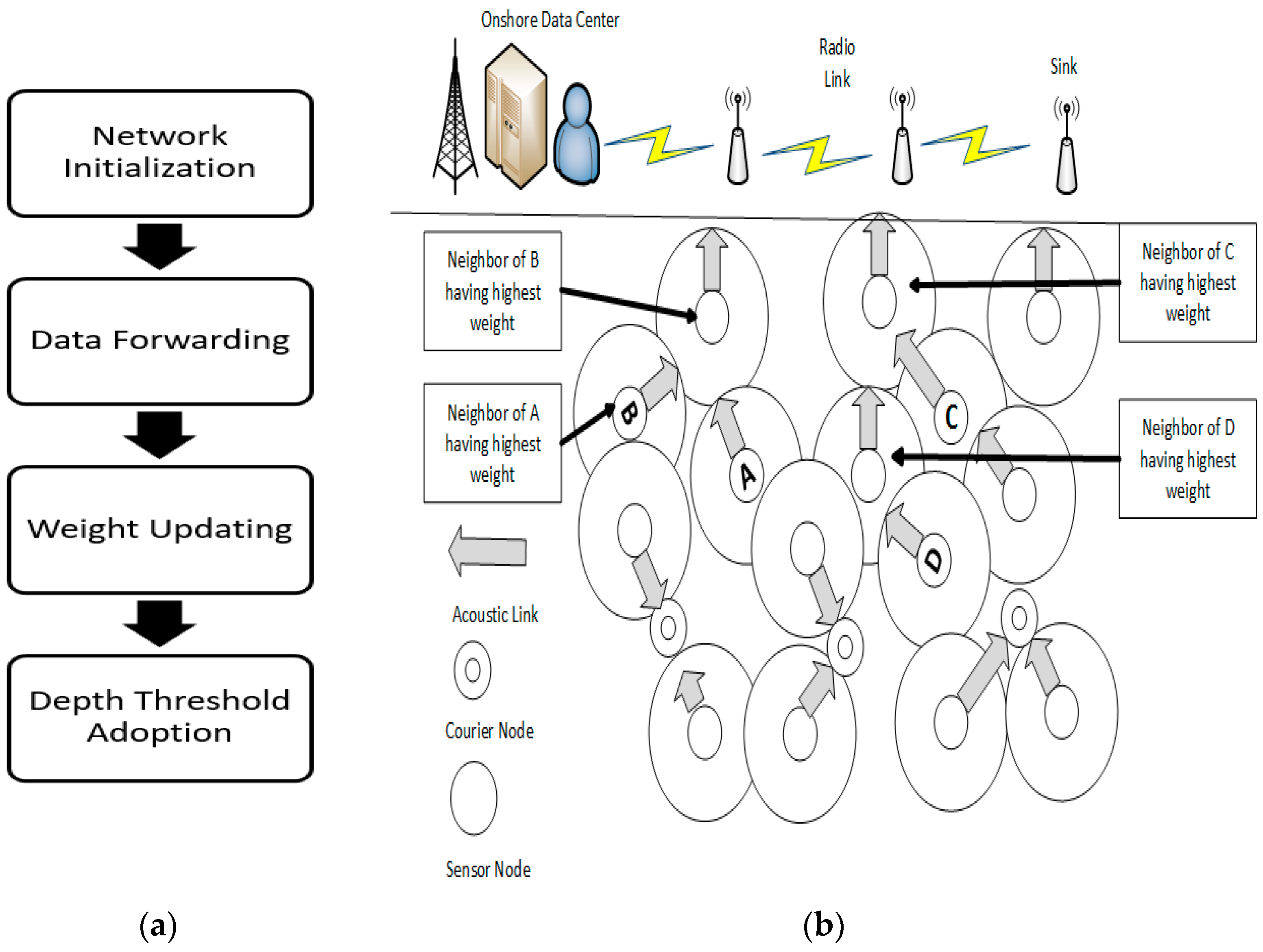
Figure 2. (a) Block diagram of AMCTD. (b) Data Transmission in AMCTD Protocol.
Hello packets are broadcasted by the sensor nodes in the first phase. Communication between sink, sensor and courier nodes starts up the network. Equation (1) is used by each sensor node to compute its weight.
where Wi represents weight of node i; Di represents depth of node i; Ri represents residual energy of node i; and priority value is constant.
Wi = (Priority value × Ri)/(Depth of water − Di)
Weight and depth of each sensor node are shared with the nearby sensor nodes during the setup phase. In this step, the neighbors within the transmission range are identified and placed in a separate queue in order to aid in finding the optimal forwarder. The sensor node transmits data towards the sink using the CSMA/CA technique in the next phase. The source node chooses the optimal forwarder by comparing their weights. The best forwarder node is the sensor node in the immediate vicinity with the highest weight.
Once the number of dead nodes in the UWSNs has increased by 2% during the weight update phase, each node then calculates its weight, utilizing Equation (2).
Wi = (priority value × Di)/Ri
The last step includes the motion of the courier sensor nodes, along with the variation in depth threshold of the nodes, designed to deal with the network sparsity.
Wi = Ri/(priority value × Di)
The AMCTD protocol in UWSNs is affected by noise, attenuation, path loss and signal to noise ratio.
3. Adaptive Mobility of Courier Nodes in Threshold-optimized Depth-based Routing Protocol and Active Attacks
Various scenarios of active attacks with variations of attacker nodes were implemented in the AMCTD protocol. Scenarios include a combination of 4, 8 and 12 attacker nodes. Different combinations of attacker nodes were utilized for the performance assessment of AMCTD in different scenarios having different numbers of attacker nodes. In UWSNs, randomly chosen sensor nodes were set up as attacker nodes. These attacker nodes had more leftover energy than the other nodes in the UWSNs environment, which increased the likelihood that one of them would be chosen as a carrier node. If an attacker node is chosen as the carrier node, the data will not be sent to the sink node and will be dropped. The data will be transmitted to the sink if the real sensor node is chosen as a carrier node. In UWSNs environment, sensor node communication is multi-hop, meaning that if an attacker node is engaged during the data transmission among the source and sink node, the data will be lost. Performance will suffer if an attacker node is chosen as a carrier node. The AMCTD protocol will perform much worse the more attacker nodes it encounters. Figure 3 depicts the steps taken to implement an active attack using the AMCTD protocol.
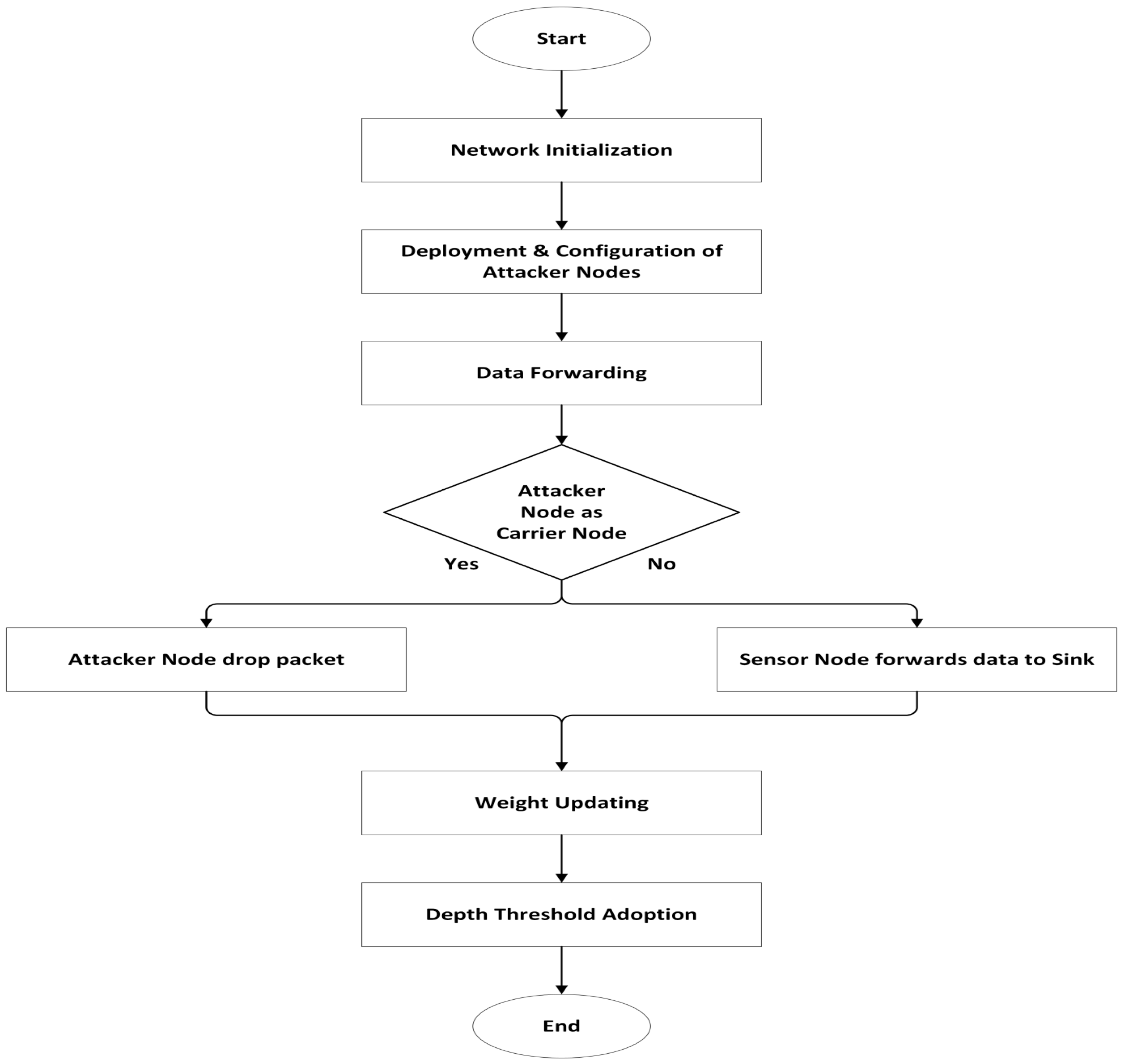
Figure 3. Active Attack in AMCTD.
References
- Sun, N.; Wang, X.; Han, G.; Peng, Y.; Jiang, J. Collision-free and low delay MAC protocol based on multi-level quorum system in underwater wireless sensor networks. Comput. Commun. 2021, 173, 56–69.
- Khan, H.; Hassan, S.A.; Jung, H. On underwater wireless sensor networks routing protocols: A review. IEEE Sens. J. 2020, 20, 10371–10386.
- Ismail, A.S.; Wang, X.; Hawbani, A.; Alsamhi, S.; Abdel Aziz, S. Routing protocols classification for underwater wireless sensor networks based on localization and mobility. Wirel. Netw. 2022, 28, 797–826.
- Gola, K.K.; Dhingra, M.; Gupta, B.; Rathore, R. An empirical study on underwater acoustic sensor networks based on localization and routing approaches. Adv. Eng. Softw. 2023, 175, 103319.
- Cuzme-Rodríguez, F.; Velasco-Suárez, A.; Domínguez-Limaico, M.; Suárez-Zambrano, L.; Farinango-Endara, H.; Mediavilla-Valverde, M. Application for the Study of Underwater Wireless Sensor Networks: Case Study. Trends Artif. Intell. Comput. Eng. Proc. ICAETT 2023, 2022, 124–136.
- Sathish, K.; Ravikumar, C.V.; Rajesh, A.; Pau, G. Underwater wireless sensor network performance analysis using diverse routing protocols. J. Sens. Actuator Netw. 2022, 11, 64.
- Khasawneh, A.M.; Kaiwartya, O.; Abualigah, L.M.; Lloret, J. Green computing in underwater wireless sensor networks pressure centric energy modeling. IEEE Syst. J. 2020, 14, 4735–4745.
- Bhaskarwar, R.V.; Pete, D.J. Clustering with Compressive Sensing Technique for Network Lifetime Enhancement in Underwater Wireless Sensor Networks. In Proceedings of the International Conference on Communication and Computational Technologies: ICCCT 2022, Jaipur, India, 26–27 February 2022; pp. 479–491.
- Lu, Q.; Liu, F.; Zhang, Y.; Jiang, S. Routing protocols for underwater acoustic sensor networks: A survey from an application perspective. In Advances in Underwater Acoustics; Intech Open: Rijeka, Croatia, 2017; p. 23.
- Ahmed, S.; Javaid, N.; Khan, F.A.; Durrani, M.Y.; Ali, A.; Shaukat, A.; Sandhu, M.M.; Khan, Z.A.; Qasim, U. Co-UWSN: Cooperative energy-efficient protocol for underwater WSNs. Int. J. Distrib. Sens. Netw. 2015, 11, 891410.
- Heidemann, J.; Ye, W.; Wills, J.; Syed, A.; Li, Y. Research challenges and applications for underwater sensor networking. In Proceedings of the IEEE Wireless Communications and Networking Conference, 2006, Las Vegas, NV, USA, 3–6 April 2006; Volume 1, pp. 228–235.
- Pompili, D.; Melodia, T. Three-dimensional routing in underwater acoustic sensor networks. In Proceedings of the 2nd ACM International Workshop on Performance Evaluation of Wireless Ad Hoc, Sensor, and Ubiquitous Networks, Montreal, QC, Canada, 10–13 October 2005; pp. 214–221.
- Venkateswara Rao, P.V.; Mohan Krishna Varma, N.; Sudhakar, R. A Systematic Survey on Software-Defined Networks, Routing Protocols and Security Infrastructure for Underwater Wireless Sensor Networks (UWSNs). In Emerging Research in Data Engineering Systems and Computer Communications; Springer: Singapore, 2020; pp. 551–559.
- Khan, Z.A.; Karim, O.A.; Abbas, S.; Javaid, N.; Zikria, Y.B.; Tariq, U. Q-learning based energy-efficient and void avoidance routing protocol for underwater acoustic sensor networks. Comput. Netw. 2021, 197, 108309.
- Zhang, R.; Zhang, J.; Wang, Q.; Zhang, H. DOIDS: An Intrusion Detection Scheme Based on DBSCAN for Opportunistic Routing in Underwater Wireless Sensor Networks. Sensors 2023, 23, 2096.
- Jodeh, H.; Mikkawi, A.; Awad, A.; Othman, O. Comparative analysis of routing protocols for under-water wireless sensor networks. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, Amman, Jordan, 26–27 June 2018; pp. 1–7.
- Ahmad, B.; Jian, W.; Enam, R.N.; Abbas, A. Classification of DoS attacks in smart underwater wireless sensor network. Wirel. Pers. Commun. 2021, 116, 1055–1069.
- Barati, A.; Dehghan, M.; Movaghar, A.; Barati, H. Improving fault tolerance in ad-hoc networks by using residue number system. J. Appl. Sci. 2008, 8, 3273–3278.
- Javanmardi, S.; Barati, A.; Dastgheib, S.J.; Attarzadeh, I. A novel approach for faulty node detection with the aid of fuzzy theory and majority voting in wireless sensor networks. Int. J. Adv. Smart Sens. Netw. Syst. 2012, 2, 1–10.
- Khazaei, E.; Barati, A.; Movaghar, A. Improvement of fault detection in wireless sensor networks. In Proceedings of the 2009 ISECS International Colloquium on Computing, Communication, Control, and Management, Sanya, China, 8–9 August 2009; Volume 4, pp. 644–646.
- Barati, A.; Movaghar, A.; Sabaei, M. RDTP: Reliable data transport protocol in wireless sensor networks. Telecommun. Syst. 2016, 62, 611–623.
- Akbari, M.R.; Barati, H.; Barati, A. An overlapping routing approach for sending data from things to the cloud inspired by fog technology in the large-scale IoT ecosystem. Wirel. Netw. 2022, 28, 521–538.
- Waite, A.D. Sonar for Practising Engineers; Wiley: Hoboken, NJ, USA, 2002.
- Ahmad, I.; Rahman, T.; Zeb, A.; Khan, I.; Ullah, I.; Hamam, H.; Cheikhrouhou, O. Analysis of security attacks and taxonomy in underwater wireless sensor networks. Wirel. Commun. Mob. Comput. 2021, 2021, 1444024.
- Pranitha, B.; Anjaneyulu, L. Analysis of underwater acoustic communication system using equalization technique for ISI reduction. Procedia Comput. Sci. 2020, 167, 1128–1138.
- Chen, K.; Zhou, Y.; He, J. A localization scheme for underwater wireless sensor networks. Int. J. Adv. Sci. Technol. 2009, 4, 9–16.
- Javaid, N.; Jafri, M.R.; Khan, Z.A.; Qasim, U.; Alghamdi, T.A.; Ali, M. IAMCTD: Improved adaptive mobility of courier nodes in threshold-optimized DBR protocol for underwater wireless sensor networks. Int. J. Distrib. Sens. Netw. 2014, 10, 213012.
- Ahmed, S.; Javaid, N.; Ahmad, A.; Ahmed, I.; Durrani, M.Y.; Ali, A.; Haider, S.B.; Ilahi, M. SPARCO: Stochastic performance analysis with reliability and cooperation for underwater wireless sensor networks. J. Sens. 2016, 2016, 7604163.
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An efficient metaheuristic-based clustering with routing protocol for underwater wireless sensor networks. Sensors 2022, 22, 415.
More
Information
Subjects:
Computer Science, Cybernetics
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
694
Revisions:
2 times
(View History)
Update Date:
29 Jan 2024
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




