Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Hugo Plácido da Silva | -- | 1963 | 2024-01-23 07:32:47 | | | |
| 2 | Camila Xu | Meta information modification | 1963 | 2024-01-23 07:52:02 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Louro Da Silva, M.; Gouveia, C.; Albuquerque, D.F.; Plácido Da Silva, H. Radar-Based Invisible Biometric Authentication. Encyclopedia. Available online: https://encyclopedia.pub/entry/54224 (accessed on 07 February 2026).
Louro Da Silva M, Gouveia C, Albuquerque DF, Plácido Da Silva H. Radar-Based Invisible Biometric Authentication. Encyclopedia. Available at: https://encyclopedia.pub/entry/54224. Accessed February 07, 2026.
Louro Da Silva, Maria, Carolina Gouveia, Daniel Filipe Albuquerque, Hugo Plácido Da Silva. "Radar-Based Invisible Biometric Authentication" Encyclopedia, https://encyclopedia.pub/entry/54224 (accessed February 07, 2026).
Louro Da Silva, M., Gouveia, C., Albuquerque, D.F., & Plácido Da Silva, H. (2024, January 23). Radar-Based Invisible Biometric Authentication. In Encyclopedia. https://encyclopedia.pub/entry/54224
Louro Da Silva, Maria, et al. "Radar-Based Invisible Biometric Authentication." Encyclopedia. Web. 23 January, 2024.
Copy Citation
Bio-Radar (BR) systems have shown great promise for biometric applications. Conventional methods can be forged, or fooled; even alternative methods intrinsic to the user, such as the Electrocardiogram (ECG), present drawbacks as they require contact with the sensor.
bio-radar
biometrics
electrocardiogram
support vector machines
1. Introduction
The term Biometrics is composed of two Greek words: bios, meaning life, and metrikos, meaning to measure [1]. Biometrics is defined as the recognition of a person’s identity based on their behavioural or biological characteristics. Since these cannot be misplaced nor forgotten, representing a tangible component of something that a user is, they are advantageous as a recognition method [2].
Nonetheless, conventional biometric systems are still vulnerable to attacks, the most common ones being spoofing, i.e., when an individual poses as another person, and subsequently gains illegitimate access [3]. Examples include the reproduction of anatomical features, such as the acquisition of facial images [4], or using gummy fingers [5], as well as the replica of behavioural features, such as the reproduction of voices [6] or handwritten signature [7]. Therefore, there is a need to explore other options less vulnerable to eavesdropping (i.e., stealthy trait measurement) or spoofing attacks [8]. Typically, the liveness information can be used as a countermeasure, since it is capable of detecting signs of life [3].
Radar systems are able to measure the chest wall displacement during the cardiopulmonary activity with the use of electromagnetic waves. These systems, henceforth referred to as the Bio-Radar (BR) systems, can not only be used as a diagnosis tool, but also contribute to lifestyle improvement [9]. BR monitoring can be seamlessly integrated into everyday routines; with the ability to map subjects to their identity, this approach could act as a health monitoring system, integrated into the context of “smart homes”. Moreover, these systems can be particularly beneficial in authentication applications, that is, in 1:1 matching.
2. Biometrics and the Importance of the Bio-Radar
Biometric recognition can be done using two distinct approaches: authentication and identification. Authentication aims to answer the question “Am I who I claim to be?” whereas Identification answers “Who am I?”. The former’s objective is to verify a person’s claimed identity, and is the main focus of this work, whilst the latter seeks to establish a subject’s identity [2].
Typically, biometric systems are divided into two categories: biological and/or behavioural. Biological biometrics are based on data taken from a direct part of the human body, whereas behavioural characteristics are based on an action taken by a person. Examples of the first include the use of the ears, face, fingerprints, irises, palms, or even physiological signals such as the Electrocardiogram (ECG), whereas the second includes gait, keystroke dynamics, as well as signature and voice recognition. These can be collected through specialised image or video capturing devices, or by contact sensors [2].
Recently, research on biosignal-based approaches has been pursued to address the limitations of conventional biometric systems, as introduced in Section 1, within which the ECG has shown promising results [8]. Its nature makes it hard to capture, and the inherent liveness makes it useful for spoofing purposes [3][8][10]. Moreover, it has been shown to possess high inter-subject variability and low intra-subject variability [8]. Regardless, ECG-based biometrics require contact with the body, which may be unpractical and disruptive to the users. To mitigate these limitations, alternatives have been explored, paving the way towards invisible approaches, which can be integrated on the topic of “smart homes”, where sensors are incorporated into day-to-day objects, allowing data acquisition during the subject’s daily activities [11]. BR systems, due to their unobtrusive nature, are particularly interesting. They send a continuous electromagnetic signal towards a subject; when the subject’s chest moves as a consequence of the cardiorespiratory activity, there is a modulation resulting from the vital signals [12].
The use of such systems can lead to innovative applications. They have shown several employments with examples ranging from the ability to detect signals through barriers such as clothes, as well as insensibility to environment factors, to identifying sudden events, and contributing to lifestyle improvement, through continuous monitoring [9][13][14]. BR systems have proved to be able of being integrated into custom objects to meet market needs. Furthermore, in such applications, these frameworks may be shared among multiple people within the household, and consequently, the ability to match the recorded data to the individual that provided it is a necessary feature. For instance, regarding the topic of “smart homes”, a possible multimodal approach in sanitary installations alongside the ECG [15] may also be pursued. It is also important to take into consideration that, in these circumstances, there is a reduced number of subjects within the household. Furthermore, considering the integration of a BR system in a car seat [16][17], it may allow the personalisation of a car’s settings, or even car-sharing, all of which require the ability to know the driver’s identity [18].
3. The Bio-Radar System
Radar stands for “Radio Detection And Ranging”, and it consists of a transmitter, a receiver, an antenna, and signal processing software [9][19]. The BR system uses the principles of radar technology; Figure 1a presents a schema of a general BR system.
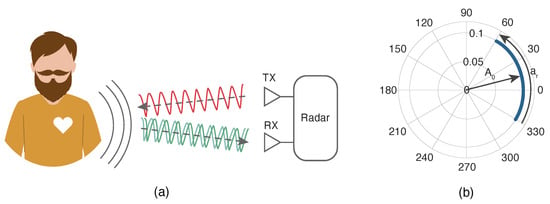
Figure 1. Basic model of a radar system applied to the measurement of vital signs. (a) represents the ideal scenario, where RX is the receiving antenna and TX the transmitting one; (b) represents the signal for an ideal scenario in the complex plane. Adapted from [9].
3.1. Doppler Radar
Based on the Doppler radar, the BR system allows the cardiorespiratory motion sensing, with precision and with no direct contact with the subject [9].
As an object undergoes motion, the radar signal reflected off the object experiences frequency shifts due to the Doppler effect [20]. Additionally, micro-Doppler analysis centres on extracting further information from the Doppler signature past the primary motion of the entire target. It investigates the smaller, modulated variations within the Doppler signature caused by the motion of internal body parts or other vibrating components within the target. For instance, in vital signs monitoring, micro-Doppler analysis can distinguish and analyse small Doppler shifts caused by chest wall movements amid breathing or heartbeats. By considering these micro-Doppler signatures, it is conceivable to estimate vital signs such as respiratory rate and heart rate [21]. Such detection depends on changes in the travelled path of the transmitted signal, which causes a phase modulation on the received signal, when reflected by the human body, more specifically due to displacements caused by both respiratory and cardiac mechanical activity [20].
There are several radar architectures based on the Doppler effect. The chosen architecture for this work is the Continuous Wave (CW) radar, a relatively simple architecture to implement. A CW radar constantly transmits and receives signals with a very narrow bandwidth [22], enabling the detection of the Doppler shift. It senses phase changes when a target is moving, allowing the target’s velocity to be calculated and even distinguish between stationary and moving objects [23].
3.2. Implications of Real-World Applications
As shown in Figure 1a, a sinusoidal signal is continuously transmitted towards the subject’s chest wall. In an ideal scenario, with no parasitic reflections, the physiological signals are perceived as an arc in the complex plane. This is shown in Figure 1b, where 𝐴0 represents the received signal amplitude, and 𝑎𝑟 the phase variation, which is proportional to the amplitude of the motion of the chest wall [9].
Nonetheless, ideal scenarios do not exist. As such, it is important to consider the surrounding conditions. The received signal is the sum of the intended signal with parasitic reflections that occur in the surrounding objects, as depicted in Figure 2a. Parasitic reflections are addressed as Complex Direct Current (CDC) offsets since they cause a misalignment of the signal in respect to the origin, increasing the spectral component magnitude. These are depicted in Figure 2b, where 𝐴1 is the parasitic component amplitude [9]. Researchers refer the reader to the work by Gouveia et al. [9][24] for a more detailed description.
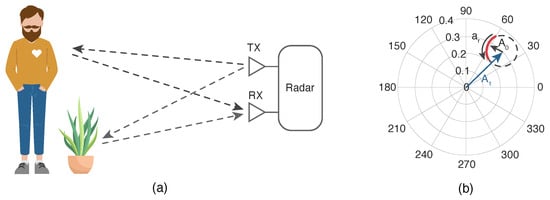
Figure 2. Effect of the surrounding objects: (a) reflections schematics on the environment; (b) equivalent projection of the received signal on the complex plane. Adapted from [9].
4. ECG-Based Biometric Recognition
Fiducial methods are those that typically rely on the use of landmarks in the time domain [8]. As such, it is dependent on the exact detection of points of interest. Initially, pioneering research used predefined medical features as the feature space [25], however it was later proved that this feature space lacked the ability to fully characterise the waveform for biometric purposes, and so revisions were made [26]. Furthermore, to accommodate the users’ needs, it was necessary to turn towards off-the-person/invisible approaches [27].
Nonetheless, this accurate fiducial detection is a difficult task, since there is no universally acknowledged rule, i.e, no way to precisely establish where the limits of the wave lie. Consequently, non-fiducial approaches were created, characterised by the lack of reference detection. Non-fiducial methods are described as those able to extract information without the need of localising fiducial points [8][28]. Usually, these methods are further divided into transform domain approaches [29] and other approaches [30], where the former concerns, as the name implies, feature extraction in the frequency domain.
Even so, the detection of R-peak proved to be desirable, which led to the partially fiducial methods, also addressed as hybrid. These methods make use of the R-peak to segment the waveform, either adopting the full waveform or a subset of it [27].
5. BR-Based Biometric Recognition
In spite of this, ECG-based biometrics require contact with the body, thus being unpractical and disruptive to users’ regular interaction. Therefore, there was the need to explore a novel invisible approach, namely the use of BR systems. That said, the use of these radars for identity recognition is still in its inception.
The detection of cardiopulmonary signals using a radar system has already been made possible [31]; moreover, in 2004 it has been demonstrated that it is possible to measure the cardiac and respiratory activity through walls [32]. In 2006, the Doppler effect was used to estimate the amount of individuals in a room [33]. Additionally, these systems could also be used to study the different stages of the heart contraction cycle [34]. Furthermore, in the last few years, research has turned to the use of cardiopulmonary signals as a biometric modality. Table 1 shows a summary of these approaches and their performance.
Table 1. Summary of state of the art approaches for BR biometrics. The Feature and Classifier columns present the feature method and classifier of choice. # shows the number of subjects, and lastly Accuracy (Acc) (%) and Equal Error Rate (EER) (%) display the accuracy and equal error rate in percentage.
shows the number of subjects, and lastly Accuracy (Acc) (%) and Equal Error Rate (EER) (%) display the accuracy and equal error rate in percentage.
 shows the number of subjects, and lastly Accuracy (Acc) (%) and Equal Error Rate (EER) (%) display the accuracy and equal error rate in percentage.
shows the number of subjects, and lastly Accuracy (Acc) (%) and Equal Error Rate (EER) (%) display the accuracy and equal error rate in percentage.| Year | Feature | Classifier | #  |
Acc % | EER % | Refs. |
|---|---|---|---|---|---|---|
| 2015 | DWT | k-NN 2 | 26 | 19.0 | – | [13] |
| 2016 | Breathing energy, frequency and patterns |
Neural Network | 3 | 92.13 | – | [35] |
| 2017 | Geometric Features | SVM | 78 | 98.61 | 4.42 | [36] |
| 2018 | Local Heartbeat | SVM | 4 | 94.6 | – | [37] |
| 2018 | Spectrogram | CNN 3 | 4 | 98.5 | – | [38] |
| 2018 | Various 1 | k-NN | 6 | 95.0 | – | [39] |
| 2019 | FFT | SVM | 6 | 100 | – | [12] |
| 2020 | Various 1 | SVM | 10 | 92 | – | [40] |
| 2020 | Breathing energy, frequency and patterns |
k-NN | 5 | 93.75 | – | [41] |
Data were collected in these experiments. Legend: 1 Breathing/heart rate; inhale/exhale speed, average distances and standard deviation of peaks; breathing depth; spectral entropy; and dynamic segmentation. Dynamic segmentation is the act of segmenting a breathing cycle episode with 30–70% amplitude and calculating the average area ratio of the inhale and exhale segment; 2 k-Nearest Neighbour; 3 Convolutional Neural Network.
In 2015, the first use of the cardiac radar signal as a biometric modality was described [13]. Shortly after, a continuous authentication system, the Cardiac Scan, was introduced. This system was based on the acquisition of geometric features of the cardiac motion, introducing the notion of “fiducial-based” identity descriptors in BR biometrics [36]. Moreover, “partially fiducial-based” features have also been pursued to establish a reproducible approach in the time domain [37]. Finally, a “non-fiducial” approach has also been described using spectrograms [38].
Unlike the former studies, other works have focused on the breathing patterns, instead of the cardiac signal [35]. These typically used “fiducial” descriptors to describe the breathing cycle [39], having been proved successful in identifying individuals under different conditions, as well as with obstructive sleep apnoea [40][41]. Nevertheless, the adopted algorithm produced false classifications, and so “non-fiducial approaches” have also been described, using the Fast Fourier Transform (FFT) [12].
References
- Prabhakar, S.; Pankanti, S.; Jain, A. Biometric recognition: Security and privacy concerns. IEEE Secur. Priv. 2003, 1, 33–42.
- Jain, A.K.; Bolle, R.; Pankanti, S. Biometrics: Personal Identification in Networked Society; Kluwer Academic Publishers: Norwell, MA, USA, 2002; ISBN 978-0-7923-8345-1.
- Hadid, A. Face Biometrics under Spoofing Attacks: Vulnerabilities, Countermeasures, Open Issues, and Research Directions. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR) Workshops, Columbus, OH, USA, 23–28 June 2014.
- Noureddine, B.; Naït-ali, A.; Fournier, R.; Bereksi Reguig, F. ECG Based Human Authentication using Wavelets and Random Forests. Int. J. Cryptogr. Inf. Secur. 2012, 2, 1–11.
- Matsumoto, T.; Matsumoto, H.; Yamada, K.; Hoshino, S. Impact of artificial “gummy” fingers on fingerprint systems. In Proceedings of the Optical Security and Counterfeit Deterrence Techniques IV, San Jose, CA, USA, 23–25 January 2002; Volume 4677, pp. 275–289.
- Phillips, P.; Martin, A.; Wilson, C.; Przybocki, M. An introduction evaluating biometric systems. Computer 2000, 33, 56–63.
- Singh, Y.N.; Gupta, P. ECG to Individual Identification. In Proceedings of the IEEE Second International Conference on Biometrics: Theory, Applications and Systems, Washington, DC, USA, 29 September–1 October 2008; pp. 1–8.
- Ribeiro Pinto, J.; Cardoso, J.S.; Lourenço, A. Evolution, Current Challenges, and Future Possibilities in ECG Biometrics. IEEE Access 2018, 6, 34746–34776.
- Gouveia, C.; Albuquerque, D.; Vieira, J.; Pinho, P. Dynamic digital signal processing algorithm for vital sign extraction in continuous-wave radars. Remote Sens. 2021, 13, 4079.
- Komeili, M.; Armanfard, N.; Hatzinakos, D. Liveness Detection and Automatic Template Updating Using Fusion of ECG and Fingerprint. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1810–1822.
- da Silva, H.P. Biomedical Sensors as Invisible Doctors. In Regenerative Design in Digital Practice: A Handbook for the Built Environment; Eurac Research: Bolzano, Italy, 2019; pp. 322–329.
- Islam, S.M.M.; Rahman, A.; Prasad, N.; Boric-Lubecke, O.; Lubecke, V.M. Identity Authentication System using a Support Vector Machine (SVM) on Radar Respiration Measurements. In Proceedings of the ARFTG Microwave Measurement Conference (ARFTG), Boston, MA, USA, 7 June 2019; pp. 1–5.
- Rissacher, D.; Galy, D. Cardiac radar for biometric identification using nearest neighbour of continuous wavelet transform peaks. In Proceedings of the IEEE International Conference on Identity, Security and Behavior Analysis (ISBA), Hong Kong, China, 23–25 March 2015; pp. 1–6.
- Hu, W.; Zhao, Z.; Wang, Y.; Zhang, H.; Lin, F. Noncontact Accurate Measurement of Cardiopulmonary Activity Using a Compact Quadrature Doppler Radar Sensor. IEEE Trans. Biomed. Eng. 2014, 61, 725–735.
- Silva, A.S.; Correia, M.V.; de Melo, F.; da Silva, H.P. Identity Recognition in Sanitary Facilities Using Invisible Electrocardiography. Sensors 2022, 22, 4201.
- Schires, E.; Georgiou, P.; Lande, T.S. Vital Sign Monitoring Through the Back Using an UWB Impulse Radar With Body Coupled Antennas. IEEE Trans. Biomed. Circuits Syst. 2018, 12, 292–302.
- Hui, X.; Kan, E.C. Seat Integration of RF Vital-Sign Monitoring. In Proceedings of the IEEE MTT-S International Microwave Biomedical Conference (IMBioC), Nanjing, China, 6–8 May 2019; Volume 1, pp. 1–3.
- Lourenço, A.; Alves, A.P.; Carreiras, C.; Duarte, R.P.; Fred, A. CardioWheel: ECG biometrics on the steering wheel. In Proceedings of the Joint European conference on machine learning and knowledge discovery in databases, Porto, Portugal, 7–11 September 2015; pp. 267–270.
- Onoja, A.E.; Oluwadamilola, A.M.; Ajao, L.A. Embedded system based radio detection and ranging (RADAR) system using Arduino and ultra-sonic sensor. Am. J. Embed. Syst. Appl. 2017, 5, 7–12.
- Boric-Lubecke, O.; Lubecke, V.; Droitcour, A.; Park, B.K.; Singh, A. Doppler Radar Physiological Sensing; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2016; pp. 1–288.
- Chen, V. The Micro-Doppler Effect in Radar; Artech House Radar Library, Artech House: Boston, MA, USA, 2019.
- Banks, D. Continuous wave (CW) radar. In Proceedings of the Electronics and Aerospace Systems Convention, Washington, DC, USA, 29 September–1 October 1975.
- Lin, J.C. Microwave sensing of physiological movement and volume change: A review. Bioelectromagnetics 1992, 13, 557–565.
- Gouveia, C.; Albuquerque, D.; Pinho, P.; Vieira, J. Evaluation of Heartbeat Signal Extraction Methods Using a 5.8 Hz Doppler Radar System in a Real Application Scenario. IEEE Sensors J. 2022, 22, 7979–7989.
- Biel, L.; Pettersson, O.; Philipson, L.; Wide, P. ECG analysis: A new approach in human identification. IEEE Trans. Instrum. Meas. 2001, 50, 808–812.
- Israel, S.; Irvine, J.; Cheng, A.; Wiederhold, M.; Wiederhold, B. ECG to identify individuals. Pattern Recognit. 2005, 38, 133–142.
- da Silva, H.P.; Fred, A.; Lourenço, A.; Jain, A.K. Finger ECG signal for user authentication: Usability and performance. In Proceedings of the IEEE International Conference on Biometrics: Theory, Applications and Systems (BTAS), Arlington, VA, USA, 23 September–2 October 2013; pp. 1–8.
- Hassan, Z.; Gilani, S.; Jamil, M. Review of Fiducial and Non-Fiducial Techniques of Feature Extraction in ECG based Biometric Systems. Indian J. Sci. Technol. 2016, 9, 94841.
- Odinaka, I.; Lai, P.H.; Kaplan, A.D.; O’Sullivan, J.A.; Sirevaag, E.J.; Kristjansson, S.D.; Sheffield, A.K.; Rohrbaugh, J.W. ECG biometrics: A robust short-time frequency analysis. In Proceedings of the IEEE International Workshop on Information Forensics and Security, Seattle, WA, USA, 12–15 December 2010; pp. 1–6.
- Coutinho, D.P.; Fred, A.L.; Figueiredo, M.A. One-lead ECG-based personal identification using Ziv-Merhav cross parsing. In Proceedings of the International Conference on Pattern Recognition, Istanbul, Turkey, 23–26 August 2010; pp. 3858–3861.
- Hu, F.; Singh, A.; Boric-Lubecke, O.; Lubecke, V. Medical Sensing Using Doppler Radar. In Telehealthcare Computing and Engineering Principles and Design; CRC Press LLC: Boca Raton, FL, USA, 2013; Chapter 10; pp. 281–301.
- Petkie, D.T.; Bryan, E.; Benton, C.; Phelps, C.; Yoakum, J.; Rogers, M.; Reed, A. Remote respiration and heart rate monitoring with millimeter-wave/terahertz radars. In Millimetre Wave and Terahertz Sensors and Technology; Krapels, K.A., Salmon, N.A., Eds.; International Society for Optics and Photonics, SPIE: Bellingham, WA, USA, 2008; Volume 7117.
- Zhou, Q.; Liu, J.; Host-Madsen, A.; Boric-Lubecke, O.; Lubecke, V. Detection of Multiple Heartbeats Using Doppler Radar. In Proceedings of the IEEE International Conference on Acoustics Speech and Signal Processing, Toulouse, France, 14–19 May 2006; Volume 2.
- Droitcour, A.D. Non-Contact Measurement of Heart and Respiration Rates with a Single-Chip Microwave Doppler Radar. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 2006.
- Rahman, A.; Yavari, E.; Lubecke, V.M.; Lubecke, O.B. Noncontact Doppler radar unique identification system using neural network classifier on life signs. In Proceedings of the IEEE Topical Conference on Biomedical Wireless Technologies, Networks, and Sensing Systems (BioWireleSS), Austin, TX, USA, 24–27 January 2016; pp. 46–48.
- Lin, F.; Song, C.; Zhuang, Y.; Xu, W.; Li, C.; Ren, K. Cardiac Scan: A Non-Contact and Continuous Heart-Based User Authentication System. In Proceedings of the Annual International Conference on Mobile Computing and Networking, San Jose, CA, USA, 23–25 January 2017; pp. 315–328.
- Shi, K.; Will, C.; Weigel, R.; Koelpin, A. Contactless person identification using cardiac radar signals. In Proceedings of the IEEE International Instrumentation and Measurement Technology Conference (I2MTC), Houston, TX, USA, 14–17 May 2018; pp. 1–6.
- Cao, P.; Xia, W.; Li, Y. Heart ID: Human Identification Based on Radar Micro-Doppler Signatures of the Heart Using Deep Learning. Remote Sens. 2019, 11, 1220.
- Rahman, A.; Lubecke, V.M.; Boric–Lubecke, O.; Prins, J.H.; Sakamoto, T. Doppler Radar Techniques for Accurate Respiration Characterization and Subject Identification. IEEE J. Emerg. Sel. Top. Circuits Syst. 2018, 8, 350–359.
- Islam, S.M.M.; Sylvester, A.; Orpilla, G.; Lubecke, V.M. Respiratory Feature Extraction for Radar-Based Continuous Identity Authentication. In Proceedings of the IEEE Radio and Wireless Symposium (RWS), San Antonio, TX, USA, 26–29 January 2020; pp. 119–122.
- Islam, S.M.M.; Rahman, A.; Yavari, E.; Baboli, M.; Boric-Lubecke, O.; Lubecke, V.M. Identity Authentication of OSA Patients Using Microwave Doppler radar and Machine Learning Classifiers. In Proceedings of the IEEE Radio and Wireless Symposium (RWS), San Antonio, TX, USA, 26–29 January 2020; pp. 251–254.
More
Information
Subjects:
Engineering, Biomedical
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.0K
Revisions:
2 times
(View History)
Update Date:
23 Jan 2024
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




