Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | JUNAID AHMAD KHAN | -- | 1122 | 2024-01-18 18:34:54 | | | |
| 2 | Lindsay Dong | Meta information modification | 1122 | 2024-01-19 04:31:52 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Khan, J.A.; Lim, D.; Kim, Y. Methods for In-Vehicle Intrusion Detection. Encyclopedia. Available online: https://encyclopedia.pub/entry/54067 (accessed on 28 February 2026).
Khan JA, Lim D, Kim Y. Methods for In-Vehicle Intrusion Detection. Encyclopedia. Available at: https://encyclopedia.pub/entry/54067. Accessed February 28, 2026.
Khan, Junaid Ahmad, Dae-Woon Lim, Young-Sik Kim. "Methods for In-Vehicle Intrusion Detection" Encyclopedia, https://encyclopedia.pub/entry/54067 (accessed February 28, 2026).
Khan, J.A., Lim, D., & Kim, Y. (2024, January 18). Methods for In-Vehicle Intrusion Detection. In Encyclopedia. https://encyclopedia.pub/entry/54067
Khan, Junaid Ahmad, et al. "Methods for In-Vehicle Intrusion Detection." Encyclopedia. Web. 18 January, 2024.
Copy Citation
For in-vehicle network communication, the controller area network (CAN) broadcasts to all connected nodes without address validation. Therefore, it is highly vulnerable to all sorts of attack scenarios. Numerous intrusion detection methodologies have been developed to prevent emerging attacks targeting in-vehicle networks, but they also have certain limitations.
intrusion detection
anomaly detection
in-vehicle networks
1. Introduction
As the automotive industry is rapidly evolving to accommodate industry-driven mechanical and communication technologies, there is a constant need for calibrated actuators, advanced sensors, and high-grade electronic control units (ECUs). The typical structure of a vehicle’s domain architecture is depicted in Figure 1 and is segmented to support the powertrain, chassis, body, and driver assistance tasks connected to many subsystems. The complexity of such subsystems used in vehicles increases with each hardware addition [1]. To comply with industry requirements, the controller area network (CAN) bus is the classic in-vehicle automotive network, allowing vehicles to reduce wiring complications and reap the benefits of design simplification. Since the CAN network is primarily responsible for real-time communication between the connected ECUs and the in-vehicle automotive network, data must accurately and reliably flow with extremely low latency [2]. Such a data-intensive application is inherently subject to malicious attacks; therefore, the automotive-based applications of the CAN bus require cutting-edge intrusion detection systems (IDS) with high accuracy and detection rates.
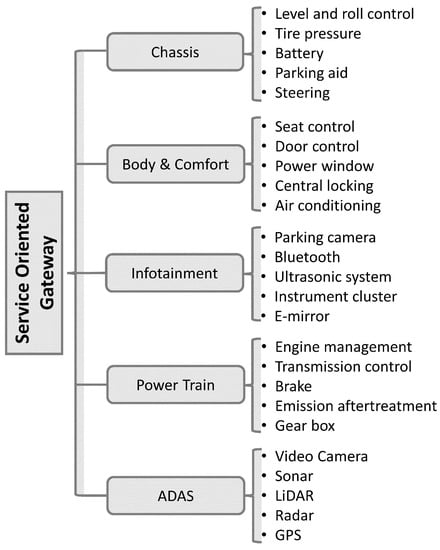
Figure 1. Vehicle domain architecture.
One way to protect the CAN bus communication for the in-vehicle automotive network is by incorporating security elements such as a reliable IDS capable of detecting various attack scenarios. Extensive research has been carried out on CAN bus IDS for in-vehicle automotive networks [3][4][5]. While the effects of CAN bus vulnerabilities have necessitated an upgrade of security requirements for in-vehicle networks over the last decade, an integrated IDS has proven to have significantly enhanced the security features of automotive applications [6][7].
Numerous intrusion detection methodologies have been developed to prevent emerging attacks targeting in-vehicle networks, but they also have certain limitations. For instance, several machine learning (ML)-based techniques have been established for anomaly detection in the CAN network, but the initial model parameter training usually requires a lot of computing power and expensive hardware, making them useless for the automotive industry as a whole [8][9][10]. Message authentication code (MAC) protocols can secure in-vehicle networks, but CAN-bus bandwidth limitation hinders the advancement in this area, which also renders most cryptographic algorithms impractical [11][12][13]. MAC-supported protocols also require altering the mechanisms by which the firmware operates or the way ECUs talk to each other, making them unfavorable for CAN bus security. The potential of parametric-based intrusion detection approaches has also been discussed in the literature. According to [14][15][16][17], the study of frequency-based IDS and the resulting outcome is an essential aspect of in-vehicle CAN bus security. However, frequency-based IDS that calculate the inter-packet timing of CAN bus frames or learn periodicity patterns for anomaly detection have significant drawbacks, such as a few advanced attacks that make these IDS ineffective by gradually changing the periodicity or content of data frames. Windowing and thresholds are used to find intrusions in CAN bus traffic. However, most IDS have not selected the optimal values for these parameters for intrusion detection.
2. Methods for In-Vehicle Intrusion Detection
2.1. Fingerprint-Based Methods
Groundbreaking work by Cho et al. demonstrated that fingerprints of hardware could be used to model the clock’s behavior [18]. The hardware generates unique fingerprint information because of the inherent physical properties, and their IDS uses the cumulative sum method on the fingerprint data collected to detect any possible abnormal behavior of the in-vehicle network. The algorithm calculates a clock offset based on message periodicity, limiting its ability to detect intrusions for aperiodic information. Later in [19], it was also observed that a voltage-based attacker identifier scheme called Viden could be built using voltage measurements to identify attackers. Voltage fingerprints of ECUs using transmitter voltages to create voltage profiles. However, voltage profiles for ECUs are required during the manufacturing stage and are updated through voltage profile adjustments for accurate detection. Researchers in [20] observed that the extra wires needed by voltage-based IDS might introduce various voltage-based attacks into the CAN bus. Moreover, due to hardware failure in their IDS, fuse and circuit breakers must be manually replaced. A similar method was used by Li et al. [21], and exploited temperature variation impact on the voltage characteristics to obtain hardware fingerprints. They showed that the temperature-variable voltage fingerprinting scheme solution is optimal compared to other fingerprint-based IDS. Nevertheless, real-time signal measurement can be a difficult job in a constrained environment and may hinder the implementation of the proposed methods.
2.2. Parametric-Based Method
Taylor et al. [14] detected malicious messages using a Hamming distance between data frames and interpacket timing-based statistics features and indicated that a significant amount of data was required to achieve a low false-positive rate. Song et al. [22] suggested a frequency-based, lightweight IDS for the CAN bus to determine whether the vehicle has been attacked by data injection. The system uses the time interval between CAN data frames for anomaly detection. However, it requires more computing power to analyze the CAN message sequence in order to improve detection accuracy.
2.3. Entropy-Based Methods
Muter and Asaj demonstrated the idea of an entropy-based method for CAN-bus network anomaly detection. Their anomaly detection method calculated the ID frequency for the in-vehicle network [23]. The limitations of the approach include the difficulty of recognizing small-scale attacks. Marchetti et al. assessed the usefulness of an entropy-based intrusion detection method for modern vehicles. Based on experimental data, they showed that accurate attack detection could only be obtained if the abnormal data size was large [24]. Wu et al., used the entropy-based method and enhanced the detection accuracy for in-vehicle automotive network attacks while maintaining a low response time. They also optimized the size of the sliding window [25]. However, calculating the intrusion detection threshold in entropy-based IDS is challenging.
2.4. Deep Learning-Based Methods
Seo et al. suggested a generative adversarial network (GAN)-based IDS for in-vehicle automotive networks using a deep learning method. The GAN-based intrusion detection system (GIDS) was trained on a fake random dataset to detect attacks in real CAN bus data [26]. Moreover, GIDS is incapable of detecting malicious or component-failure data. Later, in [27], CANnolo was proposed to use long short-term memory (LSTM) autoencoders to identify intrusions in CAN bus data. CANnolo generated a model using normal data and detected intrusion based on the difference between reconstructed and real CAN bus data, but it requires complex computation for the in-vehicle environment. Amato et al., in their latest work, suggested a method based on deep learning to detect attacks on CAN-bus data frames [28]. Their work aimed to detect malicious attacks based on the human behavior of attackers. The algorithm applies multilayer perceptrons (MLP) to train it. However, the lack of ensemble learning limits the performance of the model.
References
- Yang, L.; Moubayed, A.; Shami, A. MTH-IDS: A Multitiered Hybrid Intrusion Detection System for Internet of Vehicles. IEEE Internet Things J. 2022, 9, 616–632.
- Young, C.; Zambreno, J.; Olufowobi, H.; Bloom, G. Survey of automotive controller area network intrusion detection systems. IEEE Des. Test 2019, 36, 48–55.
- Xun, Y.; Zhao, Y.; Liu, J. Vehicleeids: A novel external intrusion detection system based on vehicle voltage signals. IEEE Internet Things J. 2021, 9, 2124–2133.
- Sun, H.; Chen, M.; Weng, J.; Liu, Z.; Geng, G. Anomaly Detection for In-Vehicle Network Using CNN-LSTM With Attention Mechanism. IEEE Trans. Veh. Technol. 2021, 70, 10880–10893.
- De Araujo-Filho, P.F.; Pinheiro, A.J.; Kaddoum, G.; Campelo, D.R.; Soares, F.L. An Efficient Intrusion Prevention System for CAN: Hindering Cyber-Attacks With a Low-Cost Platform. IEEE Access 2021, 9, 166855–166869.
- Elkhail, A.A.; Refat, R.U.D.; Habre, R.; Hafeez, A.; Bacha, A.; Malik, H. Vehicle Security: A Survey of Security Issues and Vulnerabilities, Malware Attacks and Defenses. IEEE Access 2021, 9, 162401–162437.
- Gao, C.; Wang, G.; Shi, W.; Wang, Z.; Chen, Y. Autonomous Driving Security: State of the Art and Challenges. IEEE Internet Things J. 2021, 9, 7572–7595.
- Kang, M.J.; Kang, J.W. Intrusion detection system using deep neural network for in-vehicle network security. PLoS ONE 2016, 11, e0155781.
- Kim, J.; Shin, N.; Jo, S.Y.; Kim, S.H. Method of intrusion detection using deep neural network. In Proceedings of the 2017 IEEE International Conference on Big Data and Smart Computing (BigComp), Jeju, Republic of Korea, 13–16 February 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 313–316.
- Wang, Y.; Chia, D.W.M.; Ha, Y. Vulnerability of deep learning model based anomaly detection in vehicle network. In Proceedings of the 2020 IEEE 63rd International Midwest Symposium on Circuits and Systems (MWSCAS), Springfield, MA, USA, 9–12 August 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 293–296.
- Patsakis, C.; Dellios, K.; Bouroche, M. Towards a distributed secure in-vehicle communication architecture for modern vehicles. Comput. Secur. 2014, 40, 60–74.
- Mundhenk, P.; Paverd, A.; Mrowca, A.; Steinhorst, S.; Lukasiewycz, M.; Fahmy, S.A.; Chakraborty, S. Security in automotive networks: Lightweight authentication and authorization. ACM Trans. Des. Autom. Electron. Syst. (TODAES) 2017, 22, 1–27.
- Radu, A.I.; Garcia, F.D. LeiA: A lightweight authentication protocol for CAN. In Proceedings of the European Symposium on Research in Computer Security, Heraklion, Greece, 26–30 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 283–300.
- Taylor, A.; Japkowicz, N.; Leblanc, S. Frequency-based anomaly detection for the automotive CAN bus. In Proceedings of the 2015 World Congress on Industrial Control Systems Security (WCICSS), London, UK, 14–16 December 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 45–49.
- Moore, M.R.; Bridges, R.A.; Combs, F.L.; Starr, M.S.; Prowell, S.J. Modeling inter-signal arrival times for accurate detection of can bus signal injection attacks: A data-driven approach to in-vehicle intrusion detection. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research, Oak Ridge, TN, USA, 4–6 April 2017; pp. 1–4.
- Stabili, D.; Marchetti, M. Detection of missing can messages through inter-arrival time analysis. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7.
- Gmiden, M.; Gmiden, M.H.; Trabelsi, H. An intrusion detection method for securing in-vehicle CAN bus. In Proceedings of the 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA), Sousse, Tunisia, 19–21 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 176–180.
- Cho, K.T.; Shin, K.G. Fingerprinting electronic control units for vehicle intrusion detection. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 911–927.
- Cho, K.; Shin, K.G. Viden: Attacker Identification on In-Vehicle Networks. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017.
- Sagong, S.U.; Ying, X.; Poovendran, R.; Bushnell, L. Exploring attack surfaces of voltage-based intrusion detection systems in controller area networks. ESCAR Eur. 2018, 2018, 1–13.
- Li, D.; Tian, M.; Jiang, R.; Yang, K. Exploiting Temperature-Varied Voltage Fingerprints for In-vehicle CAN Intrusion Detection. In Proceedings of the ACM Turing Award Celebration Conference-China (ACM TURC 2021), Hefei, China, 30 July–1 August 2021; pp. 116–120.
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the 2016 International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 63–68.
- Müter, M.; Asaj, N. Entropy-based anomaly detection for in-vehicle networks. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 1110–1115.
- Marchetti, M.; Stabili, D.; Guido, A.; Colajanni, M. Evaluation of anomaly detection for in-vehicle networks through information-theoretic algorithms. In Proceedings of the 2016 IEEE 2nd International Forum on Research and Technologies for Society and Industry Leveraging a better tomorrow (RTSI), Bologna, Italy, 7–9 September 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6.
- Wu, W.; Huang, Y.; Kurachi, R.; Zeng, G.; Xie, G.; Li, R.; Li, K. Sliding window optimized information entropy analysis method for intrusion detection on in-vehicle networks. IEEE Access 2018, 6, 45233–45245.
- Seo, E.; Song, H.M.; Kim, H.K. Gids: Gan based intrusion detection system for in-vehicle network. In Proceedings of the 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 28–30 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6.
- Longari, S.; Valcarcel, D.H.N.; Zago, M.; Carminati, M.; Zanero, S. CANnolo: An anomaly detection system based on LSTM autoencoders for controller area network. IEEE Trans. Netw. Serv. Manag. 2020, 18, 1913–1924.
- Amato, F.; Coppolino, L.; Mercaldo, F.; Moscato, F.; Nardone, R.; Santone, A. CAN-Bus Attack Detection With Deep Learning. IEEE Trans. Intell. Transp. Syst. 2021, 22, 5081–5090.
More
Information
Subjects:
Transportation Science & Technology
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
617
Revisions:
2 times
(View History)
Update Date:
19 Jan 2024
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No





