Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Alexios Mylonas | -- | 1607 | 2024-01-18 03:14:33 | | | |
| 2 | Rita Xu | Meta information modification | 1607 | 2024-01-18 03:38:57 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Ali, S.; Tan, S.C.; Lee, C.K.; Yusoff, Z.; Haque, M.R.; Mylonas, A.; Pitropakis, N. Attack-Aware Logical Link Assignment. Encyclopedia. Available online: https://encyclopedia.pub/entry/54001 (accessed on 07 February 2026).
Ali S, Tan SC, Lee CK, Yusoff Z, Haque MR, Mylonas A, et al. Attack-Aware Logical Link Assignment. Encyclopedia. Available at: https://encyclopedia.pub/entry/54001. Accessed February 07, 2026.
Ali, Sameer, Saw Chin Tan, Ching Kwang Lee, Zulfadzli Yusoff, Muhammad Reazul Haque, Alexios Mylonas, Nikolaos Pitropakis. "Attack-Aware Logical Link Assignment" Encyclopedia, https://encyclopedia.pub/entry/54001 (accessed February 07, 2026).
Ali, S., Tan, S.C., Lee, C.K., Yusoff, Z., Haque, M.R., Mylonas, A., & Pitropakis, N. (2024, January 18). Attack-Aware Logical Link Assignment. In Encyclopedia. https://encyclopedia.pub/entry/54001
Ali, Sameer, et al. "Attack-Aware Logical Link Assignment." Encyclopedia. Web. 18 January, 2024.
Copy Citation
Software-Defined Networking (SDN), which is used in Industrial Internet of Things, uses a controller as its “network brain” located at the control plane. This uniquely distinguishes it from the traditional networking paradigms because it provides a global view of the entire network. In SDN, the controller can become a single point of failure, which may cause the whole network service to be compromised.
internet of things
distributed denial of service
software-defined networks
1. Introduction
Software-Defined Networking (SDN) has been attracting attention in data centre network operators, academia, and industry for its programmability and agility. SDN empowers smart industries, such as Industrial Internet of Things, with central network device configuration and administration by providing a global view of the network. The SDN framework is regarded as the hardware-less networking paradigm in which networking through programming is possible. Compared to traditional networking, in SDN technology the control and data planes are decoupled, which make it more agile in terms of networking management. A controller is responsible for the management of the entire network, whereas networking switches are responsible for operating based on the instructions deployed through controllers [1]. One of the factors for network performance and scalability is how the network is being designed [2]. The SDN architecture is flexible and can be programmed using any high-level programming language to serve the purpose of the client devices and end-users [3]. The SDN platform is not only capable of providing high performance, but also providing energy efficiency and network security [4]. However, it is necessary to counter Distributed Denial of Service (DDoS) attacks by employing controller clustering methods to control the efficiency and performance from the view of entire network security [3][4]. Due to the central location of the controller, many security concerns caused by a single point of failure have been reported [5]. Firstly, the SDN control plane is unable to handle all the flow requests due to resource consumption or malicious traffic resulting from DDoS. Secondly, the fake flow request from switches can generate several unnecessary flow rules, which makes it difficult for the data plane to store flow rules for a normal flow of traffic [6][7].
The logical links in AALLA model are used to provide connectivity and restore the availability of resources when DDoS attacks happen. The AALLA model considers a link assignment technique and is capable of restoring the network service availability under a disruption of existing links. When a given switch is affected by a DDoS attack, the logical links will take up the switch using the backup links connecting another available port on the switch. This will restore or resume the disrupted service again to the requested users, ensuring service availability. The past literature has focused on the security of controller placement, the security of message transformation, bandwidth optimization, and network scalability [8][9][10][11][12][13][14][15][16][17][18][19]. However, the past literature has not focused on link assignment strategies considering bandwidth and cost optimization under single points of failure in SDN networks. AALLA considers metrics such as latency, throughput, cost optimization for links, switches, and controllers along with the high availability (HA) of network services in the SDN environment.
Security has been regarded as a detrimental factor in the development of SDN networks [20]. Among the security requirements of SDN networks, undisrupted availability is critical since the core function of SDN is to provide uninterrupted network services and resources. DDoS flooding attacks are the culprit in destroying availability in SDN networks [20][21]. DDoS attacks are created by two or more systems or botnets. A botnet is a compromised host system created when a computer is penetrated by software from a malware code [20]. It is essential to ensure SDN network availability for its end-users under DDoS flooding attacks. Current DDoS attacks have many forms, e.g., consumption of computational resources, disruption of configuration information, etc. [22]. To improve scalability and performance and avoid a single point of failure, the control plane is implemented as a distributed system with a cluster of controllers [23]. The hierarchy of controllers using controller clustering system is proposed as shown in Figure 1. More than one controller in SDN will serve as backup support controllers and also distribute the load of flow requests from switches.
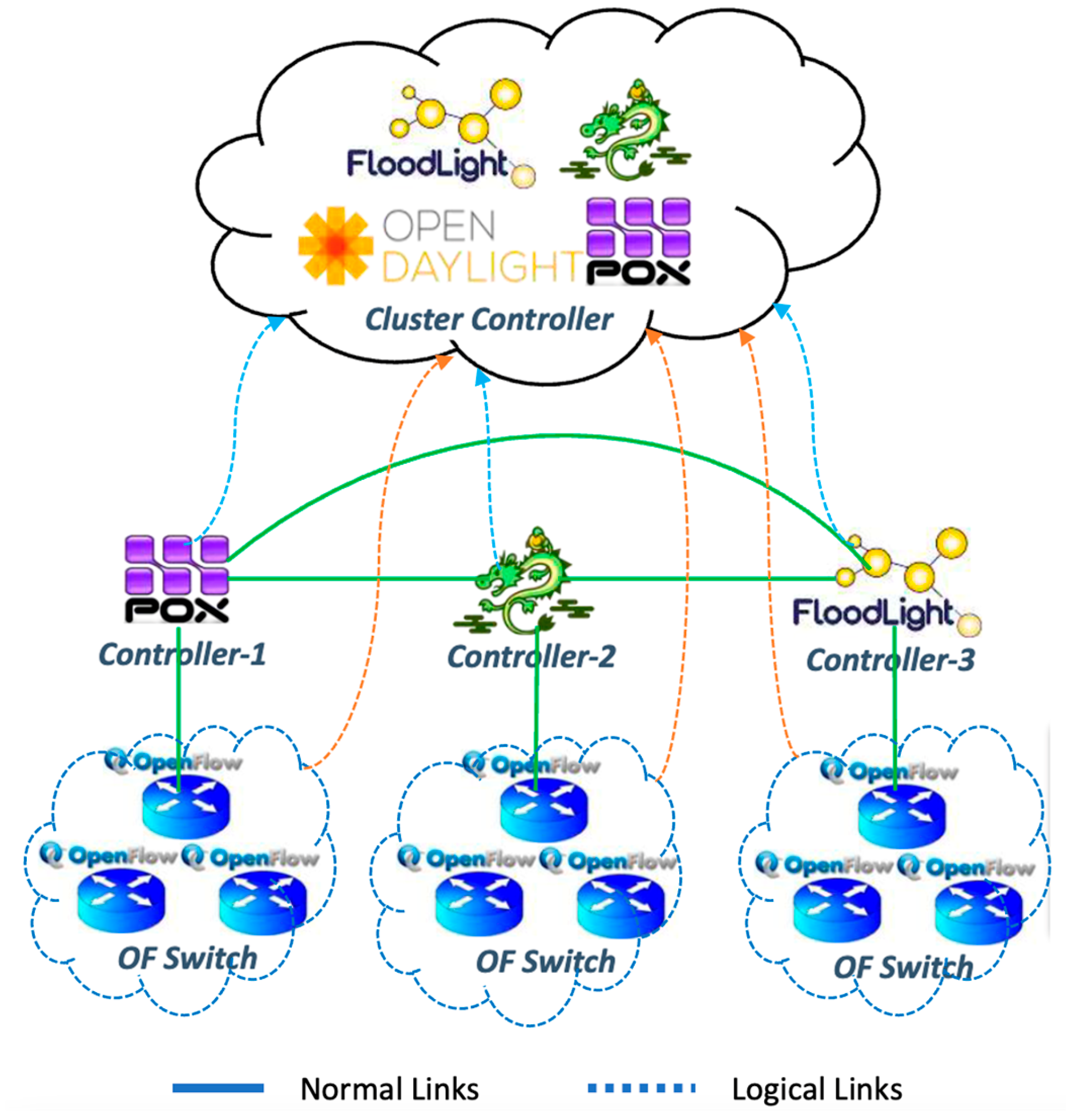
Figure 1. Controller cluster using logical link assignment in SDN network.
2. Attack-Aware Logical Link Assignment
The authors in [24] present a heuristic approach Pareto-based Optimal Controller (POCO), a mathematical model for small- and medium-sized networks that provides operators with Pareto optimal placements with respect to different performance metrics. The authors in [25][26][27] present an integer linear model that proposes Survivor, a controller placement strategy that considers path diversity, capacity, and failover mechanisms in network design. In [28][29], the authors proposed a mathematical model for the controller placement in SDN that determines the optimal number, location, and type of controllers. The goal of the model is to minimize the cost of the network while considering different constraints. The work in [30][31][32][33][34][35] introduces mixed-integer programming formulations for the optimal placement of multi-controller switches in virtualized Open Flow-enabled SDN networks. The authors in [36][37][38][39] address the deployment of multiple controllers that work cooperatively to control a network. The authors proposed a Dynamic Controller Provisioning Problem (DCPP). The DCPP dynamically adapts the number of controllers and their locations with changing network conditions in order to minimize flow setup time and communication overhead. They formulated this problem by using integer linear programming (ILP). So far, the research studies on SDN have been focusing on the controller placement problem, scalability issues, number of controllers and reliability metrics, etc.
The authors of [40][41][42][43][44] address how the centralized paradigm of SDN is a potential vulnerability to the system assuming attackers may launch DDoS attacks against the switches and controllers. The authors further reported that an attacker may create a large number of new flows within a short period of time [21], intending to overwhelm the controller and cause network failure for legitimate users. The authors in [45][46][47] discuss how DDoS attack vulnerabilities in Open Flow SDN networks involve overpowering computing or networking resources such that a switch is unable to forward packets as expected. The authors in [48][49][50][51] illustrate controller vulnerability to flooding attacks by injecting spoofed request packets continuously; attackers deliberately generate heavy traffic to the controller, causing huge bandwidth occupation in the controller–switch channel, subsequently overloading the flow table in switches. The final goal of attackers is to downgrade or even shutdown the stability and quality of service of the network. Furthermore, the authors introduce a feasible method to protect the network against DDoS attacks more effectively. The authors in [52][53][54][55][56] investigate how an SDN can be utilized to overcome difficulties and effectively block legitimate-looking DDoS attacks mounted by a larger number of bots. Specifically, they discuss a DDoS-blocking application that runs over the SDN controller while using the standard Open Flow interface.
In the work in [50][57][58][59][60], some of the authors proposed a novel clustered distributed controller architecture in a real setting of SDN. The distributed cluster implementation comprises multiple popular SDN controllers. The proposed mechanism is evaluated using a real-world network topology running on top of an emulated SDN environment. Their proposed architecture [61][62][63] is based on distributed controller clustering in SDN that consists of two different types of controllers: an open-source and a commercial-based controllers. Both types of controllers manage different SDN networks. Each controller is set up within a cluster of three nodes; the controllers in each cluster are configured in active mode with one of the controllers acting as the primary controller. The authors of [64][65][66][67] address cluster hierarchy and highlight that the implementation of a controller cluster is outside the scope of Open Flow specifications. Their research primarily focused on providing the distributed controllers in SDN and proposed the concept of hierarchy of controllers. However, the hierarchy of controllers and attack-aware logical link assignment needs to be examined to address to the single point of failure in SDN networks. The AALLA model will provide the logical link assignment from networking devices to the cluster (backup) controllers. This mechanism of controller clustering will address the single point of failure under DDoS attacks.
A trust mechanism designed to enhance security protection in SDN-based IoT networks is proposed in [12]. The authors proposed a method to evaluate the trust level of IoT devices based on their operational behaviours and characteristics, allowing the SDN controller to actively monitor and block abnormal devices. The study in [13] presents the DARFESS (Attack-Resilient Framework for Energy Security System), which uses software-defined networking to monitor and control the cyber infrastructure of power systems. Authors provide insights into the security landscape of SDN in [14], aiming to enhance the security posture of SDN deployments and address the evolving security challenges posed by the programmability and centralization of network control. Another study in [15] presents an optimized AI model that effectively detects and mitigates DDoS attacks in SDN environments, showcasing its superiority over traditional machine learning models. The work in [16] emphasizes the significance of a dynamic controller configuration in enhancing the security and resilience of SDN networks, particularly in SCADA systems, and provides insights into the implementation and effectiveness of this approach. The focus of [17] is on the security aspects of distributed SDN controllers in an enterprise SD-WLAN. The authors highlight the security, scalability, reliability, and consistency issues associated with this design.
Currently, research in SDN has been focusing on controller placement strategies, determining the number of controllers, the location for controller placement, and scaling SDN networks. However, failover techniques using attack-aware link assignment methods aiming to mitigate DDoS-based large volumetric attacks have not been investigated thoroughly in SDN, e.g., in [8][9][10][11][12][13][14][15][16][17][18][19]. This work focuses on tackling a single point of failure and studying the hierarchy of controllers in SDN and presents a novel mathematical model for logical link assignment from switches to the cluster (backup) controllers under DDoS attacks.
References
- Rawat, D.B.; Reddy, S.R. Software defined networking architecture, security and energy efficiency: A survey. IEEE Commun. Surv. Tutor. 2017, 19, 325–346.
- Shin, S.; Gu, G. Attacking software-defined networks: A first feasibility study. In Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking, Hong Kong, China, 16 August 2013; pp. 165–166.
- Cox, J.H.; Chung, J.; Donovan, S.; Ivey, J.; Clark, R.J.; Riley, G.; Owen, H.L. Advancing Software-Defined Networks: A Survey. IEEE Access 2017, 5, 25487–25526.
- Lange, S.; Gebert, S.; Zinner, T.; Tran-Gia, P.; Hock, D.; Jarschel, M.; Hoffmann, M. Heuristic approaches to the controller placement problem in large scale SDN networks. IEEE Trans. Netw. Serv. Manag. 2015, 12, 4–17.
- Yeganeh, S.; Ganjali, Y. Kandoo: A framework for efficient and scalable offloading of control applications. In Proceedings of the ACM SIGCOMM Hot Topics in Software Defined Networking (HotSDN), Helsinki, Finland, 13 August 2012.
- Casado, M. Scalability and reliability of logically centralized controller. In Proceedings of the Stanford CIO Summit, Stanford, CA, USA, 15 June 2010.
- Shu, Z.; Wan, J.; Li, D.; Lin, J.; Vasilakos, A.V.; Imran, M. Security in software-defined networking: Threats and countermeasures. Mob. Netw. Appl. 2016, 21, 764–776.
- Shohani, R.B.; Mostafavi, S.A. Introducing a new linear regression based method for early DDoS attack detection in SDN. In Proceedings of the 2020 6th International Conference on Web Research (ICWR), Tehran, Iran, 22–23 April 2020; pp. 126–132.
- Sufiev, H.; Haddad, Y. DCF: Dynamic cluster flow architecture for SDN control plane. In Proceedings of the 2017 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 8–10 January 2017; pp. 172–173.
- Bouzidi, E.H.; Outtagarts, A.; Langar, R.; Boutaba, R. Dynamic clustering of software defined network switches and controller placement using deep reinforcement learning. Comput. Netw. 2022, 207, 108852.
- Macedo, R.; de Castro, R.; Santos, A.; Ghamri-Doudane, Y.; Nogueira, M. Self-Organized SDN Controller Cluster Conformations Against DDoS Attacks Effects. In Proceedings of the Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6.
- Tsai, P.W.; Lee, C.W.; Wang, T.W. Design and Development of a Trust Mechanism to Enhance Security Protection on SDN-based IoT Network. In Proceedings of the 2023 24st Asia-Pacific Network Operations and Management Symposium (APNOMS), Detroit, MI, USA, 21–23 September 2023; pp. 125–130.
- Jin, D.; Qu, Y.; Liu, X.; Hannon, C.; Yan, J.; Aved, A.J.; Morrone, P. Dynamic Data-Driven Approach for Cyber-Resilient and Secure Critical Energy Systems. In Handbook of Dynamic Data Driven Applications Systems; Springer International Publishing: Cham, Switzerland, 2023; Volume 2, pp. 807–831.
- Bhuiyan, Z.A.; Islam, S.; Islam, M.M.; Ullah, A.A.; Naz, F.; Rahman, M.S. On the (in) Security of the Control Plane of SDN Architecture: A Survey. IEEE Access 2023, 11, 91550–91582.
- Al-Dunainawi, Y.; Al-Kaseem, B.R.; Al-Raweshidy, H.S. Optimized Artificial Intelligence Model for DDoS Detection in SDN Environment. IEEE Access 2023, 11, 106733–106748.
- DeLany, R.; Smith, A.; Li, Y.; Du, L. SDN Dynamic Controller Configuration to Mitigate Compromised Controllers. In Proceedings of the 2023 IEEE Transportation Electrification Conference & Expo (ITEC), Detroit, MI, USA, 21–23 June 2023; pp. 1–5.
- Shaji, N.S.; Muthalagu, R. Survey on security aspects of distributed software-defined networking controllers in an enterprise SD-WLAN. Digit. Commun. Netw. 2023.
- Lemeshko, O.; Yeremenko, O.; Mersni, A.; Gazda, J. Improvement of Confidential Messages Secure Routing over Paths with Intersection in Cyber Resilient Networks. In Proceedings of the 2022 XXVIII International Conference on Information, Communication and Automation Technologies (ICAT), Sarajevo, Bosnia and Herzegovina, 16–18 June 2022; pp. 1–6.
- Lemeshko, O.; Yeremenko, O.; Yevdokymenko, M.; Shapovalova, A.; Baranovskyi, O. Complex investigation of the compromise probability behavior in traffic engineering oriented secure routing model in software-defined networks. In Future Intent-Based Networking: On the QoS Robust and Energy Efficient Heterogeneous Software Defined Networks; Springer International Publishing: Cham, Switzerland, 2021; pp. 145–160.
- Yan, Q.; Yu, F.R.; Gong, Q.; Li, J. Software-defined networking (SDN) and distributed denial of service (DDoS) attacks in cloud computing environments: A survey, some research issues, and challenges. IEEE Commun. Surv. Tutor. 2016, 18, 602–622.
- Mallikarjunan, K.N.; Muthupriya, K.; Shalinie, S.M. A survey of distributed denial of service attack. In Proceedings of the 2016 10th International Conference on Intelligent Systems and Control (ISCO), Coimbatore, India, 7–8 January 2016; pp. 1–6.
- Xu, Y.; Liu, Y. DDoS attack detection under SDN context. In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9.
- Wang, T.; Liu, F.; Guo, J.; Xu, H. Dynamic sdn controller assignment in data center networks: Stable matching with transfers. In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; pp. 1–9.
- Dvir, A.; Haddad, Y.; Zilberman, A. The controller placement problem for wireless SDN. Wirel. Netw. 2019, 25, 4963–4978.
- Müller, L.F.; Oliveira, R.R.; Luizelli, M.C.; Gaspary, L.P.; Barcellos, M.P. Survivor: An enhanced controller placement strategy for improving SDN survivability. In Proceedings of the Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 1909–1915.
- Muqaddas, A.S.; Bianco, A.; Giaccone, P.; Maier, G. Inter-controller traffic in ONOS clusters for SDN networks. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6.
- Luo, M.; Li, Q.; Bo, M.; Lin, K.; Wu, X.; Li, C.; Lu, S.; Chou, W. Design and implementation of a scalable sdn-of controller cluster. In Proceedings of the INFOCOMP 2015, Brussels, Belgium, 21–26 June 2015; p. 55.
- Sallahi, A.; St-Hilaire, M. Optimal model for the controller placement problem in software defined networks. IEEE Commun. Lett. 2015, 19, 30–33.
- Zilberman, A.; Haddad, Y.; Erlich, S.; Peretz, Y.; Dvir, A. SDN Wireless Controller Placement Problem—The 4G LTE-U Case. IEEE Access 2021, 9, 16225–16238.
- Blenk, A.; Basta, A.; Zerwas, J.; Reisslein, M.; Kellerer, W. Control plane latency with sdn network hypervisors: The cost of virtualization. IEEE Trans. Netw. Serv. Manag. 2016, 13, 366–380.
- Karakus, M.; Durresi, A. A survey: Control plane scalability issues and approaches in Software-Defined Networking (SDN). Comput. Netw. 2017, 112, 279–293.
- Wang, G.; Zhao, Y.; Huang, J.; Wang, W. The controller placement problem in software defined networking: A survey. IEEE Netw. 2017, 31, 21–27.
- Samir, M.; Azab, M.; Samir, E. SD-CPC: SDN Controller Placement Camouflage based on Stochastic Game for Moving-target Defense. Comput. Commun. 2021, 168, 75–92.
- Hu, Y.; Wendong, W.; Gong, X.; Que, X.; Shiduan, C. Reliability-aware controller placement for software-defined networks. In Proceedings of the 2013 IFIP/IEEE International Symposium on Integrated Network Management (IM 2013), Ghent, Belgium, 27–31 May 2013; pp. 672–675.
- Li, X.; Tang, F.; Fu, L.; Yu, J.; Chen, L.; Liu, J.; Zhu, Y.; Yang, L.T. Optimized controller provisioning in software-defined LEO satellite networks. IEEE Trans. Mob. Comput. 2022, 22, 4850–4864.
- Bari, M.F.; Roy, A.R.; Chowdhury, S.R.; Zhang, Q.; Zhani, M.F.; Ahmed, R.; Boutaba, R. Dynamic controller provisioning in software defined networks. In Proceedings of the 2013 9th International Conference on Network and Service Management (CNSM), Zurich, Switzerland, 14–18 October 2013; pp. 18–25.
- Han, Z.; Xu, C.; Xiong, Z.; Zhao, G.; Yu, S. On-Demand Dynamic Controller Placement in Software Defined Satellite-Terrestrial Networking. IEEE Trans. Netw. Serv. Manag. 2021, 18, 2915–2928.
- Das, T.; Gurusamy, M. Controller placement for resilient network state synchronization in multi-controller sdn. IEEE Commun. Lett. 2020, 24, 1299–1303.
- Heller, B.; Sherwood, R.; McKeown, N. The controller placement problem. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks, Helsinki, Finland, 13 August 2012; pp. 7–12.
- Wei, L.; Fung, C. FlowRanger: A request prioritizing algorithm for controller DoS attacks in software defined networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 5254–5259.
- Balarezo, J.F.; Wang, S.; Chavez, K.G.; Al-Hourani, A.; Kandeepan, S. A survey on DoS/DDoS attacks mathematical modelling for traditional, SDN and virtual networks. Eng. Sci. Technol. Int. J. 2022, 31, 101065.
- Scaranti, G.F.; Carvalho, L.F.; Barbon, S.; Proença, M.L. Artificial Immune Systems and Fuzzy Logic to Detect Flooding Attacks in Software-Defined Networks. IEEE Access 2020, 8, 100172–100184.
- Ali, T.E.; Chong, Y.W.; Manickam, S. Machine Learning Techniques to Detect a DDoS Attack in SDN: A Systematic Review. Appl. Sci. 2023, 13, 3183.
- Aladaileh, M.A.; Anbar, M.; Hasbullah, I.H.; Chong, Y.W.; Sanjalawe, Y.K. Detection Techniques of Distributed Denial of Service Attacks on Software-Defined Networking Controller—A Review. IEEE Access 2020, 8, 143985–143995.
- Kandoi, R.; Antikainen, M. Denial-of-service attacks in OpenFlow SDN networks. In Proceedings of the 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM), Ottawa, ON, Canada, 11–15 May 2015; pp. 1322–1326.
- Yan, Q.; Yu, F.R. Distributed denial of service attacks in software-defined networking with cloud computing. IEEE Commun. Mag. 2015, 53, 52–59.
- Yonghong, F.; Jun, B.; Jianping, W.; Ze, C.; Ke, W.; Min, L. A dormant multi-controller model for software defined networking. China Commun. 2014, 11, 45–55.
- Dao, N.N.; Park, J.; Park, M.; Cho, S. A feasible method to combat against DDoS attack in SDN network. In Proceedings of the 2015 International Conference on Information Networking (ICOIN), Siem Reap, Cambodia, 12–14 January 2015; pp. 309–311.
- Saxena, U.; Sodhi, J.S.; Singh, Y. An Analysis of DDoS Attacks in a Smart Home Networks. In Proceedings of the 2020 10th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 29–31 January 2020; pp. 272–276.
- Erhan, D.; Anarım, E.; Kurt, G.K. DDoS attack detection using matching pursuit algorithm. In Proceedings of the 2016 24th Signal Processing and Communication Application Conference (SIU), Zonguldak, Turkey, 16–19 May 2016; pp. 1081–1084.
- Huang, K.; Yang, L.X.; Yang, X.; Xiang, Y.; Tang, Y.Y. A low-cost distributed denial-of-service attack architecture. IEEE Access 2020, 8, 42111–42119.
- Lim, S.; Ha, J.; Kim, H.; Kim, Y.; Yang, S. A SDN-oriented DDoS blocking scheme for botnet-based attacks. In Proceedings of the 2014 Sixth International Conference on Ubiquitous and Future Networks (ICUFN), Shanghai, China, 8–11 July 2014; pp. 63–68.
- Wang, B.; Zheng, Y.; Lou, W.; Hou, Y.T. DDoS attack protection in the era of cloud computing and software-defined networking. Comput. Netw. 2015, 81, 308–319.
- Wang, H.; Xu, L.; Gu, G. Floodguard: A dos attack prevention extension in software-defined networks. In Proceedings of the 2015 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Rio de Janeiro, Brazil, 22–25 June 2015; pp. 239–250.
- Haider, S.; Akhunzada, A.; Mustafa, I.; Patel, T.B.; Fernandez, A.; Choo, K.K.R.; Iqbal, J. A deep cnn ensemble framework for efficient ddos attack detection in software defined networks. IEEE Access 2020, 8, 53972–53983.
- Pérez-Díaz, J.A.; Valdovinos, I.A.; Choo, K.K.R.; Zhu, D. A flexible SDN-based architecture for identifying and mitigating low-rate DDoS attacks using machine learning. IEEE Access 2020, 8, 155859–155872.
- Abdelaziz, A.; Fong, A.T.; Gani, A.; Garba, U.; Khan, S.; Akhunzada, A.; Talebian, H.; Choo, K.K.R. Distributed controller clustering in software defined networks. PLoS ONE 2017, 12, e0174715.
- Wang, S.; Balarezo, J.F.; Chavez, K.G.; Al-Hourani, A.; Kandeepan, S.; Asghar, M.R.; Russello, G. Detecting flooding DDoS attacks in software defined networks using supervised learning techniques. Eng. Sci. Technol. Int. J. 2022, 35, 101176.
- Singh, M.P.; Bhandari, A. New-flow based DDoS attacks in SDN: Taxonomy, rationales, and research challenges. Comput. Commun. 2020, 154, 509–527.
- Li, J.; Tu, T.; Li, Y.; Qin, S.; Shi, Y.; Wen, Q. DoSGuard: Mitigating denial-of-service attacks in software-defined networks. Sensors 2022, 22, 1061.
- Gurusamy, U.; Hariharan, K.; Manikandan, M.S.K. Path optimization of box-covering based routing to minimize average packet delay in software defined network. Peer-to-Peer Netw. Appl. 2020, 13, 932–939.
- Wang, X.; Yang, Y.; Liu, H.; Ren, J.; Xu, S.; Wang, S.; Yu, S. Efficient measurement of round-trip link delays in software-defined networks. J. Netw. Comput. Appl. 2020, 150, 102468.
- Parashar, M.; Poonia, A.; Satish, K. A Survey of Attacks and their Mitigations in Software Defined Networks. In Proceedings of the 2019 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kanpur, India, 6–8 July 2019; pp. 1–8.
- Goransson, P.; Black, C.; Culver, T. Software Defined Networks: A Comprehensive Approach; Morgan Kaufmann: Burlington, MA, USA, 2016.
- Ros, F.J.; Ruiz, P.M. On reliable controller placements in software-defined networks. Comput. Commun. 2016, 77, 41–51.
- Rasol, K.A.R.; Domingo-Pascual, J. Joint Latency and Reliability-Aware Controller Placement. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Republic of Korea, 13–16 January 2021; pp. 197–202.
- Hock, D.; Hartmann, M.; Gebert, S.; Jarschel, M.; Zinner, T.; Tran-Gia, P. Pareto-optimal resilient controller placement in SDN-based core networks. In Proceedings of the 2013 25th International Teletraffic Congress (ITC), Shanghai, China, 10–12 September 2013; pp. 1–9.
More
Information
Subjects:
Computer Science, Software Engineering
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
514
Revisions:
2 times
(View History)
Update Date:
18 Jan 2024
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




