Software-Defined Networking (SDN), which is used in Industrial Internet of Things, uses a controller as its “network brain” located at the control plane. This uniquely distinguishes it from the traditional networking paradigms because it provides a global view of the entire network. In SDN, the controller can become a single point of failure, which may cause the whole network service to be compromised.
1. Introduction
Software-Defined Networking (SDN) has been attracting attention in data centre network operators, academia, and industry for its programmability and agility. SDN empowers smart industries, such as Industrial Internet of Things, with central network device configuration and administration by providing a global view of the network. The SDN framework is regarded as the hardware-less networking paradigm in which networking through programming is possible. Compared to traditional networking, in SDN technology the control and data planes are decoupled, which make it more agile in terms of networking management. A controller is responsible for the management of the entire network, whereas networking switches are responsible for operating based on the instructions deployed through controllers
[1]. One of the factors for network performance and scalability is how the network is being designed
[2]. The SDN architecture is flexible and can be programmed using any high-level programming language to serve the purpose of the client devices and end-users
[3]. The SDN platform is not only capable of providing high performance, but also providing energy efficiency and network security
[4]. However, it is necessary to counter Distributed Denial of Service (DDoS) attacks by employing controller clustering methods to control the efficiency and performance from the view of entire network security
[3][4][3,4]. Due to the central location of the controller, many security concerns caused by a single point of failure have been reported
[5]. Firstly, the SDN control plane is unable to handle all the flow requests due to resource consumption or malicious traffic resulting from DDoS. Secondly, the fake flow request from switches can generate several unnecessary flow rules, which makes it difficult for the data plane to store flow rules for a normal flow of traffic
[6][7][6,7].
The logical links in AALLA model are used to provide connectivity and restore the availability of resources when DDoS attacks happen. The AALLA model considers a link assignment technique and is capable of restoring the network service availability under a disruption of existing links. When a given switch is affected by a DDoS attack, the logical links will take up the switch using the backup links connecting another available port on the switch. This will restore or resume the disrupted service again to the requested users, ensuring service availability. The past literature has focused on the security of controller placement, the security of message transformation, bandwidth optimization, and network scalability
[8][9][10][11][12][13][14][15][16][17][18][19][8,9,10,11,12,13,14,15,16,17,18,19]. However, the past literature has not focused on link assignment strategies considering bandwidth and cost optimization under single points of failure in SDN networks. AALLA considers metrics such as latency, throughput, cost optimization for links, switches, and controllers along with the high availability (HA) of network services in the SDN environment.
Security has been regarded as a detrimental factor in the development of SDN networks
[20]. Among the security requirements of SDN networks, undisrupted availability is critical since the core function of SDN is to provide uninterrupted network services and resources. DDoS flooding attacks are the culprit in destroying availability in SDN networks
[20][21][20,21]. DDoS attacks are created by two or more systems or botnets. A botnet is a compromised host system created when a computer is penetrated by software from a malware code
[20]. It is essential to ensure SDN network availability for its end-users under DDoS flooding attacks. Current DDoS attacks have many forms, e.g., consumption of computational resources, disruption of configuration information, etc.
[22]. To improve scalability and performance and avoid a single point of failure, the control plane is implemented as a distributed system with a cluster of controllers
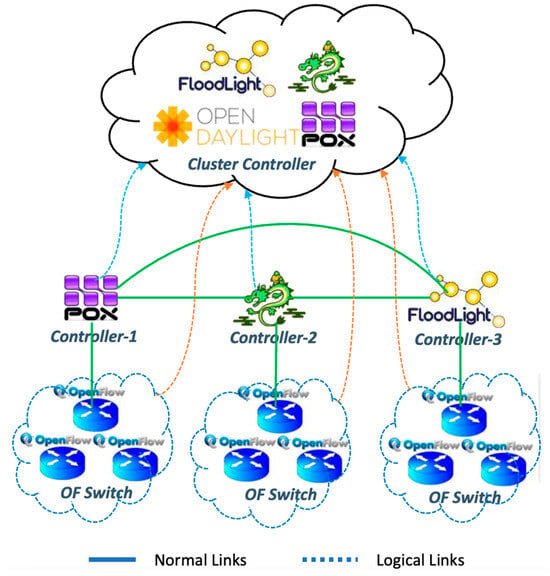
[23]. The hierarchy of controllers using controller clustering system is proposed as shown in
Figure 1. More than one controller in SDN will serve as backup support controllers and also distribute the load of flow requests from switches.
Figure 1. Controller cluster using logical link assignment in SDN network.
2. Attack-Aware Logical Link Assignment
The authors in
[24] present a heuristic approach Pareto-based Optimal Controller (POCO), a mathematical model for small- and medium-sized networks that provides operators with Pareto optimal placements with respect to different performance metrics. The authors in
[25][26][27][25,26,27] present an integer linear model that proposes Survivor, a controller placement strategy that considers path diversity, capacity, and failover mechanisms in network design. In
[28][29][28,29], the authors proposed a mathematical model for the controller placement in SDN that determines the optimal number, location, and type of controllers. The goal of the model is to minimize the cost of the network while considering different constraints. The work in
[30][31][32][33][34][35][30,31,32,33,34,35] introduces mixed-integer programming formulations for the optimal placement of multi-controller switches in virtualized Open Flow-enabled SDN networks. The authors in
[36][37][38][39][36,37,38,39] address the deployment of multiple controllers that work cooperatively to control a network. The authors proposed a Dynamic Controller Provisioning Problem (DCPP). The DCPP dynamically adapts the number of controllers and their locations with changing network conditions in order to minimize flow setup time and communication overhead. They formulated this problem by using integer linear programming (ILP). So far, the research studies on SDN have been focusing on the controller placement problem, scalability issues, number of controllers and reliability metrics, etc.
The authors of
[40][41][42][43][44][40,41,42,43,44] address how the centralized paradigm of SDN is a potential vulnerability to the system assuming attackers may launch DDoS attacks against the switches and controllers. The authors further reported that an attacker may create a large number of new flows within a short period of time
[21], intending to overwhelm the controller and cause network failure for legitimate users. The authors in
[45][46][47][45,46,47] discuss how DDoS attack vulnerabilities in Open Flow SDN networks involve overpowering computing or networking resources such that a switch is unable to forward packets as expected. The authors in
[48][49][50][51][48,49,50,51] illustrate controller vulnerability to flooding attacks by injecting spoofed request packets continuously; attackers deliberately generate heavy traffic to the controller, causing huge bandwidth occupation in the controller–switch channel, subsequently overloading the flow table in switches. The final goal of attackers is to downgrade or even shutdown the stability and quality of service of the network. Furthermore, the authors introduce a feasible method to protect the network against DDoS attacks more effectively. The authors in
[52][53][54][55][56][52,53,54,55,56] investigate how an SDN can be utilized to overcome difficulties and effectively block legitimate-looking DDoS attacks mounted by a larger number of bots. Specifically, they discuss a DDoS-blocking application that runs over the SDN controller while using the standard Open Flow interface.
In the work in
[50][57][58][59][60][50,57,58,59,60], some of the authors proposed a novel clustered distributed controller architecture in a real setting of SDN. The distributed cluster implementation comprises multiple popular SDN controllers. The proposed mechanism is evaluated using a real-world network topology running on top of an emulated SDN environment. Their proposed architecture
[61][62][63][61,62,63] is based on distributed controller clustering in SDN that consists of two different types of controllers: an open-source and a commercial-based controllers. Both types of controllers manage different SDN networks. Each controller is set up within a cluster of three nodes; the controllers in each cluster are configured in active mode with one of the controllers acting as the primary controller. The authors of
[64][65][66][67][64,65,66,67] address cluster hierarchy and highlight that the implementation of a controller cluster is outside the scope of Open Flow specifications. Their research primarily focused on providing the distributed controllers in SDN and proposed the concept of hierarchy of controllers. However, the hierarchy of controllers and attack-aware logical link assignment needs to be examined to address to the single point of failure in SDN networks. The AALLA model will provide the logical link assignment from networking devices to the cluster (backup) controllers. This mechanism of controller clustering will address the single point of failure under DDoS attacks.
A trust mechanism designed to enhance security protection in SDN-based IoT networks is proposed in
[12]. The authors proposed a method to evaluate the trust level of IoT devices based on their operational behaviours and characteristics, allowing the SDN controller to actively monitor and block abnormal devices. The study in
[13] presents the DARFESS (Attack-Resilient Framework for Energy Security System), which uses software-defined networking to monitor and control the cyber infrastructure of power systems. Authors provide insights into the security landscape of SDN in
[14], aiming to enhance the security posture of SDN deployments and address the evolving security challenges posed by the programmability and centralization of network control. Another study in
[15] presents an optimized AI model that effectively detects and mitigates DDoS attacks in SDN environments, showcasing its superiority over traditional machine learning models. The work in
[16] emphasizes the significance of a dynamic controller configuration in enhancing the security and resilience of SDN networks, particularly in SCADA systems, and provides insights into the implementation and effectiveness of this approach. The focus of
[17] is on the security aspects of distributed SDN controllers in an enterprise SD-WLAN. The authors highlight the security, scalability, reliability, and consistency issues associated with this design.
Currently, research in SDN has been focusing on controller placement strategies, determining the number of controllers, the location for controller placement, and scaling SDN networks. However, failover techniques using attack-aware link assignment methods aiming to mitigate DDoS-based large volumetric attacks have not been investigated thoroughly in SDN, e.g., in
[8][9][10][11][12][13][14][15][16][17][18][19][8,9,10,11,12,13,14,15,16,17,18,19]. This work focuses on tackling a single point of failure and studying the hierarchy of controllers in SDN and presents a novel mathematical model for logical link assignment from switches to the cluster (backup) controllers under DDoS attacks.