Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Ahmed Alhusayni | -- | 3029 | 2023-09-27 18:13:47 | | | |
| 2 | Catherine Yang | Meta information modification | 3029 | 2023-09-28 02:44:24 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Alghamdi, S.; Albeshri, A.; Alhusayni, A. IoT Environment Using a Blockchain-Based Local-Global Consensus Manager. Encyclopedia. Available online: https://encyclopedia.pub/entry/49733 (accessed on 02 March 2026).
Alghamdi S, Albeshri A, Alhusayni A. IoT Environment Using a Blockchain-Based Local-Global Consensus Manager. Encyclopedia. Available at: https://encyclopedia.pub/entry/49733. Accessed March 02, 2026.
Alghamdi, Saleh, Aiiad Albeshri, Ahmed Alhusayni. "IoT Environment Using a Blockchain-Based Local-Global Consensus Manager" Encyclopedia, https://encyclopedia.pub/entry/49733 (accessed March 02, 2026).
Alghamdi, S., Albeshri, A., & Alhusayni, A. (2023, September 27). IoT Environment Using a Blockchain-Based Local-Global Consensus Manager. In Encyclopedia. https://encyclopedia.pub/entry/49733
Alghamdi, Saleh, et al. "IoT Environment Using a Blockchain-Based Local-Global Consensus Manager." Encyclopedia. Web. 27 September, 2023.
Copy Citation
The Internet of Things (IoT) refers to the network of interconnected devices that can communicate and share data over the Internet. The widespread adoption of smart devices within Internet of Things (IoT) networks poses considerable security challenges for their communication. To address these issues, blockchain technology, known for its decentralized and distributed nature, offers potential solutions within consensus-based authentication in IoT networks.
blockchain
Internet of Things
clustering
1. Introduction
The term “Internet of Things” (IoT) describes a scenario in which a wide variety of gadgets, automobiles, appliances, and other things are linked together and equipped with applications, sensors, and network connections [1]. Through the use of the internet, these gadgets may share information with one another and with centralized databases. The IoT environment enables these devices to communicate, interact, and share information, leading to increased automation, efficiency, and connectivity in various domains. The IoT environment typically involves a combination of hardware, software, and network infrastructure. It includes devices such as sensors, actuators, gateways, embedded systems, communication protocols, cloud computing platforms, and data analytics tools. These components work together to enable seamless communication, data exchange, and interoperability among different devices and systems [2].
A distributed IoT environment refers to an Internet of Things (IoT) system where the network and computing resources are decentralized and distributed across multiple locations or devices. In this environment, the IoT infrastructure does not rely on a central system or cloud-based platform for data processing and decision-making. Instead, the intelligence and processing capabilities are distributed among the devices themselves or within localized edge computing nodes. In a distributed IoT environment, devices at the network’s edge (e.g., sensors, actuators, and gateways) are equipped with processing power and storage capabilities. These devices can perform data collection, preprocessing, analysis, and even decision-making tasks locally without relying heavily on cloud resources. This approach offers several advantages, including reduced latency, improved reliability, enhanced privacy and security, and efficient bandwidth utilization [3].
There are too many issues with the distributed IoT environment, such as connectivity, data management, privacy, and security, of which securing a distributed IoT environment is the most challenging due to the decentralized nature of the system. Ensuring the identity and trustworthiness of devices within a distributed IoT environment is crucial [4]. Device authentication mechanisms, such as certificates or cryptographic keys, need to be implemented to verify the identity of devices and prevent unauthorized access. Addressing these issues requires a comprehensive security strategy that encompasses device-level security, secure communication protocols, access control mechanisms, and ongoing monitoring and updates. Following industry best practices and standards is crucial to building a secure and resilient distributed IoT environment.
In recent years, it has been observed that blockchain technology and consensus protocols can play a significant role in securing IoT environments due to their immutable and tamper-resistant data. Blockchain provides a decentralized and distributed ledger that can store IoT data in a transparent and immutable manner. By storing data in blocks linked using cryptographic hashes, the integrity and immutability of the data can be ensured [5]. This helps prevent data tampering and unauthorized modifications. Consensus protocols, such as Proof of Work (PoW) or Proof of Stake (PoS), ensure agreement and trust in a blockchain network. These protocols enable nodes in the network to reach a consensus on the validity of transactions and the state of the blockchain. By employing consensus mechanisms, IoT environments can ensure data integrity and prevent malicious activities [6].
When used in the IoT, blockchain technology helps solve the problem of centralization while also allowing for the safe flow of data across IoT nodes, even in untrusted situations. Nevertheless, most existing blockchain consensus algorithms are too computationally intensive and cannot be scaled to meet the ever-increasing demands for efficiency and responsiveness in IoT devices. Additionally, IoT nodes may be attacked in several different ways. Hence, developing a reliable reputation evaluation scheme is important in establishing a secure and trustworthy IoT ecosystem for specific applications [7][8][9].
2. Internet of Things (IoT)
“Internet of Things” refers to the interconnection of “smart” devices, which can include both mechanical and digital machinery, items, and people and are capable of exchanging data over a network without the participation of a human. Figure 1 shows the typical IoT system. On a more macro scale, IoT applications include things like smart cities, smart homes, and smart healthcare systems, among others. The following are some of the most important parts [10] of the Internet of Things ecosystem:
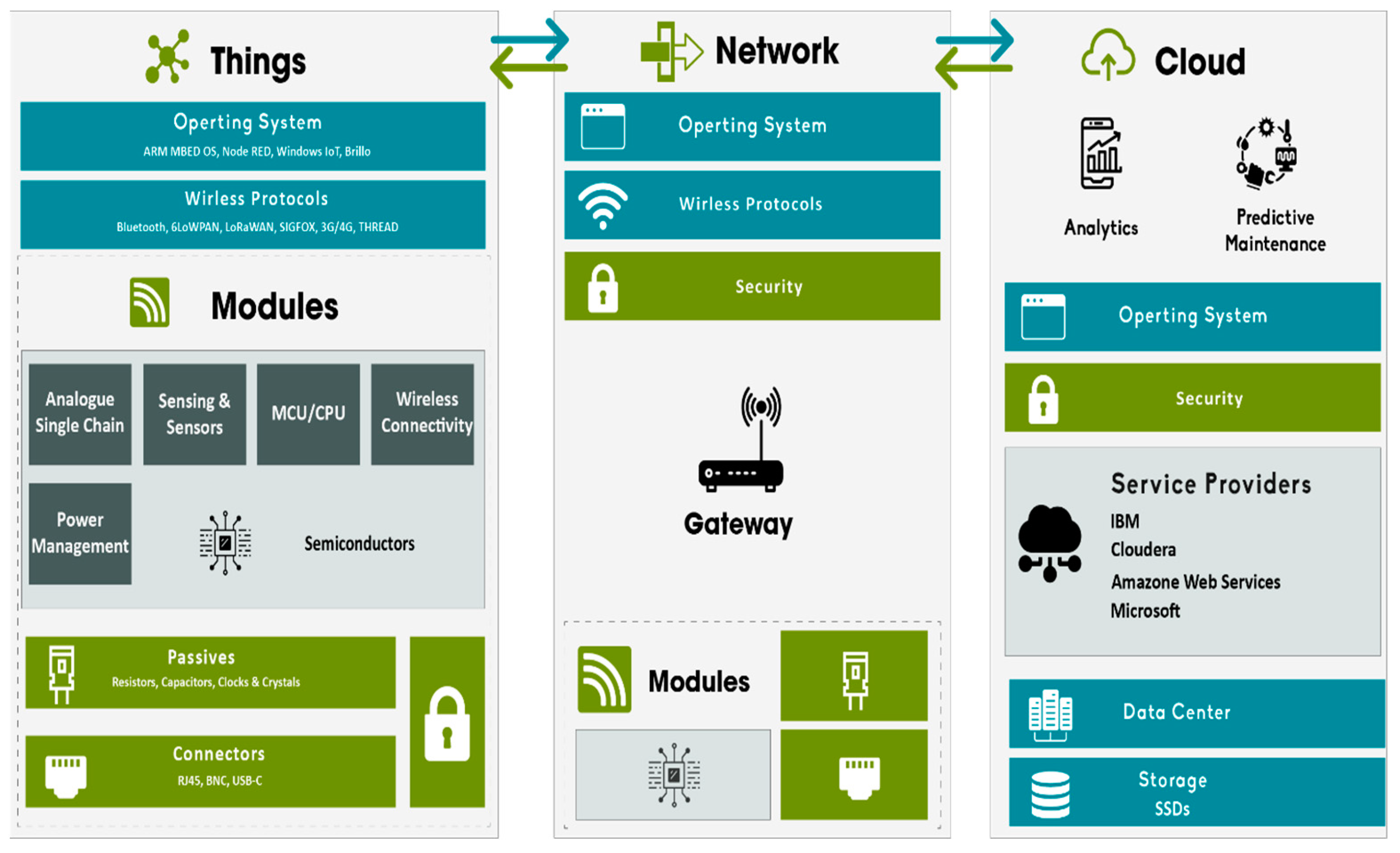
Figure 1. The typical IOT architecture, adopted from [1].
-
Sensors and Smart Devices: These are the physical things outfitted with sensors, actuators, and connections. Smartphones, wearables, smart home gadgets (thermostats, lighting, security cameras), industrial sensors, and even cars are some of the examples;
-
Connection: To connect to the internet or local networks, IoT devices use a variety of communication protocols. Some examples are Wi-Fi, Bluetooth, cellular networks (3G, 4G, or 5G), Zigbee, Z-Wave, and LoRaWAN;
-
Processing and Analysis: IoT devices use internal sensors to gather data about their surroundings. This data’s processing and analysis occur locally on the device or in the cloud. It is possible to use advanced analytics and machine learning techniques to glean insightful information from the gathered data;
-
Storage: The cloud is essential to IoT systems because it offers scalability, processing power, and storage. IoT devices frequently upload their data to the cloud for analysis and storage. Additionally, remote device management, firmware updates, and connections with other programs and services are all made possible by cloud platforms.
3. Security Issues in IoT
The wide-ranging diversity among IoT devices and their limited security visibility give rise to significant concerns regarding trust and security [11]. The absence of standardized trust mechanisms and essential security standards, combined with the scarcity and inadequate management of firmware updates for IoT devices, creates security vulnerabilities that attract malicious actors. Additionally, the IoT ecosystem lacks transparent identification and privacy solutions that grant individuals control over the identity data of their devices. Furthermore, there is a lack of security training and protocol implementation for both individuals and devices, along with ineffective information sharing with CERTs/CSIRTs (Computer Emergency Response Teams/Computer Security Incident Response Teams).
In theory, current blockchain solutions hold promise for bolstering the security and trustworthiness of IoT networks. However, practical restrictions, such as the extra processing resources needed owing to sophisticated encryption, limit their usefulness and provide issues that may be solved by improving certain blockchain network components.
4. The Blockchain Technology
Blockchain technology was first developed and used by a well-known cryptocurrency, Bitcoin, in 2008 [12]. It is a peer-to-peer network-based decentralized ledger technology. The usual blockchain paradigm is seen in Figure 2. Under this model, each node in the blockchain network keeps its copy of the ledger up-to-date. The blockchain primarily relied on cryptocurrencies to detect and handle the double-spending problem. IoT networks are only one of the many new areas where blockchain technology is being explored for its potential to secure and centrally record digital transactions.

Figure 2. The blockchain architecture.
The ledger of a blockchain is composed of blocks, with each block consisting of two components. The first component represents the transaction, which needs to be stored in a database, and it can take various forms, such as a patient record, network traffic log, and commodity transaction, among others. On the other hand, the second component contains header information, including the hash of the current transaction, the combined previous hash, and a timestamp.
Thus, storage in this manner results in a linked chain block with a sequence, as shown in Figure 3. A new transaction will also first contribute to a specific block if it begins. Second, following previously established standards, miners confirm the block contains the transaction. A group of miners uses a consensus technique to validate the transactions after verification. After successful validation, the confirmed transaction is prepared to be added to the blockchain ledger.
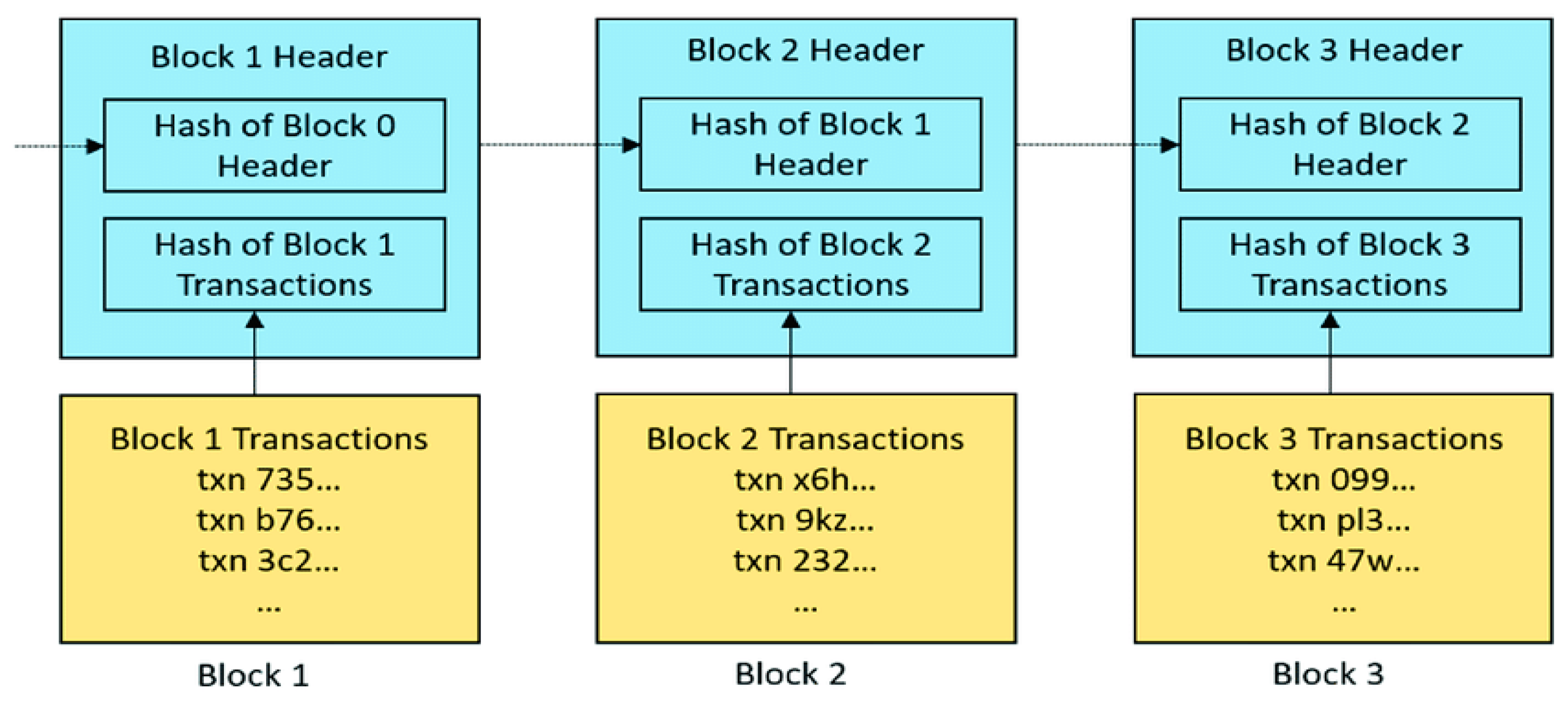
Figure 3. Block inter-links mechanism in blockchain.
5. Consensus Algorithms
In the realm of blockchain systems, a consensus mechanism refers to a program designed to foster widespread agreement on the current state of a ledger. The schematic diagram of the blockchain architecture is shown in Figure 4. In contrast, Table 1 presents the standard consensus algorithms that are most suitable for networks with many users and operations. The utilization of consensus mechanisms brings about numerous advantages for distributed ledgers, blockchains, and cryptocurrencies, as they can effectively replace the relatively slow processes of human auditors and verifiers. True decentralization and security are achieved in the two variations of consensus algorithms, namely public and permissionless blockchains. However, the need to ensure both privacy and security in their consensus processes results in the consumption of significant resources, leading to scalability challenges. Proof of Work (PoW) and Proof of Stake (PoS) are prime examples of such algorithms. Conversely, private and permissioned blockchains opt to sacrifice a portion of their decentralization, but they can still offer scalability, portability, and safety.
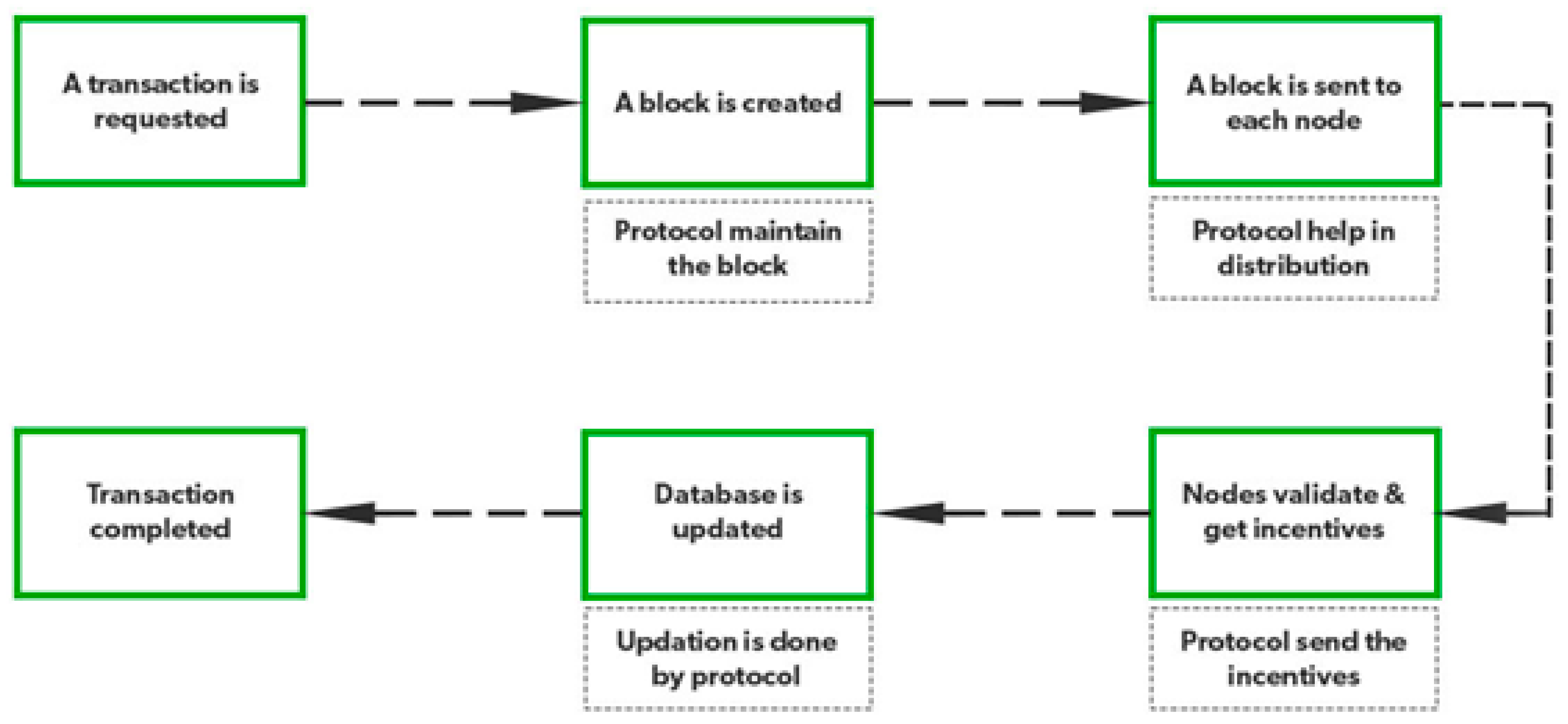
Figure 4. The blockchain protocol architecture.
Table 1. Existing consensus algorithms [13].
| Reference | Merits | Demerits |
|---|---|---|
| Proof of Work (PoW) | More Secure Provides decentralized power and control |
Required more power and electricity Fail to cover a wide area network |
| Proof of Stake (PoS) | Energy efficient Fast processing Mechanism |
Less decentralization as compared to PoW Low Security |
| Delegated Proof of Stake | Faster in processing as compared to PoW and PoS Less expensive Low hardware requirements |
Less resilience because of the decentralization strategy More suspects able to attack |
| Transaction as Proof of Stake (TPoS) | More secure due to the combined contribution of all nodes Easy adaptable algorithms |
Speed degradation due to the combined contribution of nodes. Failed against short fork in the blockchain |
| Ripple | Path-dependent and un-editable chain helps fast transaction. Low power consumption as compared to PoW |
Required to maintain node list which is difficult to manage Highly decentralize |
| Proof-of-Personhood | Remove the disadvantages of POW and POS | Expensive |
This is made possible by employing consensus algorithms like Paxos, Raft, and PBFT, which impose less demanding security requirements due to their permissioned nature and the identities they employ [13].
PoW is not as energy-intensive as before. Paxos has been the preferred protocol for achieving consensus in distributed networks, particularly in permissioned blockchains. Over the past decade, it has practically become synonymous with consensus, leading to numerous implementations based on or influenced by Paxos. However, a consensus method called Raft has emerged to enhance Paxos’ comprehension, correctness, and performance. Raft focuses heavily on leader elections and aims to make Paxos easier to understand and execute. Another consensus technique, Practical Byzantine Fault Tolerance (PBFT), was initially developed in the late 1990s. It provides fault tolerance for asynchronous systems by allowing up to (n − 1)/3 faults, where n is the total number of alternations.
6. Blockchain Models for Secure IoT Environment
This section provides a comprehensive discussion of the existing secure IOT environment. Due to the limited availability of time and space, some additional literature has been shown in Table 2. Sachi Nandan Mohanty et al. [14] express that current models of BC do not suit IOT because of model complexity, limited support for scalability, and the overhead of high bandwidth and latency. The authors have put forward a highly efficient and lightweight integrated blockchain (ELIB) model to address the specific requirements for IoT suitability. They conducted tests by implementing this model in a smart home environment to validate its applicability in various IoT settings. To overcome the limitations of resource-constrained smart homes, the authors introduced a centralized manager responsible for generating shared keys, facilitating data transportation, and managing incoming and outgoing requests. The ELIB model they propose establishes an overlay network that allows the integration of highly capable resources with a public blockchain, ensuring dedicated security and privacy. The authors used a lightweight consensus method in their proposed ELIB model. These optimizations were used in order to achieve the best possible performance.
Moreover, the authors conducted thorough simulations in different scenarios, taking into account processing speed, energy consumption, and overhead. They compared the results of their model with the baseline technique and demonstrated that the ELIB model achieved a remarkable 50% reduction in total processing time while consuming the least amount of energy possible (0.07 mJ). The authors asserted that the ELIB model outperforms the baseline technique when evaluated against multiple criteria.
Yongfeng Qian et al. [15] also discussed that the Internet of Things (IoT) has advanced quickly, providing customers with significant convenience in a variety of areas, including smart homes, smart transportation, and more. They pointed out that it could potentially pose security issues, though. The authors used the three IoT layers of perception, network, and application in order to address this difficulty, followed by the accompanying security issues for each layer. Afterward, they suggested a high-level security management scheme based on blockchain for various IoT devices across their whole life cycles.
IoT security remains a significant challenge that requires further investigation. To instill trust in IoT systems, IoT authentication is essential, as emphasized by Osama A. et al. [16] The authors argue that centralized authentication methods have proven ineffective for cross-domain authentication and fail to accommodate the expanding IoT networks. The authors propose a hybrid architecture for IoT systems that combines centralized and blockchain-based authentication to address these issues. The proposed approach establishes edge servers for centralized authentication for interconnected IoT devices. The authors emphasize the need for efficient authentication, which entails minimizing the utilization of IoT resources. Therefore, lightweight cryptographic algorithms were implemented by the authors. To illustrate the proposed architecture, a local Ethereum blockchain network was employed. Before concluding, the authors conducted a side-by-side comparison of the proposed method with centralized and blockchain-based authentication systems. They assert that their approach provides considerable benefits to IoT devices in terms of the total computation cost, the amount of time required for execution, and the amount of power used.
To address concerns with trustworthiness, Punam Prabha presented a hybrid consensus mechanism (HCM) based on blockchain that is used in electronic healthcare systems (EHS) [17]. The purpose of the suggested HCM is to fulfill the role of a reputation module based on the actions of the blocks. HCM also includes five algorithms, one for each of the following: creation, validation, handling of forks (if any), generation of Merkle trees, and reward/punishment modules.
In their study [18], Sharda Tiwari explored a blockchain- and internet-based real-time medical management system that is protected using cryptography. The authors described how electronic healthcare systems are expanding significantly today. Since various patients have different data, it is necessary to record the data that is retrieved from IoT devices in a database for future reference. They expressed that the IoT is vulnerable to privacy and security breaches because it lacks inherent security measures, as this information is crucial for a certain patient. The doctor cannot identify the patient’s real issue and cannot treat the patient properly if this data is manipulated by an intrusive party, which results in significant injury to the patient. The authors suggested that there should be a security mechanism for patient data using blockchain. To eliminate this anonymous data access, the authors created an IoT-based prototype using blockchain technology to keep the patient data private.
Table 2. Literature review of existing state-of-the-art secure IOT models.
| Reference | Methodology (Protocol Used) | Limitations |
|---|---|---|
| Subhi Alrubei et al. [19] | HDPoA Honesty-based Distributed Proof of Authority, Scalability mechanism |
Did not deploy over a large area with more nodes. Did not test in different IoT contexts, to fully evaluate the performance of HDPoA. |
| Abdella, J. et al. [20] | HiCoOB: Hierarchical Concurrent Optimistic Blockchain Consensus Protocol, Concurrent execution of transactions |
The inability to provide assistance for mobile energy users and producers. |
| Pabitha, P. [21] | ModChain: A blockchain infrastructure that is hybridized, secure, and scalable, designed specifically for the IoT | Did not cater addition of false data in chain effectively. |
| Kaur, M. [22] | DPoAC: Delegated Proof of Accessibility, Data privacy and Encrypted communication |
Large-scale experimentation is missing to ensure the validity of the proposed protocol. A comparison of the proposed protocol’s performance with existing protocols is missing. |
| Xu, R. et al. [23] | μDFL: Micro chained Decentralized Federated Learning, Performance and scalability |
Validation of the proposed μDFL in real-world FL applications is missing. Evaluation of performance and security on various attacks. |
| Alhejazi, M. et al. [24] | WMCA: Weighted Majority Consensus Algorithm, Security, |
A protection mechanism for the master node from cyber attacks is missing. As master node will be the only node to calculate and maintain the weights for each minder. |
Jawad Ali et al. [25] proposed a technique to address the issue generated by the nature and proliferation of IoT systems. These features make the devices vulnerable to a wide range of threats. Their method included observing how blockchain-supported IoT devices interacted with other networks to determine their trustworthiness. In order to extract each device’s activity and analyze behavior using deep machine learning techniques, they built a unique behavior monitor and implemented it on a chosen node. And they employed Trusted Execution Technology (TEE), which can be used to set up a safe place for the blockchain’s most important applications to run and store their data. In the evaluation phase, the authors concluded with an analysis of data from various IoT devices that a Mirai attack had impacted [25]. They claimed that their suggested method has more strength in terms of detection speed and accuracy than other models available.
From the above discussion, it has been observed that the selection of consensus algorithms depends on various factors such as scalability, energy efficiency, interoperability, and integration with existing IoT protocols and standards. Because blockchain platforms like Bitcoin and Ethereum blockchains are computationally costly, have large bandwidth overheads, and experience IoT delays, lightweight consensus algorithms are necessary for IoT to embrace blockchain [26]. In order to overcome this challenge, a suitable consensus protocol must be created by taking into account IoT issues, including a lack of security, disparate device standards, limited device memory, and a vast volume of data. Alternative to this, some IoT security issues may be resolved by a distributed blockchain, according to a novel blockchain-based solution disclosed in [27], which demonstrated a decentralized blockchain-based identity management system that protects patients’ confidentiality and privacy when they get remote medical treatment. Using blockchain for medical IoT to protect privacy is a suggestion made in [28]. The storage problem for industrial IoT was solved by offering a hierarchical blockchain storage structure (ChainSplitter), in which most of the blockchain is hosted on cloud services. Lastly, lightweight algorithms are required for IoT blockchain to overcome power and processing time constraints [29][30].
References
- Boyes, H.; Hallaq, B.; Cunningham, J.; Watson, T. The industrial internet of things (IIoT): An analysis framework. Comput. Ind. 2018, 101, 1–12.
- Vitturi, S.; Zunino, C.; Sauter, T. Industrial Communication Systems and Their Future Challenges: Next-Generation Ethernet, IIoT, and 5G. Proc. IEEE 2019, 107, 944–961.
- Minoli, D. IoT Applications to Smart Campuses and a Case Study. EAI Endorsed Trans. Smart Cities 2017, 2, 153483.
- Abdulhamid, A.; Kabir, S.; Ghafir, I.; Lei, C. An Overview of Safety and Security Analysis Frameworks for the Internet of Things. Electronics 2023, 12, 3086.
- McCutcheon, W.; Pappa, A.; Bell, B.A.; McMillan, A.; Chailloux, A.; Lawson, T.; Mafu, M.; Markham, D.; Diamanti, E.; Kerenidis, I.; et al. Experimental Verification of Multipartite Entanglement in Quantum Networks. Nat. Commun. 2016, 7, 13251.
- Cheng, Y.; Chen, W.; Fan, W.; Huang, W.; Yu, G.; Liu, W. IoTFuzzBench: A Pragmatic Benchmarking Framework for Evaluating IoT Black-Box Protocol Fuzzers. Electronics 2023, 12, 3010.
- Stanley, M.; Gui, Y.; Unnikrishnan, D.; Hall, S.R.G.; Fatadin, I. Recent Progress in Quantum Key Distribution Network Deployments and Standards. J. Phys. Conf. Ser. 2022, 2416, 012001.
- Qiu, X.; Yao, D.; Kang, X.; Abulizi, A. Blockchain and K-Means Algorithm for Edge AI Computing. Comput. Intell. Neurosci. 2022, 2022, 1–13.
- Sobecki, A.; Barański, S.; Szymański, J. Privacy-Preserving, Scalable Blockchain-Based Solution for Monitoring Industrial Infrastructure in the Near Real-Time. Appl. Sci. 2022, 12, 7143.
- Plageras, A.P.; Psannis, K.E.; Stergiou, C.; Wang, H.; Gupta, B.B. Efficient IoT-Based Sensor BIG Data Collection–Processing and Analysis in Smart Buildings. Future Gener. Comput. Syst. 2018, 82, 349–357.
- Guo, J.; Xiong, Q.; Yang, M.; Zhao, Z. A Double-Compensation-Based Federated Learning Scheme for Data Privacy Protection in a Social IoT Scenario. Comput. Mater. Contin. 2023, 76, 827–848.
- Saad, M.; Bin Ahmad, M.; Asif, M.; Khalid Khan, M.; Mahmood, T.; Tag Eldin, E.; Abdel Hameed, H. Blockchain and IIoT Enabled Solution for Social Distancing and Isolation Management to Prevent Pandemics. Comput. Mater. Contin. 2023, 76, 687–709.
- Alsaqqa, S.; Almajali, S. Blockchain Technology Consensus Algorithms and Applications: A Survey. Int. J. Interact. Mob. Technol. 2020, 14, 142.
- Mohanty, S.N.; Ramya, K.C.; Rani, S.S.; Gupta, D.; Shankar, K.; Lakshmanaprabu, S.K.; Khanna, A. An Efficient Lightweight Integrated Blockchain (ELIB) Model for IoT Security and Privacy. Future Gener. Comput. Syst. 2020, 102, 1027–1037.
- Qian, Y.; Jiang, Y.; Chen, J.; Zhang, Y.; Song, J.; Zhou, M.; Pustišek, M. Towards Decentralized IoT Security Enhancement: A Blockchain Approach. Comput. Electr. Eng. 2018, 72, 266–273.
- Meinert, E.; Alturkistani, A.; Foley, K.A.; Osama, T.; Car, J.; Majeed, A.; Van Velthoven, M.; Wells, G.; Brindley, D. Blockchain Implementation in Health Care: Protocol for a Systematic Review. JMIR Res. Protoc. 2019, 8, e10994.
- Prabha, P.; Chatterjee, K. Design and Implementation of Hybrid Consensus Mechanism for IoT Based Healthcare System Security. Int. J. Inf. Technol. 2022, 14, 1381–1396.
- Wankhade, V.R. Adoption of Blockchain Based Smart Application in Machine Learning. Int. J. Res. Appl. Sci. Eng. Technol. 2021, 9, 600–605.
- Alrubei, S.M.; Ball, E.A.; Rigelsford, J.M.; Willis, C.A. Latency and Performance Analyses of Real-World Wireless IoT-Blockchain Application. IEEE Sens. J. 2020, 20, 7372–7383.
- Abdella, J.; Tari, Z.; Mahmud, R.; Sohrabi, N.; Anwar, A.; Mahmood, A. HiCoOB: Hierarchical Concurrent Optimistic Blockchain Consensus Protocol for Peer-to-Peer Energy Trading Systems. IEEE Trans. Smart Grid 2022, 14, 3927–3943.
- Pabitha, P.; Priya, J.C.; Praveen, R.; Jagatheswari, S. ModChain: A Hybridized Secure and Scaling Blockchain Framework for IoT Environment. Int. J. Inf. Technol. 2023, 15, 1741–1754.
- Kaur, M.; Gupta, S.; Kumar, D.; Verma, C.; Neagu, B.-C.; Raboaca, M.S. Delegated Proof of Accessibility (DPoAC): A Novel Consensus Protocol for Blockchain Systems. Mathematics 2022, 10, 2336.
- Xu, R.; Chen, Y. μDFL: A Secure Microchained Decentralized Federated Learning Fabric Atop IoT Networks. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2677–2688.
- Alhejazi, M.M.; Mohammad, R.M.A. Enhancing the Blockchain Voting Process in IoT Using a Novel Blockchain Weighted Majority Consensus Algorithm (WMCA). Inf. Secur. J. A Glob. Perspect. 2021, 31, 125–143.
- Khezr, S.; Yassine, A.; Benlamri, R. Towards a Secure and Dependable IoT Data Monetization Using Blockchain and Fog Computing. Clust. Comput. 2022, 26, 1551–1564.
- Xu, H.; Zhang, L.; Onireti, O.; Fang, Y.; Buchanan, W.J.; Imran, M.A. BeepTrace: Blockchain-Enabled Privacy-Preserving Contact Tracing for COVID-19 Pandemic and Beyond. IEEE Internet Things J. 2021, 8, 3915–3929.
- Kumar, R.N. Comparative Study of Proof of Work (PoW) and Delegated Proof of Stake (DPoS) Blockchain Consensus Algorithm. Int. J. Res. Appl. Sci. Eng. Technol. 2021, 9, 650–654.
- Rashid, M.M.; Choi, P.; Lee, S.-H.; Kwon, K.-R. Block-HPCT: Blockchain Enabled Digital Health Passports and Contact Tracing of Infectious Diseases like COVID-19. Sensors 2022, 22, 4256.
- Rustam, F.; Raza, A.; Ashraf, I.; Jurcut, A.D. Deep Ensemble-based Efficient Framework for Network Attack Detection. In Proceedings of the 2023 21st Mediterranean Communication and Computer Networking Conference (MedComNet), Ponza, Italy, 13–15 June 2023; pp. 1–10.
- Ezhilarasi, M.; Gnanaprasanambikai, L.; Kousalya, A.; Shanmugapriya, M. A novel implementation of routing attack detection scheme by using fuzzy and feed-forward neural networks. Soft Comput. 2023, 27, 4157–4168.
More
Information
Subjects:
Computer Science, Cybernetics
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
616
Revisions:
2 times
(View History)
Update Date:
28 Sep 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No





