Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Mohammed Amin Almaiah | -- | 2271 | 2023-09-24 10:26:11 | | | |
| 2 | Peter Tang | Meta information modification | 2271 | 2023-09-25 03:33:56 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Al Hwaitat, A.K.; Almaiah, M.A.; Ali, A.; Al-Otaibi, S.; Shishakly, R.; Lutfi, A.; Alrawad, M. Blockchain-Based Authentication Framework for Secure IoT Networks. Encyclopedia. Available online: https://encyclopedia.pub/entry/49567 (accessed on 28 February 2026).
Al Hwaitat AK, Almaiah MA, Ali A, Al-Otaibi S, Shishakly R, Lutfi A, et al. Blockchain-Based Authentication Framework for Secure IoT Networks. Encyclopedia. Available at: https://encyclopedia.pub/entry/49567. Accessed February 28, 2026.
Al Hwaitat, Ahmad K., Mohammed Amin Almaiah, Aitizaz Ali, Shaha Al-Otaibi, Rima Shishakly, Abdalwali Lutfi, Mahmaod Alrawad. "Blockchain-Based Authentication Framework for Secure IoT Networks" Encyclopedia, https://encyclopedia.pub/entry/49567 (accessed February 28, 2026).
Al Hwaitat, A.K., Almaiah, M.A., Ali, A., Al-Otaibi, S., Shishakly, R., Lutfi, A., & Alrawad, M. (2023, September 24). Blockchain-Based Authentication Framework for Secure IoT Networks. In Encyclopedia. https://encyclopedia.pub/entry/49567
Al Hwaitat, Ahmad K., et al. "Blockchain-Based Authentication Framework for Secure IoT Networks." Encyclopedia. Web. 24 September, 2023.
Copy Citation
Most current research on decentralized IoT applications focuses on a specific vulnerability. However, for IoT applications, only a limited number of techniques are dedicated to handling privacy and trust concerns. To address that, blockchain-based solutions that improve the quality of IoT networks are becoming increasingly used. In the context of IoT security, a blockchain-based authentication framework could be used to store and verify the identities of devices in a decentralized manner, allowing them to communicate with each other and with external systems in a secure and trust-less manner.
security
privacy
blockchain
smart contracts
IoT
encryption
transaction
1. Introduction
The proliferation of industrial IoT applications and networking services has facilitated a tremendous increase in the number of connected devices. These application devices can capture real-time industrial data with a dedicated sensor unit [1]. Industrial advancement and technological guidance are behind this shift in how systems interact with physical and logical things. A centralized architecture is used to communicate real-time industrial data and evaluate the critical components of IoT, including identity management [2]. A single failure point is feasible due to this common technique [3]. A significant issue with the Internet of Things (IoT) is the difficulty in maintaining and managing many connected devices [4]. A system of networks can talk interactively through adaptive self-configuration. IoT applications can be commercialized over the 6G network. A fundamental component of the IoT, the wireless sensor network (WSN) gathers and transmits physical data using various heterogeneous models [5].
Data security is a major concern of IoT systems because they are built by connecting many IoT devices [6]. Data generated by these devices are stored in the cloud and transmitted across various networks. A cyber-attack on a smart healthcare system can substantially impact the system’s ability to produce and supply electricity. In addition to financial and other types of damage, cyber-attacks on smart healthcare can cause operational failures, power outages, the theft of critical data, and complete security breaches [7]. Cyber experts face difficulties keeping tabs on everything that passes via a smart grid and recognizing potential threats and attacks. Even though machine learning has become an essential part of cybersecurity, the problem is that this field requires distinct approaches and theoretical viewpoints to handle the enormous volume of data generated and transported across numerous networks in a smart grid [8]. The attacks and threats that could be launched against this proof-of-concept environment are being determined using threat modeling. Several potential threats have been tested, including detection, tampering, repudiation, information leakage, denial of service (DoS), and extended privilege (EoP). Each of the risks and the security elements associated with them are addressed using STRIDE. STRIDE is a typical threat modeling technique for finding and classifying attack vectors [9]. Using the well-known industrial framework MITRE ATTCK, researchers can detect threats disguised as tactics, techniques, and procedures (TTP) [10].
Based on the above, blockchain technology could be one of the main solutions for IoT security issues [11]. A blockchain provides a decentralized system using a consensus mechanism and smart contracts [12]. Smart contracts are the protocols that trigger the blockchain to act according to a particular activity or situation [13]. Blockchains can be categorized into three classes: private, public, and hybrid public blockchain technology. The main feature of a blockchain is to provide security and only keep records and transactions within a single organization. A public blockchain provides access to the public using a public API. Moreover, such a model interacts with external networks such as gateway networks or cloud outsourcing. A hybrid blockchain is also called a consortium blockchain, which provides features of both a private and public blockchain.
2. Blockchain-Based Authentication Framework for Secure IoT Networks
Blockchain technology can be used to build trust and monitor node activity in IoT networks. It is challenging to integrate a blockchain into IoT applications due to its high power consumption and job outsourcing [14]. Several blockchain-based Internet of Things (IoT) applications have recently been created to address these concerns. These blocks can be used to delete old transactions and blocks from the blockchain without jeopardizing security. Pan et al. [15] created an IoT resource management prototype using blockchain technology and smart contracts to securely record all IoT transactions [15]. Deploying smart contracts involves evaluating the source code, bytes of code, and execution histories. This is how we test our computer traffic analysis deployment scenario. Ali et al. [16] investigated blockchain technology and smart contract applications in cloud storage. Tam et al. utilize a pay-as-you-go car business model. This technology’s strengths are traceability and tamper-proof characteristics. Ali et al. [17] created a blockchain-based publisher–subscriber model. They designed their solution to ensure data integrity in real-time IoT processing by balancing computational resources and workload. Liu et al. delegated computationally intensive POW mining tasks to nearby edge servers in blockchain-enabled mobile IoT systems [18]. Chen et al. conducted additional research. Securing biometric data for patient authentication is a common issue. In particular, finger vein biometric data has been studied extensively. A strong verification mechanism with high levels of reliability, privacy, and security is required to better secure these data. Also, biometric data are difficult to replace, and any leakage of biometric data exposes users to serious threats, such as replay attacks employing stolen biometric data. This research offers a unique verification secure framework based on triplex blockchain-based particle swarm optimization (PSO)-advanced encryption standard (AES) approaches in medical systems for patient authentication. The discussion has three stages. First presented is a new hybrid model pattern based on RFID and finger vein biometrics to boost randomness. It proposes a new merge method that combines RFID and finger vein characteristics in a random pattern. Second, the suggested verification safe framework is based on the CIA standard for telemedicine authentication using AES encryption, blockchain technology, and PSO in steganography [19]. Finally, the proposed secure verification architecture was validated and evaluated [20]. The combination of WSN functional activities with 6G network topologies allows us to test a wide range of IoT application deployment models. Many IoT devices collect data using IPV6 across low-power wireless personal area networks and wearables (6LoWPAN) [21][22]. We were able to keep user data confidential with the help of AKA [23]. Companies that use public cloud services and large-scale data storage systems have long prioritized client data protection [24].
Some studies have used other approaches such as physical layer security (PLS) in order to ensure secure transmission via a signal and reduce the quality of the signal in the attacker device [25][26][27][28][29][30]. As compared with other security approaches, the PLS approach has several strong advantages, such as the PLS technique does not depend on keys in the encryption/decryption processes, which will help through minimizing the difficulty of the secret keys distribution and its management in an IoT environment [31][32][33][34]. In addition, the PLS approach uses simple signal processing algorithms, which need low overhead as compared to other encryption methods. Recognizing the value of reliable data in decision-making batch processing may be required when working with huge datasets in the cloud. Even so, comparing the two seems impossible [35]. To safeguard user passwords, Edward et al. [36] examined privacy laws and regulations. In real-time data communication with the Internet, dispersed mobility management rules and smart computer activities are separated. Unlike real-time systems, cryptographic algorithms establish a public/private key pair. The cloud server can read private cloud data by sharing a secret key [37]. Statista predicts there will be 50 billion connected IoT devices by 2030. As a result, the market will increase rapidly in the future. Consistently protecting user privacy, blockchain-based trust might be used to provide seamless authentication (TAB-SAPP). Smart design architecture is presented for spreading device connectivity over physical networks. Zigbee, Z-Wave, and Bluetooth Low Energy (BLE) are the most widely used industrial automation standards. The blockchain’s peer-to-peer nature allows IoT devices to connect to each other. Decentralized IoT devices and consensus methods generate and store data in encrypted chain-like blocks, while smart contracts modify data and control the system [38]. Blockchain-enabled IoT relies on a secure security paradigm (also known as IoT-EBT). This is possible because smart contracts retain and limit computing resources associated with a device’s identification [39].
Different applications demand different levels of security, and resource scarcity plays a factor. Finding the best encryption technique for IoT medical data protection is essential [40][41][42][43]. Electronic sensors capture medical data from patients and safely transmit them to the healthcare system. To avoid unwanted access or needless interruptions, trust and data privacy must be ensured from the start sensors [44][45][46].
Thus, data encryption from the start sensors is required, but due to restrictions in CPU complexity, battery consumption, and transmission bandwidth, using standard crypto algorithms is impractical [47][48][49][50]. Research on realistic, lightweight encryption techniques for IoT medical systems is ongoing. This research compares eight cryptographic algorithms in terms of memory usage and speed. The research determines the best candidate algorithm for the proposed health care system, balancing the ideal requirement and future dangers [51][52][53][54]. Both parties must be authenticated to use these services safely [55][56][57][58]. The server should require authentication to protect records from unauthorized users and ensure patient privacy (client side). Patient authentication is required to prevent server impersonation [59][60][61][62]. This proof of concept addresses emergency situations where a patient arrives unconscious at the hospital and needs to access information without providing an authorization key. This issue requires safe biometric identification technologies such as palm vein and iris [63][64][65][66]. In addition to providing high levels of security, usability, and dependability, biometric technology authentication has grown in popularity [67][68][69][70][71][72]. For example, the finger vein (FV) biometric is highly secure. Most modern authentication systems save biometric patterns in a database. Authentication extracts this data as biological biometrics. Secure biometric authentication with FV will be more resistant to security breaches and impersonation attempts. The human FV is a physiological biometric used to identify people by their blood veins’ morphological characteristics. Individuals and offenders (in legal situations) are identified using this new technology, which is more accurate than other biometric systems. In order to secure FV biometrics, many researchers have used uni- or multi-biometrics, which include FV biometrics as part of the verification system. These approaches are applied in two steps as follows: To protect FV patterns, researchers are trying to extract trustworthy properties from FVs, which can be used to uniquely identify individuals. These exclusive properties from the FV junction sites and the angles between veins are used to build a unique key (biokey). This key is used to encrypt data patterns. The observation matrix extracts patterns and features, which are then encrypted with a random key [73]. Some researchers employed multi-biometrics to add to existing features. These traits have been used to identify people (FV, retina, and fingerprint). The main issues with the system the author devised in [74][75][76] were communication cost and computational cost.
3. Overview of Blockchain Structure
A blockchain is a decentralized, distributed ledger that is used to record transactions across a network of computers [77]. Each block in the chain contains a record of multiple transactions, and once a block is added to the chain, it cannot be altered [78]. This makes the blockchain a secure and transparent way to store data. As shown in Figure 1, the data structure of a blockchain is typically a linked list of blocks, with each block containing a set of transactions. The transactions are organized using a data structure called a Merkle tree, which facilitates efficient verification of the integrity of the transactions. The data model for a blockchain is typically based on a distributed ledger model, in which the ledger is maintained and updated by a network of computers rather than a central authority. The ledger is structured as a chain of blocks, with each block containing a set of transactions and a cryptographic hash of the previous block. This structure facilitates the secure and transparent storage of data on the blockchain [79]. In a blockchain, the data are stored in a decentralized manner, with copies of the ledger being maintained by multiple nodes on the network [80]. This ensures that the data are secure and cannot be altered without the consensus of the network [81]. Each transaction on the blockchain is cryptographically signed, providing a secure and verifiable record of the transaction [82]. Overall, the data structure and data model of a blockchain are designed to provide a secure and transparent way to store and manage data in a decentralized manner.
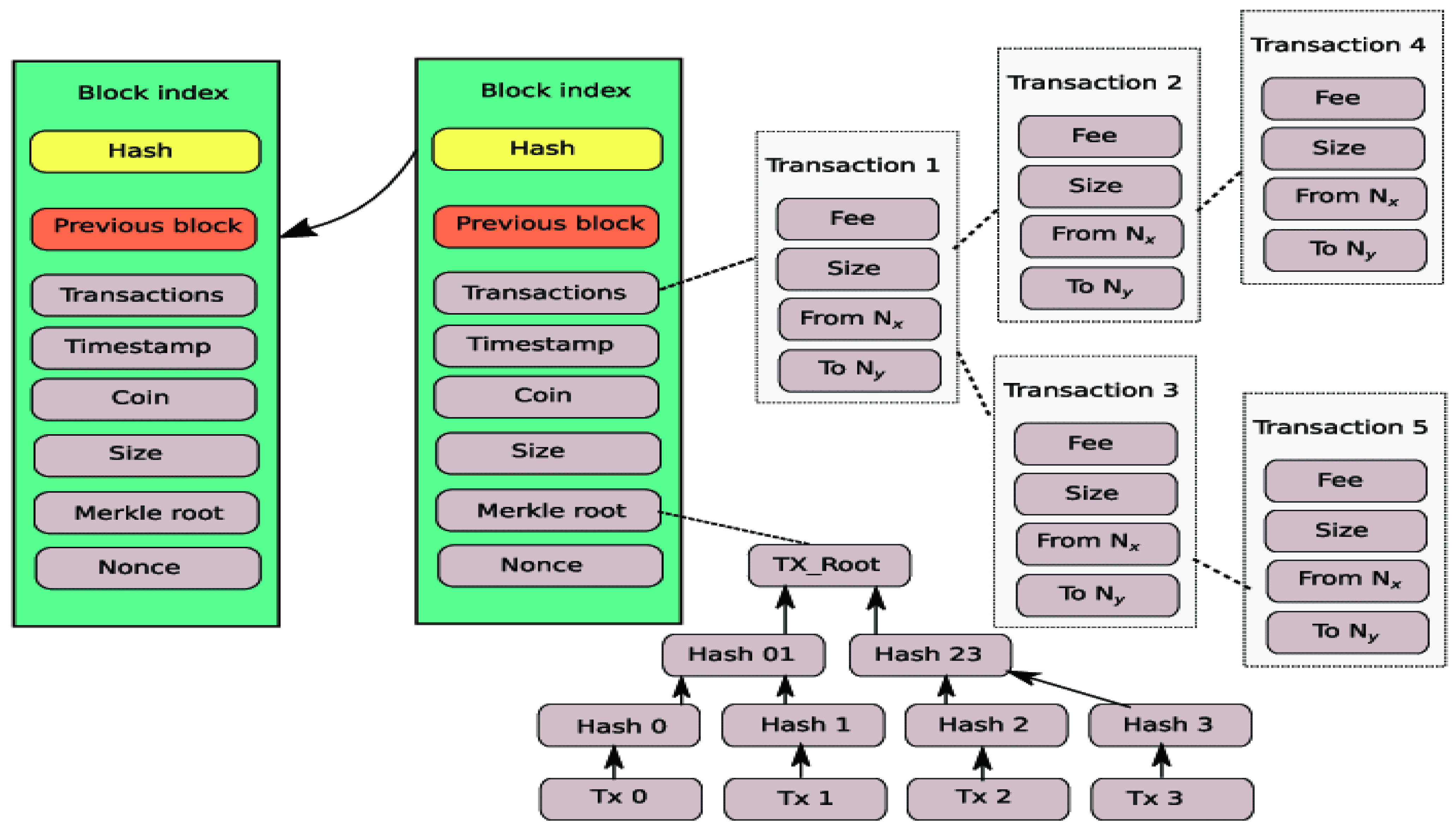
Figure 1. The blockchain data structure.
4. IoT Data Flow
IoT data refer to the vast amount of information generated by connected devices and sensors that comprise the Internet of Things. These devices can include anything from industrial machinery and consumer appliances to vehicles and home security systems. The data generated by these devices can include a wide variety of information, such as sensor readings, GPS coordinates, usage patterns, etc.
IoT data and blockchain technology can be combined through the use of smart contracts. A smart contract is a self-executing contract with the terms of the agreement between buyer and seller being directly written into lines of code. The code and the transactions are stored on a blockchain network, making them transparent and secure. Smart contracts can be used to automate the process of collecting and storing IoT data on the blockchain, creating a tamper-proof record of the data.
As shown in Figure 2, one way to authenticate IoT data using blockchain technology is through the use of blockchain-based smart contracts to authenticate the data. In this model, the smart contract is programmed to verify the authenticity of the data before it is recorded on the blockchain [31]. This can help ensure that only authentic data are stored on the blockchain, increasing the reliability and trustworthiness of the data. In this research, the use of smart contracts can help to provide a secure and verifiable way to authenticate IoT data using blockchain technology.
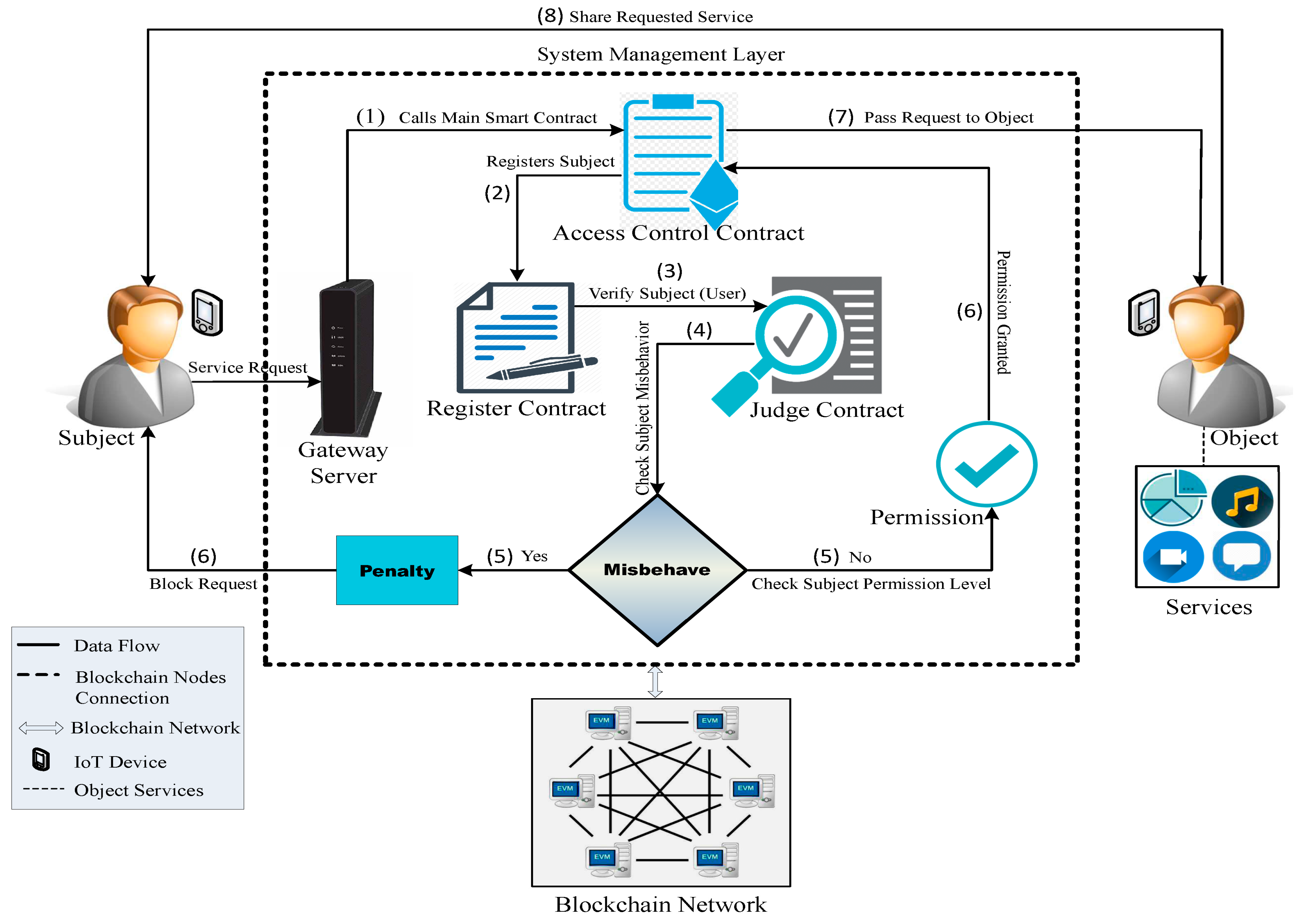
Figure 2. IoT using blockchain smart contracts.
References
- Siam, A.I.; Almaiah, M.A.; Al-Zahrani, A.; Elazm, A.A.; El Banby, G.M.; El-Shafai, W.; El-Samie, F.E.A.; El-Bahnasawy, N.A. Secure Health Monitoring Communication Systems Based on IoT and Cloud Computing for Medical Emergency Applications. Comput. Intell. Neurosci. 2021, 2021, 8016525.
- Ali, A.; Pasha, M.F.; Fang, O.H.; Khan, R.; Almaiah, M.A.; KAl Hwaitat, A. Big data based smart blockchain for information retrieval in privacy-preserving healthcare system. In Big Data Intelligence for Smart Applications; Springer International Publishing: Cham, Switzerland, 2022; pp. 279–296.
- Altulaihan, E.; Almaiah, M.A.; Aljughaiman, A. Cybersecurity Threats, Countermeasures and Mitigation Techniques on the IoT: Future Research Directions. Electronics 2022, 11, 3330.
- Hasnain, M.; Pasha, M.F.; Ghani, I.; Mehboob, B.; Imran, M.; Ali, A. Benchmark Dataset Selection of Web Services Technologies: A Factor Analysis; IEEE Access: Piscataway, NJ, USA, 2020; Volume 8, pp. 53649–53665.
- Ali, A.; Rahim, H.A.; Pasha, M.F.; Dowsley, R.; Masud, M.; Ali, J.; Baz, M. Security, Privacy, and Reliability in Digital Healthcare Systems Using Blockchain. Electronics 2021, 10, 2034.
- Almaiah, M.A.; Hajjej, F.; Ali, A.; Pasha, M.F.; Almomani, O. An AI-Enabled Hybrid Lightweight Authentication Model for Digital Healthcare Using Industrial Internet of Things Cyber-Physical Systems. Sensors 2022, 22, 1448.
- Yazdinejad, A.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G.; Karimipour, H. Secure Intelligent Fuzzy Blockchain Framework: Effective Threat Detection in IoT Networks. Comput. Ind. 2023, 144, 103801.
- Hameed, K.; Ali, A.; Naqvi, M.H.; Jabbar, M.; Junaid, M.; Haider, A. Resource management in operating systems-a survey of scheduling algorithms. In Proceedings of the International Conference on Innovative Computing (ICIC), Lanzhou, China, 2–5 August 2016; Volume 1.
- Singh, H.; Ahmed, Z.; Khare, M.D.; Bhuvana, J. An IoT and Blockchain-Based Secure Medical Care Framework Using Deep Learning and Nature-Inspired Algorithms. Int. J. Intell. Syst. Appl. Eng. 2023, 11, 183–191.
- Kim, H.; Kim, S.-H.; Hwang, J.Y.; Seo, C. Efficient Privacy-Preserving Machine Learning for Blockchain Network. IEEE Access 2019, 7, 136481–136495.
- Sharma, P.; Namasudra, S.; Crespo, R.G.; Parra-Fuente, J.; Trivedi, M.C. EHDHE: Enhancing security of healthcare documents in IoT-enabled digital healthcare ecosystems using blockchain. Inf. Sci. 2023, 629, 703–718.
- Almadani, M.S.; Alotaibi, S.; Alsobhi, H.; Hussain, O.K.; Hussain, F.K. Blockchain-based multi-factor authentication: A systematic literature review. Internet Things 2023, 23, 100844.
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R.; Jolfaei, A.; Islam, A.N. A blockchain-orchestrated deep learning approach for secure data transmission in IoT-enabled healthcare system. J. Parallel Distrib. Comput. 2023, 172, 69–83.
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R. P4-to-blockchain: A secure blockchain-enabled packet parser for software defined networking. Comput. Secur. 2020, 88, 101629.
- Sharma, P.C.; Mahmood, R.; Raja, H.; Yadav, N.S.; Gupta, B.B.; Arya, V. Secure authentication and privacy-preserving blockchain for industrial internet of things. Comput. Electr. Eng. 2023, 108, 108703.
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y. Fairness-Based Packing of Industrial IoT Data in Permissioned Blockchains. IEEE Trans. Ind. Inform. 2020, 17, 7639–7649.
- Bordel, B.; Alcarria, R.; Robles, T. A Blockchain Ledger for Securing Isolated Ambient Intelligence Deployments Using Reputation and Information Theory Metrics; Wireless Networks: New York, NY, USA, 2023; pp. 1–7.
- Selvarajan, S.; Srivastava, G.; Khadidos, A.O.; Khadidos, A.O.; Baza, M.; Alshehri, A.; Lin, J.C.-W. An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J. Cloud Comput. 2023, 12, 38.
- Lacity, M.C. Addressing Key Challenges to Making Enterprise Blockchain Applications a Reality. J. Mis. Q. Exec. 2018, 17, 3.
- Sengupta, J.; Ruj, S.; Das Bit, S. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481.
- Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Multi-Layer Blockchain-Based Security Architecture for Internet of Things. Sensors 2021, 21, 772.
- Peng, C.; Wu, C.; Gao, L.; Zhang, J.; Yau, K.-L.A.; Ji, Y. Blockchain for Vehicular Internet of Things: Recent Advances and Open Issues. Sensors 2020, 20, 5079.
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.-K.R. Blockchain: A Panacea for Healthcare Cloud-Based Data Security and Privacy? IEEE Cloud Comput. 2018, 5, 31–37.
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2018, 25, 1398–1411.
- Kim, T.M.; Lee, S.-J.; Chang, D.-J.; Koo, J.; Kim, T.; Yoon, K.-H.; Choi, I.-Y. DynamiChain: Development of Medical Blockchain Ecosystem Based on Dynamic Consent System. Appl. Sci. 2021, 11, 1612.
- Hang, L.; Kim, D.-H. Design and Implementation of an Integrated IoT Blockchain Platform for Sensing Data Integrity. Sensors 2019, 19, 2228.
- Figorilli, S.; Antonucci, F.; Costa, C.; Pallottino, F.; Raso, L.; Castiglione, M.; Pinci, E.; Del Vecchio, D.; Colle, G.; Proto, A.R.; et al. A Blockchain Implementation Prototype for the Electronic Open Source Traceability of Wood along the Whole Supply Chain. Sensors 2018, 18, 3133.
- Zhu, X.; Badr, Y. Identity management systems for the internet of things: A survey towards blockchain solutions. Sensors 2018, 18, 4215.
- Jia, X.; Hu, N.; Su, S.; Yin, S.; Zhao, Y.; Cheng, X.; Zhang, C. IRBA: An Identity-Based Cross-Domain Authentication Scheme for the Internet of Things. Electronics 2020, 9, 634.
- Ali, A.; Rahim, H.; Ali, J.; Pasha, M.F.; Masud, M.; Rehman, A.U.; Chen, C.; Baz, M. A Novel Secure Blockchain Framework for Accessing Electronic Health Records Using Multiple Certificate Authority. Appl. Sci. 2021, 11, 9999.
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724.
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-based Secure Energy Efficient Beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 59, 2085–2088.
- Niu, H.; Lin, Z.; Chu, Z.; Zhu, Z.; Xiao, P.; Nguyen, H.X.; Lee, I.; Al-Dhahir, N. Joint Beamforming Design for Secure RIS-Assisted IoT Networks. IEEE Internet Things J. 2022, 10, 1628–1641.
- Lin, Z.; Lin, M.; de Cola, T.; Wang, J.-B.; Zhu, W.-P.; Cheng, J. Supporting IoT With Rate-Splitting Multiple Access in Satellite and Aerial-Integrated Networks. IEEE Internet Things J. 2021, 8, 11123–11134.
- Tan, L.; Shi, N.; Yu, K.; Aloqaily, M.; Jararweh, Y. A Blockchain-empowered Access Control Framework for Smart Devices in Green Internet of Things. ACM Trans. Internet Technol. 2021, 21, 1–20.
- Yu, K.; Tan, L.; Yang, C.; Choo, K.-K.R.; Bashir, A.K.; Rodrigues, J.J.P.C.; Sato, T. A Blockchain-Based Shamir’s Threshold Cryptography Scheme for Data Protection in Industrial Internet of Things Settings. IEEE Internet Things J. 2021, 9, 8154–8167.
- Peng, Z.; Xu, J.; Hu, H.; Chen, L.; Kong, H. BlockShare: A Blockchain empowered system for privacy-preserving verifiable data sharing Bull. IEEE Comput. Soc. Tech. Comm. Data Eng. 2022, 1, 14–24.
- Peng, Z.; Zhang, Y.; Xu, Q.; Liu, H.; Gao, Y.; Li, X.; Yu, G. NeuChain: A fast permissioned blockchain system with deterministic ordering. Proc. VLDB Endow. 2022, 15, 2585–2598.
- Peng, Z.; Huang, J.; Wang, H.; Wang, S.; Chu, X.; Zhang, X.; Chen, L.; Huang, X.; Fu, X.; Guo, Y.; et al. BU-trace: A permissionless mobile system for privacy-preserving intelligent contact tracing. In International Conference on Database Systems for Advanced Applications; Springer: Cham, Switzerland, 2021; pp. 381–397.
- Ruan, P.; Chen, G.; Dinh, T.T.A.; Lin, Q.; Ooi, B.C.; Zhang, M. Fine-grained, secure and efficient data provenance on blockchain systems. Proc. VLDB Endow. 2019, 12, 975–9888.
- Wang, H.; Xu, C.; Zhang, C.; Xu, J.; Peng, Z.; Pei, J. vChain+: Optimizing Verifiable Blockchain Boolean Range Queries. In Proceedings of the 2022 IEEE 38th International Conference on Data Engineering (ICDE), Kuala Lumpur, Malaysia, 9–12 May 2022; pp. 1927–1940.
- Ruan, P.; Dinh, T.T.A.; Lin, Q.; Zhang, M.; Chen, G.; Ooi, B.C. Revealing Every Story of Data in Blockchain Systems. ACM SIGMOD Rec. 2020, 49, 70–77.
- Saadeh, M.; Sleit, A.; Qatawneh, M.; Almobaideen, W. Authentication techniques for the internet of things: A survey. In Proceedings of the 2016 Cybersecurity and Cyberforensics Conference (CCC), Amman, Jordan, 2–4 August 2016; pp. 28–34.
- AbuAlghanam, O.; Qatawneh, M.; Almobaideen, W.; Saadeh, M. A new hierarchical architecture and protocol for key distribution in the context of IoT-based smart cities. J. Inf. Secur. Appl. 2022, 67, 103173.
- Altarawneh, M.; Qatawneh, M.; Almobaideen, W. Overview of Applied Data Analytic Mechanisms and Approaches Using Permissioned Blockchains. Int. J. Adv. Sci. Eng. Inf. Technol. 2022, 12, 42–52.
- Qatawneh, M.; Almobaideen, W.; AbuAlghanam, O. Challenges of Blockchain Technology in Context Internet of Things: A Survey. Int. J. Comput. Appl. 2020, 175, 13–20.
- Abualghanam, O.R.; Qatawneh, M.O.; Almobaideen, W.E. A survey of key distribution in the context of internet of things. J. Theor. Appl. Inf. Technol. 2019, 97, 3217–3241.
- Adil, M.; Almaiah, M.A.; Alsayed, A.O.; Almomani, O. An Anonymous Channel Categorization Scheme of Edge Nodes to Detect Jamming Attacks in Wireless Sensor Networks. Sensors 2020, 20, 2311.
- Adil, M.; Khan, R.; Almaiah, M.A.; Al-Zahrani, M.; Zakarya, M.; Amjad, M.S.; Ahmed, R. MAC-AODV Based Mutual Authentication Scheme for Constraint Oriented Networks. IEEE Access 2020, 8, 44459–44469.
- Adil, M.; Khan, R.; Ali, J.; Roh, B.-H.; Ta, Q.T.H.; Almaiah, M.A. An Energy Proficient Load Balancing Routing Scheme for Wireless Sensor Networks to Maximize Their Lifespan in an Operational Environment. IEEE Access 2020, 8, 163209–163224.
- Adil, M.; Khan, R.; Almaiah, M.A.; Binsawad, M.; Ali, J.; Al Saaidah, A.; Ta, Q.T.H. An Efficient Load Balancing Scheme of Energy Gauge Nodes to Maximize the Lifespan of Constraint Oriented Networks. IEEE Access 2020, 8, 148510–148527.
- Rahman, H.U.; Almaiah, M.A.; Khan, M.Z.; Khan, A.; Raza, M.; Al-Zahrani, M.; Almomani, O.; Khan, R. Improving Energy Efficiency With Content-Based Adaptive and Dynamic Scheduling in Wireless Sensor Networks. IEEE Access 2020, 8, 176495–176520.
- Tatnall, A. Editorial for EAIT issue 2, 2019. Educ. Inf. Technol. 2019, 24, 953–962.
- Almaiah, M.A.; Al-Zahrani, A.; Almomani, O.; Alhwaitat, A.K. Classification of cyber security threats on mobile devices and applications. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer: Cham, Switzerland, 2021; pp. 107–123.
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data Sharing System Integrating Access Control Mechanism using Blockchain-Based Smart Contracts for IoT Devices. Appl. Sci. 2020, 10, 488.
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient Healthcare Data Sharing via Blockchain. Appl. Sci. 2019, 9, 1207.
- Sharma, A.; Sarishma; Tomar, R.; Chilamkurti, N.; Kim, B.-G. Blockchain Based Smart Contracts for Internet of Medical Things in e-Healthcare. J. Electron. 2020, 9, 1609.
- Alam Khan, F.; Asif, M.; Ahmad, A.; Alharbi, M.; Aljuaid, H. Blockchain technology, improvement suggestions, security challenges on smart grid and its application in healthcare for sustainable development. Sustain. Cities Soc. 2020, 55, 102018.
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A Decentralized Privacy-Preserving Healthcare Blockchain for IoT. Sensors 2020, 19, 326.
- Alamer, M.; Almaiah, M.A. Cybersecurity in Smart City: A systematic mapping study. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 719–724.
- Rathi, V.K.; Chaudhary, V.; Rajput, N.K.; Ahuja, B.; Jaiswal, A.K.; Gupta, D.; Elhoseny, M.; Hammoudeh, M. A blockchain-enabled multi domain edge computing orchestrator. J. IEEE Internet Things Mag. 2020, 3, 30–36.
- Al Hwaitat, A.K.; Almaiah, M.A.; Almomani, O.; Al-Zahrani, M.; Al-Sayed, R.M.; Asaifi, R.M.; Adhim, K.K.; Althunibat, A.; Alsaaidah, A. Improved security particle swarm optimization (PSO) algorithm to detect radio jamming attacks in mobile networks. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 4.
- Ali, A.; Almaiah, M.A.; Hajjej, F.; Pasha, M.F.; Fang, O.H.; Khan, R.; Teo, J.; Zakarya, M. An Industrial IoT-Based Blockchain-Enabled Secure Searchable Encryption Approach for Healthcare Systems Using Neural Network. Sensors 2022, 22, 572.
- Almaiah, M.A.; Dawahdeh, Z.; Almomani, O.; Alsaaidah, A.; Al-Khasawneh, A.; Khawatreh, S. A new hybrid text encryption approach over mobile ad hoc network. Int. J. Electr. Comput. Eng. IJECE 2020, 10, 6461–6471.
- Nkenyereye, L.; Adhi Tama, B.; Shahzad, M.K.; Choi, Y.-H. Secure and blockchain-based emergency driven message protocol for 5G enabled vehicular edge computing. Sensors 2020, 20, 154.
- Feng, C.; Yu, K.; Bashir, A.K.; Al-Otaibi, Y.D.; Lu, Y.; Chen, S.; Zhang, D. Efficient and secure data sharing for 5G flying drones: A blockchain-enabled approach. IEEE Netw. 2021, 35, 130–137.
- Khujamatov, K.; Reypnazarov, E.; Akhmedov, N.; Khasanov, D. Blockchain for 5G Healthcare architecture. In Proceedings of the 2020 International Conference on Information Science and Communications Technologies (ICISCT), Karachi, Pakistan, 8–9 February 2020; pp. 1–5.
- Almaiah, M.A. A new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology. In Artificial Intelligence and Blockchain for Future Cybersecurity Applications; Springer: Cham, Switzerland, 2021; pp. 217–234.
- Bubukayr, M.A.; Almaiah, M.A. Cybersecurity concerns in smart-phones and applications: A survey. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14 July 2021; pp. 725–731.
- Almaiah, M.A.; Hajjej, F.; Ali, A.; Pasha, M.F.; Almomani, O. A Novel Hybrid Trustworthy Decentralized Authentication and Data Preservation Model for Digital Healthcare IoT Based CPS. Sensors 2022, 22, 1448.
- Al Nafea, R.; Almaiah, M.A. Cyber security threats in cloud: Literature review. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14 July 2021; pp. 779–786.
- Almomani, O.; Almaiah, M.A.; Alsaaidah, A.; Smadi, S.; Mohammad, A.H.; Althunibat, A. Machine learning classifiers for network intrusion detection system: Comparative study. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 440–445.
- Almaiah, M.A.; Ali, A.; Hajjej, F.; Pasha, M.F.; Alohali, M.A. A Lightweight Hybrid Deep Learning Privacy Preserving Model for FC-Based Industrial Internet of Medical Things. Sensors 2022, 22, 2112.
- Vivekanandan, M.; Sastry, V.N. BIDAPSCA5G: Blockchain Based Internet of Things (IoT) Device to Device Authentication Protocol for Smart City Applications Using 5G Technology Peer-to-Peer Networking and Applications; Springer: Cham, Switzerland, 2021; Volume 14, pp. 403–419.
- Gao, J.; Agyekum, K.O.O.; Sifah, E.B.; Acheampong, K.N.; Xia, Q.; Du, X.; Guizani, M.; Xia, H. A blockchain-SDN-enabled Internet of vehicles environment for fog computing and 5G networks. IEEE Internet Things J. 2019, 7, 4278–4291.
- Zhou, S.; Huang, H.; Chen, W.; Zhou, P.; Zheng, Z.; Guo, S. Pirate: A blockchain-based secure framework of distributed machine learning in 5g networks. IEEE Netw. 2020, 34, 84–91.
- Zhang, Y.; Wang, K.; Moustafa, H.; Wang, S.; Zhang, K. Guest Editorial: Blockchain and AI for Beyond 5G Networks. IEEE Netw. 2020, 34, 22–23.
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.-K.R. Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans. Netw. Sci. Eng. 2019, 8, 1120–1132.
- Zhao, Y.; Zhao, J.; Zhai, W.; Sun, S.; Niyato, D.; Lam, K. A Survey of 6G Wireless Communications: Emerging Technologies Future of Information and Communication Conference; Springer: Cham, Switzerland, 2021; pp. 150–170.
- Bhattacharya, P.; Tanwar, S.; Shah, R.; Ladha, A. Mobile edge computing-enabled blockchain framework—A survey. In Proceedings of the ICRIC 2019; Springer: Cham, Switzerland, 2020; pp. 797–809.
- Blockchain and 5G-Enabled Internet of Things: Background and Preliminaries Blockchain for 5G-Enabled IoT; Springer: Cham, Switzerland, 2021; pp. 3–31.
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382.
More
Information
Subjects:
Computer Science, Cybernetics
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
827
Revisions:
2 times
(View History)
Update Date:
25 Sep 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No





