The proliferation of industrial IoT applications and networking services has facilitated a tremendous increase in the number of connected devices. These application devices can capture real-time industrial data with a dedicated sensor unit [
1]. Industrial advancement and technological guidance are behind this shift in how systems interact with physical and logical things. A centralized architecture is used to communicate real-time industrial data and evaluate the critical components of IoT, including identity management [
2]. A single failure point is feasible due to this common technique [
3]. A significant issue with the Internet of Things (IoT) is the difficulty in maintaining and managing many connected devices [
4]. A system of networks can talk interactively through adaptive self-configuration. IoT applications can be commercialized over the 6G network. A fundamental component of the IoT, the wireless sensor network (WSN) gathers and transmits physical data using various heterogeneous models [
5].
Data security is a major concern of IoT systems because they are built by connecting many IoT devices [
6]. Data generated by these devices are stored in the cloud and transmitted across various networks. A cyber-attack on a smart healthcare system can substantially impact the system’s ability to produce and supply electricity. In addition to financial and other types of damage, cyber-attacks on smart healthcare can cause operational failures, power outages, the theft of critical data, and complete security breaches [
7]. Cyber experts face difficulties keeping tabs on everything that passes via a smart grid and recognizing potential threats and attacks. Even though machine learning has become an essential part of cybersecurity, the problem is that this field requires distinct approaches and theoretical viewpoints to handle the enormous volume of data generated and transported across numerous networks in a smart grid [
8]. The attacks and threats that could be launched against this proof-of-concept environment are being determined using threat modeling. Several potential threats have been tested, including detection, tampering, repudiation, information leakage, denial of service (DoS), and extended privilege (EoP). Each of the risks and the security elements associated with them are addressed using STRIDE. STRIDE is a typical threat modeling technique for finding and classifying attack vectors [
9]. Using the well-known industrial framework MITRE ATTCK, researchers can detect threats disguised as tactics, techniques, and procedures (TTP) [
10].
2. Blockchain-Based Authentication Framework for Secure IoT Networks
Blockchain technology can be used to build trust and monitor node activity in IoT networks. It is challenging to integrate a blockchain into IoT applications due to its high power consumption and job outsourcing [
14]. Several blockchain-based Internet of Things (IoT) applications have recently been created to address these concerns. These blocks can be used to delete old transactions and blocks from the blockchain without jeopardizing security. Pan et al. [
15] created an IoT resource management prototype using blockchain technology and smart contracts to securely record all IoT transactions [
15]. Deploying smart contracts involves evaluating the source code, bytes of code, and execution histories. This is how we test our computer traffic analysis deployment scenario. Ali et al. [
16] investigated blockchain technology and smart contract applications in cloud storage. Tam et al. utilize a pay-as-you-go car business model. This technology’s strengths are traceability and tamper-proof characteristics. Ali et al. [
17] created a blockchain-based publisher–subscriber model. They designed their solution to ensure data integrity in real-time IoT processing by balancing computational resources and workload. Liu et al. delegated computationally intensive POW mining tasks to nearby edge servers in blockchain-enabled mobile IoT systems [
18]. Chen et al. conducted additional research. Securing biometric data for patient authentication is a common issue. In particular, finger vein biometric data has been studied extensively. A strong verification mechanism with high levels of reliability, privacy, and security is required to better secure these data. Also, biometric data are difficult to replace, and any leakage of biometric data exposes users to serious threats, such as replay attacks employing stolen biometric data. This research offers a unique verification secure framework based on triplex blockchain-based particle swarm optimization (PSO)-advanced encryption standard (AES) approaches in medical systems for patient authentication. The discussion has three stages. First presented is a new hybrid model pattern based on RFID and finger vein biometrics to boost randomness. It proposes a new merge method that combines RFID and finger vein characteristics in a random pattern. Second, the suggested verification safe framework is based on the CIA standard for telemedicine authentication using AES encryption, blockchain technology, and PSO in steganography [
19]. Finally, the proposed secure verification architecture was validated and evaluated [
20]. The combination of WSN functional activities with 6G network topologies allows us to test a wide range of IoT application deployment models. Many IoT devices collect data using IPV6 across low-power wireless personal area networks and wearables (6LoWPAN) [
21,
22]. We were able to keep user data confidential with the help of AKA [
23]. Companies that use public cloud services and large-scale data storage systems have long prioritized client data protection [
24].
Some studies have used other approaches such as physical layer security (PLS) in order to ensure secure transmission via a signal and reduce the quality of the signal in the attacker device [
25,
26,
27,
28,
29,
30]. As compared with other security approaches, the PLS approach has several strong advantages, such as the PLS technique does not depend on keys in the encryption/decryption processes, which will help through minimizing the difficulty of the secret keys distribution and its management in an IoT environment [
31,
32,
33,
34]. In addition, the PLS approach uses simple signal processing algorithms, which need low overhead as compared to other encryption methods. Recognizing the value of reliable data in decision-making batch processing may be required when working with huge datasets in the cloud. Even so, comparing the two seems impossible [
35]. To safeguard user passwords, Edward et al. [
36] examined privacy laws and regulations. In real-time data communication with the Internet, dispersed mobility management rules and smart computer activities are separated. Unlike real-time systems, cryptographic algorithms establish a public/private key pair. The cloud server can read private cloud data by sharing a secret key [
37]. Statista predicts there will be 50 billion connected IoT devices by 2030. As a result, the market will increase rapidly in the future. Consistently protecting user privacy, blockchain-based trust might be used to provide seamless authentication (TAB-SAPP). Smart design architecture is presented for spreading device connectivity over physical networks. Zigbee, Z-Wave, and Bluetooth Low Energy (BLE) are the most widely used industrial automation standards. The blockchain’s peer-to-peer nature allows IoT devices to connect to each other. Decentralized IoT devices and consensus methods generate and store data in encrypted chain-like blocks, while smart contracts modify data and control the system [
38]. Blockchain-enabled IoT relies on a secure security paradigm (also known as IoT-EBT). This is possible because smart contracts retain and limit computing resources associated with a device’s identification [
39].
Different applications demand different levels of security, and resource scarcity plays a factor. Finding the best encryption technique for IoT medical data protection is essential [
40,
41,
42,
43]. Electronic sensors capture medical data from patients and safely transmit them to the healthcare system. To avoid unwanted access or needless interruptions, trust and data privacy must be ensured from the start sensors [
44,
45,
46].
Thus, data encryption from the start sensors is required, but due to restrictions in CPU complexity, battery consumption, and transmission bandwidth, using standard crypto algorithms is impractical [
47,
48,
49,
50]. Research on realistic, lightweight encryption techniques for IoT medical systems is ongoing. This study compares eight cryptographic algorithms in terms of memory usage and speed. The study determines the best candidate algorithm for the proposed health care system, balancing the ideal requirement and future dangers [
51,
52,
53,
54]. Both parties must be authenticated to use these services safely [
55,
56,
57,
58]. The server should require authentication to protect records from unauthorized users and ensure patient privacy (client side). Patient authentication is required to prevent server impersonation [
59,
60,
61,
62]. This proof of concept addresses emergency situations where a patient arrives unconscious at the hospital and needs to access information without providing an authorization key. This issue requires safe biometric identification technologies such as palm vein and iris [
63,
64,
65,
66]. In addition to providing high levels of security, usability, and dependability, biometric technology authentication has grown in popularity [
67,
68,
69,
70,
71,
72]. For example, the finger vein (FV) biometric is highly secure. Most modern authentication systems save biometric patterns in a database. Authentication extracts this data as biological biometrics. Secure biometric authentication with FV will be more resistant to security breaches and impersonation attempts. The human FV is a physiological biometric used to identify people by their blood veins’ morphological characteristics. Individuals and offenders (in legal situations) are identified using this new technology, which is more accurate than other biometric systems. In order to secure FV biometrics, many researchers have used uni- or multi-biometrics, which include FV biometrics as part of the verification system. These approaches are applied in two steps as follows: To protect FV patterns, researchers are trying to extract trustworthy properties from FVs, which can be used to uniquely identify individuals. These exclusive properties from the FV junction sites and the angles between veins are used to build a unique key (biokey). This key is used to encrypt data patterns. The observation matrix extracts patterns and features, which are then encrypted with a random key [
73]. Some researchers employed multi-biometrics to add to existing features. These traits have been used to identify people (FV, retina, and fingerprint). The main issues with the system the author devised in [
74,
75,
76] were communication cost and computational cost.
3. Overview of Blockchain Structure
A blockchain is a decentralized, distributed ledger that is used to record transactions across a network of computers [
77]. Each block in the chain contains a record of multiple transactions, and once a block is added to the chain, it cannot be altered [
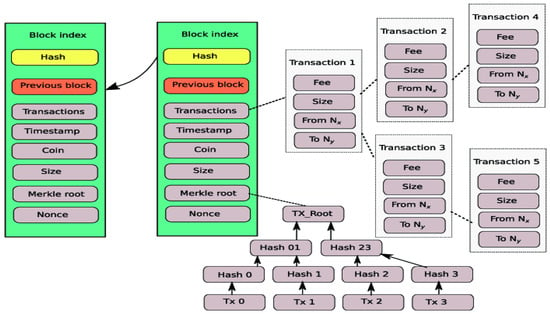
78]. This makes the blockchain a secure and transparent way to store data. As shown in
Figure 1, the data structure of a blockchain is typically a linked list of blocks, with each block containing a set of transactions. The transactions are organized using a data structure called a Merkle tree, which facilitates efficient verification of the integrity of the transactions. The data model for a blockchain is typically based on a distributed ledger model, in which the ledger is maintained and updated by a network of computers rather than a central authority. The ledger is structured as a chain of blocks, with each block containing a set of transactions and a cryptographic hash of the previous block. This structure facilitates the secure and transparent storage of data on the blockchain [
79]. In a blockchain, the data are stored in a decentralized manner, with copies of the ledger being maintained by multiple nodes on the network [
80]. This ensures that the data are secure and cannot be altered without the consensus of the network [
81]. Each transaction on the blockchain is cryptographically signed, providing a secure and verifiable record of the transaction [
82]. Overall, the data structure and data model of a blockchain are designed to provide a secure and transparent way to store and manage data in a decentralized manner.
Figure 1. The blockchain data structure.
4. IoT Data Flow
IoT data refer to the vast amount of information generated by connected devices and sensors that comprise the Internet of Things. These devices can include anything from industrial machinery and consumer appliances to vehicles and home security systems. The data generated by these devices can include a wide variety of information, such as sensor readings, GPS coordinates, usage patterns, etc.
IoT data and blockchain technology can be combined through the use of smart contracts. A smart contract is a self-executing contract with the terms of the agreement between buyer and seller being directly written into lines of code. The code and the transactions are stored on a blockchain network, making them transparent and secure. Smart contracts can be used to automate the process of collecting and storing IoT data on the blockchain, creating a tamper-proof record of the data.
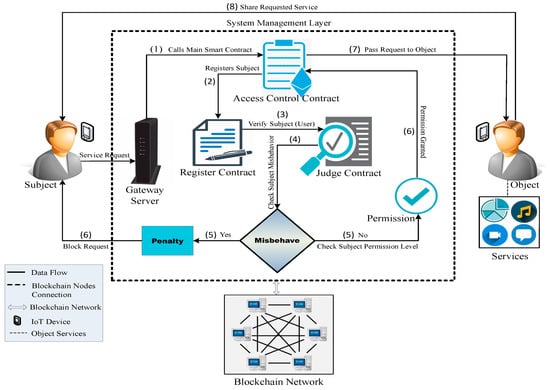
As shown in
Figure 2, one way to authenticate IoT data using blockchain technology is through the use of blockchain-based smart contracts to authenticate the data. In this model, the smart contract is programmed to verify the authenticity of the data before it is recorded on the blockchain [
31]. This can help ensure that only authentic data are stored on the blockchain, increasing the reliability and trustworthiness of the data. In this study, the use of smart contracts can help to provide a secure and verifiable way to authenticate IoT data using blockchain technology.
Figure 2. IoT using blockchain smart contracts.