
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Maurizio Capra | + 1067 word(s) | 1067 | 2020-03-27 10:49:53 | | | |
| 2 | Nora Tang | + 7 word(s) | 1074 | 2020-04-13 05:26:33 | | | | |
| 3 | Nora Tang | + 6 word(s) | 1080 | 2020-10-28 03:43:05 | | | | |
| 4 | Nora Tang | Meta information modification | 1080 | 2020-10-28 03:48:41 | | |
Video Upload Options
The growth of the number of devices connected to the Internet is steadily increasing. In the future, more and more everyday objects will host embedded electronics to make them smarter and more useful then before, under the name of Internet of Things (IoT). Most of these items will be powered by small batteries and thus will have a limited energy budget. They will have to accurately balance performances and power usage to extend their lifespan. This can be implemented at various level, from the lowest one, the technology, to the highest, the algorithm. It is not possible to send all the data to a cloud server for processing, in particular if data can be preprocessed effectively to save computational resources on the cloud and to send only useful information. This paradigm is called edge-computing, as the end devices act at the "edge" of the cloud. This survey paper presents various recent ultra-low power hardware architectures for IoT, along with the explanation of some low power techniques to make the IoT tasks possibile at the large scales required. Some newest research topics are discussed, leading to the description of a fully functional digital system which encloses all the presented techniques.
1. The Internet of Things (IoT)
The Internet of Things (IoT), coined in 1999 by Kevin Ashton, is gaining more and more attention in these years due to the increasing amount of connected devices and consequently to the amount of data. In the big data era, recording data from several environments and users is extremely valuable from a statistic as well as a business and economic point of view. Nowadays, almost every device present in everyday life presents some embedded electronics, which turns it into a potential IoT node. Indeed, IoT nodes are able to sense information and transmit it, thanks to a communication interface.
So far, the IoT paradigm had a huge impact on both consumers’ lives and business models, due to the decreasing cost of implementation of these devices and the increasing demand. The trend is expected to rapidly increase, as shown in Figure 1. Gartner [1] (world’s leading company in research and advisory fields) states that 23.14 billion of connected devices have been produced in the past year (2018), up to 30.73 billion are expected for 2020. This represents a great opportunity for investors, producers and companies to collect big data. In fact, companies are expected to spend around 5 trillion dollars in 2021 to expand the market [2] and introduce new applications, embedded in everyday gadgets.
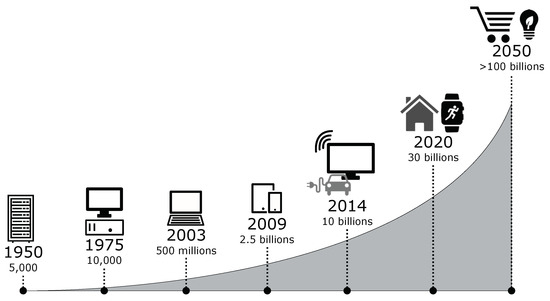
Figure 1. Expected adoption growth of IoT devices.
2. Introduce New Applications
In a highly dynamic scenario, as depicted above, the opportunities to diversify the possible solutions and applications are many. In addition, there still exists a main common factor: the hardware implementation. Indeed, hardware architectures are quite similar regardless of the final use since their organization relies very often on microcontroller-based platforms. Most IoT devices rely on batteries or energy harvesters. Given that their energy budget is limited, even the power that can be consumed will need smart energy management, driving the hardware engineering toward an ultra-low power approach. Limited power represents a huge constraint to many components of the architecture, especially the energy-hungry ones, like wireless transmitters. In such a case, communication and data to be broadcast must be reduced to the essential, which translates to low energy technology, such as Ultra-Wide Band (UWB) [3][4][5][6][7][8], and transmit only useful features by exploiting state-of-the-art techniques, like Compressing Sensing.
IoT nodes have to sense and collect data with respect to their specific task. The tasks could be many, ranging from a smart household appliance, sleep monitoring, physical activity tracking, caretaker condition monitoring, etc. Such information, collected over thousands of individuals, must ensure absolute privacy for final users. Indeed, such personal data must be kept safe from outside attacks, avoiding any hacking attempt. Even localization-based services are affected by this problem. The position is part of a privacy policy that must be prevented from threats [9]. In order to protect data, the common procedure is to encrypt the communication so that nobody can steal precious info. Device security, together with encryption techniques, are a matter of discussion and research widely spread around the globe.
Many of the aforementioned tasks, including the last one described above, can be performed directly on the platform without accessing the cloud or a remote hosting service. This considerably reduces the power needed to transmit and receive data before and after elaboration, relieving much of the effort from servers. This change of paradigm is called Edge Computing: part of the workload is decentralized and distributed among the IoT nodes, turning them from simple sensors into more powerful and smart embedded systems, capable of several new features.
Thanks to this innovative and effective approach, measured information can be further analyzed directly on the field, allowing for a more responsive application and a faster post-processing operation once data has been transmitted. Edge Computing paradigm is considered, from many, an environmentally friendlier alternative to the Cloud Computing one, due to its ability to restrain the volume of data to be moved, consequently cutting down the energy cost.
As described above, the decentralization of the workload is the focus of many works of research. The aim is to reduce the latency by offloading some of the tasks on surrounding servers [10][11]. In fact, in urban environments, it is possible to rely on such infrastructure to enhance performances. However, in order to correctly manage the workload, there is often the need to split it homogeneously and to synchronize all the different duties. To achieve this goal, something more is required, such as an Operating System (OS). The use of a complete OS instead of a limited embedded firmware becomes a powerful tool when handling complex tasks. In order to manage multiple users and different scenarios, required for IoT, the main OS can run virtualized operating systems (which emulates the entire hardware resources required by an OS) or it can exploit the containerization paradigm, which lets the user have multiple instances of the OS running at the same time while sharing the kernel for resources allocation. The containerization of tasks makes the organization and the allocation of workloads more efficient, by exploiting the bandwidth of the system at its maximum, without exceeding constraints [12]. For sake of clarity, since this current survey is focusing on hardware aspects, OS and software related technologies are not discussed in the following sections; however, the reader can refer to the provided references for further details.
References
- Gartner Website. Available online: http://www.gartner.com (accessed on 20 April 2019).
- Koustav Routh; Tannistha Pal; A survey on technological, business and societal aspects of Internet of Things by Q3, 2017. 2018 3rd International Conference On Internet of Things: Smart Innovation and Usages (IoT-SIU) 2018, null, 1-4, 10.1109/iot-siu.2018.8519898.
- Kerim Ture; Arnout Devos; Franco Maloberti; Catherine Dehollain; Area and Power Efficient Ultra-Wideband Transmitter Based on Active Inductor. Microwave Circuit Conditional Stability: Two-Parameter Criteria 2018, 65, 1325-1329, 10.1109/tcsii.2018.2853190.
- Nitz Saputra; John R. Long; A Fully-Integrated, Short-Range, Low Data Rate FM-UWB Transmitter in 90 nm CMOS. IEEE Journal of Solid-State Circuits 2011, 46, 1627-1635, 10.1109/JSSC.2011.2144050.
- Patrick P. Mercier; Denis C. Daly; Anantha P. Chandrakasan; An Energy-Efficient All-Digital UWB Transmitter Employing Dual Capacitively-Coupled Pulse-Shaping Drivers. IEEE Journal of Solid-State Circuits 2009, 44, 1679-1688, 10.1109/JSSC.2009.2020466.
- Zhe Zhang; Yongfu Li; Guoxing Wang; Yong Lian; The Design of an Energy-Efficient IR-UWB Transmitter With Wide-Output Swing and Sub-Microwatt Leakage Current. Microwave Circuit Conditional Stability: Two-Parameter Criteria 2018, 65, 1485-1489, 10.1109/tcsii.2018.2861833.
- Ming Jian Zhao; Bin Li; Zhao Hui Wu; 20-pJ/Pulse 250 Mbps Low-Complexity CMOS UWB Transmitter for 3–5 GHz Applications. IEEE Microwave and Wireless Components Letters 2013, 23, 158-160, 10.1109/lmwc.2013.2245412.
- Rui Xu; Y. Jin; C. Nguyen; Power-efficient switching-based CMOS UWB transmitters for UWB communications and Radar systems. IEEE Transactions on Microwave Theory and Techniques information for authors 2006, 54, 3271-3277, 10.1109/TMTT.2006.877830.
- Liang Chen; Sarang Thombre; Kimmo Jarvinen; Elena Simona Lohan; Anette Alén-Savikko; Helena Leppäkoski; M. Zahidul H. Bhuiyan; Shakila Bu-Pasha; Giorgia Nunzia Ferrara; Salomon Honkala; Jenna-Sofia Lindqvist; Laura Ruotsalainen; Päivi Korpisaari; Heidi Kuusniemi; Robustness, Security and Privacy in Location-Based Services for Future IoT: A Survey. Variable-length cable dynamics of payout and reel-in with a vertically tethered underwater drill rig 2017, 5, 8956-8977, 10.1109/access.2017.2695525.
- Futian Futian Wang School of Computer Science and Technology, Anhui University, Hefei, China; Xingxiang Huang; Hongfang Nian; Qiang He; Yun Yun Yang School of Software and Electrical Engineering, Swinburne University of Technology; Cheng Zhang; Cost-Effective Edge Server Placement in Edge Computing. Proceedings of the 2019 5th International Conference on Systems, Control and Communications 2019, 127, 160–168, 10.1145/3377458.3377461.
- Muhammad Rizwan Anwar; Shangguang Wang; Muhammad Azam Zia; Ahmer Khan Jadoon; Umair Akram; Salman Raza; Fog Computing: An Overview of Big IoT Data Analytics. Wireless Communications and Mobile Computing 2018, 2018, 1-22, 10.1155/2018/7157192.
- Liu, J.; Wang, S.; Zhou, A.; Yang, F.; Buyya, R. Availability-aware Virtual Cluster Allocation in Bandwidth-Constrained Datacenters. IEEE Trans. Serv. Comput. 2018, 1. [Google Scholar] [CrossRef]




