Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Saja Theab Ahmed | -- | 6241 | 2023-08-25 22:11:53 | | | |
| 2 | Jason Zhu | Meta information modification | 6241 | 2023-08-29 04:04:54 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Ahmed, S.T.; Hammood, D.A.; Chisab, R.F.; Al-Naji, A.; Chahl, J. Techniques of Image Encryption For Medical Applications. Encyclopedia. Available online: https://encyclopedia.pub/entry/48499 (accessed on 08 February 2026).
Ahmed ST, Hammood DA, Chisab RF, Al-Naji A, Chahl J. Techniques of Image Encryption For Medical Applications. Encyclopedia. Available at: https://encyclopedia.pub/entry/48499. Accessed February 08, 2026.
Ahmed, Saja Theab, Dalal Abdulmohsin Hammood, Raad Farhood Chisab, Ali Al-Naji, Javaan Chahl. "Techniques of Image Encryption For Medical Applications" Encyclopedia, https://encyclopedia.pub/entry/48499 (accessed February 08, 2026).
Ahmed, S.T., Hammood, D.A., Chisab, R.F., Al-Naji, A., & Chahl, J. (2023, August 25). Techniques of Image Encryption For Medical Applications. In Encyclopedia. https://encyclopedia.pub/entry/48499
Ahmed, Saja Theab, et al. "Techniques of Image Encryption For Medical Applications." Encyclopedia. Web. 25 August, 2023.
Copy Citation
In medical information systems, image data can be considered crucial information. As imaging technology and methods for analyzing medical images advance, there will be a greater wealth of data available for study. Hence, protecting those images is essential. Image encryption methods are crucial in multimedia applications for ensuring the security and authenticity of digital images.
medical image encryption
security
E-healthcare
chaotic map
ECC
DNA
PQC
lightweight cryptography
1. Introduction
Here presents a taxonomy of image encryption techniques. Compressive sensing, optical encryption, spatial encryption, and transform domain encryption are the four primary categories that are used to classify image encryption techniques. Various methods of encrypting images are categorized in Figure 1. Several cryptographic processes can be used to ensure that medical images are transferred securely and cannot be intercepted [1]. As a result of their widespread popularity, the three methods employed because they are achieving the following goals in the field of medical image encryption:
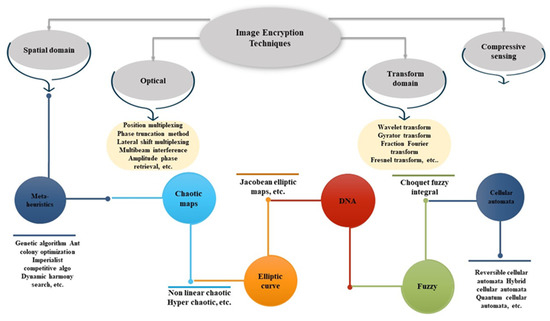
Figure 1. A taxonomy of image encryption techniques.
For chaotic maps:
-
Safety: According to the theory of chaos, the state of a chaotic system can change drastically depending on its initial conditions. Encryption algorithms with high resilience to attacks can be designed by making use of this unpredictability and complexity. In order to improve the security of the encryption process, chaos-based encryption methods seek to utilize the chaotic behavior of mathematical models to either produce encryption keys or directly change the medical imaging data.
-
Nonlinearity: Medical photos frequently feature complex structures and patterns that might be difficult to encrypt using linear methods. The nonlinear approach provided by chaos-based encryption algorithms makes it possible to encrypt medical image information in a more safe and reliable fashion. Complexity can be introduced by the chaotic dynamics, making it more difficult for an adversary to decipher the encryption.
-
Resistance to Statistical Attacks: Healthcare images frequently display statistical regularities or patterns that could be used maliciously. To protect its encrypted data from statistical attacks, chaos-based encryption techniques might inject a large amount of unpredictability.
For ECC:
-
Key Size Efficiency: ECC provides the same or more security than other encryption methods like RSA but with more manageable key sizes. This is helpful for protecting medical photos, which often measure in gigabytes and require speedy encryption and decryption procedures. ECC is a useful option for protecting medical images since its smaller key sizes allow for faster computations, and less storage space is needed.
-
Scalability: It is common for medical imaging equipment to require the transmission and storage of several images. With ECC encryption methods, massive datasets can be encrypted and decrypted quickly and efficiently, allowing for scalability. ECC’s faster computations and reduced key sizes make it possible to encrypt and handle large numbers of medical images without compromising security.
-
Regulatory Compliance: HIPAA (Health Insurance Portability and Accountability Act) compliance is essential in the healthcare sector because of the sensitive nature of patient information. Several government agencies have acknowledged ECC as a secure encryption method. When used to encrypt medical images, it aids institutions in fulfilling regulatory mandates for keeping patient information secure.
For DNA:
There are various potential motives and benefits for adopting DNA encryption techniques in medical image encryption:
-
Security: Due to the unique properties of DNA, methods of DNA encryption can provide high levels of security. DNA-based encryption methods use the randomness and complexity of DNA sequences to encrypt and decrypt data. This protects the confidentiality of the patient’s information by making it incredibly challenging for hackers to crack the encryption on medical photos.
-
Scalability: DNA has a huge storage capacity, enabling the compact storage of massive amounts of data, such as medical images. Because of their potential size, high-resolution medical images benefit greatly from this scalability’s encryption protection. The secure storing and encryption of massive volumes of visual data is a breeze for DNA-based encryption technologies.
-
Robustness: DNA is a robust medium for long-term data storage since it is unchanging and resistant to external influences. DNA encryption technologies can protect the quality and endurance of encrypted data, making them ideal for archiving medical imaging for long periods of time.
-
Biocompatibility: DNA encryption techniques are excellent for medical applications since they are compatible with living systems. DNA-based encryption techniques, for instance, can provide a biocompatible and non-toxic solution for the safe transmission and storage of medical pictures within the human body.
-
Emerging Technology: DNA-based encryption techniques are an innovative and cutting-edge approach to data security. Researchers and practitioners in the field of medical image encryption can push the boundaries of the discipline and make significant contributions to the development of both encryption and medical imaging by incorporating such technologies.
DNA encryption technologies are still in the experimental stages of development and application. Although they hold promise for the future, additional research and development are necessary to completely comprehend their potential benefits and challenges in the context of medical image encryption.
For PQC
One of the key reasons for opting for Post-Quantum Cryptography (PQC) encryption methods is the expectation that quantum computers may one day be developed. Classical computers process and store information using binary digits (bits), but quantum computers employ quantum bits (qubits), which can be in more than one state at once. For some mathematical problems, such as those at the heart of many popular encryption techniques, quantum computers may be able to find solutions significantly more quickly than classical ones, thanks to their intrinsic parallelism. Researchers and security experts have been investigating and creating PQC encryption ways to counteract this immediate danger. PQC methods are designed to protect data in the long term from being compromised by either classical or quantum computers.
As a result of this, there is a heightened interest in learning more about these methods.
2. Encryption Based on Chaotic Maps
Given their behavior, chaotic maps are of particular interest in dynamic systems. This means that even a seemingly minor shift in the inputs might have a significant impact on the results. There are two main types, called discrete and continuous, respectively. Because of their advantageous balance of security and processing speed, chaotic maps see widespread use in various communication scenarios [2]. Figure 2 represents the chaotic image encrypting process [3].
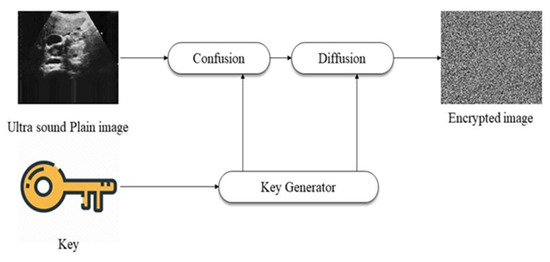
Figure 2. The encryption of images using chaotic maps [3].
The author in [4] used a method for the double encryption of images that was based on chaos to provide high security. The first step was encrypting the face extracted from the image, and the second encryption of the entire image. 2D SFSIMM (Two-dimensional hyperchaotic map, sinusoidal feedback Sine ICMIC modulation map) is responsible for generating the keystream for the cryptosystem. At the same time, both scrambling and diffusion were proposed. This technique is robust against various statistical attacks since the attacker needs to crack two rounds of the encryption algorithm.
In [5], to encode and decode images securely, a new cryptosystem based on three maps has been developed. The sine map is used in the permutation technique to adjust the coordinates of the pixels in the source image, while the substitution is performed on the permuted image using the second secret key K. Lastly, the CTM-based image scrambling is performed with a bit XOR.
A developed technique for chaotic image encryption using Latin squares and random shifts was suggested in [6]. Four steps comprise the algorithm: creating a key, scrambling pixels, swapping out pixels, and scrambling bits. The security and robustness of the procedure are both improved by increasing the resulting Latin square matrix’s complexity. In order to increase the high sensitivity of the cryptography approach, the key is first produced from the plain image. The second step in achieving pixel position scrambling is to cyclically shift each pixel to the right within each row of the image matrix. Then, the image matrix’s coordinate elements are replaced by the results of a lookup table comprised of a 256-by-256 Latin square matrix containing a chaotic sequence, with replacement coordinates determined depending on the values of the image’s pixels and the sequence’s values. The implementation of a multimedia encryption technique is difficult since it takes more resources (time and storage). Due to this, the lightweight image encryption technique, which uses minimal memory, time, or energy and offers the highest level of security for low-powered devices, is becoming more and more popular.
Therefore, a study by Ferdush et al. [7] studied the lightweight image encryption approach that was based on chaos. As a first step, the author developed a standardized approach and method for lightweight image cryptography based on two different chaotic maps, specifically Arnold and Logistic.
Another study [8] discussed the modification of pixel values and positions based on the SCAN algorithm and chaotic theory. The SCAN method includes converting the pixel value of an image to a new pixel value and then rearranging the pixels in the image in a specific order. Meanwhile, within the block, the coordinates of the pixels can be moved about with the use of a chaotic map. Pixels are diffused using the SCAN method, while permutations are generated using chaotic maps. Since limitations of wavelet-based approaches include insufficient phase information, inadequate directionality, and sensitivity to shifts.
Another study [9] applied (ICE) Improved Chaos Encryption to strengthen the protection that was based on randomization. The ICE approach was employed to increase the medical encryption’s level of security. ICE first partitions the original image into three parts which were: border area, (ROI) Region of interest and (RONI) Region of noninterest. The Lorenz 96 model was applied for medical image encryption. The information would be embedded based on LSB.
In order to guarantee the authenticity of the integrity authentication, ROI has been recovered and returned to its starting position. S-HC-DNA in [10] was an upgraded image encryption scheme to increase the protection afforded to medical images during information-sharing procedures, such as those conducted over the internet. The SHA-3 technique was utilized to compute the hash value of the input image, and the resulting value was utilized as the starting point for the hyper-chaotic system. The input image’s intensity value was then transformed into a sequential binary digital stream. In order to improve the encryption performance, the values of the DNA encoding were subjected to algebraic and complementary operations during the hyperchaotic sequence and DNA sequence operation.
The SCAN pattern and tent map are also proposed in [11]. The method consists of a bit plane decomposition, a SCAN-based shuffling process, and a diffusion operation. In order to obtain a more unpredictable result, the SCAN method was implemented on both the upper and lower four-bit planes independently. After that, the XOR operation would be included in the diffusion operation.
Securing E-healthcare image encryption based on a six-dimensional hyperchaotic map (SDHM) was suggested in [12]. This scheme was used to retrieve hidden keys. After that, these keys were applied to the medical images to diffuse them. In general, the proposed SDHM was divided into three sections: the creation of a key, the encrypting procedure, and the decrypting procedure. The key size has been greatly expanded due to the SDHM that was proposed. Thus, the SDHM that has been presented was capable of withstanding various security attacks.
In [13], the author proposed a chaotic-based cryptography architecture for the secure storage and transmission of medical images. The key was first generated by employing the chaotic map approach on the medical image. This produced the initial result. Second, it was implemented in a way that creates confusion both row by row and column by column. In addition, a binary complement operation and a reverse complement operation were used to complete the diffusion process. Images that have been diffused were XORed with key images that have a chaotic appearance. Several attacks were used to evaluate the proposed system’s security. According to the simulation results, the created cryptosystem must meet the needs of IoT healthcare applications.
Another study [14] suggested a method for encrypting medical images using chaotic logistic maps and linear feedback shift registers to produce pseudo-random sequences, which were then utilized to form a cipher key by being XORed together. The suggested approach protected several different medical image formats from a wide range of threats.
In [15], the authors presented a novel image encryption algorithm that could be used for both gray and colored medical images. The authors claimed that their algorithm was superior to current encryption methods that were already in use.
The authors in [16] designed a selective image encryption algorithm that was both secure and effective. The encryption method was designed with the foundations of polynomial secret picture sharing and chaotic maps. A polynomial-based secret image sharing (SIS) and a chaotic map system are used to encrypt the essential component of the ROI after image processing techniques are employed to partition the image into a region of interest (ROI) and a region of non-interest (RONI). In order to reduce the amount of time spent encrypting and decrypting data, as well as the amount of computing complexity involved in processing the enormous amount of image data, a preset section of the original image data were encrypted. The experimental results demonstrated the efficiency of Polynomial-based SIS and chaotic image encryption for the concealment-critical tasks of diffusion and confusion, respectively.
A new, most significant bit (MSB) based reversible data encryption solution for huge amounts of data is proposed in [17]. In the first step, the encrypted domain data undergoes MSB data concealing after the three stages of prediction error detection, fusion error encryption, and substitution data encryption have been taken into account. As a result, the initial phase of the method involves locating and cataloging every instance of incorrect prediction in the source image using a binary map. Then, to fix the mistake in the predictions, a high-capacity reversible data hiding technique (CPHCRDH) is proposed. A map of where mistakes are likely to occur in the prediction process is created, and the original image is preprocessed using this map before encryption takes place. Through MSP prediction, the original, undamaged image can be rebuilt. The simulation experiment on three test cases of CT images of the eyes, body, and brain demonstrates that the suggested method outperforms the selected contrasting methodology across six indicators, including the horizontal and vertical correlation coefficients.
Introducing 2D-LGHM, a brand new Logistic-Gaussian hyperchaotic map in [18]. First, the author builds a 2D Logistic-Gaussian hyperchaotic map (2D-LGHM) with a wide variety of hyperchaos and it finds that it has superior ergodicity and unpredictability based on performance test metrics.
3. Encryption Based on Elliptic Curve Cryptography (ECC)
The characteristics of algebraic curves serve as the foundation for the construction of elliptic curves. The use of an elliptic curve was integral to the creation of a public key encryption method by Koblitz and Miller. Elliptic curve encryption’s main advantages are its low key size and high processing efficiency [19]. The function of an elliptic curve within an image encryption is illustrated in Figure 3 [3].
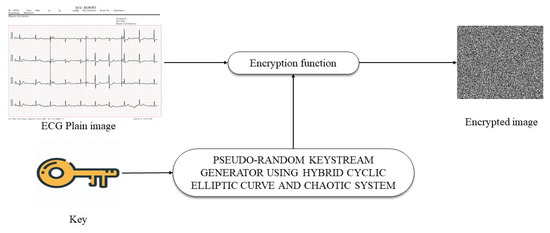
Figure 3. The encryption of images using ECC [3].
In [20], an existing encryption system that was created with elliptic curve cryptography (ECC) and a Hill cipher was analyzed through the process of cryptanalysis. Affine Hill ciphers were utilized to spread the original image matrix into 4 × 4 blocks, which were then employed as keys in the scheme. Most importantly, the selected elliptic curve was used to construct the chaotic map’s primary parameters. Bit-wise XOR was then performed with the produced Arnold map sequence on top of the scrambled data. According to the results of the research, the current system was insecure and could be broken by a brute-force attack.
ECC also proposed in [21] as a security for medical images in the IoT which was proposed by combining visual cryptography and Optimal Elliptic Curve Cryptography (IoT). Using an imperialist competitive algorithm, the best possible key was constructed. The ESEA strategy that has been presented shortens the amount of time needed to upload files and cuts down on the amount of memory that was consumed by encryption. The simulation results showed that the suggested system had a good chance of achieving the optimal global solutions faster and more precisely than the current methods.
In [22], the authors discussed a new cryptographic approach for protecting medical images created by IoHT healthcare devices by applying an advanced optimization technique, based on elliptical curves and Grasshopper Particle Swarm Optimization (GOPSO) to choose the best possible key to protect medical images. Compared to previous optimal encryption methods, the study’s findings showed that the proposed algorithm was secure and resistant against a wide range of assaults. The results of the experiments demonstrate increased sensitivity of the keys, improved accuracy of the encryption, and excellent resistance to statistical attacks.
The authors discuss a novel cryptographic method for securing medical images that rely on Hill cipher in conjunction with ECC (ECCHC). The authors employ this strategy to overcome the vulnerability of certain encryption techniques to specific attacks and the difficulty of using a key length that is resistant to brute-force methods of decryption. The ECCHC scheme was found to be secure and perform better than competing schemes through extensive testing and research.
A homomorphic encryption method based on an elliptic curve was presented in [23] for use with medical images. The author used the improved ECC to bring about the addition homomorphism and the multiplication homomorphism. It has recently been demonstrated that cryptosystems based on ECs over finite rings may offer higher security than those based on other algorithms, such as the factorization problem or the discrete logarithm problem.
Prompted by this realization, a fresh approach to cryptography based on ECs over finite rings was introduced in [24]. The approach consists of three primary phases, the first of which involves masking the simple image with points of an EC across a finite ring. Step two involved generating diffusion within the masked image by transferring the EC through the finite ring to the EC over the finite field. In order to produce a large amount of confusion in the plain text, the author first constructed a substitution box (S-box) based on the ordered EC. This box was then used to permute the pixels of the diffused image to produce a cipher image.
Upgraded image encryption using MAES-ECC was developed for use in embedded systems in [25]. This technique employed a modified variant of AES in which the mix column transformation phase was replaced with a permutation-based shift of columns, resulting in reduced temporal complexity while maintaining the Shannon principle of diffusion and confusion.
Using the elliptic curve cryptosystem and the hill cipher, the author of [26] created a robust image encryption technique. Hill Cipher transforms a symmetric encryption method into an asymmetric one, making it more secure and resistant to attacks. In this technique, the burden of locating and disseminating the inverse key for decryption was eliminated by using a self-invertible key matrix for the purpose of encrypting and decrypting confidential information. Intruders would have a difficult time deciphering this strategy because the key matrix that used was based on ECC. The results of the simulation have shown that the method was effective in both protecting against a variety of attacks and saving time.
The author in [27] used a moving S-box and a random additive mask to encrypt images. The approach used two methods: the first was the use of random nonce and safe hash algorithm in computing per-image Henon map setup, and the second was the use of elliptic curve encryption in securing the secret key. The suggested approach achieved encryption speeds that were close to 60 MB/s due to its excellent computational efficiency.
In [28], the study sought to accomplish two goals at once. First, by establishing a total order on an EC over a prime field, the author introduced new techniques for building s-boxes and generating pseudo random numbers (PRN). The second component was a two-phase image encryption system that was based on the recently established s-box and PRN generating method. The plain-image would be first confused by a suggested PRN, which was then masked by a fully dynamic S-box in this security system. This process began by diffusing the plain-image. The proposed methods were capable of constructing cryptographically robust S-boxes and PRNs with high entropy and excellent resistance to contemporary image cryptanalysis.
4. Encryption Based on DNA (Deoxyribonucleic Acid)
Deoxyribonucleic acid (DNA) technology has recently touched many fields, including the medical system, information science, etc. Information was stored in DNA molecules, which carry genetic code that could be converted from one form to another. Pseudo-DNA technology was a simulation environment for DNA-based biological experiments recently developed by scientists. DNA encryption has been advanced by this idea [29].
The DNA-based image encryption mechanism is depicted in the block diagram found in Figure 4 [3]. The first step was to separate the image into its individual color channels: red (R), green (G), and blue (B). Each of these three channels was converted into a binary matrix. These matrices were subsequently encoded according to the rules of DNA encoding. DNA operations were performed on the encoded matrices, which scrambled the similarity between pixel values. Applying the decoding rules results in a new set of binary matrices. Eventually, a cipher-colored image was created by combining these three color channels [30].
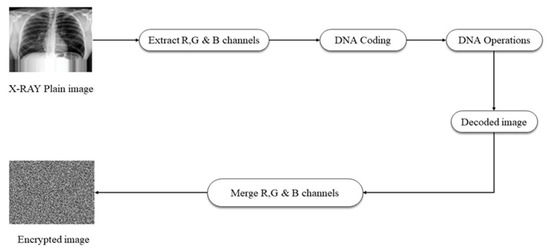
Figure 4. The encryption of images using DNA [3].
In [31], a method for encrypting images using DNA coding and annealing was presented as a possible solution. The image pixels were modified with the chaotic system’s pseudo-random number sequence by adding the mutation step to the conventional scrambling and diffusion framework. This outcome was in an image that was more difficult to decipher. There was an 80% probability that every pixel would have just one bit reversed and a 20% chance that every bit would be reversed. Authors generated ciphertext images by applying the same encryption approach to the RGB, YC, and BG channels of a color image.
To secure sensitive medical images, a new cryptosystem is presented in [32]. Using DNA sequencing, Knight’s trip map, intertwining chaotic maps, and affinity transforming. First, a B1 pixel DNA-coded matrix is created from the original medical image. The remaining pixels in matrix B2 were deployed on the pixel index values selection using DNA coding. After that, the system and control parameters generated chaotic sequences, which were depicted as a through-like pattern in the chaotic map. The performance analysis results showed that the suggested DMIES effectively reduces the risk of attacks like differential cropping, exhaustive probing, noise, and statistical analysis.
In [33], The image was encrypted using three different stages: one phase of confusion and two phases of diffusion. In the first stage of diffusion, DNA XOR was used to partially encrypt the image by operating on DNA-encoded image pixels and a hyperchaotic sequence. The next step involved using a Baker map to scramble the placements of each pixel in the partially encrypted image. A two-dimensional discrete cosine transform (DCT) was applied to the image in the diffusion phase, which converted the information from the spatial domain to the frequency domain. Due to its key sensitivity and resistance to various crypt-analytic attacks, the proposed algorithm demonstrated a high level of security.
For medical image encryption, Ref. [34] suggested system combines the hyperchaotic RKF-45 random sequence with DNA computation. The suggested framework used the RKF45 approach to generate chaotic sequences. After that, a 4-dimensional hyperchaotic integration was used to produce a random key sequence. The proposed framework cipher’s unpredictability and efficiency were also improved by adopting DNA addition and subtraction operations. According to the findings, the suggested HC-RK45-DNA framework could withstand differential attacks.
A new DNA-based medical image encryption method and a 3D unified chaotic system were presented in [35] to increase the safety of medical image storage. In the beginning, a key value was constructed by using the input image for the sake of avoiding specific plaintext attacks. The execution of the chaotic system and its starting values were determined by this freshly produced key value. Here, a chaotic system was driven to generate a pseudorandom sequence that could be used for image scrambling and diffusion, as well as for converting pixels to DNA bases. The DNA bases were then converted and decoded using straightforward reversible methods. First, random numbers were used to swap out DNA bases, and then the bases were decoded to produce a new pixel value.
An image steganography scheme based on DNA was proposed in [36]; the proposed method involved encrypting the image to be concealed by using a DNA tape as a key, which was agreed upon by both parties, executing the hybridization process, and performing the hiding process in a different way, also dependent on the same key. In addition, the proposed method included performing the hybridization process. Implementing the BIO-XOR procedure between the DNA strand created in the previous stage and another DNA strand follows the hybridization process for the sequence of nitrogenous bases. The author in [34] presented a keyless process that helps to increase the unpredictability of the original image. The suggested approach used a generalized version of Arnold’s Cat Map to add to the chaos. Additionally, a new diffusion mechanism has been implemented, and it worked on two different levels: the pixel level and the DNA plane. It included all potential DNA encoding, decoding, and XOR rules, chosen in a random-ish fashion according to the values of a chaotic 2D-Logistic Sine Coupling Map. This strengthened the cipher image against brute force and statistical attacks, and it became complicated for an intruder to decipher the cipher and see the original image without the correct key.
The proposed algorithm for medical image encryption in [37] used 2D-LSCM. In the formulated cryptosystem, 2D-LSCM performed the primary confusion-diffusion. The algorithm suggested a new masking strategy, which was one that did not require a key. In order to increase the entropy of the image, this step was performed before the confusion and diffusion process. The number of iterations in the ACM-based confusion stage has been optimized to produce a heavily garbled image while avoiding periodicity. The most crucial part of this cryptosystem was the diffusion algorithm, which modified the image’s pixel values at both the bit and pixel levels.
Hyper chaos and DNA encoding were introduced in [38]. It consisted of four stages, which were the formation of starting values of a chaotic system, the generation of key streams, scrambling, and diffusing. The suggested approach provided the following benefits. The first step was to extract ROI images and encrypt select crucial pixels. It could decrease the total amount of encryption pixels, which would assist in reducing the encryption time. Second, in order to lower the pixel correlation, hyperchaotic sequences were implemented. Lastly, because of the utilization of DNA encoding, it was possible to save resources that were used for computational storage.
A selective digitalization of medical images utilizing dual hyper chaos maps and DNA sequencing were proposed as methods of image encryption in [39]. First, a DNA-encoded matrix C1 was created from the selected pixels in the original medical digital image by applying all DNA rules depending on the pixel index value, and a DNA-encoded matrix C2 was created from the remaining pixels. The parameters and system elements of the dual hyperchaotic map were used to generate the chaotic sequences. Selected pixels of the DNA-encoded matrix, C1, were scrambled using the dual hyperchaotic map. The DNA XOR method was used to combine the DNA-encoded matrix C1 that has been scrambled with the DNA-encoded matrix C2. After applying all of the DNA decoding rules to the combined DNA-encoded matrix, the resulting binary image was transformed to grayscale to produce the cipher image.
The authors in [40] proposed a DNA masking combined with the Secure Hash Algorithm (SHA-2) in a hybrid model. With the purpose of making the diffusion process more effective, a hybrid chaotic function was applied. DNA XOR was used in the confusion step. In order to produce one-time keys from plain images and secret hash keys, the Secure Hash Algorithm 2 (SHA-2) was employed. The encryption key was this hash value. The pixels were shuffled using random sequences as part of the diffusion process. Random sequences were produced using the chaotic hybrid map. These sequences were utilized to randomize the image. In order to confuse things, authors used DNA XOR to scramble the original image’s pixel values.
The suggested system in [41] consisted of a transmitter and a receiver that were responsible for performing the tasks of encrypting and decrypting, respectively. Despite their different functions, both components had the same structure design with two effective modules, which were: A Content-Aware Permutation and Diffusion Module and a Random-DNA-Encoding Module. The former constructed a random encryption rule selector in the DNA encoding process, which boosted security by constructing an abundance of random mappings from image pixels to calculations and significantly increased key sensitivity. The second part of the program created a permutation sequence that did more than save the values of individual pixels—it also disrupted the strong association between neighboring pixels within the same patch.
5. Encryption Based on PQC (Post Quantum Cryptography)
This means algorithms for cryptography that are guaranteed to be secure even when attacked by quantum computers. As a result of their superior speed in performing specific mathematical operations compared to conventional computers, quantum computers pose a threat to several of the currently-used cryptographic techniques, such as RSA and elliptic curve cryptography (ECC). Traditional cryptographic methods that rely on the hardness of mathematical problems, such as integer factorization or discrete logarithms, are vulnerable to quantum computers, despite the former’s impressive computational capacity for particular issues. Shor’s algorithm [42] is just one example of a quantum algorithm that can efficiently address these challenges, which undermines the credibility of many currently used cryptographic systems. Post-quantum cryptography can be accomplished using a variety of methods, including the following:
-
Lattice-based cryptography: Many methods used in post-quantum cryptography can be reduced to solving lattice problems. Certain difficulties in addressing issues on high-dimensional lattices are the basis for these algorithms. Regev proposed the first standard LWE-based lattice-based encryption technique in [43]. Using quantum processing, this approach factors huge integers by equating their prime number phases expressed as sine waves. This is an important step toward addressing the discrete logarithm issue, which is the focus of many modern cryptographic algorithms [44].
-
Code-based cryptography: In order to generate secure cryptographic protocols, code-based cryptography makes use of error-correcting codes. These methods are built on the fact that deciphering random linear codes is extremely difficult. Two relatively straightforward Code-based cryptographic methods bear Robert McEliece’s name and Harald Niederreiter [45].
-
Multivariate cryptography: Cryptographic schemes in multivariate cryptography are founded on systems of multivariate polynomial equations. These schemes are secure because of the difficulty in solving systems of polynomial equations.
A new method for hiding information in medical images employing quantum walking, 3-dimensional chaotic systems, and a modified PSO algorithm is introduced in [46]. The method proposed here involves incorporating a private medical photograph into a publicly-available cover photo. The customized PSO algorithm is run using a 3-D chaotic system and quantum walks, and the generated velocity sequence is used to replace the secret data, while the position sequence is used to choose which location in the carrier image will be used to host the substituted confidential data. This form of image steganography can be applied to both black-and-white and colored photos. A PSNR of 44.1 is achieved on average with the introduced technique, and its embedding capacity is 2 bits per byte.
Quantum selective encryption is being studied as a potential new way of protecting sensitive medical images in [47]. By performing operations on the bit-planes of the images in accordance with a key, the suggested approach successfully encrypts ROI (also known as a region of interest). For a BRQI (Bitplane Representation of Quantum Image) with 2n pixels and a key length of m, researchers have estimated the time complexity of the introduction approach, which offers a huge improvement over its traditional equivalent. In contrast to the time constraints, the size of medical images has no bearing on the method.
In order to ensure the safety of quantum-encrypted medical images, the authors of [48] presented a novel framework. Before being encrypted using the suggested method and sent to the cloud, patient photos are first converted to a NEQR (Novel Enhanced Quantum Representation) representation at a central site. The suggested technique employs a three-step encryption process for its various stages of operation. Quantum-controlled picture preparation, Select secret map keys, and Quantum picture encryption using a scrambled state.
Encryption and decryption of medical images using symmetric cryptography with a chaotic map and a key generator (KG) based on quantum mechanics presented in [49]. The three main phases of the technique are, first, the production of random cipher codes; second, the training of an encryptor and a decryptor based on gray relational analysis (GRA); and finally, the assessment of the encrypted image. To generate cipher codes for substituting values of pixels (substitution technique) in a 2D image using 256 key-space cipher codes, the chaotic map is combined with a quantum-based key generator (KG) to boost the chaotic complexity and unexpected levels.
The GRA models 1 and 2 are used to train the cipher codes for an encryptor and a decryptor, respectively. A method for quantum watermarking of images is proposed in [50]. Arnold’s cat map is used in this approach to introduce chaos into the enlarged watermark. The presented technique relies on the encrypted secret image and the controlled-“NOT” image, both of which are derived from the logistic map. The embedding procedure generates a key matrix that plays a crucial role in improving visual quality but is also utilized to bolster security. In the process of extraction, in addition to the key matrix, control parameters are necessary in order to operate the logistic map.
An original quantum LSB For quantum images of color, a steganographic technique based on the Gray code, has been developed by the authors in [51]. The described data concealing technique makes use of the gray code to conceal a 2m × 2m grayscale image within a 2n × 2n colored image (the “secret image” and “cover image,” respectively). In advance of the embedding process, a quantum Hilbert image scrambling technique was used to encrypt the hidden image. Since the key is short, it can be quickly and readily transmitted across the quantum transitional channel from sender to recipient.
Also, A strong protocol for quantum watermarking that employs both the least significant and most significant bits is proposed in [52]. Extraction of the watermarked image using the present protocol is more secure since it requires the production of two key images (scrambling key). Using a novel scrambling technique, the grayscale watermark image is transformed into a scrambled binary image that guarantees the original watermark image cannot be recovered by any attacker, even if the attacker recovers the scrambled binary image. The results of the simulation that were given reveal a superior peak-signal-to-noise ratio, which demonstrates that the cover image undergoes fewer changes while the method is being performed.
Ref. [53] proposed a strategy for quantum steganography that makes use of the two LSQb to conceal a picture with dimensions of 2n1 × 2n1 within one of dimensions 2n × 2n. The proposed technique has good visibility and high capacity, and it does not require the original cover image or original secret image for the extraction process.
The author has shown the first working version of the Ed448 DSA protocol in [54], which is designed to run on the ARM-based Cortex-M4 processor found in many low-end devices. The evaluation findings of the performance are based on the implementation design using only C code and the assembly language for the specific target being evaluated. Finally, the achieved performance describes that the design is resistant to fault and side-channel attacks.
The first implementation of HPKE is immune to the problems that quantum computers pose for asymmetric algorithms introduced in [55]. Using two different postquantum key encapsulation strategies and a wide range of plaintext sizes, researchers evaluate the efficacy of PQ-only and PQ-hybrid HPKE variants. The system has been expanded to enable both PQ-only and PQ-hybrid choices, and it has been merged with two PQ KEM algorithms that were developed during Round 3 of the PQ Project by NIST.
Ref. [56] provides a study of the energy needed to run potential PQC algorithms using data collected from extensive testing on a Cortex M4-based reference platform. The data transmission costs of PQC algorithms, which are predicted to rise with the introduction of novel public keys and ciphertext encodings, are related to their computational (energy) costs. The author discovers that even with existing radio technology, and especially with 5G’s increased transmission speeds, the post-quantum transition can imply energy savings over present ECC cryptography. There will still be applications that require ECC that can’t easily accommodate the lengthier messages required by the PQC alternatives (or RSA), but this isn’t an issue with TLS.
The NIST-recommended platform for benchmarking post-quantum secure protocols, the STM32F407VG, was the focus of the author’s first implementation of compressed SIKE in [57]. By expanding the stack and adding a new memory region in the CCM RAM, researchers were able to run compressed SIKEp610 without risking memory corruption. To further improve the speedup, researchers write assembly code subroutines for subtraction and multiplication with compressed data.
The research [58] detailed a variety of optimization strategies for efficiently deploying KyberKEM on 64-bit ARM CPUs. In order to reduce the amount of time needed for the execution, the author suggested optimizations for the basic operations of Kyber and symmetric functions. Key generation, encapsulation, and decapsulation were all enhanced by 1.72×, 1.88, and ×2.29, respectively, in comparison to prior works using the planned Kyber512 implementation on ARM64. Additionally, the suggested Kyber512-90s implementation is enhanced by 8.57×, 6.94×, and 8.26× when employing an AES accelerator for key generation, encapsulation, and decapsulation, respectively.
References
- Jebur, R.S.; Der, C.S.; Hammood, D.A. A Review and Taxonomy of Image Denoising Techniques. In Proceedings of the 6th International Conference on Interactive Digital Media (ICIDM), Bandung, Indonesia, 14–15 December 2020; pp. 1–6.
- Gu, G.; Ling, J. A fast image encryption method by using chaotic 3D cat maps. Optik 2014, 125, 4700–4705.
- El-Latif, A.A.A.; Niu, X. A hybrid chaotic system and cyclic elliptic curve for image encryption. AEU-Int. J. Electron. Commun. 2013, 67, 136–143.
- Cheng, Z.; Wang, W.; Dai, Y.; Li, L. A High-Security Privacy Image Encryption Algorithm Based on Chaos and Double Encryption Strategy. J. Appl. Math. 2022, 2022, 9040702.
- Kanwal, U.S.; Inam, S.; Hajjej, F.; Cheikhrouhou, O.; Nawaz, Z.; Waqar, A.; Khan, M. A New Image Encryption Technique Based on Sine Map, Chaotic Tent Map, and Circulant Matrices. Secur. Commun. Netw. 2022, 2022, 4152683.
- Zhang, X.; Wu, T.; Wang, Y.; Jiang, L.; Niu, Y. A Novel Chaotic Image Encryption Algorithm Based on Latin Square and Random Shift. Comput. Intell. Neurosci. 2021, 2021, 2091053.
- Ferdush, J.; Begum, M.; Uddin, M.S. Chaotic Lightweight Cryptosystem for Image Encryption. Adv. Multimedia 2021, 2021, 5527295.
- Kiran, K.; Gururaj, H.L.; Almeshari, M.; Alzamil, Y.; Ravi, V.; Sudeesh, K.V. Efficient SCAN and Chaotic Map Encryption System for Securing E-Healthcare Images. Information 2023, 14, 47.
- Rashmi, P.; Supriya, M.C.; Hua, Q. Enhanced Lorenz-Chaotic Encryption Method for Partial Medical Image Encryption and Data Hiding in Big Data Healthcare. Secur. Commun. Netw. 2022, 2022, 9363377.
- Li, M.; Pan, S.; Meng, W.; Guoyong, W.; Ji, Z.; Wang, L. Medical image encryption algorithm based on hyper-chaotic system and DNA coding. Cogn. Comput. Syst. 2022, 4, 378–390.
- Roitblat, H.L. Recent Advances in Artificial Intelligence; MIT: Cambridge, MA, USA, 2020.
- Jain, J.; Jain, A. Securing E-Healthcare Images Using an Efficient Image Encryption Model. Sci. Program. 2022, 2022, 6438331.
- Rajendran, S.; Doraipandian, M. Chaos Based Secure Medical Image Transmission Model for IoT- Powered Healthcare Systems. IOP Conf. Ser. Mater. Sci. Eng. 2021, 1022, 012106.
- Harshitha, M.; Rupa, C.; Pujitha Sai, K.; Pravallika, A.; Kusuma Sowmya, V. Secure Medical Multimedia Data Using Symmetric Cipher Based Chaotic Logistic Mapping. In Proceedings of the 2021 International Conference on System, Computation, Automation and Networking (ICSCAN), Puducherry, India, 30–31 July 2021; pp. 476–481.
- Kamal, S.T.; Hosny, K.M.; Elgindy, T.M.; Darwish, M.M.; Fouda, M.M. A New Image Encryption Algorithm for Grey and Color Medical Images. IEEE Access 2021, 9, 37855–37865.
- Salman, L.A.; Hashim, A.T.; Hasan, A.M. Selective Medical Image Encryption Using Polynomial-Based Secret Image Sharing and Chaotic Map. Int. J. Saf. Secur. Eng. 2022, 12, 357–369.
- Ke, G.; Wang, H.; Zhou, S.; Zhang, H. Encryption of medical image with most significant bit and high capacity in piecewise linear chaos graphics. Measurement 2019, 135, 385–391.
- Lai, Q.; Hu, G.; Erkan, U.; Toktas, A. High-efficiency medical image encryption method based on 2D Logistic-Gaussian hyperchaotic map. Appl. Math. Comput. 2023, 442, 127738.
- Forouzan, B. Cryptography and Network Security. 2015. Available online: https://www.just.edu.jo/FacultiesandDepartments/it/Departments/NES/Documents/2009Syllabus/NES452-Syllabus.pdf (accessed on 20 February 2023).
- Lone, P.N.; Singh, D.; Stoffová, V.; Mishra, D.C.; Mir, U.H.; Kumar, N. Cryptanalysis and Improved Image Encryption Scheme Using Elliptic Curve and Affine Hill Cipher. Mathematics 2022, 10, 3878.
- Kumar, L.A.; Srivastava, S.; Balaji, S.R.; Shajin, F.H.; Rajesh, P. Hybrid Visual and Optimal Elliptic Curve Cryptography for Medical Image Security in Iot. ECTI Trans. Comput. Inf. Technol. (ECTI-CIT) 2022, 16, 324–337.
- Vincent B., A.; Cecil Donald, A.; Shanthan, B.J.H.; Bist, A.S.; Mehraj, H.; VijendraBabu, D. Medical Image Detection & Privacy Management with Elliptic Curve GOPSO Cryptographic Optimization Technique on the Internet of Health Things. 2021. Available online: https://europepmc.org/article/ppr/ppr371633 (accessed on 20 February 2023).
- Yin, S.; Liu, J.; Teng, L. Improved Elliptic Curve Cryptography with Homomorphic Encryption for Medical Image En-cryption. Int. J. Netw. Secur. 2020, 22, 419–424.
- Haider, T.; Azam, N.A.; Hayat, U. A Novel Image Encryption Scheme Based on ABC Algorithm and Elliptic Curves. Arab. J. Sci. Eng. 2022, 48, 9827–9847.
- Hafsa, A.; Sghaier, A.; Malek, J.; Machhout, M. Image encryption method based on improved ECC and modified AES algorithm. Multimed. Tools Appl. 2021, 80, 19769–19801.
- Benssalah, M.; Rhaskali, Y. A Secure DICOM Image Encryption Scheme Based on ECC, Linear Cryptography and Chaos. In Proceedings of the 2020 1st International Conference on Communications, Control Systems and Signal Processing (CCSSP), El Oued, Algeria, 16–17 May 2020; pp. 131–136.
- Ibrahim, S.; Alharbi, A. Efficient Image Encryption Scheme Using Henon Map, Dynamic S-Boxes and Elliptic Curve Cryptography. IEEE Access 2020, 8, 194289–194302.
- Hayat, U.; Azam, N.A. A novel image encryption scheme based on an elliptic curve. Signal Process. 2019, 155, 391–402.
- Zhang, Q.; Liu, L.; Wei, X. Improved algorithm for image encryption based on DNA encoding and multi-chaotic maps. AEU-Int. J. Electron. Commun. 2014, 68, 186–192.
- Li, X.; Wang, L.; Yan, Y.; Liu, P. An improvement color image encryption algorithm based on DNA operations and real and complex chaotic systems. Optik 2016, 127, 2558–2565.
- Zhang, S.; Liu, L. A novel image encryption algorithm based on SPWLCM and DNA coding. Math. Comput. Simul. 2021, 190, 723–744.
- Adithya, B.; Santhi, G. A DNA Sequencing Medical Image Encryption System (DMIES) Using Chaos Map and Knight’s Travel Map. Int. J. Reliab. Qual. E-Healthc. 2022, 11, 1–22.
- Mir, U.H. Hyperchaotic Image Encryption Using DNA Coding and Discrete Cosine Transform. 2023. Available online: https://www.researchsquare.com/article/rs-2429075/v1 (accessed on 20 February 2023).
- Alqazzaz, S.F.; Elsharawy, G.A.; Eid, H.F. Robust 4-D Hyperchaotic DNA Framework for Medical Image Encryption. Int. J. Comput. Netw. Inf. Secur. 2022, 14, 67–76.
- Das, S. Medical Image Encryption Using 3D Unified Chaotic System and Dynamic DNA Coding. 2022. Available online: https://www.researchsquare.com/article/rs-2244229/v1 (accessed on 20 February 2023).
- Ismael, Y. Secure Image Steganography by Utilizing DNA Properties. Zanco J. Pure Appl. Sci. 2022, 34, 66–71.
- Mishra, P.; Bhaya, C.; Pal, A.K.; Singh, A.K. A medical image cryptosystem using bit-level diffusion with DNA coding. J. Ambient. Intell. Humaniz. Comput. 2021, 14, 1731–1752.
- Xie, H.-W.; Zhang, Y.-Z.; Zhang, H.; Li, Z.-Y. Novel medical image cryptogram technology based on segmentation and DNA encoding. Multimed. Tools Appl. 2023, 82, 27593–27613.
- Akkasaligar, P.T.; Biradar, S. Selective medical image encryption using DNA cryptography. Inf. Secur. J. A Glob. Perspect. 2020, 29, 91–101.
- Guesmi, R.; Ben Farah, M.A. A new efficient medical image cipher based on hybrid chaotic map and DNA code. Multimed. Tools Appl. 2021, 80, 1925–1944.
- Wu, Y.; Zhang, L.; Berretti, S.; Wan, S. Medical Image Encryption by Content-Aware DNA Computing for Secure Healthcare. IEEE Trans. Ind. Inform. 2023, 19, 2089–2098.
- Park, C.-S.; Park, R.; Krishna, G. Constitutive expression and structural diversity of inducible isoform of nitric oxide synthase in human tissues. Life Sci. 1996, 59, 219–225.
- Regev, O. On lattices, learning with errors, random linear codes, and cryptography. J. ACM 2009, 56, 1–40.
- Quantum Algorithms: An Overview. The Morning Paper. 2016. Available online: https://blog.acolyer.org/2018/02/06/quantum-algorithms-an-overview/ (accessed on 20 February 2023).
- McEliece, R.J. A public-key cryptosystem based on algebraic coding theory. Coding Thv. 1978, 4244, 114–116.
- Abd-El-Atty, B. A robust medical image steganography approach based on particle swarm optimization algorithm and quantum walks. Neural Comput. Appl. 2022, 35, 773–785.
- Heidari, S.; Naseri, M.; Nagata, K. Quantum Selective Encryption for Medical Images. Int. J. Theor. Phys. 2019, 58, 3908–3926.
- El-Latif, B.; Abd-El-Atty Ahmed, A.; Talha, M. Robust encryption of quantum medical images. IEEE Access 2018, 6, 1073–1081.
- Lin, C.-H.; Wu, J.-X.; Chen, P.-Y.; Lai, H.-Y.; Li, C.-M.; Kuo, C.-L.; Pai, N.-S. Intelligent Symmetric Cryptography with Chaotic Map and Quantum Based Key Generator for Medical Images Infosecurity. IEEE Access 2021, 9, 118624–118639.
- El-Latif, A.A.A.; Abd-El-Atty, B.; Hossain, M.S.; Rahman, A.; Alamri, A.; Gupta, B.B. Efficient Quantum Information Hiding for Remote Medical Image Sharing. IEEE Access 2018, 6, 21075–21083.
- Heidari, S.; Farzadnia, E. A novel quantum LSB-based steganography method using the Gray code for colored quantum images. Quantum Inf. Process. 2017, 16, 1–28.
- Naseri, M.; Heidari, S.; Batle, J.; Baghfalaki, M.; Fatahi, N.; Gheibi, R.; Farouk, A.; Habibi, A. A new secure quantum watermarking scheme. Optik 2017, 139, 77–86.
- Zhang, T.-J.; Abd-El-Atty, B.; Amin, M.; El-Latif, A.A.A. QISLSQb: A Quantum Image Steganography Scheme Based on Least Significant Qubit. In Proceedings of the 2016 International Conference on Mathematical, Computational and Statistical Sciences and Engineering (MCSSE 2016), Shenzhen, China, 30–31 October 2016; pp. 40–45.
- Anastasova, M.; Bisheh-Niasar, M.; Seo, H.; Azarderakhsh, R.; Kermani, M.M. Efficient and Side-Channel Resistant Design of High-Security Ed448 on ARM Cortex-M4. In Proceedings of the 2022 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 27–30 June 2022; pp. 93–96.
- Anastasova, M.; Kampanakis, P.; Massimo, J. PQ-HPKE: Post-Quantum Hybrid Public Key Encryption. Cryptology ePrint Archive. 2022. Available online: https://eprint.iacr.org/2022/414 (accessed on 20 February 2023).
- Saarinen, M.-J.O. Mobile Energy Requirements of the Upcoming NIST Post-Quantum Cryptography Standards. In Proceedings of the 2020 8th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 3–6 August 2020; pp. 23–30.
- Anastasova, M.; Bisheh-Niasar, M.; Azarderakhsh, R.; Kermani, M.M. Compressed SIKE Round 3 on ARM Cortex-M4. In Proceedings of the Security and Privacy in Communication Networks: 17th EAI International Conference, SecureComm 2021, Virtual Event, 6–9 September 2021; Proceedings, Part II 17. Springer International Publishing: Cham, Switzerland, 2021; pp. 441–457.
- Sanal, P.; Karagoz, E.; Seo, H.; Azarderakhsh, R.; Mozaffari-Kermani, M. Kyber on ARM64: Compact implementations of Kyber on 64-bit ARM Cortex-A processors. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Virtual, 6–9 September 2021; Cryptology ePrint Archive, Report 2021/561. Springer International Publishing: Cham, Switzerland, 2021.
More
Information
Subjects:
Others
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
2.3K
Revisions:
2 times
(View History)
Update Date:
29 Aug 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




