Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Oluwagbenga Apata | -- | 2046 | 2023-07-19 23:13:03 | | | |
| 2 | Camila Xu | Meta information modification | 2046 | 2023-07-20 03:04:25 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Apata, O.; Bokoro, P.N.; Sharma, G. Risks of Electric Vehicle Integration into Smart Cities. Encyclopedia. Available online: https://encyclopedia.pub/entry/47001 (accessed on 07 February 2026).
Apata O, Bokoro PN, Sharma G. Risks of Electric Vehicle Integration into Smart Cities. Encyclopedia. Available at: https://encyclopedia.pub/entry/47001. Accessed February 07, 2026.
Apata, Oluwagbenga, Pitshou N. Bokoro, Gulshan Sharma. "Risks of Electric Vehicle Integration into Smart Cities" Encyclopedia, https://encyclopedia.pub/entry/47001 (accessed February 07, 2026).
Apata, O., Bokoro, P.N., & Sharma, G. (2023, July 19). Risks of Electric Vehicle Integration into Smart Cities. In Encyclopedia. https://encyclopedia.pub/entry/47001
Apata, Oluwagbenga, et al. "Risks of Electric Vehicle Integration into Smart Cities." Encyclopedia. Web. 19 July, 2023.
Copy Citation
The integration of electric vehicles (EVs) into smart cities presents a promising opportunity for reducing greenhouse gas emissions and enhancing urban sustainability. However, there are significant risks and challenges associated with the integration of EVs into smart cities, which must be carefully considered.
electric vehicle
gasoline vehicle
grid integration
smart city
1. Introduction
The concept of smart cities has been around for several decades, but it has gained significant attention in recent years due to advances in technology and growing urbanization. The idea of using technology to improve urban living can be traced back to the 1970s, when researchers began to explore the potential of using computer networks to manage urban infrastructure. In the 1990s, the concept of the “digital city” emerged, which focused on using digital technologies to improve urban services and public participation. The term “smart city” was first coined in the early 2000s, and it has since become a popular buzzword in urban planning and development. The smart city concept gained momentum in 2008 when IBM launched its Smarter Planet initiative [1][2], which focused on using technology and data to address global challenges such as climate change, energy management, and urbanization. Since then, smart city initiatives have been implemented in cities around the world, and the concept has continued to evolve with advances in technology. These cities use sensors, devices, and networks to collect and analyse data, which is used to inform decision-making processes and optimize resource usage. One of the key challenges faced by smart cities is reducing their carbon footprint and promoting sustainable transportation. Electric vehicles (EVs) have emerged as a promising solution to this challenge, as they offer a more efficient and cleaner alternative to conventional gasoline-powered vehicles. This can be seen in the exponential growth of EV sales globally when compared to conventional gasoline-powered vehicles [3].
2. Risks of EV Integration into Smart Cities
The integration of EVs into smart cities is critical in promoting sustainable transportation solutions and reducing the impact of climate change. However, this integration process presents several risks. The major risks associated with integrating EVs into smart cities are the risks of cybersecurity and data privacy. Policymakers, energy managers, and other stakeholders must address these risks and develop effective strategies to mitigate these risks.
2.1. Cybersecurity Risks
As EVs gain traction in smart cities, the risks and challenges associated with their integration are becoming increasingly evident. Cybersecurity risks are one of the most significant challenges that need to be addressed during the integration of EVs into smart cities. With the integration of information and communication technologies (ICT) in the energy sector, the power grid components and utility servers of a smart city are susceptible to malware attacks from EVs [4]. Previous research on cybersecurity of the smart grid has largely focused on local attacks that impact specific components of the grid. This is because local attacks are often more straightforward to execute and require less skill and fewer resources than global attacks that impact the entire grid. As a result, local attacks remain the most common cyber threats to the smart grid, with malicious actors employing various techniques such as jamming, denial of service (DoS), controller malfunction, and load alteration attacks. Jamming attacks involve degrading the quality of communication signals between grid components, resulting in information loss and system malfunction [5]. Similarly, DoS attacks aim to disrupt normal communication channels by flooding them with traffic, and degrading the components of the grid. The issue of cybersecurity in smart cities has been well documented in different pieces of literature. In [6], the authors categorized the risk of cybersecurity in smart cities into passive and active attacks. A passive cyberattack in a smart city refers to a type of cyber threat where an attacker attempts to gain unauthorized access to sensitive information or systems without actively disrupting or altering their normal functioning. These attacks often target the vulnerabilities in the smart city’s infrastructure, such as communication networks, sensors, data repositories, and control systems. The attacker aims to exploit weaknesses in these systems to gain access to sensitive data, monitor activities, or gather information for further malicious activities. The active cyberattack typically involves actions taken by an attacker to gain unauthorized access, disrupt operations, manipulate data, or cause damage to critical infrastructure components. The attacker may employ various techniques, such as hacking, malware, social engineering, or denial-of-service attacks, to compromise the security and integrity of the smart city’s systems. Ref. [7] carried out a comprehensive literature review detailing the various privacy and security concerns in a smart city and proposed various solutions to addressing them.
A model was designed in [8] to detect attacks on the industrial control system (ICS) of smart cities, and by using interactive visualization, false alarms can be filtered out. The risk of cyberattacks originating from online social networks was studied in [9], where focal structure analysis (FSA) and deviant cyber flash mob detection (DCFM) techniques were used to develop a model to prevent damage from such attacks. Ref. [10] presented the Application, Communication, Infrastructure, Data, and Stakeholders (ACIDS) security framework to develop security measures and identify possible threats in the various layers of a smart city system. The overall security of a smart city system was improved by this proposed layered approach. Different cybersecurity issues and their associated risks in the operations of a smart city as well as different strategies for reducing such cyber-attacks in a smart city have been well documented in [11][12], respectively. The charging infrastructure of EVs are typically connected to a network, making them potential targets for cyber-attacks. The authors in [13] conducted a semi-quantitative analysis of the vulnerabilities between the various end-to-end subsystems of an EV. Malicious actors can exploit the connection between EVs and the grid to disrupt power supply, potentially causing widespread blackouts or other disruptions. In [14], the authors presented the various challenges and issues that can be exploited to seriously harm the charging stations of EVs, the power grid, or both. The communication protocols between EVs, chargers, and back-end systems are vulnerable to tampering. The protocols used to communicate the state of charge, the authentication of the charging process, and the billing systems can be manipulated by hackers to steal personal data and query the charging status of the vehicle. The report presented by the Kaspersky Lab in [15] indicated that the threats of cyber-attacks were linked to the charge points of home electric vehicle supply equipment (EVSE) units. This report validated the previous research done by the authors in [16], which outlined the risks associated with the deployment of EVSE devices. The various authors in [17][18][19][20] identified potential areas of vulnerabilities associated with EVSE. These could lead to security breaches in a smart city such as spoofing, data loss, and DoS. The phasor measurement unit (PMU) networks and electric vehicle infrastructure (EVI) in a smart city are vulnerable to cyberattacks, with potential consequences ranging from grid instability and power disruptions due to compromised PMU data, to unauthorized access and control of EV charging infrastructure leading to service disruptions and potential safety risks. This is well discussed and highlighted in [21] where the authors researched on the vulnerability of EVI and PMU networks to cyberattacks. Overall, cyberattacks on phasor measurement units (PMUs) in smart cities can lead to inaccurate power system measurements, faulty control strategies, and pose a significant threat to the overall reliability and safety of the power grid.
The use of third-party libraries in implementing various features such as navigation and communication in an EV makes it vulnerable to cyberattacks, thereby posing a significant risk in smart cities. Attackers may target vulnerabilities in the EV’s software or network connectivity to gain unauthorized remote access to the vehicle’s systems [22]. Once inside, they can potentially manipulate or disrupt critical functions, such as braking, acceleration, or steering. Electric vehicles often use keyless entry systems or wireless key fobs for authentication and remote access. Attackers may use various techniques to intercept or clone these key fobs, allowing them to gain unauthorized access to the vehicle without physical contact. The vulnerability of EVs with regards to third party libraries is well documented in [23], where a vulnerable application in a Tesla car was well exploited by a hacker to remotely access the features of the car and even bypass its keyless entry to start the vehicle. In [24], the infotainment system of an EV was attacked using third-party libraries to remotely perform software updates on the vehicle. While the integration of third-party libraries in EVs integrated into a smart city offers numerous advantages, it is crucial to carefully consider and address the associated risks.
2.2. Data Privacy Risks
With the increasing adoption of EVs in smart cities, there has been a significant increase in the amount of data generated by these vehicles and their supporting infrastructure. The data generated include information about the location of the vehicle, battery life, driving patterns, and more. All of these data provide valuable information that can be used in many ways, including optimizing traffic management, predicting maintenance needs, and developing new business models. However, there are significant privacy risks associated with collecting these data. In particular, the collection of personal data and driving patterns is a major concern. This information can be used to identify an individual’s behavior, movements, and preferences, creating a high risk of identity theft, stalking, and other privacy violations. Moreover, as seen in [25], these data can also be used for targeted marketing or insurance pricing, exposing drivers to financial risks. The data collected from EVs, when combined with other datasets, can lead to the identification and tracking of individuals. For example, by correlating location data from EVs with other publicly available information, it may be possible to determine an individual’s home address, workplace, or frequently visited locations. This personal identifiability increases the risk of privacy breaches and surveillance. In some cases, EV data may be shared with third parties, such as service providers, government entities, or researchers, for various purposes, such as traffic management or infrastructure planning. However, the sharing of data raises concerns about who has access to the data, how they will be used, and whether individuals’ privacy rights are adequately protected. According to [26], it is estimated that by the year 2030, global profits from vehicle generated information could reach a staggering USD 75 billion, making EVs an ideal target for hackers to steal data from.
As EVs become increasingly connected and integrated into smart city ecosystems, they generate vast amounts of data that can include personally identifiable information (PII), vehicle telemetry, location data, and more. Understanding the sensitivity of these data is essential for implementing appropriate security measures and ensuring privacy protection in the smart city. It is important to note that different data from the EV require different amounts of protection based on their sensitivity. It is therefore important to determine the sensitivity of EV data. Data classification involves categorizing data based on their levels of sensitivity, enabling organizations to allocate appropriate security controls and determine access privileges. By applying data classification techniques to EV data, it becomes possible to identify and differentiate between different types of information based on their potential impact if compromised. The authors in [27] determined the sensitivity of EV data using data classification techniques. These data have been grouped into confidential, sensitive, unclassified, and secret by the authors in [22][28] and depicted in Figure 1.
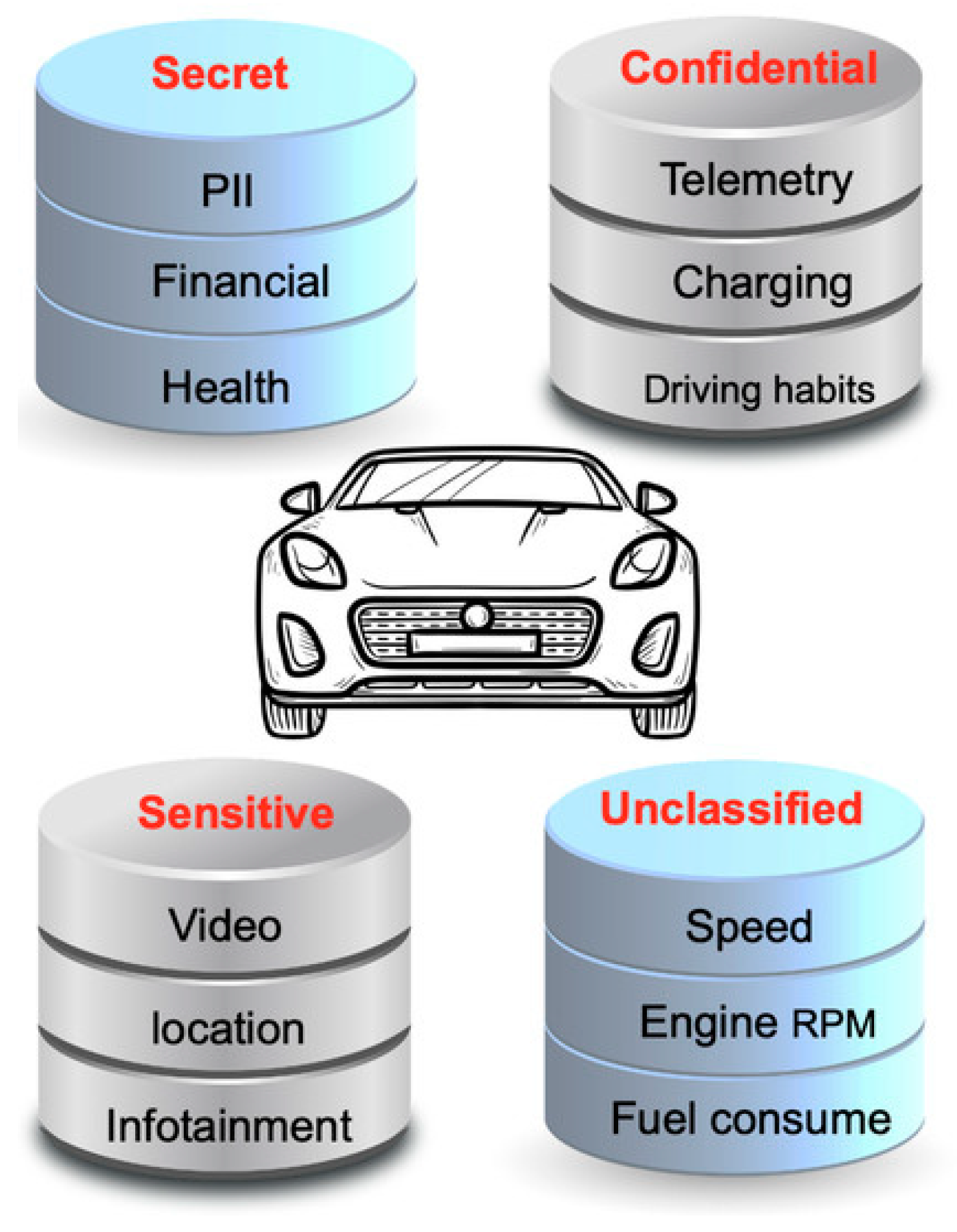
Figure 1. Data classification in EV [29].
One approach to data classification is the use of metadata tags [30], which can be attached to individual data elements to indicate their sensitivity level. For example, PII, such as driver’s license numbers, social security numbers, or credit card information, would be classified as highly sensitive, while anonymized vehicle telemetry data may be considered less sensitive. Another technique is automated machine learning (AutoML) [31][32], which can analyze large volumes of EV data and classify them based on patterns, features, or predefined rules. By training machine learning models on labeled datasets, it becomes possible to automate the classification process and identify sensitive data accurately. By leveraging data classification techniques, EV manufacturers, smart city operators, and other stakeholders can gain insights into the sensitivity of EV data. This knowledge enables them to implement appropriate security measures, such as encryption, access controls, and data anonymization, to protect sensitive information effectively. Additionally, data classification aids in compliance with data protection regulations, such as the General Data Protection Regulation (GDPR) or other regional privacy laws.
References
- Smarter Planet. Available online: https://www.ibm.com/ibm/history/ibm100/us/en/icons/smarterplanet/ (accessed on 20 May 2023).
- Taft, D.K. 25 Things You Might Not Know about IBMs Smarter Planet Strategy; eWeek: Nashville, TN, USA, 2009.
- IEA. Global EV Outlook 2023; IEA: Paris, France, 2023; Available online: https://www.iea.org/reports/global-ev-outlook-2023 (accessed on 22 May 2023).
- Carryl, C.; Ilyas, M.; Mahgoub, I.; Rathod, M. The PEV security challenges to the smart grid: Analysis of threats and mitigation strategies. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 300–305.
- Reyes, H.I.; Kaabouch, N. Jamming and lost link detection in wireless networks with fuzzy logic. Int. J. Sci. Eng. Res. 2013, 4, 1–7.
- Kalinin, M.; Krundyshev, V.; Zegzhda, P. Cybersecurity risk assessment in smart city infrastructures. Machines 2021, 9, 78.
- AlDairi, A. Cyber security attacks on smart cities and associated mobile technologies. Procedia Comput. Sci. 2017, 109, 1086–1091.
- Neshenko, N. Illuminating Cyber Threats for Smart Cities: A Data-Driven Approach for Cyber Attack Detection with Visual Capabilities. Doctoral Dissertation, Florida Atlantic University, Boca Raton, FL, USA, 2021.
- Alassad, M.; Spann, B.; Al-khateeb, S.; Agarwal, N. Using computational social science techniques to identify coordinated cyber threats to smart city networks. In Design and Construction of Smart Cities: Toward Sustainable Community; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 316–326.
- Hamid, S.; Bawany, N.Z. Acids: A secure smart city framework and threat model. In Proceedings of the 4th International Conference on Wireless, Intelligent and Distributed Environment for Communication: WIDECOM 2021, Milan, Italy, 11–13 February 2019; Springer International Publishing: Cham, Switzerland; pp. 79–98.
- Figueiredo, B.J.; Costa RL, D.C.; Santos, L.; Rabadão, C. Cybersecurity and Privacy in Smart Cities for Citizen Welfare. In Smart Cities, Citizen Welfare, and the Implementation of Sustainable Development Goals, 2022; IGI Global: Hershey, PN, USA, 2022; pp. 197–221.
- Wang, P.; Ali, A.; Kelly, W. Data security and threat modeling for smart city infrastructure. In Proceedings of the 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC), Shanghai, China, 5–7 August 2015; IEEE: Piscataway, NJ, USA; pp. 1–6.
- Basmadjian, R. Communication Vulnerabilities in Electric Mobility HCP Systems: A Semi-Quantitative Analysis. Smart Cities 2021, 4, 405–428.
- Acharya, S.; Dvorkin, Y.; Pandžić, H.; Karri, R. Cybersecurity of smart electric vehicle charging: A power grid perspective. IEEE Access 2020, 8, 214434–214453.
- Sklyar, D. ChargePoint Home Security Research; Kaspersky Lab Security Services: Moscow, Russia, 2018.
- Force, J.T.; Initiative, T. Guide for Applying the Risk Management Framework to Federal Information Systems; NIST Special Publication: Gaithersburg, MD, USA, 2010; Volume 800, p. 37.
- Basnet, M.; Ali, M.H. Exploring Cybersecurity Issues in 5G Enabled Electric Vehicle Charging Station with Deep Learning. IET Gener. Transm. Distrib. 2021, 15, 3435–3449.
- Reeh, D.; Cruz Tapia, F.; Chung, Y.W.; Khaki, B.; Chu, C.; Gadh, R. Vulnerability Analysis and Risk Assessment of EV Charging System under Cyber-Physical Threats. In Proceedings of the 2019 IEEE Transportation Electrification Conference and Expo (ITEC), Detroit, MI, USA, 19–21 June 2019.
- Johnson, J.; Berg, T.; Anderson, B.; Wright, B. Review of electric vehicle charger cybersecurity vulnerabilities, potential impacts, and defenses. Energies 2022, 15, 3931.
- Falk, R.; Fries, S. Securely connecting electric vehicles to the smart grid. Int. J. Adv. Internet Technol. 2013, 6, 57–67.
- Mousavian, S.; Erol-Kantarci, M.; Mouftah, H.T. Cyber-Security and Resiliency of Transportation and Power Systems in Smart Cities. In Transportation and Power Grid in Smart Cities: Communication Networks and Services; John & Wiley: Hoboken, NJ, USA, 2018; pp. 507–527.
- Ntousakis, G.; Ioannidis, S.; Vasilakis, N. Detecting Third-Party Library Problems with Combined Program Analysis. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Online, 15–19 November 2021; pp. 2429–2431.
- Vice Article. How a Hacker Controlled Dozens of Teslas Using a Flaw in Third-Party App. 2022. Available online: https://www.vice.com/en/article/akv7z5/how-a-hacker-controlled-dozens-of-teslas-using-a-flaw-in-third-party-app (accessed on 4 May 2023).
- O’Donnell, L. Volkswagen Cars Open to Remote Hacking, Researchers Warn. 2018. Available online: https://threatpost.com/volkswagen-cars-open-to-remote-hacking-researchers-warn/131571/ (accessed on 15 May 2023).
- Dibaei, M.; Zheng, X.; Jiang, K.; Abbas, R.; Liu, S.; Zhang, Y.; Yu, S. Attacks and defences on intelligent connected vehicles: A survey. Digit. Commun. Netw. 2020, 6, 399–421.
- Mckinsey. Monetizing Car Data. 2016. Available online: https://www.mckinsey.com/industries/automotive-and-assembly/our-insights/monetizing-car-data (accessed on 15 May 2023).
- Guo, L.; Ye, J.; Yang, B. Cyberattack detection for electric vehicles using physics-guided machine learning. IEEE Trans. Transp. Electrif. 2020, 7, 2010–2022.
- Aggarwal, C.C.; Aggarwal, C.C. Data Classification; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 285–344.
- Muhammad, Z.; Anwar, Z.; Saleem, B.; Shahid, J. Emerging Cybersecurity and Privacy Threats to Electric Vehicles and Their Impact on Human and Environmental Sustainability. Energies 2023, 16, 1113.
- De Clercq, D.; Diop, N.F.; Jain, D.; Tan, B.; Wen, Z. Multi-label classification and interactive NLP-based visualization of electric vehicle patent data. World Pat. Inf. 2019, 58, 101903.
- Balan, G.; Arumugam, S.; Muthusamy, S.; Panchal, H.; Kotb, H.; Bajaj, M.; Ghoneim, S.S. An Improved Deep Learning-Based Technique for Driver Detection and Driver Assistance in Electric Vehicles with Better Performance. Int. Trans. Electr. Energy Syst. 2022, 2022, 8548172.
- Ha, S.; Marchetto, D.J.; Dharur, S.; Asensio, O.I. Topic classification of electric vehicle consumer experiences with transformer-based deep learning. Patterns 2021, 2, 100195.
More
Information
Subjects:
Engineering, Electrical & Electronic
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
900
Revisions:
2 times
(View History)
Update Date:
20 Jul 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




