
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Ijaz Ahmad | -- | 3756 | 2023-04-25 11:01:51 | | | |
| 2 | Lindsay Dong | -20 word(s) | 3736 | 2023-04-26 07:30:00 | | |
Video Upload Options
The sixth-generation (6G) communication networks must be highly dependable due to the foreseen connectivity of critical infrastructures through these networks. Dependability is a compound metric of four well-known concepts—reliability, availability, safety, and security.
1. Introduction
2. Dependability
Dependability is the ability of a system to deliver a service that can justifiably be trusted; in other words, it should avoid frequent and severe service failures [13]. Though crucial in importance, dependability is often overlooked in favor of other research directions. Priority has been given to coordinating computing activities between distributed nodes in order to achieve higher performance, or security mechanisms that help in protecting users and their data. As previously mentioned, dependability is a compound metric and can be discussed through four important indicators: reliability, availability, safety, and security. Although performance and security are important, and as such most of the works focus on them, the other three requirements of dependable systems should not be underestimated [14][15]. Moreover, there are many facets of dependability, for instance, confidentiality and integrity [16]. However, some of the concepts converge into the four aspects discussed throughout this entry.
2.1. Reliability
2.2. Availability
2.3. Safety
2.4. Security
3. 6G and Dependability
3.1. Brief Introduction to 6G Networks
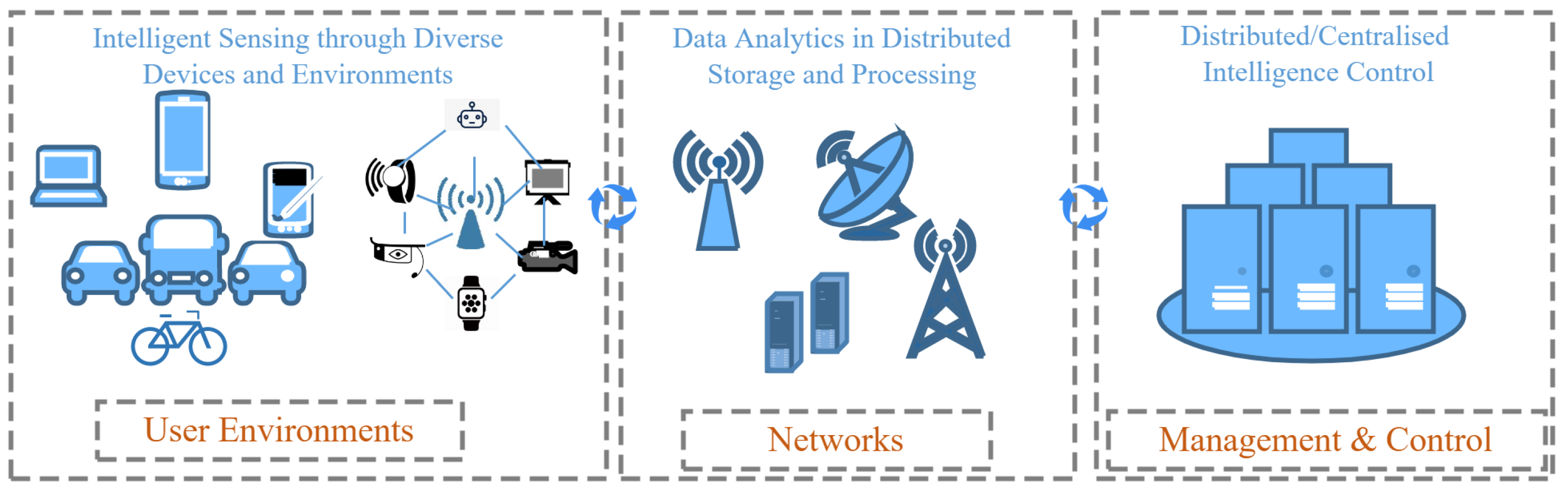
3.2. Dependability in 6G Networks
3.2.1. Reliability
3.2.2. Availability
3.2.3. Safety
3.2.4. Security
4. Machine Learning, Dependability, and 6G
AI and its major branch, ML, will shape 6G networks [24][30]. Due to its tight QoS requirements, future 6G networks will posses such a complex architecture that performing legacy network operations will be deemed unsound. For this, ML techniques are emerging as a response to achieve truly intelligent orchestration and network management [47]. The dynamic nature of communication networks provides data for ML-enabled spectrum management and channel estimation, which are the basis of ultra-broadband techniques. Additionally, ML is being used to improve security, resource allocation, mobility management, and low-latency services in MCAs [24]. In particular, ML techniques such as deep learning have proved to be extremely efficient in preventing serious security attacks, such as distributed DoS attacks [48]. Distributed ML will be highly important in 6G due to the emerging needs of distributed processing at the edges of the network [49]. FL is currently among the most used distributed ML techniques in communication networks [32][50] and is highly important for 6G due to its ability to be used in a distributed manner, much like the foreseen distributed control nature of 6G networks.
Reliability
Availability
Safety
Security
5. Dependability for MCAs in 6G
References
- Saad, W.; Bennis, M.; Chen, M. A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems. IEEE Netw. 2020, 34, 134–142.
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G Networks: Use Cases and Technologies. IEEE Commun. Mag. 2020, 58, 55–61.
- Ahmad, I.; Suomalainen, J.; Porambage, P.; Gurtov, A.; Huusko, J.; Höyhtyä, M. Security of Satellite-Terrestrial Communications: Challenges and Potential Solutions. IEEE Access 2022, 10, 96038–96052.
- AbdulRahman, S.; Tout, H.; Ould-Slimane, H.; Mourad, A.; Talhi, C.; Guizani, M. A survey on federated learning: The journey from centralized to distributed on-site learning and beyond. IEEE Internet Things J. 2021, 8, 5476–5497.
- Peltonen, E.; Bennis, M.; Capobianco, M.; Debbah, M.; Ding, A.; Gil-Castiñeira, F.; Jurmu, M.; Karvonen, T.; Kelanti, M.; Kliks, A.; et al. 6G white paper on edge intelligence. arXiv 2020, arXiv:2004.14850.
- Sekaran, R.; Patan, R.; Raveendran, A.; Al-Turjman, F.; Ramachandran, M.; Mostarda, L. Survival Study on Blockchain Based 6G-Enabled Mobile Edge Computation for IoT Automation. IEEE Access 2020, 8, 143453–143463.
- Nawaz, S.J.; Sharma, S.K.; Mansoor, B.; Patwary, M.N.; Khan, N.M. Non-Coherent and Backscatter Communications: Enabling Ultra-Massive Connectivity in 6G Wireless Networks. IEEE Access 2021, 9, 38144–38186.
- Bariah, L.; Mohjazi, L.; Muhaidat, S.; Sofotasios, P.C.; Kurt, G.K.; Yanikomeroglu, H.; Dobre, O.A. A Prospective Look: Key Enabling Technologies, Applications and Open Research Topics in 6G Networks. IEEE Access 2020, 8, 174792–174820.
- Ren, J.; Zhang, D.; He, S.; Zhang, Y.; Li, T. A Survey on End-Edge-Cloud Orchestrated Network Computing Paradigms: Transparent Computing, Mobile Edge Computing, Fog Computing, and Cloudlet. ACM Comput. Surv. 2019, 52.
- Hashima, S.; Fadlullah, Z.M.; Fouda, M.M.; Mohamed, E.M.; Hatano, K.; ElHalawany, B.M.; Guizani, M. On Softwarization of Intelligence in 6G Networks for Ultra-Fast Optimal Policy Selection: Challenges and Opportunities. IEEE Netw. 2022, 1–9.
- Letaief, K.B.; Shi, Y.; Lu, J.; Lu, J. Edge Artificial Intelligence for 6G: Vision, Enabling Technologies, and Applications. IEEE J. Sel. Areas Commun. 2022, 40, 5–36.
- Ahmed, W.; Wu, Y.W. A survey on reliability in distributed systems. J. Comput. Syst. Sci. 2013, 79, 1243–1255.
- Avizienis, A.; Laprie, J.C.; Randell, B.; Landwehr, C. Basic concepts and taxonomy of dependable and secure computing. IEEE Trans. Dependable Secur. Comput. 2004, 1, 11–33.
- Heimann, D.I.; Mittal, N.; Trivedi, K.S. Dependability modeling for computer systems. In Proceedings of the Annual Reliability and Maintainability Symposium, Orlando, FL, USA, 29–31 January 1991; pp. 120–128.
- Chen, D.; Garg, S.; Kintala, C.M.; Trivedi, K.S. Dependability Enhancement for IEEE 802.11 Wireless LAN with Redundancy Techniques. In Proceedings of the Dependable Systems and Networks, San Francisco, CA, USA, 22–25 June 2003; pp. 521–528.
- Laprie, J.C. Dependable computing: Concepts, limits, challenges. In Proceedings of the Special issue of the 25th International Symposium on Fault-Tolerant Computing, Pasadena, CA, USA, 27–30 June 1995; pp. 42–54.
- Gupta, R.; Reebadiya, D.; Tanwar, S. 6G-enabled Edge Intelligence for Ultra -Reliable Low Latency Applications: Vision and Mission. Comput. Stand. Interfaces 2021, 77, 103521.
- Ahmad, I.; Namal, S.; Ylianttila, M.; Gurtov, A. Security in Software Defined Networks: A Survey. IEEE Commun. Surv. Tutorials 2015, 17, 2317–2346.
- Banerjee, A.; Venkatasubramanian, K.K.; Mukherjee, T.; Gupta, S.K.S. Ensuring Safety, Security, and Sustainability of Mission-Critical Cyber–Physical Systems. Proc. IEEE 2012, 100, 283–299.
- Raytis, J.L.; Yuh, B.E.; Lau, C.S.; Fong, Y.; Lew, M.W. Anesthetic Implications of Robotically Assisted Surgery with the Da Vinci Xi Surgical Robot. Open J. Anesthesiol. 2016, 6, 115–118.
- Rim, L.J. Anesthetic considerations for robotic surgery. Korean J. Anesth. 2014, 66, 3–11.
- Ahmad, I.; Shahabuddin, S.; Kumar, T.; Okwuibe, J.; Gurtov, A.; Ylianttila, M. Security for 5G and beyond. IEEE Commun. Surv. Tutor. 2019, 21, 3682–3722.
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. Overview of 5G security challenges and solutions. IEEE Commun. Stand. Mag. 2018, 2, 36–43.
- Ahmad, I.; Shahabuddin, S.; Malik, H.; Harjula, E.; Leppänen, T.; Lovén, L.; Anttonen, A.; Sodhro, A.H.; Mahtab Alam, M.; Juntti, M.; et al. Machine Learning Meets Communication Networks: Current Trends and Future Challenges. IEEE Access 2020, 8, 223418–223460.
- Suomalainen, J.; Juhola, A.; Shahabuddin, S.; Mämmelä, A.; Ahmad, I. Machine learning threatens 5G security. IEEE Access 2020, 8, 190822–190842.
- Ahmad, I.; Shahabuddin, S.; Sauter, T.; Harjula, E.; Kumar, T.; Meisel, M.; Juntti, M.; Ylianttila, M. The Challenges of Artificial Intelligence in Wireless Networks for the Internet of Things: Exploring Opportunities for Growth. IEEE Ind. Electron. Mag. 2020, 15, 16–29.
- Dibaei, M.; Zheng, X.; Xia, Y.; Xu, X.; Jolfaei, A.; Bashir, A.K.; Tariq, U.; Yu, D.; Vasilakos, A.V. Investigating the Prospect of Leveraging Blockchain and Machine Learning to Secure Vehicular Networks: A Survey. IEEE Trans. Intell. Transp. Syst. 2021, 23, 683–700.
- Zhang, Z.; Xiao, Y.; Ma, Z.; Xiao, M.; Ding, Z.; Lei, X.; Karagiannidis, G.K.; Fan, P. 6G Wireless Networks: Vision, Requirements, Architecture, and Key Technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41.
- David, K.; Berndt, H. 6G Vision and Requirements: Is There Any Need for Beyond 5G? IEEE Veh. Technol. Mag. 2018, 13, 72–80.
- Tariq, F.; Khandaker, M.R.A.; Wong, K.K.; Imran, M.A.; Bennis, M.; Debbah, M. A Speculative Study on 6G. IEEE Wirel. Commun. 2020, 27, 118–125.
- Nezami, Z.; Zamanifar, K. Internet of ThingsInternet of Everything: Structure and Ingredients. IEEE Potentials 2019, 38, 12–17.
- Wang, X.; Han, Y.; Wang, C.; Zhao, Q.; Chen, X.; Chen, M. In-Edge AI: Intelligentizing Mobile Edge Computing, Caching and Communication by Federated Learning. IEEE Netw. 2019, 33, 156–165.
- Pham, Q.V.; Fang, F.; Ha, V.N.; Piran, M.J.; Le, M.; Le, L.B.; Hwang, W.J.; Ding, Z. A Survey of Multi-Access Edge Computing in 5G and Beyond: Fundamentals, Technology Integration, and State-of-the-Art. IEEE Access 2020, 8, 116974–117017.
- Osorio, D.P.M.; Ahmad, I.; Sánchez, J.D.V.; Gurtov, A.; Scholliers, J.; Kutila, M.; Porambage, P. Towards 6G-enabled Internet of Vehicles: Security and Privacy. IEEE Open J. Commun. Soc. 2022, 3, 82–105.
- Okwuibe, J.; Haavisto, J.; Kovacevic, I.; Harjula, E.; Ahmad, I.; Islam, J.; Ylianttila, M. SDN-Enabled Resource Orchestration for Industrial IoT in Collaborative Edge-Cloud Networks. IEEE Access 2021, 9, 115839–115854.
- Zhou, Z.; Chen, X.; Li, E.; Zeng, L.; Luo, K.; Zhang, J. Edge Intelligence: Paving the Last Mile of Artificial Intelligence with Edge Computing. Proc. IEEE 2019, 107, 1738–1762.
- Deng, S.; Zhao, H.; Fang, W.; Yin, J.; Dustdar, S.; Zomaya, A.Y. Edge Intelligence: The Confluence of Edge Computing and Artificial Intelligence. IEEE Internet Things J. 2020, 7, 7457–7469.
- Li, C.; Guo, W.; Sun, S.C.; Al-Rubaye, S.; Tsourdos, A. Trustworthy Deep Learning in 6G-Enabled Mass Autonomy: From Concept to Quality-of-Trust Key Performance Indicators. IEEE Veh. Technol. Mag. 2020, 15, 112–121.
- Harjula, E.; Karhula, P.; Islam, J.; Leppänen, T.; Manzoor, A.; Liyanage, M.; Chauhan, J.; Kumar, T.; Ahmad, I.; Ylianttila, M. Decentralized IoT edge nanoservice architecture for future gadget-free computing. IEEE Access 2019, 7, 119856–119872.
- Herlich, M.; Maier, C. Measuring and Monitoring Reliability of Wireless Networks. IEEE Commun. Mag. 2021, 59, 76–81.
- Bhagwan, R.; Savage, S.; Voelker, G.M. Understanding availability. In Proceedings of the International Workshop on Peer-to-Peer Systems, Berkeley, CA, USA, 21–22 February 2003; Springer: Berlin/Heidelberg, Germany; pp. 256–267.
- Young, W.; Leveson, N.G. An integrated approach to safety and security based on systems theory. Commun. ACM 2014, 57, 31–35.
- Ahmad, I.; Lembo, S.; Rodriguez, F.; Mehnert, S.; Vehkaperä, M. Security of Micro MEC in 6G: A Brief Overview. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; pp. 332–337.
- Ma, J.; Shrestha, R.; Adelberg, J.; Yeh, C.Y.; Hossain, Z.; Knightly, E.; Jornet, J.M.; Mittleman, D.M. Security and eavesdropping in terahertz wireless links. Nature 2018, 563, 89–93.
- Song, F. A note on quantum security for post-quantum cryptography. In Proceedings of the International Workshop on Post-Quantum Cryptography, Waterloo, ON, Canada, 23 September 2014; pp. 246–265.
- Omolara, A.E.; Alabdulatif, A.; Abiodun, O.I.; Alawida, M.; Alabdulatif, A.; Alshoura, W.H.; Arshad, H. The internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 2022, 112, 102494.
- Khan, L.U.; Pandey, S.R.; Tran, N.H.; Saad, W.; Han, Z.; Nguyen, M.N.H.; Hong, C.S. Federated Learning for Edge Networks: Resource Optimization and Incentive Mechanism. IEEE Commun. Mag. 2020, 58, 88–93.
- Mittal, M.; Kumar, K.; Behal, S. Deep learning approaches for detecting DDoS attacks: A systematic review. Soft Comput. 2022, 1–37.
- Mwase, C.; Jin, Y.; Westerlund, T.; Tenhunen, H.; Zou, Z. Communication-efficient distributed AI strategies for the IoT edge. Future Gener. Comput. Syst. 2022, 131, 292–308.
- Liu, Y.; Yuan, X.; Xiong, Z.; Kang, J.; Wang, X.; Niyato, D. Federated learning for 6G communications: Challenges, methods, and future directions. China Commun. 2020, 17, 105–118.
- Mahmood, N.H.; Böcker, S.; Munari, A.; Clazzer, F.; Moerman, I.; Mikhaylov, K.; López, O.L.A.; Park, O.; Mercier, E.; Bartz, H.; et al. White Paper on Critical and Massive Machine Type Communication Towards 6G. arXiv 2020, arXiv:2004.14146.
- She, C.; Dong, R.; Gu, Z.; Hou, Z.; Li, Y.; Hardjawana, W.; Yang, C.; Song, L.; Vucetic, B. Deep Learning for Ultra-Reliable and Low-Latency Communications in 6G Networks. IEEE Netw. 2020, 34, 219–225.





