Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | jisu kim | -- | 2930 | 2023-04-14 16:08:32 | | | |
| 2 | Catherine Yang | + 1 word(s) | 2931 | 2023-04-17 02:53:28 | | | | |
| 3 | Catherine Yang | -14 word(s) | 2917 | 2023-04-17 08:37:47 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Kim, K.; Alshenaifi, I.M.; Ramachandran, S.; Kim, J.; Zia, T.; Almorjan, A. Cybersecurity in Smart Cities. Encyclopedia. Available online: https://encyclopedia.pub/entry/43066 (accessed on 07 February 2026).
Kim K, Alshenaifi IM, Ramachandran S, Kim J, Zia T, Almorjan A. Cybersecurity in Smart Cities. Encyclopedia. Available at: https://encyclopedia.pub/entry/43066. Accessed February 07, 2026.
Kim, Kyounggon, Istabraq Mohammed Alshenaifi, Sundaresan Ramachandran, Jisu Kim, Tanveer Zia, Abdulrazaq Almorjan. "Cybersecurity in Smart Cities" Encyclopedia, https://encyclopedia.pub/entry/43066 (accessed February 07, 2026).
Kim, K., Alshenaifi, I.M., Ramachandran, S., Kim, J., Zia, T., & Almorjan, A. (2023, April 14). Cybersecurity in Smart Cities. In Encyclopedia. https://encyclopedia.pub/entry/43066
Kim, Kyounggon, et al. "Cybersecurity in Smart Cities." Encyclopedia. Web. 14 April, 2023.
Copy Citation
Smart technologies, such as the Internet of Things (IoT), cloud computing, and artificial intelligence (AI), are being adopted in cities and transforming them into smart cities. In smart cities, various network technologies, such as the Internet and IoT, are combined to exchange real-time information, making the everyday lives of their residents more convenient. Cybersecurity for smart cities includes a combination of technologies that have emerged to address the highly complex challenges of insecure devices and networks, which can lead to unbounded attacks.
smart city
cybersecurity
digital forensics
1. Smart Transportation/Mobility
Javed et al. [1] conducted a security study on next-generation intelligent transport system (ITS) applications in smart cities, as shown in Figure 1. After analysing the security architecture of the European Telecommunications Standards Institute (ETSI) ITS standard, they implemented ECC-based digital signatures and encryption procedures using experimental test beds. In their study, a network simulation model was used to reproduce the smart city scenario. From the experimental results, they found that existing security solutions could directly affect the quality of service and safety perception of vehicle applications. Wang et al. [2] provided strategies to protect connected vehicles and the AI in the vehicles and also discussed automobile cybersecurity attacks. Kim et al. [3] discussed the implications of attacks on autonomous vehicles and how to defend against such attacks when integrated with the AI within the main components of smart cities, based on a systemic survey.
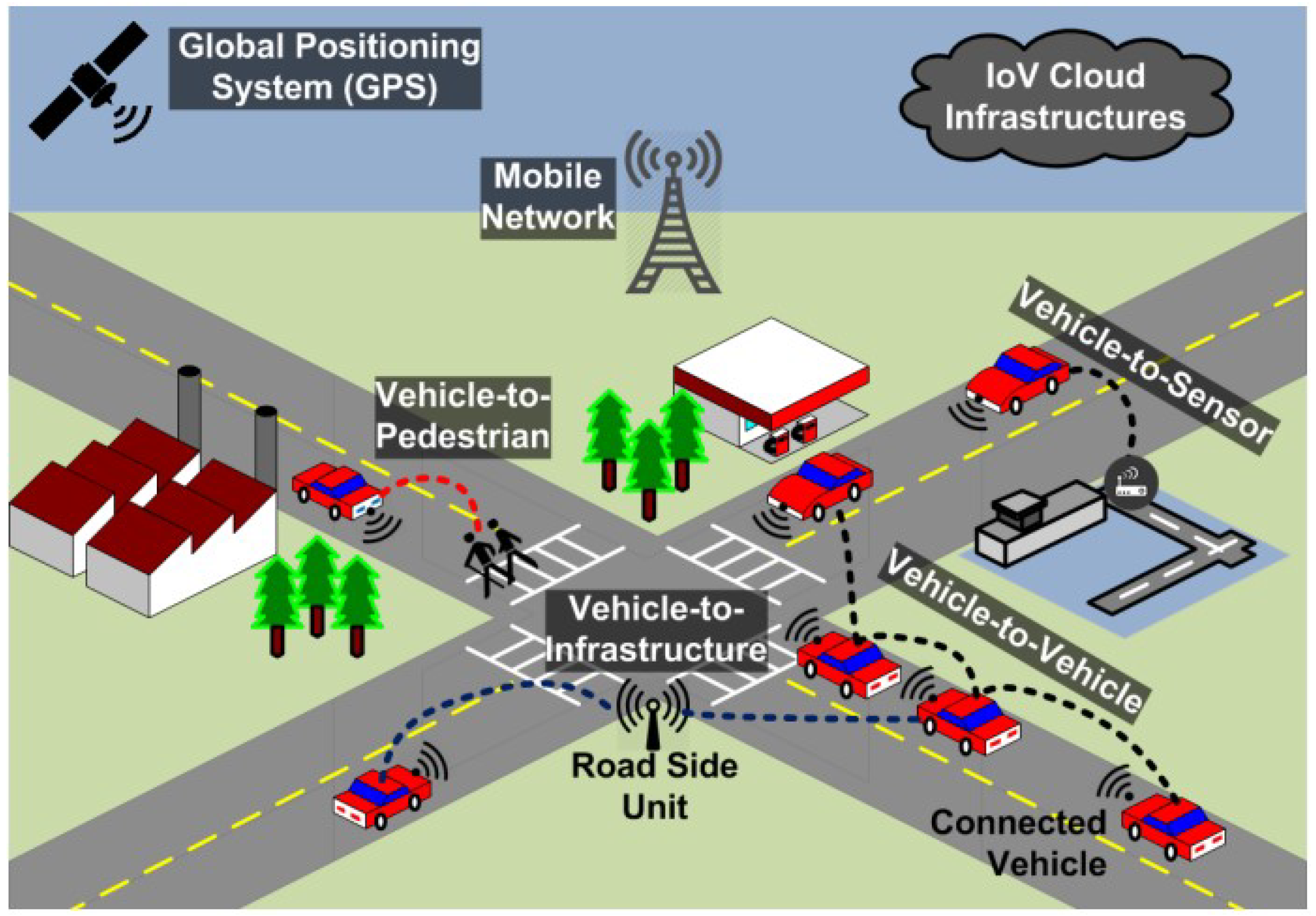
Figure 1. The ITS communication architecture in smart cities [1].
Sharmila et al. [4] analysed the different vulnerabilities and threats in autonomous vehicles and provided a model to mitigate security threats. Chen and Quan [5] discussed various attacks and targets within the Internet of Vehicles (IoV). They also proposed a framework for the IoV based on blockchain and suggested solutions for security, authentication, and privacy issues in the IoV.
ITSs and autonomous vehicles are essential components of smart cities. Researchers have analysed the security of these systems, including their architecture, vulnerabilities, and potential attacks. They have proposed various strategies to safeguard connected vehicles and mitigate security threats, including digital signatures and encryption procedures, as well as the use of blockchain frameworks. Studies have also shown that existing security solutions can affect the quality of service and safety perception of vehicle applications.
2. Smart Homes
Several research papers have addressed the cybersecurity and privacy concerns regarding smart homes. Ryu and Kwak [6] investigated the risk of unauthorized access to smart homes and proposed a secure data access control scheme to prevent data leakage, privacy invasion, and the falsification of data. McGee [7] evaluated the personally identifiable information (PII) vulnerabilities in smart home ecosystems and developed a security as a service (SECaaS) capability to assess the results. Liu and Hu [8] highlighted the cybersecurity vulnerabilities in smart home infrastructure, particularly energy bill scheduling techniques, and described current detection methods and cyberattack tools. Nsunza et al. [9] conducted an experiment to assess the performance of TCP and UDP network traffic using field programmable gate arrays (FPGAs) and system-on-chip (SoC) platforms in smart home routers.
Gamundani et al. [10] and Ghirardello et al. [11] investigated the vulnerabilities of authentication and home automation systems in smart homes and potential attack opportunities. Kraemer and Flechais [12] explored the future directions of privacy research within the smart home domain. Bastos et al. [13] proposed solutions for security issues in IoT devices in smart homes and predicted possible future cyberattacks. Sturgess et al. [14] identified three factors that contributed to smart home privacy risks. The first factor involved evaluating heterogeneous devices from a top-down perspective. The second factor concerned the various cyberthreats that exist in smart homes. The final factor explained the difficulties in aggregating the highly valuable private data of homeowners. They suggested a capability-oriented model to facilitate the rapid development of smart homes. Siddhanti et al. [15] suggested using a cybersecurity maturity assessment tool to secure smart home environments from cyberthreats.
Elmisery and Sertovic [16] suggested a permission-based approach for revealing log records that require involvement with third parties. Personal usage logs from homes that are shared with third parties can lead to attacks on smart home environments. Rossi et al. [17] identified a solution for detecting the exploitation of smart home systems by monitoring vulnerabilities in the systems-of-systems domain using a combination of defensive programming and Shodan APIs. Shodan APIs are a set of application programming interfaces (APIs) provided by the Shodan search engine that enable users to search and access information about Internet-connected devices and systems. Giannoutakis et al. [18] presented a framework to address this issue by using blockchain technology to ensure the integrity of smart home devices and block malicious IPs from accessing smart home environments.
In 2021, Rauti et al. [19] demonstrated attacks on the Chrome web browser by implementing a malicious browser extension. The user activities were modified, which affected the management consoles of smart homes. They showed that the connection of IoT devices to smart home networks caused potential man-in-the-browser attacks to target the remote control systems. Awang et al. [20] proposed solutions to enhance the IoT ecosystems in smart homes and analysed the possible threats to smart home operational environments. Turner et al. [21] discussed how the Internet connection between devices introduces security risks to smart homes as it allows access to private user information. They also provided recommendations for users regarding safely accessing cybersecurity data. Alshboul et al. [22] also proposed a methodology for detecting and predicting intruders attempting to recognize the identities of smart home sensors. They emphasized that data should preserve their identity by knowing their sources and not adding extra loads to the network.
In 2022, Mahor et al. [23] proposed a security solution using blockchain to evaluate performance parameters and analyse and detect correlations between traffic functions in smart home networks. Bringhenti et al. [24] presented a configurable automation security system to secure personalization data in smart homes and improve usability by minimizing human interventions and implementing policy-based management. Allifah and Zualkernan [25] presented a novel methodology to rank the security of home consumer devices. They also discussed the analytic hierarchy process (AHP) and applied it to ranking the overall security risks. Thammarat and Techapanupreeda [26] proposed a protocol to fill the gap in security messages in smart homes regarding confidentiality, integrity, and mutual authentication using symmetric cryptography. They demonstrated the efficacy of their protocol using the Burrows–Abadi–Needham (BAN) logic and scyther tool framework.
The security and privacy of smart homes are of concern within the field of cybersecurity. Research on IoT security in smart homes has focused on identifying and addressing issues, such as unauthorized device access, vulnerabilities in PII, cybersecurity vulnerabilities in smart home infrastructure, and potential attacks on authentication and home automation systems. Proposed solutions to these security concerns include using blockchain technology to ensure the integrity of smart home devices and implementing policy-based management to secure personalization data. Additionally, protocols using symmetric cryptography have been suggested to protect confidentiality, integrity, and mutual authentication in smart homes.
3. IoT Cybersecurity Research
In this section, the researchers summarized the IoT cybersecurity research papers related to smart cities, as shown in Table 1. Abomhara and Køien [27] classified the types of cyberthreats to IoT devices and services and analysed the characteristics of attackers. Rohokale and Prasad [28] proposed an approach for designing robust cybersecurity solutions for IoT device networks since heterogeneous networks are targeted by attackers and often encounter cyberthreats.
Table 1. A summary of the approaches and experiments presented in existing IoT cybersecurity research.
| Category | Authors | Year | Approach/Experiment |
|---|---|---|---|
| IoT | Abomhara and Køien [27] | 2015 | Threat classification, attack characterization and an analysis of IoT devices |
| Rohokale and Prasad [28] | 2015 | A critical systematic review of cyberthreats to heterogeneous IoT networks | |
| Saadeh et al. [29] | 2016 | A survey of IoT authentication techniques | |
| Sivanathan et al. [30] | 2017 | An evaluation of vulnerabilities through CIA and the capability of DDoS attacks | |
| Neshenko [31] | 2018 | An evaluation of large-scale malicious IoT data from cyberthreat intelligence | |
| Ainane et al. [32] | 2018 | An identification of data and protocol exchanges between users and IoT applications | |
| Vrabie [33] | 2018 | How IoT networks and services can develop smart cities | |
| Viswanadham and Jayavel [34] | 2018 | The implementation of blockchain in IoT security and its domain | |
| Lewis [35] | 2018 | The security of IoT networks and devices | |
| Wu et al. [36] | 2018 | Hyperconnected interdependent IoT services and future applications | |
| James [37] | 2019 | The detection of critical attacks on IoT devices by executing cybersecurity- based attacks |
|
| Shokeen et al. [38] | 2019 | An accurate evaluation of each vulnerability of IoT systems | |
| Roukounaki et al. [39] | 2019 | The identification of threats using security analytics algorithms, vulnerabilities, and attacks | |
| Van Kleek et al. [40] | 2019 | The classification of IoT device data in privacy-empowering networks | |
| Thorburn et al. [41] | 2019 | Basic future frameworks for IoT devices that share data with third parties | |
| Nwafor and Olufowobi [42] | 2019 | An anomaly detection system for events in IoT ecosystems | |
| Ullah et al. [43] | 2019 | The detection of infected SW and files across IoT networks using deep learning (DL) |
|
| Sharma et al. [44] | 2020 | The computerized security of IoT devices | |
| Karie et al. [45] | 2020 | A literature review of IoT threat detection and security challenges | |
| Andrade et al. [46] | 2020 | An evaluation of IoT cybersecurity maturity in smart cities according to its risk levels |
|
| Singh et al. [47] | 2020 | The types of IoT security threats and their countermeasures | |
| Cvitić et al. [48] | 2021 | The detection of DDoS traffic attack using logistic model trees on different IoT devices |
|
| Jhanjhi et al. [49] | 2021 | An investigation of cyberattacks that target the four layers of the IoT | |
| Strecker et al. [50] | 2021 | The detection of malicious and anomalous data in IoT systems using machine learning (ML) | |
| Ahmed et al. [51] | 2021 | An analysis of the security and privacy concepts in IoT networks using ML and DL | |
| Houichi et al. [52] | 2021 | The detection of infected IoT devices, alerts, and reports based on ML and other methods | |
| Bhargava et al. [53] | 2021 | The implementation of ML/DL on IoT platforms to prevent security issues | |
| Al Solami [54] | 2021 | The use of secure resource administration to stop IoT services from being replicated |
|
| Hulicki and Hulicki [55] | 2021 | The threats to network security mechanisms and their vulnerabilities to attacks | |
| Ali et al. [56] | 2021 | A literature review of IoT security issues, their classification, and solutions | |
| Debnath and Chettri [57] | 2021 | A literature review of the security challenges in IoT applications | |
| Toutsop et al. [58] | 2021 | DoS attacks on IoT devices through networks | |
| Balaji et al. [59] | 2021 | An analysis of cyberthreats and prevention methods for avoiding IoT attacks | |
| Khan [60] | 2021 | Privacy preservation based on pseudonymization and anonymization | |
| Nakkeeran and Mathi [61] | 2021 | The detection of anomalies in IoT networks and solutions for cross-layer issues | |
| Kowta et al. [62] | 2022 | A identification of security threats to different IoT devices by implementing attacks on them | |
| Maidamwar et al. [63] | 2022 | An intrusion detection design for the WSN-based IoT | |
| Raimundo and Rosário [64] | 2022 | A literature review of cybersecurity threats to the IoT | |
| Fan et al. [65] | 2022 | Security guidelines for developing IoT-enabled smart cities |
Saadeh et al. [29] presented a literature review of authentication and communication processes between IoT objects. Sivanathan et al. [30] evaluated the vulnerabilities of IoT devices to cyberattacks by rating their confidentiality, integrity, availability, and reflectiveness capabilities as either good, average, or poor. The evaluation process was divided into four categories: confidentiality, integrity, availability, and reflectiveness capabilities against attacks.
Neshenko [31] generated cyberthreat intelligence related to Internet-scale inference and the assessment of malicious activity generated by compromised IoT devices for the immediate detection, mitigation, and prevention of IoT exploitation. Ainane et al. [32] described how flooding occurs when data are exchanged between citizens and smart cities. They also identified the types of protocols that revolve around the IoT applications that are used during these exchanges. Vrabie [33] presented IoT services that could help to develop smart cities and provided numerous examples of cities that have implemented these concepts. Viswanadham and Jayavel [34] surveyed related research on blockchain technology implemented within IoT devices and applications. They aimed to provide an understanding of blockchain security and privacy features for IoT services. Lewis [35] used a graph database to understand the complexity of IoT networks, as well as different devices that impact the security of networks and associated data. Wu et al. [36] proposed a framework for the development of future IoT applications and analysed the future directions of IoT communication and its challenging aspects.
In 2019, James [37] attempted to fill the gap in the research on cybersecurity challenges in IoT services and applications by conducting intrusion attacks on several IoT devices within smart homes. They also established a method to protect affected devices and smart home systems from future attacks using an intrusion prevention system. Shokeen et al. [38] suggested a framework to assess the risks of cyberthreats to IoT systems that avoids external factors from being involved in the evaluation. Furthermore, it also reduces existing vulnerabilities. Roukounaki et al. [39] proposed deploying security data collection systems in complex IoT devices and applying effective security analysis algorithms to identify threats, vulnerabilities, and related attack patterns. Van Kleek et al. [40] proposed disaggregating the privacy of IoT networks to help prevent private end-user data from being collected. Thorburn et al. [41] presented possible future development directions for third-party entities that collect personal information without the knowledge of homeowners, based on data flows in smart home environments. Nwafor and Olufowobi [42] presented a framework to detect anomalous system events in IoT ecosystems and associated devices. Ullah et al. [43] proposed a solution to classify the performance of measuring cyberthreats to IoT devices.
In 2020, Sharma et al. [44] discussed the IoT cybersecurity issues and noted that the innovation of IoT devices is growing and expanding progressively. Karie et al. [45] focused on developing combat strategies against IoT cybersecurity threats and also discussed future directions in this domain. Andrade et al. [46] proposed a model for evaluating the risk levels related to IoT cybersecurity. The assessment model was based on a systematic literature review of research on developing smart city applications and cybersecurity risk levels. Singh et al. [47] provided several examples of cyberthreats and countermeasures, as well as discussing how the combination of cloud computing and IoT devices could be used in smart city applications to identify these types of security threats.
In 2021, research on IoT was very active, especially in relation to smart cities. Cvitić et al. [48] presented a model to detect DDoS traffic and identify IoT devices that were categorized into four different classes. Jhanjhi et al. [49] proposed a solution to analyse cybersecurity privacy challenges by understanding the current state of cybersecurity. Ahmed et al. [51] discussed various aspects of cybersecurity in IoT networks and analysed MLP, CNN, LSTP, and AI/ML models. Strecker et al. [50] presented a cyberthreat intelligence model to evaluate and infer malicious activities targeting IoT devices and their data integrity. This model could also mitigate the exploitation of IoT devices. Houichi et al. [52] discovered that ML could be used to detect anomalous threats and vulnerabilities in IoT devices and localize them, as well as generating reports and alerts for the threats. This solution was evaluated experimentally using the NSL-KDD dataset and demonstrated high accuracy (99.31%).
Bhargava et al. [53] suggested enhancing the experience in smart cities by addressing security and privacy issues in IoT platforms and provided an overview of how ML and DL could be implemented in IoT devices and services. Al Solami [54] presented a framework for secure resource administration that enhances IoT services in smart city applications by preventing replication. This involves the distribution of the cloud, networks, IoT platforms, and sensors. They also demonstrated how to prevent unintended attacks from original supplier sources by monitoring non-replicated services. Hulicki and Hulicki [55] explored cyberthreats and vulnerabilities of customer premises networks and the resulting attacks associated with IoT applications and services. Ali et al. [56] discussed the security issues in IoT devices and services that have been gathered and reported. They also classified these issues and provided solutions. Debnath and Chettri [57] reviewed the current trends in IoT research, as well as identifying the recent issues and challenges in IoT applications and industries. Toutsop et al. [58] proved that hackers can exploit sensors and gain unauthorized access to IoT networks. Furthermore, they attempted to carry out DoS attacks on IoT devices to understand the device vulnerabilities and provide intrusion detection using ML and DL. Balaji et al. [59] analysed the types of cyberthreats and consequences that IoT systems may face. They also discussed how to prevent and avoid these attacks.
Khan [60] suggested different privacy protection methods based on pseudonymization, clustering, anonymization, and more to prevent private data from being exchanged with service providers and third parties. Kowta et al. [62] discussed the various cybersecurity threats and vulnerabilities in IoT devices. They performed several attacks on IoT devices and devised with solutions and methods to prevent these attacks. Nakkeeran and Mathi [61] provided a framework for end-to-end IoT sensor and device solutions and a detection method for identifying suspicious and anomalous network behaviour through cross-layer analysis. Maidamwar et al. [63] reviewed the design of an intrusion detection framework for the WSN-based IoT, which they described as being able to increase confidence in the reliability of IoT networks and contain network intrusions. Raimundo and Rosário [64] filled a gap in the research on cybersecurity risks in the IoT domain by discussing the existing solutions and cyberthreats in the industrial Internet of Things (IIoT), based on a literature review. Fan et al. [65] provided general security guidelines for enhancing the IoT in smart cities, which were presented in four main points. Firstly, they provided an overview of recent innovations and common security challenges. Secondly, they discussed the latest security implementations that use cryptography in the IoT. Thirdly, they analysed the security challenges using the activity–network–things architecture. Lastly, they discussed potential IoT security prospects.
Cybersecurity is a critical concern for the widespread adoption of IoT devices and services. To address this challenge, robust cybersecurity solutions have been proposed, including vulnerability assessments for IoT devices, cyberthreat intelligence generation, AI/ML-based threat detection, and models for mitigating malicious activities targeting IoT devices. The combination of cloud computing and IoT devices is also being explored as a means of enhancing the security of smart city applications.
References
- Javed, M.A.; Ben Hamida, E.; Znaidi, W. Security in intelligent transport systems for smart cities: From theory to practice. Sensors 2016, 16, 879.
- Wang, Z.; Wang, Y.; Zhang, Y.; Liu, Y.; Ma, C.; Wang, H. A brief survey on cyber security attack entrances and protection strategies of intelligent connected vehicle. In Proceedings of the Smart Computing and Communication: 4th International Conference, SmartCom 2019, Birmingham, UK, 11–13 October 2019; pp. 73–82.
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150.
- Sharmila, V.C.; Aslam, H.M.; Riswan, M.M. Analysing and Identifying Harm Propagation of Cyber Threats in Autonomous Vehicles and Mitigation Through ANN. In Proceedings of the Smart Trends in Computing and Communications: Proceedings of SmartCom 2021, Las Vegas, NA, USA, 2–3 March 2021; pp. 405–417.
- Chen, C.; Quan, S. A Summary of Security Techniques-Based Blockchain in IoV. Secur. Commun. Netw. 2022, 2022, 8689651.
- Ryu, H.S.; Kwak, J. Secure data access control scheme for smart home. In Advances in Computer Science and Ubiquitous Computing: CSA &CUTE; Springer: Berlin/Heidelberg, Germany, 2015; pp. 483–488.
- McGee, T.M. Evaluating the Cyber Security in the Internet of Things: Smart Home Vulnerabilities. Ph.D. Thesis, Colorado Technical University, Colorado Springs, CO, USA, 2016.
- Liu, Y.; Hu, S. Smart home scheduling and cybersecurity: Fundamentals. In Smart Cities and Homes; Elsevier: Amsterdam, The Netherlands, 2016; pp. 191–217.
- Nsunza, W.W.; Rutunda, S.; Hei, X. Design and implementation of a low-cost software defined wireless network testbed for smart home. In Proceedings of the Security, Privacy, and Anonymity in Computation, Communication, and Storage: SpaCCS 2017 International Workshops, Guangzhou, China, 12–15 December 2017; pp. 379–388.
- Gamundani, A.M.; Phillips, A.; Muyingi, H.N. An overview of potential authentication threats and attacks on Internet of Things (IoT): A focus on Smart home applications. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Espoo, Finland, 22–25 August 2022; pp. 50–57.
- Ghirardello, K.; Maple, C.; Ng, D.; Kearney, P. Cyber security of smart homes: Development of a reference architecture for attack surface analysis. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT-2018, London, UK, 28–29 March 2018; pp. 1–10.
- Kraemer, M.J.; Flechais, I. Researching privacy in smart homes: A roadmap of future directions and research methods. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT-2018, London, UK, 28–29 March 2018; pp. 1–10.
- Bastos, D.; Shackleton, M.; El-Moussa, F. Internet of things: A survey of technologies and security risks in smart home and city environments. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT-2018, London, UK, 28–29 March 2018; pp. 30–37.
- Sturgess, J.; Nurse, J.R.; Zhao, J. A capability-oriented approach to assessing privacy risk in smart home ecosystems. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT-2018, London, UK, 28–29 March 2018; pp. 1–8.
- Siddhanti, P.; Asprion, P.M.; Schneider, B. Cybersecurity by Design for Smart Home Environments. In Proceedings of the ICEIS (1), Heraklion, Greece, 3–5 May 2019; pp. 587–595.
- Elmisery, A.M.; Sertovic, M. Privacy preserving threat hunting in smart home environments. In Proceedings of the Advances in Cyber Security: First International Conference, ACeS 2019, Penang, Malaysia, 30 July–1 August 2019; pp. 104–120.
- Rossi, M.T.; Greca, R.; Iovino, L.; Giacinto, G.; Bertoli, A. Defensive Programming for Smart Home Cybersecurity. In Proceedings of the 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 16–18 June 2020; pp. 600–605.
- Giannoutakis, K.M.; Spathoulas, G.; Filelis-Papadopoulos, C.K.; Collen, A.; Anagnostopoulos, M.; Votis, K.; Nijdam, N.A. A blockchain solution for enhancing cybersecurity defence of IoT. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Virtual, 2–6 November 2020; pp. 490–495.
- Rauti, S.; Laato, S.; Pitkämäki, T. Man-in-the-Browser Attacks Against IoT Devices: A Study of Smart Homes. In Proceedings of the 12th International Conference on Soft Computing and Pattern Recognition (SoCPaR 2020) 12, Online, 15–18 December 2020; pp. 727–737.
- Awang, N.F.; Zainudin, A.F.I.M.; Marzuki, S.; Alsagoff, S.N.; Tajuddin, T.; Jarno, A.D. Security and threats in the internet of things based smart home. In Innovative Systems for Intelligent Health Informatics: Data Science, Health Informatics, Intelligent Systems, Smart Computing; Springer: Berlin/Heidelberg, Germany, 2021; pp. 676–684.
- Turner, S.; Nurse, J.; Li, S. When googling it does not work: The challenge of finding security advice for smart home devices. In Proceedings of the Human Aspects of Information Security and Assurance: 15th IFIP WG 11.12 International Symposium, HAISA 2021, Virtual, 7–9 July 2021; pp. 115–126.
- Alshboul, Y.; Bsoul, A.A.R.; Al Zamil, M.; Samarah, S. Cybersecurity of smart home systems: Sensor identity protection. J. Netw. Syst. Manag. 2021, 29, 1–27.
- Mahor, V.; Badodia, S.K.; Kumar, A.; Bijrothiya, S.; Temurnikar, A. Cyber Security for Secured Smart Home Applications Using Internet of Things, Dark Web, and Blockchain Technology in the Future. In Dark Web Pattern Recognition and Crime Analysis Using Machine Intelligence; IGI Global: Hershey, PA, USA, 2022; pp. 208–219.
- Bringhenti, D.; Valenza, F.; Basile, C. Toward Cybersecurity Personalization in Smart Homes. IEEE Secur. Priv. 2022, 20, 45–53.
- Allifah, N.M.; Zualkernan, I.A. Ranking Security of IoT-Based Smart Home Consumer Devices. IEEE Access 2022, 10, 18352–18369.
- Thammarat, C.; Techapanupreeda, C. Secure Key Establishment Protocol for Smart Homes Based on Symmetric Cryptography. In Proceedings of the 2022 International Conference on Information Networking (ICOIN), Jeju-si, Republic of Korea, 12–15 January 2022; pp. 46–51.
- Abomhara, M.; Køien, G.M. Cyber security and the internet of things: Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88.
- Rohokale, V.; Prasad, R. Cyber security for intelligent world with Internet of Things and machine to machine communication. J. Cyber Secur. Mobil. 2015, 4, 23–40.
- Saadeh, M.; Sleit, A.; Qatawneh, M.; Almobaideen, W. Authentication techniques for the internet of things: A survey. In Proceedings of the 2016 Cybersecurity and Cyberforensics Conference (CCC), Amman, Jordan, 2–4 August 2016; pp. 28–34.
- Sivanathan, A.; Loi, F.; Gharakheili, H.H.; Sivaraman, V. Experimental evaluation of cybersecurity threats to the smart-home. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bhubaneswar, India, 17–20 December 2017; pp. 1–6.
- Neshenko, N. A Network Telescope Approach for Inferring and Characterizing IoT Exploitations. Ph.D. Thesis, Florida Atlantic University, Boca Raton, FL, USA, 2018.
- Ainane, N.; Ouzzif, M.; Bouragba, K. Data security of smart cities. In Proceedings of the 3rd International Conference on Smart City Applications, Tetouan, Morocco, 10–11 October 2018; pp. 1–13.
- Vrabie, C. IoT and its role in developing smart cities. In Proceedings of the Information Systems: Research, Development, Applications, Education: 11th SIGSAND/PLAIS EuroSymposium 2018, Gdansk, Poland, 20 September 2018; pp. 105–113.
- Viswanadham, Y.V.; Jayavel, K. Blockchain Implementation in IoT Privacy and Cyber Security Feasibility Study and Analysis. In High Performance Computing and Networking: Select Proceedings of CHSN 2021; Springer: Berlin/Heidelberg, Germany, 2022; pp. 259–271.
- Lewis, M. Using Graph Databases to Assess the Security of Thingernets Based on the Thingabilities and Thingertivity of Things; IET: London, UK, 2018.
- Wu, F.J.; Solmaz, G.; Kovacs, E. Toward the Future World of Internet-of-Things. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6.
- James, F. IoT cybersecurity based smart home intrusion prevention system. In Proceedings of the 2019 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, 23–25 October 2019; pp. 107–113.
- Shokeen, R.; Shanmugam, B.; Kannoorpatti, K.; Azam, S.; Jonkman, M.; Alazab, M. Vulnerabilities analysis and security assessment framework for the internet of things. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference (CCC), Melbourne, Australia, 8–9 May 2019; pp. 22–29.
- Roukounaki, A.; Efremidis, S.; Soldatos, J.; Neises, J.; Walloschke, T.; Kefalakis, N. Scalable and configurable end-to-end collection and analysis of IoT security data: Towards end-to-end security in IoT systems. In Proceedings of the 2019 Global IoT Summit (GIoTS), Aarhus, Denmark, 17–21 June 2019; pp. 1–6.
- Van Kleek, M.; Seymour, W.; Binns, R.; Zhao, J.; Karandikar, D.; Shadbolt, N. IoT Refine: Making Smart Home Devices Accountable for Their Data Harvesting Practices; IET: London, UK, 2019.
- Thorburn, R.; Margheri, A.; Paci, F. Towards an Integrated Privacy Protection Framework for IoT: Contextualising Regulatory Requirements with Industry Best Practices; IET: London, UK, 2019.
- Nwafor, E.; Olufowobi, H. Towards an Interactive Visualization Framework for IoT Device Data Flow. In Proceedings of the 2019 IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; pp. 4175–4178.
- Ullah, F.; Naeem, H.; Jabbar, S.; Khalid, S.; Latif, M.A.; Al-Turjman, F.; Mostarda, L. Cyber security threats detection in internet of things using deep learning approach. IEEE Access 2019, 7, 124379–124389.
- Sharma, R.; Mahapatra, R.P.; Sharma, N. The internet of things and its applications in cyber security. In A Handbook of Internet of Things in Biomedical and Cyber Physical System; Springer: Berlin/Heidelberg, Germany, 2020; pp. 87–108.
- Karie, N.M.; Sahri, N.M.; Haskell-Dowland, P. IoT threat detection advances, challenges and future directions. In Proceedings of the 2020 workshop on emerging technologies for security in IoT (ETSecIoT), Sydney, Australia, 21 April 2020; pp. 22–29.
- Andrade, R.O.; Yoo, S.G.; Tello-Oquendo, L.; Ortiz-Garcés, I. A Comprehensive Study of the IoT Cybersecurity in Smart Cities. IEEE Access 2020, 8, 228922–228941.
- Singh, D.; Pati, B.; Panigrahi, C.R.; Swagatika, S. Security issues in IoT and their countermeasures in smart city applications. In Advanced Computing and Intelligent Engineering: Proceedings of ICACIE 2018; Springer: Berlin/Heidelberg, Germany, 2020; Volume 2, pp. 301–313.
- Cvitić, I.; Perakovic, D.; Gupta, B.B.; Choo, K.K.R. Boosting-based DDoS detection in internet of things systems. IEEE Internet Things J. 2021, 9, 2109–2123.
- Jhanjhi, N.; Humayun, M.; Almuayqil, S.N. Cyber Security and Privacy Issues in Industrial Internet of Things. Comput. Syst. Sci. Eng. 2021, 37, 361–380.
- Strecker, S.; Van Haaften, W.; Dave, R. An analysis of IoT cyber security driven by machine learning. In Proceedings of the International Conference on Communication and Computational Technologies: ICCCT 2021, Virtual, 16–17 December 2021; pp. 725–753.
- Ahmed, K.D.; Askar, S. Deep learning models for cyber security in IoT networks: A review. Int. J. Sci. Bus. 2021, 5, 61–70.
- Houichi, M.; Jaidi, F.; Bouhoula, A. A systematic approach for IoT cyber-attacks detection in smart cities using machine learning techniques. In Proceedings of the Advanced Information Networking and Applications: Proceedings of the 35th International Conference on Advanced Information Networking and Applications (AINA-2021), Toronto, ON, Canada, 12–14 May 2021; Volume 2, pp. 215–228.
- Bhargava, A.; Salunkhe, G.; Bhargava, S.; Goswami, P. A Comprehensive Study of IoT Security Risks in Building a Secure Smart City. Digit. Cities Roadmap IOT-Based Archit. Sustain. 2021, 14, 401–448.
- Al Solami, E. Replication-aware secure resource administration scheme for Internet of Things-smart city applications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4200.
- Hulicki, Z.; Hulicki, M. Cyber Security Aspects of Digital Services Using IoT Appliances. In Proceedings of the Recent Challenges in Intelligent Information and Database Systems: 13th Asian Conference, ACIIDS 2021, Phuket, Thailand, 7–10 April 2021; pp. 227–237.
- Ali, R.F.; Muneer, A.; Dominic, P.; Taib, S.M.; Ghaleb, E.A. Internet of things (IoT) security challenges and solutions: A systematic literature review. In Proceedings of the Advances in Cyber Security: Third International Conference, ACeS 2021, Penang, Malaysia, 24–25 August 2021; pp. 128–154.
- Debnath, D.; Chettri, S.K. Internet of Things: Current Research, Challenges, Trends and Applications. In Proceedings of the Applications of Artificial Intelligence in Engineering: Proceedings of First Global Conference on Artificial Intelligence and Applications (GCAIA 2020), Jaipur, India, 8–10 September 2020; pp. 679–694.
- Toutsop, O.; Das, S.; Kornegay, K. Exploring The Security Issues in Home-Based IoT Devices Through Denial of Service Attacks. In Proceedings of the 2021 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/IOP/SCI), Atlanta, GA, USA, 18–21 October 2021; pp. 407–415.
- Balaji, S.; Jaishanker, A.; Gokhale, S.; Sinhal, S.; Rajeshkumar, M. A Review on Cybersecurity of Internet of Things. In Proceedings of the Microelectronic Devices, Circuits and Systems: Second International Conference, ICMDCS 2021, Vellore, India, 11–13 February 2021; pp. 172–196.
- Khan, M.A. A formal method for privacy-preservation in cognitive smart cities. Expert Syst. 2022, 39, e12855.
- Nakkeeran, M.; Mathi, S. A Generalized Comprehensive Security Architecture Framework for IoT Applications Against Cyber-Attacks. In Artificial Intelligence and Technologies: Select Proceedings of ICRTAC-AIT 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 455–471.
- Kowta, A.S.L.; Harida, P.; Venkatraman, S.V.; Das, S.; Priya, V. Cyber Security and the Internet of Things: Vulnerabilities, Threats, Intruders, and Attacks. In Proceedings of the International Conference on Computational Intelligence and Data Engineering: ICCIDE 2021, Vijayawada, India, 13–14 August 2021; pp. 387–401.
- Maidamwar, P.R.; Bartere, M.M.; Lokulwar, P.P. Implementation of network intrusion detection system using artificial intelligence: Survey. In Proceedings of the 2nd International Conference on Recent Trends in Machine Learning, IoT, Smart Cities and Applications: ICMISC 2021, Hyderabad, India, 28–29 March 2021; pp. 185–198.
- Raimundo, R.J.; Rosário, A.T. Cybersecurity in the Internet of Things in Industrial Management. Appl. Sci. 2022, 12, 1598.
- Fan, J.; Yang, W.; Lam, K.Y. Cybersecurity Challenges Of IoT-enabled Smart Cities: A Survey. arXiv 2022, arXiv:2202.05023.
More
Information
Subjects:
Others
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
802
Revisions:
3 times
(View History)
Update Date:
17 Apr 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




