
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Dean Liu | -- | 1730 | 2022-10-24 01:49:55 |
Video Upload Options
A proprietary device driver is a closed-source device driver published only in binary code. In the context of free and open-source software, a closed-source device driver is referred to as a blob or binary blob. The term usually refers to a closed-source kernel module loaded into the kernel of an open-source operating system, and is sometimes also applied to code running outside the kernel, such as system firmware images, microcode updates, or userland programs. The term blob was first used in database management systems to describe a collection of binary data stored as a single entity. When computer hardware vendors provide complete technical documentation for their products, operating system developers are able to write hardware device drivers to be included in the operating system kernels. However, some vendors, such as Nvidia, do not provide complete documentation for some of their products and instead provide binary-only drivers. This practice is most common for accelerated graphics drivers, wireless networking devices, and hardware RAID controllers. Most notably, binary blobs are very uncommon for non-wireless network interface controllers, which can almost always be configured via standard utilities (like ifconfig) out of the box; Theo de Raadt of OpenBSD attributes this to the work done by a single FreeBSD developer.
1. Open Source Operating Systems
Some FSF-approved projects strive to provide a free operating system and will remove all binary blobs when no documentation for hardware or source code for device drivers and all applicable firmware is available; such projects include Linux-libre kernel packaging from FSFLA, Parabola, Devuan, Trisquel, and LibreCMC.[1] However, the vast majority of open-source projects make a distinction between binary-only device drivers (blobs) and binary-only firmware (not considered blobs[2]:...), allowing for certain proprietary firmware to be freely distributed as part of their kernels, and, to the disagreement of some core contributors, also support the use of proprietary device drivers that are distributed externally, providing internal compatibility interfaces for such proprietary drivers and userspace components to work with their system.[3][4] Projects following this policy include the Linux kernel itself, NetBSD, FreeBSD, DragonFly BSD, and most Linux distributions.[5] Some of these projects do provide options for building the system without proprietary firmware, thus excluding sourceless microcode on demand.[6]
The OpenBSD project has a notable policy of not only not accepting any binary device drivers into its source tree, but also officially not supporting any third-party proprietary device driver components on its platform, either;[7]:38... citing not only the potential for undetectable or irreparable security flaws, but also the encroachment onto the openness and freedom of its software.[8] The Free Software Foundation (FSF) is actively campaigning against binary blobs.[9] FSF also considers OpenBSD's policy confusingly worded, as "blobs" in the BSD community refer only to what it considers non-free drivers, and does not apply to proprietary firmware and sourceless microcode.[10]:BSD The Debian project included both free and non-free binary firmware from the Linux kernel, clearly marking and separating the non-free packages[11] according to the Debian Social Contract. As of Debian 6.0 those blobs were removed.[10]:Debian
For OpenBSD, project leader Theo de Raadt defends the policy of asking for distribution rights only for microcode firmware. "Once they are distributed... at least the device works." Implying that the alternative would be for the members of his small project to code free firmware themselves in the assembly language of many chipsets, he pleads "don't load us up with more tasks." Despite this he favours chipsets that run without firmware and speaks warmly of Asian designs which he describes as slower to market but more mature.[8]
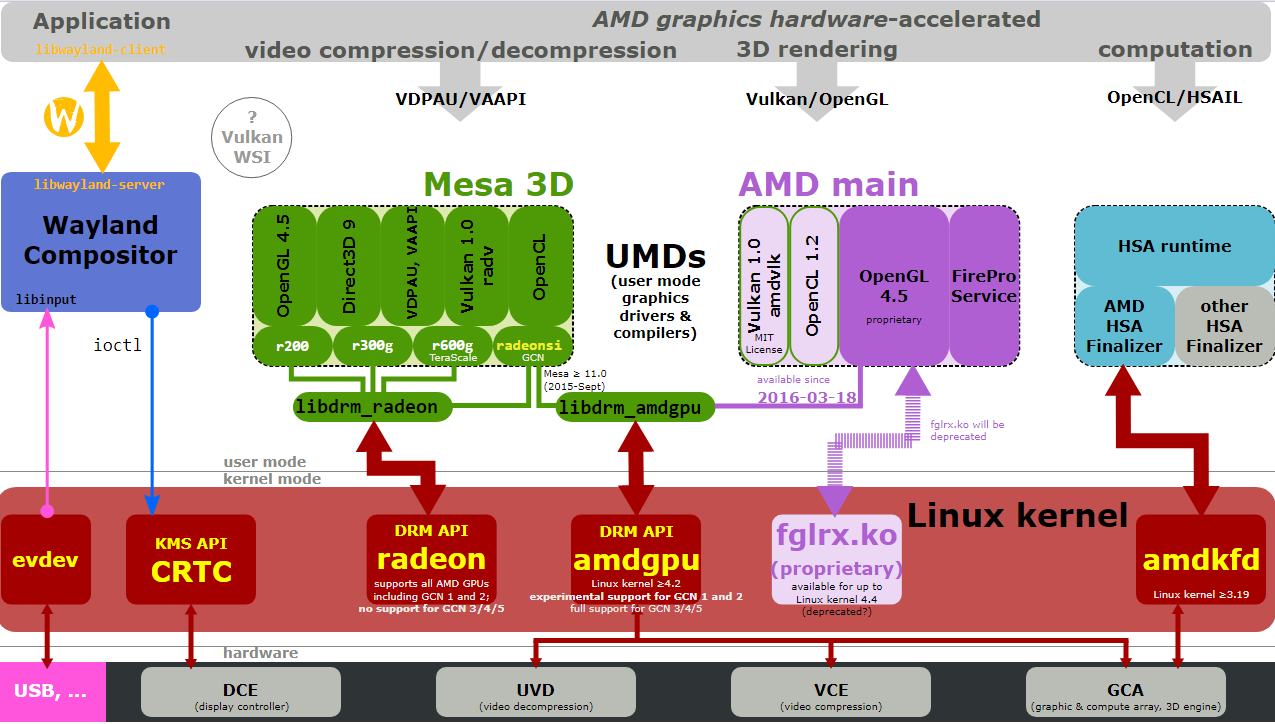
In the Linux kernel development community, Linus Torvalds has made strong statements on the issue of binary-only modules, asserting: "I refuse to even consider tying my hands over some binary-only module", and continuing: "I want people to know that when they use binary-only modules, it's THEIR problem."[12] In 2008, 176 Linux kernel developers signed a Position Statement on Linux Kernel Modules that stated "We, the undersigned Linux kernel developers, consider any closed-source Linux kernel module or driver to be harmful and undesirable... We have repeatedly found them to be detrimental to Linux users, businesses, and the greater Linux ecosystem."[13] The Linux kernel maintainer Greg Kroah-Hartman has stated that it is illegal to redistribute closed source modules for the GNU General Public License-licensed Linux kernel.[14]
However, the Linux kernel contains closed-source firmware required by various device drivers.[10][15] Alexandre Oliva, the maintainer of Linux-libre, a version of the Linux kernel that attempts to remove all binary blobs, including sourceless microcode, wrote in 2011: "Linux hasn't been Free Software since 1996, when Mr Torvalds accepted the first pieces of non-Free Software in the distributions of Linux he has published since 1991. Over these years, while this kernel grew by a factor of 14, the amount of non-Free firmware required by Linux drivers grew by an alarming factor of 83."[16]
Most of the drivers for mobile devices running the Android operating system are shipped in binary and are linked against a specific version of the Linux kernel. This makes it very hard to upgrade a kernel version because it may require reverse-engineering, reimplementing the proprietary device drivers as free software, creating and debugging wrappers, binary patching, or a combination of these steps, all of which implies that legacy devices will never get the latest Android version.
2. Problems
There are a number of reasons why binary blobs can be problematic.[2]
Firstly, their precise operation cannot be known and bugs cannot be detected by auditing source code; bugs are frequently only diagnosed by painstaking investigation when a system begins to behave unexpectedly. Such undetected bugs may also silently expose users and systems to security hazards. The fitness for purpose of the driver thus cannot be checked, and even if a bug is found there is no easy way to fix it.
Secondly, as the source code is not available, the driver cannot be readily improved by its users, cannot be ported to architectures not originally supported, nor adapted to operate for slight variants of the hardware or updated it to be workable in new kernels having the changed API and architecture.
Thirdly, using this software would force users to trust vendors or third parties not to put backdoors, spyware or malicious code into the blob. As well, the hardware vendor can decide not to support a given operating system, abandon driver maintenance at any time, or, in the event the company goes out of business, leave the driver completely unsupported.
Finally, binary blobs can be seen as drawing a line between the portion of the community that believes in free software ideals, rejecting proprietary software, and the portion that sees open source as desirable for purely technical reasons, often lacking a strong opposition to binary blobs "as long as they work". This fragmentation, and the acceptance of a growing number of proprietary components into Linux, is seen as weakening the ability of the community to resist the trend of manufacturers to increasingly refuse to provide documentation for their binaries.
3. Use via Wrappers
A wrapper is software which allows one operating system to use a binary proprietary device driver written for another operating system. Examples of wrappers are NdisWrapper for Linux, and Project Evil for FreeBSD and NetBSD. These wrappers allow these operating systems to use network drivers written for Microsoft Windows by implementing Microsoft's NDIS API.
Another example is providing compatibility layers so that foreign utilities could be used to service the hardware. Examples include some RAID controller drivers in FreeBSD, where the system administrator would have to enable Linux compatibility layer in FreeBSD and independently procure Linux-specific binary blobs directly from the hardware manufacturer in order to monitor and service the hardware.[3][4][17] Circa 2005, this state of affairs prompted OpenBSD to create and popularise its bio(4), bioctl and sensor drive concepts as an alternative solution for RAID monitoring,[7][18] both of which concepts have subsequently found its way into NetBSD as well.
4. Device Firmware
Firmware is the software required by the onboard microcontrollers that accompany some hardware, is generally not considered to be a binary blob.[10][19]:BSD[2]:... In many devices, firmware is stored in non-volatile onboard flash memory, but to decrease costs and ease upgrades, some devices contain only static RAM and require the host operating system to upload firmware each time they are connected (especially USB devices). Although the firmware is thus present in the operating system driver, it is merely copied to the device and not executed by the CPU, removing concerns about extra security flaws compared to what's already possible with a DMA attack even if the firmware was already stored within the device at all times. The OpenBSD project accepts binary firmware/microcode images and will redistribute these images if the license permits;[19][20] if free and unconditional redistribution is not permitted by the vendor, the machine instructions on fetching these images may be provided in the ports tree (which precludes some encumbered wireless devices (e.g., Intel Wireless) from being available during the initial install).[21]
5. BIOS and UEFI
The BIOS, which functions as a bootloader and supports legacy real mode applications, is a crucial component of many IBM-compatible computers. The BIOS can be a security backdoor.[22][23] In the late 1990s work started on EFI (Extensible Firmware Interface) with the objective to move legacy BIOS to a modern interface with a modular driver model. EFI is closed source and was eventually adopted by many industry leading hardware manufacturers as UEFI (Unified Extensible Firmware Interface). The EDK (EFI Development Kit) was developed to assist EFI firmware development projects.[24]
Also in the late 1990s, the coreboot project was started to create an open source alternative to legacy BIOS from scratch.[24] The coreboot developer community organises around Stefan Reinauer and is led by firmware developers with commit rights.[25] Despite closed source binary firmware having been at the heart of the x86 architecture coreboot only incorporates the few proprietary binaries that are necessary to provide users with a base level hardware support.[26] A completely open source alternative to BIOS and UEFI is libreboot, which was promoted by the Free Software Foundation (FSF).[27]
References
- "List of Free GNU/Linux Distributions". GNU Project. Free Software Foundation. https://www.gnu.org/distros/free-distros.html.
- Andrews, Jeremy (2006-04-19). "Interview with Jonathan Gray and Damien Bergamini". kerneltrap.org. http://kerneltrap.org/node/6497.
- "aac(4) — Adaptec AdvancedRAID Controller driver". FreeBSD. http://bxr.su/f/share/man/man4/aac.4. "If the kernel is compiled with the COMPAT_LINUX option, or the aac_linux.ko and linux.ko modules are loaded..." FreeBSD Manual Pages. http://mdoc.su/f/aac.4.
- "aacraid(4) — Adaptec AACRAID Controller driver". FreeBSD. 2013. http://bxr.su/f/share/man/man4/aacraid.4. "If the kernel is compiled with the COMPAT_LINUX option, or the aacraid_linux.ko and linux.ko modules are loaded..." FreeBSD Manual Pages. http://mdoc.su/f/aacraid.4.
- Matzan, Jem (15 June 2005). "BSD cognoscenti on Linux". NewsForge. http://os.newsforge.com/os/05/06/09/2132233.shtml?tid=8&tid=2. See Christos Zoulas's response to "Is sharing between Free/Open/NetBSD and the Linux kernel a common occurrence? And if so, does it go both ways?"
- "build/options/WITHOUT_SOURCELESS_UCODE". FreeBSD. 2012-02-04. http://bxr.su/f/tools/build/options/WITHOUT_SOURCELESS_UCODE.
- "3.8: "Hackers of the Lost RAID"". OpenBSD Release Songs. OpenBSD. 2005-11-01. http://www.openbsd.org/lyrics.html#38.
- Andrews, Jeremy (2006-05-02), "Interview: Theo de Raadt", KernelTrap (Jeremy Andrews), http://kerneltrap.org/node/6550
- "Protest against ATI nearly led to the arrest of RMS". Free Software Foundation. 27 April 2006. https://www.fsf.org/blogs/community/rms-ati-protest.html.
- "Explaining Why We Don't Endorse Other Systems". GNU Project. Free Software Foundation. https://www.gnu.org/distros/common-distros.html.
- "Debian firmware-linux packages". 2010. https://packages.debian.org/firmware-linux.
- "a/lt-binary". lwn.net. https://lwn.net/1999/0211/a/lt-binary.html.
- Greg Kroah-Hartman (June 2008). "A position statement on Linux Kernel Modules". The Linux Foundation. https://lwn.net/Articles/287056/.
- Greg Kroah-Hartman (2006). "Myths, Lies, and Truths about the Linux kernel". Linux Symposium. http://www.kroah.com/log/linux/ols_2006_keynote.html.
- "Nonfree Firmware". GNU Project § Free System Distribution Guidelines (GNU FSDG). Free Software Foundation. https://www.gnu.org/distros/free-system-distribution-guidelines.html#nonfree-firmware.
- "::[FSFLA:: Take your freedom back, with Linux-2.6.33-libre"]. fsfla.org. https://www.fsfla.org/ikiwiki/anuncio/2010-03-Linux-2.6.33-libre.en.
- Jonathan Gray (2006-12-02). "Driver Architecture and Implementation in OpenBSD". OpenCON 2006, 2–3 December 2006. Courtyard Venice Airport, Venice/Tessera, Italy. http://www.openbsd.org/papers/opencon06-drivers/index.html. Retrieved 2019-03-27. "drivers designed for binary only Linux RAID management tools"
- Theo de Raadt (2005-09-09). "RAID management support coming in OpenBSD 3.8". misc@ (Mailing list). OpenBSD. https://marc.info/?l=openbsd-misc&m=112630095818062
- "OpenBSD Works To Open Wireless Chipsets". KernelTrap. November 2, 2004. http://kerneltrap.org/node/4118.
- "/sys/dev/microcode/". OpenBSD. http://openbsd.su/src/sys/dev/microcode/.
- "sysutils/firmware". OpenBSD ports. http://openbsd.su/ports/sysutils/firmware.
- "Intel vPro Technology". Intel.com. 2012-05-14. http://www.intel.com/content/www/us/en/architecture-and-technology/vpro/vpro-technology-general.html.
- "BIOS & Firmware Compatibility". Absolute.com. https://www.absolute.com/en/partners/bios-compatibility.aspx.
- Vincent Zimmer; Jiming Sun; Marc Jones; Stefan Reinauer (2015). Embedded Firmware Solutions: Development Best Practices for the Internet of Things. Apress. p. 121. ISBN 9781484200704.
- Vincent Zimmer; Jiming Sun; Marc Jones; Stefan Reinauer (2015). Embedded Firmware Solutions: Development Best Practices for the Internet of Things. Apress. p. 61. ISBN 9781484200704.
- Vincent Zimmer; Jiming Sun; Marc Jones; Stefan Reinauer (2015). Embedded Firmware Solutions: Development Best Practices for the Internet of Things. Apress. p. 65. ISBN 9781484200704.
- "Campaign for Free BIOS". Free Software Foundation. 2006-11-29. https://www.fsf.org/campaigns/free-bios.html.





