
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Marius-Constantin Vochin | -- | 3233 | 2022-09-27 11:17:02 | | | |
| 2 | Amina Yu | + 1 word(s) | 3234 | 2022-09-30 09:41:11 | | | | |
| 3 | Amina Yu | Meta information modification | 3234 | 2022-09-30 09:41:52 | | | | |
| 4 | Rita Xu | -4 word(s) | 3230 | 2024-04-17 05:25:41 | | |
Video Upload Options
Traditional power grid models are based on a central system for generating and distributing energy and have undergone significant changes in recent years. The integration of the latest generation of technologies, rare in critical infrastructure such as the Internet of Things (IoT), has facilitated the evolution to a more dynamic and connected power grid model now known as the Smart Grid (SG). SG’s contributions result from introducing a mutual flow of information between manufacturers and customers, from which both can benefit. This flow enables fine-grained consumption measurements reported to each energy service provider in near real-time to provide consumers with up-to-date price data or control a utility that contains the grid’s energy load in real-time according to actual demand, allowing utilities to perform accurate demand response procedures by anticipating high demand peaks, avoiding and mitigating power outages, and distributing the load on available generators. On the other hand, consumers can take part in programs that reduce electricity consumption in the event of rising energy prices while using home-generated (renewable) electricity (such as the so-called microgrid).
1. Introduction
The above measurement model is called Advanced Metering Infrastructure (AMI) [1]. Technically speaking, this infrastructure consists of several interconnected elements that collect home-measured consumption data, later passed to the power company via an aggregation point. Part of this information is analyzed through Meter Data Management Systems [2]. As a result, further control procedures for the system include industry and information technology equipment (integrated throughout the infrastructure) and correct usage of devices and resources by all involved parties. The architecture for capturing measurement information from IoT devices and consistently controlling power generation contributes to the development of cybersecurity attacks that can compromise resource availability and thus network stability. Access control is essential to manage permissions for all users, processes, and heterogeneous devices that interact continuously within the infrastructure in this complex environment. Therefore, it is imperative to consider the full range of requirements for this scenario to apply the available solutions accurately and propose hybrid access control mechanisms with integrated security monitoring mechanisms.
2. Authorization in Smart Grid (SG)
2.1. Definition and Participants
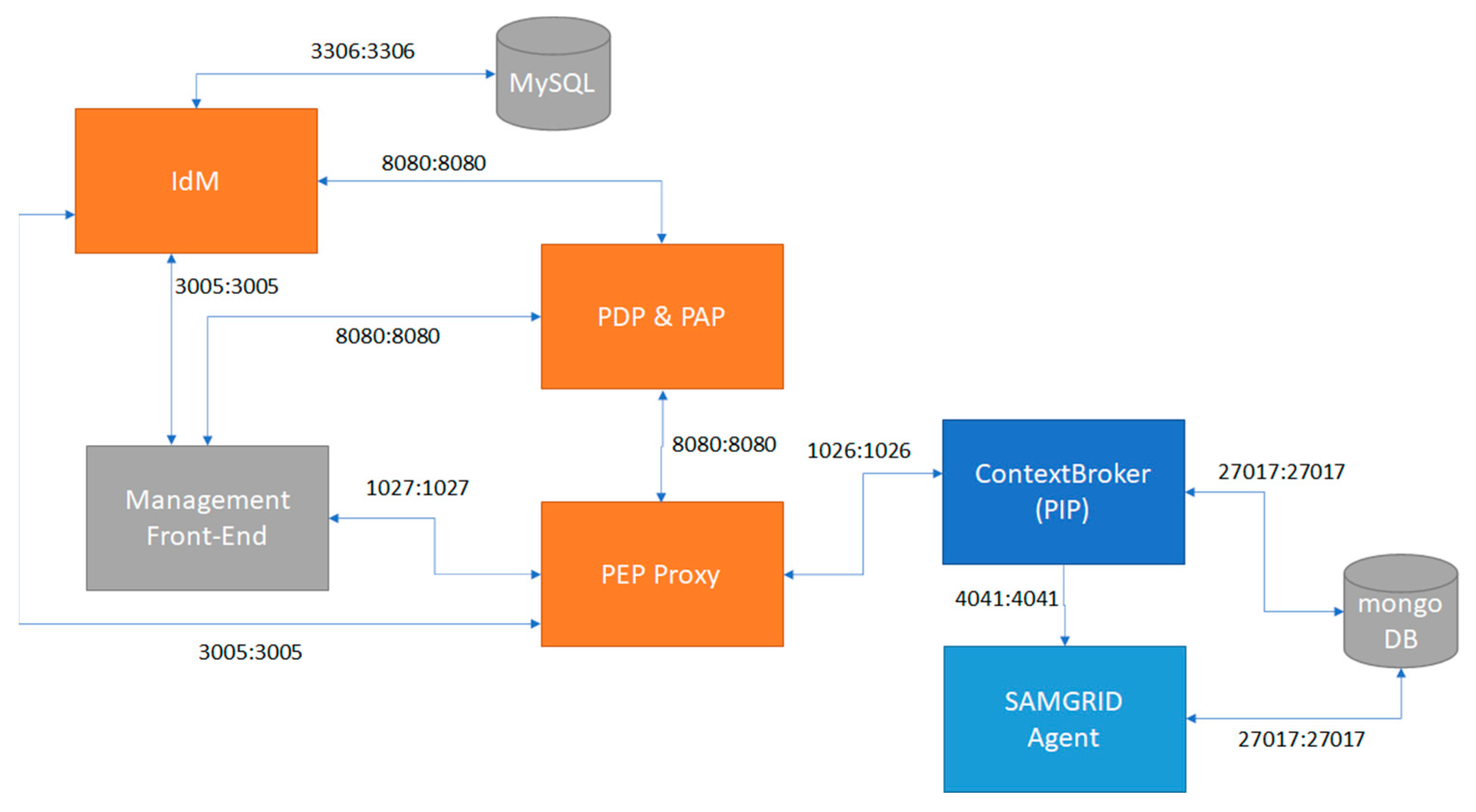
2.2. Motivating Examples
2.3. Security and Functional Requirements
2.3.1. Security Requirements
- S1.
-
Data confidentiality: Data exchanged within a SG ecosystem should be available only to SG components with the respective privilege.
- S2.
-
Data integrity and authenticity: Data exchanged among the participating SG components should be safeguarded against alteration and replication; thus, these should be capable of verifying the origin of the acquired data.
- S3.
-
Accountability: Devices, handlers/employees and end-users should be accountable for their actions.
- S4.
-
Non-repudiation: Devices, handlers and end-users should not be able to deny their actions.
- S5.
-
Physical protection: All electronic devices that participate in a SG ecosystem should contain protection mechanisms to prevent being tampered by adversaries with physical access.
2.3.2. Functional Requirements
- F1.
-
Time consuming: As it is well known, the SG concept aims to support real-time services to its end-user. Thus, the implemented application for authentication, authorization, policy updating should not consume much time and deplete the available sources.
- F2.
-
Scalability: A SG ecosystem should consist of applications that are capable of handling the numerous fluctuations of grid’s size (e.g., nodes can join and leave a grid) without negatively affecting their performance.
- F3.
-
Delegated access control: Any application access must be authenticated and authorized by a security policy, and the granting decisions must be made relying on a trusted party.
- F4.
-
Authorization: Any access to applications must be authorized according to a security policy.
- F5.
-
Authentication: Requesters should be authenticated before accessing any application.
3. Security Authorization Approaches
4. Opinion Dynamics Approaches
References
- Ghosal, A.; Conti, M. Key management systems for smart grid advanced metering infrastructure: A survey. IEEE Commun. Surv. Tutor. 2019, 21, 2831–2848.
- Rendroyoko, I.; Setiawan, A.D. Development of Meter Data Management System Based-on Event-Driven Streaming Architecture for IoT-based AMI Implementation. In Proceedings of the 2021 3rd International Conference on High Voltage Engineering and Power Systems (ICHVEPS), Bandung, Indonesia, 5 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 403–407.
- Bolgouras, V.; Ntantogian, C.; Panaousis, E.; Xenakis, C. Distributed key management in microgrids. IEEE Trans. Ind. Inform. 2019, 16, 2125–2133.
- Karopoulos, G.; Ntantogian, C.; Xenakis, C. MASKER: Masking for privacy-preserving aggregation in the smart grid ecosystem. Comput. Secur. 2018, 73, 307–325.
- Farao, A.; Veroni, E.; Ntantogian, C.; Xenakis, C. P4G2Go: A Privacy-Preserving Scheme for Roaming Energy Consumers of the Smart Grid-to-Go. Sensors 2021, 21, 2686.
- Suciu, G.; Istrate, C.I.; Vulpe, A.; Sachian, M.A.; Vochin, M.; Farao, A.; Xenakis, C. Attribute-based access control for secure and resilient smart grids. In Proceedings of the 6th International Symposium for ICS & SCADA Cyber Security Research 2019, Athens, Greece, 10–12 September 2019; pp. 67–73.
- Suciu, G.; Istrate, C.; Sachian, M.A.; Vulpe, A.; Vochin, M.; Farao, A.; Xenakis, C. FI-WARE authorization in a Smart Grid scenario. In Proceedings of the 2020 Global Internet of Things Summit (GIoTS), Dublin, Ireland, 3 June 2020; IEEE: Piscataway, NJ, USA; pp. 1–5.
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51.
- FireEye. Cyber Attacks on the Ukrainian Grid: What You Should Know. 2015. Available online: https://www.fireeye.com/content/dam/fireeye-www/global/en/solutions/pdfs/fe-cyber-attacks-ukrainian-grid.pdf (accessed on 17 May 2022).
- Kaspersky. BlackEnergy APT Attack in Ukraine. Available online: https://www.kaspersky.com/resource-center/threats/blackenergy (accessed on 17 March 2022).
- Wired. The Untold Story of a Cyberattack, a Hospital and a Dying Woman. Available online: https://www.wired.co.uk/article/ransomware-hospital-death-germany (accessed on 17 March 2022).
- Nbc News. Colonial Announces Pipeline Restart, Says Normal Service Will Take ‘Several Days’. Available online: https://www.nbcnews.com/tech/security/colonial-announces-pipeline-restart-says-normal-service-will-take-seve-rcna917 (accessed on 17 March 2022).
- Hackers Breached Colonial Pipeline Using Compromised Password. Available online: https://www.bloomberg.com/news/articles/2021-06-04/hackers-breached-colonial-pipeline-using-compromised-password (accessed on 17 March 2022).
- Farao, A.; Panda, S.; Menesidou, S.A.; Veliou, E.; Episkopos, N.; Kalatzantonakis, G.; Mohammadi, F.; Georgopoulos, N.; Sirivianos, M.; Salamanos, N.; et al. SECONDO: A platform for cybersecurity investments and cyber insurance decisions. In Proceedings of the International Conference on Trust and Privacy in Digital Business, Bratislava, Slovakia, 14–17 September 2020; Springer: Cham, Switzerland, 2020; pp. 65–74.
- The Cyber Kill Chain. Available online: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html (accessed on 17 March 2022).
- Yadav, T.; Rao, A.M. Technical aspects of cyber kill chain. In Proceedings of the International Symposium on Security in Computing and Communication, Kochi, India, 10 August 2015; Springer: Cham, Switzerland, 2015; pp. 438–452.
- Rubio, J.E.; Alcaraz, C.; Lopez, J. Preventing advanced persistent threats in complex control networks. In Proceedings of the European Symposium on Research in Computer Security, Oslo, Norway, 11–15 September 2017; Volume 10493, pp. 402–418.
- Mitre Att&Ck. Available online: https://attack.mitre.org/ (accessed on 17 March 2022).
- Nisioti, A.; Loukas, G.; Laszka, A.; Panaousis, E. Data-driven decision support for optimizing cyber forensic investigations. IEEE Trans. Inf. Forensics Secur. 2021, 16, 2397–2412.
- Rubio, J.E.; Roman, R.; Alcaraz, C.; Zhang, Y. Tracking apts in industrial ecosystems: A proof of concept. J. Comput. Secur. 2019, 27, 521–546.
- Rubio, J.E.; Roman, R.; Lopez, J. Integration of a threat traceability solution in the industrial internet of things. IEEE Trans. Ind. Inform. 2020, 16, 6575–6583.
- Gopstein, A.; Nguyen, C.; O’Fallon, C.; Hastings, N.; Wollman, D. NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release 4.0; NIST Special Publication; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021.
- Alcaraz, C.; Lopez, J. Secure interoperability in cyber-physical systems. In Cyber Warfare and Terrorism: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2020; pp. 521–542.
- Hasankhani, A.; Hakimi, S.M.; Bisheh-Niasar, M.; Shafie-khah, M.; Asadolahi, H. Blockchain technology in the future smart grids: A comprehensive review and frameworks. Int. J. Electr. Power Energy Syst. 2021, 129, 106811.
- Javaid, N.; Gul, H.; Baig, S.; Shehzad, F.; Xia, C.; Guan, L.; Sultana, T. Using GANCNN and ERNET for Detection of Non-Technical Losses to Secure Smart Grids. IEEE Access 2021, 9, 98679–98700.
- Yang, H.; Liu, S.; Fang, C. Model-based secure load frequency control of smart grids against data integrity attack. IEEE Access 2020, 8, 159672–159682.
- Boudko, S.; Aursand, P.; Abie, H. Evolutionary Game for Confidentiality in IoT-enabled Smart Grids. Information 2020, 11, 582.
- Veichtlbauer, A.; Engel, D.; Knirsch, F.; Langthaler, O.; Moser, F. Advanced metering and data access infrastructures in smart grid environments. In Proceedings of the Seventh International Conference on Sensor Technologies and Applications (SENSORCOMM) 2013, Barcelona, Spain, 25–31 August 2013; pp. 63–68, ISBN 978-1-61208-296-7.
- Alcaraz, C.; Lopez, J.; Wolthusen, S. Policy enforcement system for secure interoperable control in distributed smart grid systems. J. Netw. Comput. Appl. 2016, 59, 301–314.
- Duan, L.; Liu, D.; Zhang, Y.; Chen, S.; Liu, R.P.; Cheng, B.; Chen, J. Secure data-centric access control for smart grid services based on publish/subscribe systems. ACM Trans. Internet Technol. (TOIT) 2016, 16, 1–7.
- Alcarria, R.; Bordel, B.; Robles, T.; Martín, D.; Manso-Callejo, M.Á. A blockchain-based authorization system for trustworthy resource monitoring and trading in smart communities. Sensors 2018, 18, 3561.
- “OpenWay Riva”, Itron. Available online: https://blogs.itron.com/tag/openway-riva/ (accessed on 17 March 2022).
- French, J.R., Jr. A formal theory of social power. Psychol. Rev. 1956, 63, 181.
- DeGroot, M.H. Reaching a consensus. J. Am. Stat. Assoc. 1974, 69, 118–121.
- Dong, Y.; Zhan, M.; Kou, G.; Ding, Z.; Liang, H. A survey on the fusion process in opinion dynamics. Inf. Fusion 2018, 43, 57–65.
- Noorazar, H. Recent advances in opinion propagation dynamics: A 2020 survey. Eur. Phys. J. Plus 2020, 135, 1–20.
- Grabisch, M.; Rusinowska, A. A Survey on Nonstrategic Models of Opinion Dynamics. Games 2020, 11, 65.
- Lopez, J.; Rubio, J.E.; Alcaraz, C. A resilient architecture for the smart grid. IEEE Trans. Ind. Inform. 2018, 14, 3745–3753.
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094.




