
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Mulugeta Kassaw Tefera | -- | 4714 | 2022-05-19 11:08:09 | | | |
| 2 | Vivi Li | -15 word(s) | 4699 | 2022-05-20 04:23:39 | | | | |
| 3 | Vivi Li | -6 word(s) | 4693 | 2022-05-23 08:06:01 | | |
Video Upload Options
With the proliferation of 5G mobile networks within next-generation wireless communication, the design and optimization of 5G networks are progressing in the direction of improving the physical layer security (PLS) paradigm. This phenomenon is due to the fact that traditional methods for the network optimization of PLS fail to adapt new features, technologies, and resource management to diversified demand applications. To improve these methods, future 5G and beyond 5G (B5G) networks will need to rely on new enabling technologies. Therefore, approaches for PLS design and optimization that are based on artificial intelligence (AI) and machine learning (ML) have been corroborated to outperform traditional security technologies. This will allow future 5G networks to be more intelligent and robust in order to significantly improve the performance of system design over traditional security methods.
1. Introduction
| Existing Papers | Research Issues | Important Content |
|---|---|---|
| [12] | Examine the security threats and corresponding defense methods in PHY security. | Summary of the security requirements and threats in wireless networks considering the network protocols at various levels of data layers. Additionally, a comprehensive review of state-of-the-art PHY security and existing security protocols for 13 various wireless networks. |
| [25] | A comprehensive survey on the basic theories and key technologies of PHY security. | Discussion of the key technologies, limitations, and solutions of PHY security from the perspective of security coding, physical-layer authentication, secret key generation, and multi-antenna techniques. |
| [26] | Security threats and the corresponding countermeasure techniques. | Technologies, security attacks, and defense mechanisms in PHY security using game-theoretic approaches. |
| [27] | Overview of the key technologies of PHY security. | Recent technologies, optimization techniques, and limitations of PHY security from the perspective of information-theoretic security and wiretap channels. |
| [28] | A comprehensive investigation of multi-antenna techniques. | Survey of multi-antenna techniques in multi-user networks for improving the security performance of PHY security, but not considering CSI accuracy. |
| [29] | A brief survey on multi-antenna techniques. | Investigation on multi-antenna techniques in PHY security for improving secrecy performance considering the accuracy of CSI. |
| [30] | A comprehensive overview of the optimization and design strategies of PHY security. | Survey on security designs and optimization techniques from the viewpoints of information theory and security metrics in wireless PHY security. |
| [31] | Comprehensive overview of all existing PHY security techniques. | Classification of the existing PHY security techniques and brief discussion of the big picture they can be easily understood and applied in different communication systems. |
| [32] | Challenges of PHY security in real-world systems. | Identification of the existing assumptions and opportunities for applying PHY security in practical applications. |
| [34] | A comprehensive investigation of AI and edge computing (EC) for PLS. |
Identification of the existing challenges in the design and optimization of PLS and design of an enhancement scheme for PLS application. |
2. Fundamental Concepts
2.1. Generic System Model
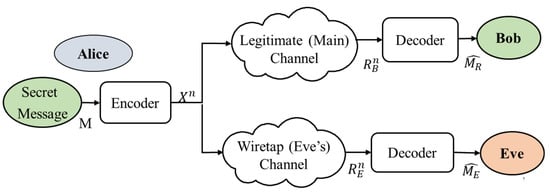
2.2. Wireless Adversary Models
3. Research Directions for System Designs and Optimization Concepts

3.1. Main Technical Challenges in System Design
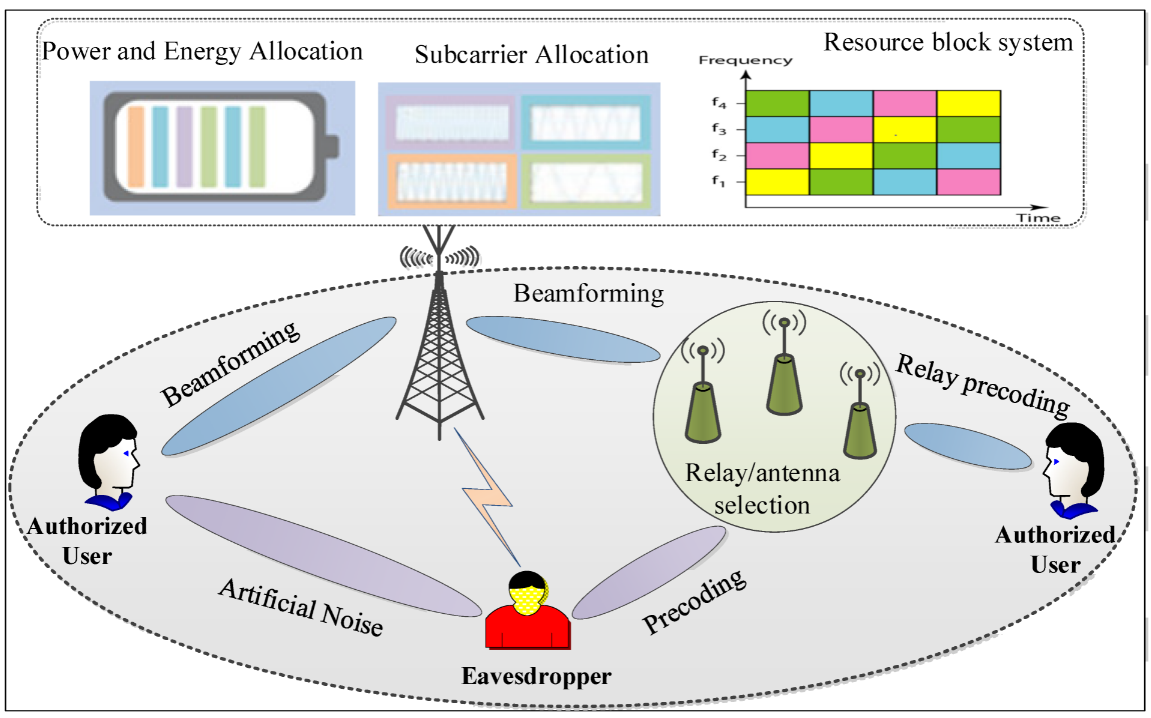
3.2. Optimization in PHY Security: Current Status and Main Issues
3.2.1. Convex Optimization Techniques
3.2.2. Secure Beamforming Techniques
3.2.3. Artificial Noise (AN) Techniques
3.2.4. Zero-Forcing (ZF) Precoding Techniques
References
- Wang, C.X.; Haider, F.; Gao, X.; You, X.H.; Yang, Y.; Yuan, D.; Aggoune, H.M.; Haas, H.; Fletcher, S.; Hepsaydir, E. Cellular architecture and key technologies for 5G wireless communication networks. IEEE Commun. Mag. 2014, 52, 122–130.
- Rawat, S.; Chaturvedi, P. A QoS Aware RA Algorithm for OFDM Network. J. Eng. Educ. Transform. 2015, 2349–2473.
- Chou, S.F.; Pang, A.C.; Yu, Y.J. Energy-aware 3D unmanned aerial vehicle deployment for network throughput optimization. IEEE Trans. Wirel. Commun. 2019, 19, 563–578.
- Hindumathi, V.; Reddy, K.R.L. A Proficient Fair Resource Allocation in the Channel of Multiuser Orthogonal Frequency Division Multiplexing using a Novel Hybrid Bat-Krill Herd Optimization. Wirel. Pers. Commun. 2021, 120, 1449–1473.
- Zhou, L.; Wu, D.; Wei, X.; Dong, Z. Seeing Isn’t Believing: QoE Evaluation for Privacy-Aware Users. IEEE JSAC 2019, 37, 1656–1665.
- Zorgui, M. Wireless Physical Layer Security: On the Performance Limits of Secret-Key Agreement. Masters’s Thesis, King Abdullah University of Science and Technology, Thuwal, Saudi Arabia, 2015.
- Campagna, M.; Chen, L.; Dagdelen, O.; Ding, J.; Fernick, J.; Gisin, N.; Hayford, D.; Jennewein, T.; Lütkenhaus, N.; Mosca, M.; et al. Quantum Safe Cryptography and Security: An Introduction, Benefits, Enablers and Challenges; European Telecommunications Standards Institute: Sophia Antipolis, France, 2015; Volume 8, pp. 1–64.
- Shiu, Y.S.; Chang, S.Y.; Wu, H.C.; Huang, S.C.H.; Chen, H.H. Physical layer security in wireless networks: A tutorial. IEEE Wireless Commun. 2011, 18, 66–74.
- Mukherjee, A. Physical-layer security in the Internet of Things: Sensing and communication confidentiality under resource constraints. Proc. IEEE 2015, 103, 1747–1761.
- Liu, Y.; Chen, H.H.; Wang, L. Secrecy Capacity Analysis of Artificial Noisy MIMO Channels—An Approach based on Ordered Eigenvalues of Wishart Matrices. IEEE Trans. Inf. Forensics Secur. 2016, 99, 1.
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Di Renzo, M. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27.
- Wang, C.; Wang, H.M. Physical layer security in millimeter wave cellular networks. IEEE Trans. Wirel. Commun. 2016, 15, 5569–5585.
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 104, 1727–1765.
- Barros, J.; Rodrigues, M.R. Secrecy capacity of wireless channels. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–16 July 2006; pp. 356–360.
- Jeon, H.; Kim, N.; Choi, J.; Lee, H.; Ha, J. Bounds on secrecy capacity over correlated ergodic fading channels at high SNR. IEEE Trans. Inf. Theory 2011, 57, 1975–1983.
- Saad, W.; Zhou, X.; Han, Z.; Poor, H.V. On the physical layer security of backscatter wireless systems. IEEE Trans. Wirel. Commun. 2014, 13, 3442–3451.
- Basciftci, Y.O.; Gungor, O.; Koksal, C.E.; Ozguner, F. On the secrecy capacity of block fading channels with a hybrid adversary. IEEE Trans. Inf. Theory 2015, 61, 1325–1343.
- Zhang, N.; Cheng, N.; Lu, N.; Zhang, X.; Mark, J.W.; Shen, X. Partner selection and incentive mechanism for physical layer security. IEEE Trans. Wirel. Commun. 2015, 14, 4265–4276.
- Bashar, S.; Ding, Z. Optimum power allocation against information leakage in wireless network. In Proceedings of the GLOBECOM 2009—2009 IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009; pp. 1–6.
- Wang, X.; Tao, M.; Mo, J.; Xu, Y. Power and subcarrier allocation for physical-layer security in OFDMA-based broadband wireless networks. IEEE Trans. Inf. Forensics Secur. 2011, 6, 693–702.
- Du, Y.N.; Han, S.; Xu, S.; Li, C. Improving secrecy under high correlation via discriminatory channel estimation. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6.
- Hong, Y.W.P.; Lan, P.C.; Kuo, C.C.J. Signal Processing Approaches to Secure Physical Layer Communications in Multi-Antenna Wireless Systems; Springer: New York, NY, USA, 2014.
- Liu, R.; Trappe, W. Securing Wireless Communications at the Physical Layer; Springer: New York, NY, USA, 2010.
- Baldi, M.; Tomasin, S. (Eds.) Physical and Data-Link Security Techniques for Future Communication Systems; Springer International: Cham, Switzerland, 2016.
- Liu, Y.; Chen, H.H.; Wang, L. Physical layer security for next generation wireless networks: Theories, technologies, and challenges. IEEE Commun. Surv. Tutor. 2017, 19, 347–376.
- Sharma, R.K.; Rawat, D.B. Advances on security threats and countermeasures for cognitive radio networks: A survey. IEEE Commun. Surv. Tutor. 2014, 17, 1023–1043.
- Sanenga, A.; Mapunda, G.A.; Jacob, T.M.L.; Marata, L.; Basutli, B.; Chuma, J.M. An overview of key technologies in physical layer security. Entropy 2020, 22, 1261.
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573.
- Chen, X.; Ng, D.W.; Gerstacker, W.H.; Chen, H.H. A Survey on Multiple-Antenna Techniques for Physical Layer Security. IEEE Commun. Surv. Tutor. 2017, 19, 1027–1053.
- Wang, D.; Bai, B.; Zhao, W.; Han, Z. A Survey of Optimization Approaches for Wireless Physical Layer Security. IEEE Commun. Surv. Tutor. 2019, 21, 1878–1911.
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and applications of physical layer security techniques for confidentiality: A comprehensive survey. IEEE Commun. Surv. Tutor. 2018, 21, 1773–1828.
- Trappe, W. The challenges facing physical layer security. IEEE Commun. Mag. 2015, 53, 16–20.
- Mao, Q.; Hu, F.; Hao, Q. Deep Learning for Intelligent Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2018, 20, 2595–2621.
- Zhao, L.; Zhang, X.; Chen, J.; Zhou, L. Physical layer security in the age of artificial intelligence and edge computing. IEEE Wirel. Commun. 2020, 27, 174–180.
- Xiao, L.; Sheng, G.; Liu, S.; Dai, H.; Peng, M.; Song, J. Deep Reinforcement Learning-Enabled Secure Visible Light Communication against Eavesdropping. IEEE Trans. Commun. 2019, 67, 6994–7005.
- Gui, L.; He, B.; Zhou, X.; Yu, C.; Shu, F.; Li, J. Learning-Based Wireless Powered Secure Transmission. IEEE Wirel. Commun. Lett. 2019, 8, 600–603.
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387.
- Li, H.; Wang, X. Physical-Layer Security Enhancement in Wireless Communication Systems. Master’s Thesis, the University of Western Ontario London, Ontario, Canada, 2013.
- Zheng, G.; Choo, L.C.; Wong, K.K. Optimal cooperative jamming to enhance physical layer security using relays. IEEE Trans. Signal Process. 2011, 59, 1317–1322.
- He, X.; Yener, A. On the Role of Feedback in Two-Way Secure Communication. In Proceedings of the 2008 42nd Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 26–29 October 2008; pp. 1093–1097.
- He, X.; Yener, A. Providing Secrecy When the Eavesdropper Channel is Arbitrarily Varying: A Case for Multiple Antennas. In Proceedings of the 2010 48th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 29 September–1 October 2010; pp. 1228–1235.
- Liao, W.C.; Chang, T.H.; Ma, W.K.; Chi, C.Y. QoS-based transmit beamforming in the presence of eavesdroppers: An optimized artificial-noise aided approach. IEEE Trans. Signal Process. 2011, 59, 1202–1216.
- Reboredo, H.; Xavier, J.; Rodrigues, M.R.D. Filter design with secrecy constraints: The MIMO Gaussian wiretap channel. IEEE Trans. Signal Process. 2013, 61, 3799–3814.
- Li, M.; Kundu, S.; Pados, D.A.; Batalama, S.N. Waveform design for secure SISO transmissions and multicasting. IEEE J. Sel. Areas Commun. 2013, 31, 1864–1874.
- Wang, H.M.; Xia, X.-G. Enhancing wireless secrecy via cooperation: Signal design and optimization. IEEE Commun. Mag. 2015, 53, 47–53.
- Hong, Y.W.P.; Lan, P.C.; Kuo, C.C.J. Enhancing physical-layer secrecy in multiantenna wireless systems: An overview of signal processing approaches. IEEE Signal Process. Mag. 2013, 30, 29–40.
- Yener, A.; Ulukus, S. Wireless physical-layer security: Lessons learned from information theory. Proc. IEEE 2015, 103, 1814–1825.
- Boyd, S.; Boyd, S.P.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004.
- Bai, B.; Chen, W.; Cao, Z. Outage optimal subcarrier allocation for downlink secure OFDMA systems. In Proceedings of the IEEE Global Communications Conference (GLOBECOM) Workshops, Austin, TX, USA, 8–12 December 2014; pp. 1320–1325.
- Jindal, A.; Bose, R. Resource allocation for secure multicarrier AF relay system under total power constraint. IEEE Commun. Lett. 2014, 19, 231–234.
- Chen, J.; Chen, X.; Gerstacker, W.H.; Ng, D.W.K. Resource allocation for a massive MIMO relay aided secure communication. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1700–1711.
- Ng, D.W.K.; Lo, E.S.; Schober, R. Secure resource allocation and scheduling for OFDMA decode-and-forward relay networks. IEEE Trans. Wirel. Commun. 2011, 10, 3528–3540.
- Huang, J.; Swindlehurst, A.L. Robust secure transmission in MISO channels based on worst-case optimization. IEEE Trans. Signal Process. 2012, 60, 1696–1707.
- Jeong, C.; Kim, I.M. Optimal power allocation for secure multicarrier relay systems. IEEE Trans. Signal Process. 2011, 59, 5428–5442.
- Tsai, S.H.; Poor, H.V. Power allocation for artificial-noise secure MIMO precoding systems. IEEE Trans. Signal Process. 2014, 62, 3479–3493.
- Wang, L.; Elkashlan, M.; Huang, J.; Tran, N.H.; Duong, T.Q. Secure transmission with optimal power allocation in untrusted relay networks. IEEE Wireless Commun. Lett. 2014, 3, 289–292.
- Benfarah, A.; Tomasin, S.; Laurenti, N. Power allocation in multiuser parallel Gaussian broadcast channels with common and confidential messages. IEEE Trans. Commun. 2016, 64, 2326–2339.
- Zheng, T.X.; Wang, H.M. Optimal power allocation for artificial noise under imperfect CSI against spatially random eavesdroppers. IEEE Trans. Veh. Technol. 2016, 65, 8812–8817.
- Oggier, F.; Hassibi, B. The secrecy capacity of the MIMO wiretap channel. IEEE Trans. Inf. Theory 2011, 57, 4961–4972.
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennas I: The MISOME wiretap channel. IEEE Trans. Inf. Theory 2010, 56, 3088–3104.
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennas—Part II the MIMOME wiretap channel. IEEE Trans. Inf. Theory 2010, 56, 5515–5532.
- Sheng, Z.; Tuan, H.D.; Sheng, Z.; Tuan, H.D.; Duong, T.Q.; Vincent Poor, H. Beamforming Optimization for Physical Layer Security in MISO Wireless Networks. IEEE Trans. Signal Process. 2018, 66, 3710–3723.
- Palomar, D.P.; Chiang, M. A tutorial on decomposition methods for network utility maximization. IEEE J. Sel. Areas Commun. 2006, 24, 1439–1451.
- Yaacoub, E.; Al-Husseini, M. Achieving physical layer security with massive MIMO beamforming. In Proceedings of the 2017 11th European Conference Antennas Propagation, EUCAP 2017, Paris, France, 19–24 March 2017; pp. 1753–1757.
- Shafiee, S.; Liu, N.; Ulukus, S. Towards the secrecy capacity of the Gaussian MIMO wire-tap channel: The 2-2-1 channel. IEEE Transactions on Information Theory 2009, 55, 4033–4039.
- Björnson, E.; Bengtsson, M.; Ottersten, B. Optimal multiuser transmit beamforming: A difficult problem with a simple solution structure . IEEE Signal Process. Mag. 2014, 31, 142–148.
- Mo, J.; Tao, M.; Liu, Y.; Wang, R. Secure beamforming for MIMO two-way communications with an untrusted relay. IEEE Trans. Signal Process. 2014, 62, 2185–2199.
- Liu, Z.; Chen, C.; Bai, L.; Xiang, H.; Choi, J. Secure beamforming via amplify-and-forward relays in wireless networks with multiple eavesdroppers. In Proceedings of the IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 4698–4703.
- Jeong, C.; Kim, I.M.; Kim, D.I. Joint secure beamforming design at the source and the relay for an amplify-and-forward MIMO untrusted relay system. IEEE Trans. Signal Process. 2012, 60, 310–325.
- Zhao, P.; Zhang, M.; Yu, H.; Luo, H.; Chen, W. Robust beamforming design for sum secrecy rate optimization in MU-MISO networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1812–1823.
- Shi, Q.; Xu, W.; Wu, J.; Song, E.; Wang, Y. Secure beamforming for MIMO broadcasting with wireless information and power transfer. IEEE Trans. Wirel. Commun. 2015, 14, 2841–2853.
- Wang, X.; Wang, K.; Zhang, X.D. Secure relay beamforming with imperfect channel side information. IEEE Trans. Veh. Technol. 2013, 62, 2140–2155.
- Zheng, G.; Arapoglou, P.D.; Ottersten, B. Physical layer security in multibeam satellite systems. IEEE Trans. Wirel. Commun. 2012, 11, 852–863.
- Nghia, N.T.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. MIMO beamforming for secure and energy-efficient wireless communication. IEEE Signal Process. Lett. 2017, 24, 236–239.
- Nasir, A.A.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. Secure and energy-efficient beamforming for simultaneous information and energy transfer. IEEE Trans. Wirel. Commun. 2017, 16, 7523–7537.
- Zhao, N.; Yu, F.R.; Sun, H. Adaptive energy-efficient power allocation in green interference-alignment-based wireless networks. IEEE Trans. Veh. Technol. 2014, 64, 4268–4281.
- Pu, W.; Xiao, J.; Zhang, T.; Luo, Z.Q. Overcoming dof limitation in robust beamforming: A penalized inequality-constrained approach. arXiv 2019, arXiv:1910.03365.
- Liu, S.; Hong, Y.; Viterbo, E. Practical secrecy using artificial noise. IEEE Commun. Lett. 2013, 17, 1483–1486.
- Li, Q.; Ma, W.K. Spatially selective artificial-noise aided transmit optimization for MISO multi-eves secrecy rate maximization. IEEE Trans. Signal Process. 2013, 61, 2704–2717.
- Lin, P.H.; Lai, S.H.; Lin, S.C.; Su, H.J. On secrecy rate of the generalized artificial-noise assisted secure beamforming for wiretap channels. IEEE J. Sel. Areas Commun. 2013, 31, 1728–1740.
- Yang, N.; Yan, S.; Yuan, J.; Malaney, R.; Subramanian, R.; Land, I. Artificial noise: Transmission optimization in multi-input single-output wiretap channels. IEEE Trans. Commun. 2015, 63, 1771–1783.
- Wang, B.; Mu, P.; Li, Z. Secrecy rate maximization with artificial noise-aided beamforming for MISO wiretap channels under secrecy outage constraint. IEEE Commun. Lett. 2015, 19, 18–21.
- Tang, Y.; Xiong, J.; Ma, D.; Zhang, X. Robust artificial noise aided transmit design for MISO wiretap channels with channel uncertainty. IEEE Commun. Lett. 2013, 17, 2096–2099.
- Reboredo, H.; Prabhu, V.; Rodrigues, M.R.; Xavier, J. Filter design with secrecy constraints: The multiple-input multiple-output Gaussian wiretap channel with zero forcing receive filters. In Proceedings of the 2011 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Prague, Czech Republic, 22–27 May 2011; pp. 3440–3443.
- Rezki, Z.; Alouini, M.S. On the finite-SNR diversity-multiplexing tradeoff of zero-forcing transmit scheme under secrecy constraint. In Proceedings of the IEEE International Conference Communication Workshops (ICC Workshops), Kyoto, Japan, 5–9 June 2011; pp. 1–5.




