
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Hadeel Alrubayyi | + 2433 word(s) | 2433 | 2021-11-04 04:54:25 | | | |
| 2 | Conner Chen | Meta information modification | 2433 | 2021-11-10 05:12:17 | | |
Video Upload Options
Malware is a major security threat to the IoT, and detecting unknown malware is one of the key challenges for two reasons. First, the limitations of IoT devices, such as their low power retention capability and low computational processing capability, represent a significant challenge when aiming to apply security solutions. Second, introducing new ways to connect networks, such as cloud services, opens the door to many security attacks, such as malware attacks. Furthermore, connecting new devices that were not part of traditional networks via these new connection methods, such as smart sensors, makes applying security measures more complex. For these reasons, traditional malware detection mechanisms are not suitable for the IoT environment.
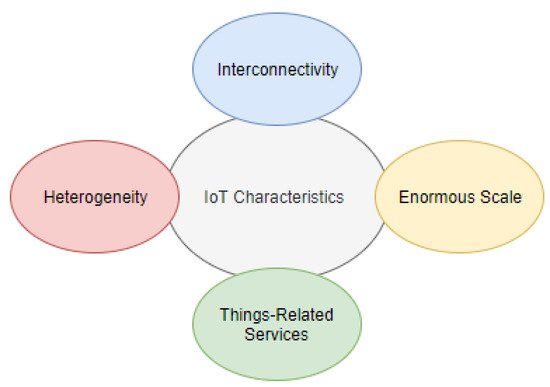
1. IoT Characteristics and Challenges on Security
-
Interconnectivity refers to the connection of the device to the cloud and/or other devices. Connectivity is needed to enable the control of the device remotely, but mostly to access the data collected by the IoT device’s sensors. For example, an IoMT device for heart disease prediction is remotely controlled to monitor the patient’s heart rate [7]. The health parameters are collected in real-time and transmitted to a data center in the cloud. Therefore, securing this connection is vital to protect critical information.
-
The IoT devices are heterogeneous as they may be built on different platforms and have different specifications. The hardware, such as a simple sensor to monitor the heart rate in [7], and virtual things, such as a data center built on the cloud, could be supplied by different vendors. These integrated IoT devices could use different security measures, leading to a lack of standardization in the network. Each connected device could use different security protocols, with their security bugs and limitations, exposing the system to different kinds of hacking.
-
In the IoT environment, physical and virtual devices are capable of exchanging services within the constraints of the devices. Since the communication between different IoT devices is not controlled by a central processor/human, this could form a serious threat. If a malicious device is disguised as an accepted IoT device, it could start to disturb other devices by installing malicious files.
-
The number of IoT devices is increasing exponentially and is generating an unprecedented amount of data. The expected number of IoT devices by 2025 is between 25 billion and 50 billion [8]. The scale is simply enormous, and data privacy and integrity are critical challenges in massive-scale networks. For instance, IoMT-based COVID-19 applications are creating massive amounts of real-time data that are stored in the cloud. However, as the amount of generated data continues to increase, the network pressure increases, which might lead to occurrences of erroneous interpretations [9].
2. Malware Analysis and Detection
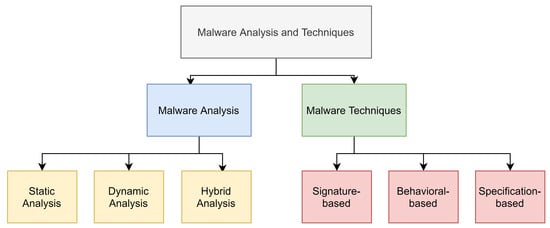
2.1. Malware Analysis
-
Static analysis, also called code analysis: In this technique, the infected file is inspected and analyzed without executing it. Low-level information is extracted such as the control flow graph (CFG), data flow graph, and system calls. Static analysis is fast at analyzing data and safe to use; also, it has a low level of false-positives, which means a higher detection rate. Moreover, the static analysis tracks all possible paths, which gives it a global view; however, it fails in detecting unknown malware using code obfuscation.
-
Dynamic analysis, also called behavioral analysis: In dynamic analysis, the infected file is inspected during execution, which is usually conducted on an invisible virtual machine, so the malware file does not change its behaviors. Dynamic analysis is time-consuming and vulnerable, and it can only detect a few paths based on triggered files. Furthermore, it is neither safe nor fast, and it suffers from a high level of false positives. However, dynamic analysis is known for its good performance in detecting new and unknown malware.
-
Hybrid analysis: this technique was designed to overcome the challenges and limitations of the previous two techniques. First, it analyzes the signature descriptions of any malware code and then combines that with other dynamic parameters to improve the analysis of malware.
2.2. Malware Detection Techniques
-
In the signature-based technique, files are analyzed and compared to an existing list, and if they are listed in the list, they are classified as malware. This method is not effective for recognizing all malware that enters the network because some malware is encrypted, and thus extracting the signature takes time and a large amount of processing energy. Furthermore, it is not effective for new or unknown malware.
-
The behavioral-based method monitors the program’s behavior rather than reading its signature. This technique follows three steps: the first step collects information about the program, the second step interprets the data through conversion to intermediate representations, and the last step matches the intermediate representation with known behavior signatures. There are two approaches to this technique, the first of which is simulating the behavior of legitimate programs and comparing any new program to that model. This approach works for the detection of most malware, even new kinds. However, it is expensive to implement because of the different behaviors of each program in the network; for example, a video reader will use different services than a mail or a web client. The second approach is simulating the behavior of known malware and comparing it to new programs, which means new (unknown) malware cannot be identified.
-
The specification-based method was introduced to overcome the disadvantages and limitations of the first two techniques. This technique uses different features for malware detection, including the following:
- (a)
-
API calls: Hofmeyr et al. were among the first to propose using application interface and system call sequences for malware detection [14].
- (b)
-
OpCode: Executable files are made of series of assembly codes, and in this method, researchers use this operational code to detect malware [15].
- (c)
-
N-Grams: this method uses executable programs’ binary codes for malware detection [16].
- (d)
-
CFG: This is a graph that illustrates the control flow of programs, and it has been used to analyze malware behavior [17].
- (e)
-
Hybrid feature: in this machine learning method, researchers combine different techniques for malware detection to get better results. For example, Eskandari et al. in [18] used CFG and API calls for metamorphic malware detection.
- (f)
-
Game theoretic-based anomaly detection algorithms: Zhu, Quanyan, and T. Başar presented different solutions to malware detection using behavioral analysis, such as the data exfiltration detection and prevention and consensus algorithm, with censored data for distributed detection [19].
- (g)
-
Prospect theoretic approaches: These approaches are based on measuring the trustworthiness of the aggregated data in the system. In [20], the authors present a hardware trojan detection game based on prospective theory approaches. Furthermore, in [21], the authors introduce a prospect theory-based framework to ensure risk awareness and protect network operations.
3. Malware in the IoT
References
- Othman, M.; El-Mousa, A. Internet of Things Cloud Computing Internet of Things as a Service Approach. In Proceedings of the 2020 11th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 7–9 April 2020; pp. 318–323.
- Asghari, P.; Rahmani, A.M.; Javadi, H.H.S. Internet of Things applications: A systematic review. Comput. Netw. 2019, 148, 241–261.
- Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT Communications: A Survey. Sensors 2020, 20, 4828.
- Marathe, S.; Nambi, A.; Swaminathan, M.; Sutaria, R. CurrentSense: A novel approach for fault and drift detection in environmental IoT sensors. In Proceedings of the International Conference on Internet-of-Things Design and Implementation, Charlottesvle, VA, USA, 18–21 May 2021; pp. 93–105.
- Lv, Z.; Qiao, L.; Kumar Singh, A.; Wang, Q. AI-Empowered IoT Security for Smart Cities. ACM Trans. Internet Technol. 2021, 21.
- Xenofontos, C.; Zografopoulos, I.; Konstantinou, C.; Jolfaei, A.; Khan, M.K.; Choo, K.K.R. Consumer, Commercial and Industrial IoT (In)Security: Attack Taxonomy and Case Studies. IEEE Internet Things J. 2021.
- Khan, M.; Algarni, F. A Healthcare Monitoring System for the Diagnosis of Heart Disease in the IoMT Cloud Environment Using MSSO-ANFIS. IEEE Access 2020, 8, 122259–122269.
- Zhang, J.; Li, G.; Marshall, A.; Hu, A.; Hanzo, L. A New Frontier for IoT Security Emerging From Three Decades of Key Generation Relying on Wireless Channels. IEEE Access 2020, 8, 138406–138446.
- Lin, H.; Garg, S.; Hu, J.; Wang, X.; Piran, M.J.; Hossain, M.S. Privacy-enhanced Data Fusion for COVID-19 Applications in Intelligent Internet of Medical Things. IEEE Internet Things J. 2020.
- Aldhaheri, S.; Alghazzawi, D.; Cheng, L.; Barnawi, A.; Alzahrani, B. Artificial Immune Systems approaches to secure the internet of things: A systematic review of the literature and recommendations for future research. J. Netw. Comput. Appl. 2020, 157, 102537.
- Jeon, J.; Park, J.; Jeong, Y. Dynamic Analysis for IoT Malware Detection With Convolution Neural Network Model. IEEE Access 2020, 8, 96899–96911.
- Greensmith, J. Securing the Internet of Things with Responsive Artificial Immune Systems. In Proceedings of the 2015 Annual Conference on Genetic and Evolutionary Computation (GECCO ’15); Association for Computing Machinery, Madrid, Spain, 18–21 May 2021; pp. 113–120.
- Aslan, Ö.; Samet, R. A comprehensive review on malware detection approaches. IEEE Access 2020, 8, 6249–6271.
- Hofmeyr, S.; Forrest, S.; Somayaji, A. Intrusion Detection Using Sequences of System Calls. J. Comput. Secur. 1998, 6, 151–180.
- Bilar, D. Opcodes as Predictor for Malware. Int. J. Electron. Secur. Digit. Forensic 2007, 1, 156–168.
- Schultz, M.; Eskin, E.; Zadok, F.; Stolfo, S. Data mining methods for detection of new malicious executables. In Proceedings of the 2001 IEEE Symposium on Security and Privacy. S & P 2001, Oakland, CA, USA, 14–16 May 2001; pp. 38–49.
- Jalote, P. An Integrated Approach to Software Engineering; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012.
- Eskandari, M.; Hashemi, S. Metamorphic malware detection using control flow graph mining. Int. J. Comput. Sci. Netw. Secur 2011, 11, 1–6.
- Buttyán, L.; Baras, J.S. Decision and Game Theory for Security; Springer: Berlin/Heidelberg, Germany, 2010.
- Saad, W.; Sanjab, A.; Wang, Y.; Kamhoua, C.A.; Kwiat, K.A. Hardware Trojan Detection Game: A Prospect-Theoretic Approach. IEEE Trans. Veh. Technol. 2017, 66, 7697–7710.
- Vamvakas, P.; Tsiropoulou, E.E.; Papavassiliou, S. Exploiting prospect theory and risk-awareness to protect UAV-assisted network operation. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 1–20.
- Pandey, S.K.; Mehtre, B. A lifecycle based approach for malware analysis. In Proceedings of the 2014 Fourth International Conference on Communication Systems and Network Technologies, Bhopal, India, 7–9 April 2014; pp. 767–771.
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad hoc Netw. 2013, 11, 2661–2674.
- Abusnaina, A.; Anwar, A.; Alshamrani, S.; Alabduljabbar, A.; Jang, R.; Nyang, D.; Mohaisen, D. Systemically Evaluating the Robustness of ML-based IoT Malware Detectors. In Proceedings of the 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks-Supplemental Volume (DSN-S), Taipei, Taiwan, 21–24 June 2021; pp. 3–4.
- Wu, H.; Han, H.; Wang, X.; Sun, S. Research on Artificial Intelligence Enhancing Internet of Things Security: A Survey. IEEE Access 2020, 8, 153826–153848.
- SonicWall 2019 Report: 55 Rise in IoT Malware Attacks. 2019. Available online: https://www.openaccessgovernment.org/iot-malware-attacks/69870/ (accessed on 1 October 2021).
- Muncaster, P. Over 100 Million IoT Attacks Detected in 1H 2019. 2019. Available online: https://www.infosecurity-magazine.com/news/over-100-million-iot-attacks/ (accessed on 1 October 2021).




