Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Cesar Muñoz | + 814 word(s) | 814 | 2021-06-16 08:23:27 | | | |
| 2 | Vicky Zhou | + 2 word(s) | 816 | 2021-07-15 02:17:22 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Muñoz, C. Radio Frequency Identification. Encyclopedia. Available online: https://encyclopedia.pub/entry/12076 (accessed on 07 February 2026).
Muñoz C. Radio Frequency Identification. Encyclopedia. Available at: https://encyclopedia.pub/entry/12076. Accessed February 07, 2026.
Muñoz, Cesar. "Radio Frequency Identification" Encyclopedia, https://encyclopedia.pub/entry/12076 (accessed February 07, 2026).
Muñoz, C. (2021, July 14). Radio Frequency Identification. In Encyclopedia. https://encyclopedia.pub/entry/12076
Muñoz, Cesar. "Radio Frequency Identification." Encyclopedia. Web. 14 July, 2021.
Copy Citation
Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore drawing the attention of many researchers.
RFID
radio frequency identification
scientometric
bibliometrics
data science
ScientoPy
1. Introduction
It is expected that technology will work for us in more transparent and ubiquitous ways. RFID is implemented in many contexts, such as logistics [1][2], supply chains [3][4], asset tracking [5][6][7], healthcare [8][9], industrial enterprise environments [5][6], and many others, making our lives easier and generating vast quantities of information on many levels.
2. RFID Applications
RFID technology is making its way into various fields, sometimes keeping a low profile. However, it is becoming more relevant in people’s lives, creating paths to new applications and complementing known ones. In some cases, these applications do not directly interact with people, but RFID supports different processes for realizing products and services used daily. Accordingly, with reason, RFID is sometimes seen as a requirement or core technology for the Internet of things (IoT). This is affirmed by the total documents published on this topic, positioning IoT well above other applications. RFID supports many applications of the Internet of Things due to characteristics such as high volume, non-contact reading, tag features and, more importantly, low price. The situation is clearly reflected in the graphs (a) and (b) in Figure 1, with the more prominent indicators in Table 1.
In second place, we have supply chain management, in which RFID is essential for identification and information capture for real-time management, using different methods such as frameworks and protocols. This allows high versatility due to the variety of tags available; all these processes are continually studied to solve security issues and possible vulnerabilities. RFID is also used in localization applications, extending the primary function of the technology, representing the second-largest activity in terms of the percentage of documents in last years (PDLY), as shown in Table 1. For traceability and logistics, RFID supports a variety of applications in supply chains and shop floor deployment. RFID is opening paths to new applications in an ever more ubiquitous fashion, blending into our lives much more, such as in healthcare spaces for ensuring data security and allowing more robust management of patients, equipment, and personnel. Similarly, it is applied to support the control of access to physical spaces and systems or enforcing the control of access to information captured by different sensors along with RFID. All these findings are presented in detail in the following sections and represented graphically in Figure 1. This chapter presents the top research applications identified through the scientometric analysis.
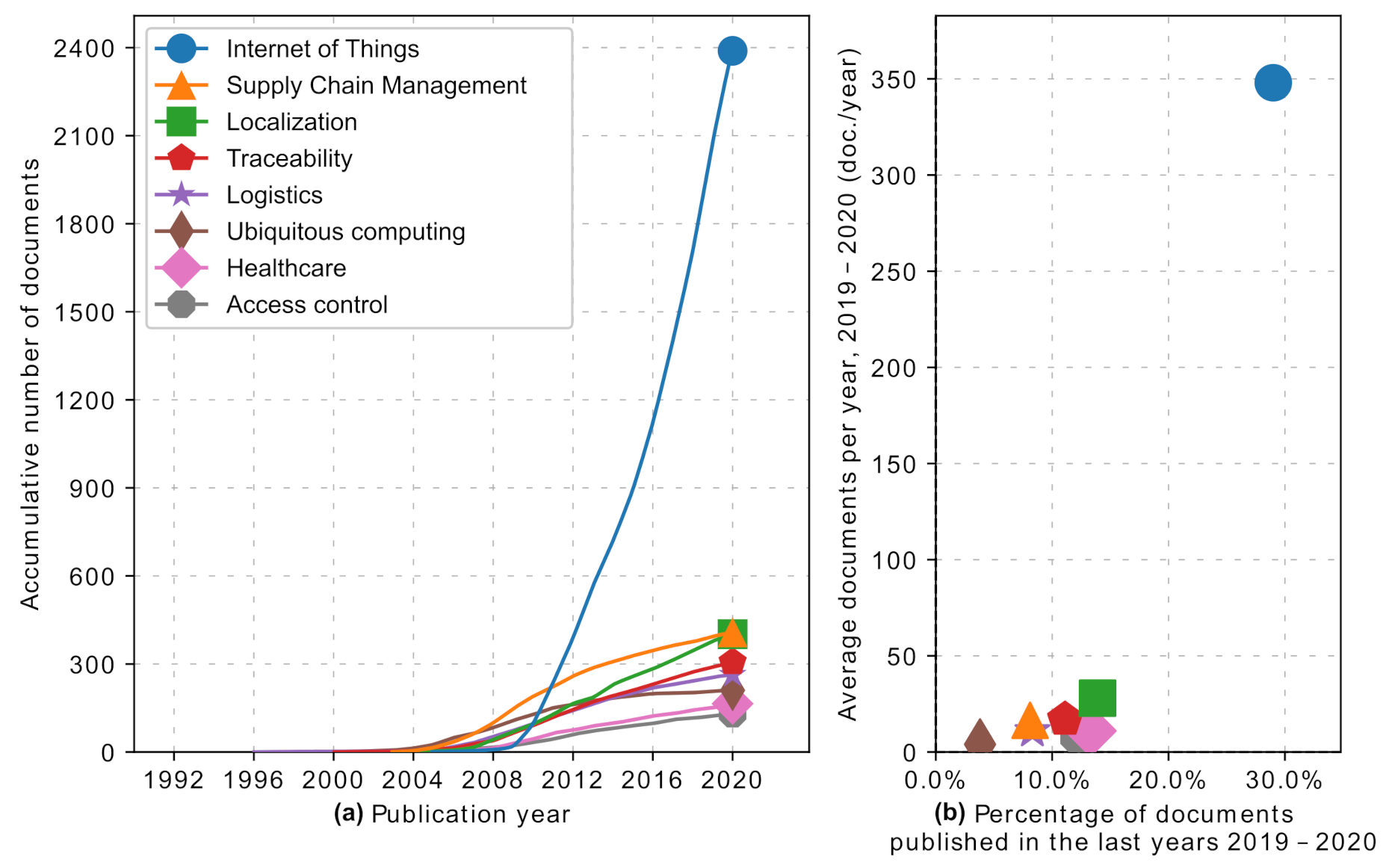 Figure 1. (a) Top applications, and number of publications by year. (b) Average number of publications per year and percentage of documents published between 2019 and 2020.
Figure 1. (a) Top applications, and number of publications by year. (b) Average number of publications per year and percentage of documents published between 2019 and 2020.Table 1. Top author keywords for RFID applications.
| Pos | Author Keywords | Total | AGR | ADY | PDLY | h-Index |
|---|---|---|---|---|---|---|
| 1 | Internet of Things | 2399 | 8.0 | 348.0 | 29.0 | 73 |
| 2 | Supply Chain Management | 408 | 1.0 | 16.5 | 8.1 | 49 |
| 3 | Localization | 402 | −4.5 | 28.0 | 13.9 | 32 |
| 4 | Traceability | 307 | −1.5 | 17.0 | 11.1 | 29 |
| 5 | Logistics | 264 | −1.5 | 11.0 | 8.3 | 20 |
| 6 | Ubiquitous Computing | 210 | 0.5 | 4.0 | 3.8 | 25 |
| 7 | Healthcare | 165 | 1.0 | 11.0 | 13.3 | 23 |
| 8 | Access Control | 131 | 2.0 | 8.0 | 12.2 | 14 |
3. Facts about RFID
Applications of RFID technologies were found in many contexts, from asset identification to tracking for industrial [5][6] and general [7] public environment applications, for instance, indoor applications [10][11], robot navigation [12][13][14][15], and the positioning of objects, even those not visible [16][17][18]. Ultra-wideband has been used to overcome some of the current problems with narrowband frequencies [19][20]. Additionally, it helps organizations with management and safety for construction [21][22] and pushes the limits of transmission signals’ ability to enhance the quality [23][24][25][26] in different frequencies [6][20].
We found privacy and authenticity to be of utmost concern [27][28][29]. Herein, we focused on the most active RFID applications based on scientometric variables, resulting in eleven groups. The applications characterized for this technology especially concern the IoT, which supports the idea that RFID is a key requirement for the Internet of Things [30][31][32]. We also found RFID to be applied in supply chains [33][34], providing ways to detect counterfeiting [35][36] and keep track of any asset [37][38][39][40][41]. The most active security topics appear to be testing the existing protocols to search for flaws, ways to solve them [42][43][44][45][46][47][48], and balancing privacy and performance for different scenarios [49][50][47][48][51]. It was found that privacy and security are of general concern, almost in all applications. In addition, it was noted that healthcare is a topic that shows a positive AGR in the results, and it includes RFID in different related operations [8][9][52][53][54][55][56][57][58][59][60][61][62][63]. RFID is also used in access control, such as for managing access to spaces and systems [44][64][65][66][45][46], and its use in the human body has also been explored from different perspectives [67][68][69].
RFID is used in diverse scenarios and continues to grow in its applications and functionalities, such as working with wireless sensors and IPv6, the new addressing system for the IoT, expanding its frequencies wherein technological advances are permitted (currently to ultra-wideband). Thus, this technology can find emerging utility in RF, electronics, and security, and it is not an exaggeration to state that RFID will be the technology that will allow reaching the point, through the IoT, where every existing object will be able to be connected to the Internet.
References
- Zhong, R.Y.; Lan, S.; Xu, C.; Dai, Q.; Huang, G.Q. Visualization of RFID-enabled shopfloor logistics Big Data in Cloud Manufacturing. Int. J. Adv. Manuf. Technol. 2016, 84, 5–16.
- Zhong, R.Y.; Xu, C.; Chen, C.; Huang, G.Q. Big Data Analytics for Physical Internet-based intelligent manufacturing shop floors. Int. J. Prod. Res. 2017, 55, 2610–2621.
- Gaukler, G.M.; Seifert, R.W.; Hausman, W.H. Item-level RFID in the retail supply chain. Prod. Oper. Manag. 2007, 16, 65–76.
- Loebbecke, C.; Huyskens, C.; Gogan, J. Emerging technologies in the service sector: An early exploration of item-level RFID on the fashion sales floor. In Proceedings of the International Working Conference on Information Technology in the Service Economy—Challenges and Possibilities for the 21st Century, Toronto, ON, Canada, 10–13 August 2008; Springer: Berlin/Heidelberg, Germany, 2008; Volume 267, pp. 189–198.
- Velandia, D.M.S.; Kaur, N.; Whittow, W.G.; Conway, P.P.; West, A.A. Towards industrial internet of things: Crankshaft monitoring, traceability and tracking using RFID. Robot.-Comput.-Integr. Manuf. 2016, 41, 66–77.
- Zhai, C.; Zou, Z.; Zhou, Q.; Mao, J.; Chen, Q.; Tenhunen, H.; Zheng, L.; Xu, L. A 2.4-GHz ISM RF and UWB hybrid RFID real-time locating system for industrial enterprise Internet of Things. Enterp. Inf. Syst. 2017, 11, 909–926.
- Yang, L.; Chen, Y.; Li, X.Y.; Xiao, C.; Li, M.; Liu, Y. Tagoram: Real-Time Tracking of Mobile RFID Tags to High Precision Using COTS Devices. In Proceedings of the 20th ACM Annual International Conference on Mobile Computing and Networking (MobiCom), Maui, HI, USA, 7–11 September 2014; Association for Computing Machinery Learned Society: New York, NY, USA, 2014; pp. 237–248.
- Amendola, S.; Lodato, R.; Manzari, S.; Occhiuzzi, C.; Marrocco, G. RFID Technology for IoT-Based Personal Healthcare in Smart Spaces. IEEE Internet Things J. 2014, 1, 144–152.
- Jara, A.J.; Zamora, M.A.; Skarmeta, A.F.G. An internet of things-based personal device for diabetes therapy management in ambient assisted living (AAL). Pers. Ubiquitous Comput. 2011, 15, 431–440.
- Saab, S.S.; Nakad, Z.S. A Standalone RFID Indoor Positioning System Using Passive Tags. IEEE Trans. Ind. Electron. 2011, 58, 1961–1970.
- Ma, Y.; Zhou, L.; Liu, K.; Wang, J. Iterative Phase Reconstruction and Weighted Localization Algorithm for Indoor RFID-Based Localization in NLOS Environment. IEEE Sens. J. 2014, 14, 597–611.
- Han, S.; Lim, H.; Lee, J. An efficient localization scheme for a differential-driving mobile robot based on RFID system. IEEE Trans. Ind. Electron. 2007, 54, 3362–3369.
- Park, S.; Lee, H. Self-Recognition of Vehicle Position Using UHF Passive RFID Tags. IEEE Trans. Ind. Electron. 2013, 60, 226–234.
- Catarinucci, L.; Tedesco, S.; Tarricone, L. Customized Ultra High Frequency Radio Frequency Identification Tags and Reader Antennas Enabling Reliable Mobile Robot Navigation. IEEE Sens. J. 2013, 13, 783–791.
- Kim, M.; Chong, N.Y. RFID-based mobile robot guidance to a stationary target. Mechatronics 2007, 17, 217–229.
- Wang, J.; Katabi, D. Dude, Where’s My Card? RFID Positioning That Works with Multipath and Non-Line of Sight. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 51–62.
- Akkaya, K.; Guvenc, I.; Aygun, R.; Pala, N.; Kadri, A. IoT-based Occupancy Monitoring Techniques for Energy-Efficient Smart Buildings. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 58–63.
- Lee, E.K.; Oh, S.Y.; Gerla, M. RFID assisted vehicle positioning in VANETs. Pervasive Mob. Comput. 2012, 8, 167–179.
- Saidi, K.S.; Teizer, J.; Franaszek, M.; Lytle, A.M. Static and dynamic performance evaluation of a commercially-available ultra wideband tracking system. Autom. Constr. 2011, 20, 519–530.
- Dardari, D.; D’Errico, R.; Roblin, C.; Sibille, A.; Win, M.Z. Ultrawide Bandwidth RFID: The Next Generation? Proc. IEEE 2010, 98, 1570–1582.
- Fang, Y.; Cho, Y.K.; Zhang, S.; Perez, E. Case Study of BIM and Cloud-Enabled Real-Time RFID Indoor Localization for Construction Management Applications. J. Constr. Eng. Manag. 2016, 142.
- Lee, H.S.; Lee, K.P.; Park, M.; Baek, Y.; Lee, S. RFID-Based Real-Time Locating System for Construction Safety Management. J. Comput. Civ. Eng. 2012, 26, 366–377.
- Brchan, J.; Zhao, L.; Wu, J.; Williams, R.; Perez, L. A real-time RFID localization experiment using propagation models. In Proceedings of the 2012 6th IEEE International Conference on RFID, Orlando, FL, USA, 3–5 April 2012; pp. 141–148.
- Hekimian-Williams, C.; Grant, B.; Liu, X.; Zhang, Z.; Kumar, P. Accurate localization of RFID tags using phase difference. In Proceedings of the 4th Annual IEEE International Conference on RFID, Orlando, FL, USA, 14–15 April 2010; pp. 89–96.
- Zhou, C.; Griffin, J.D. Accurate Phase-Based Ranging Measurements for Backscatter RFID Tags. IEEE Antennas Wirel. Propag. Lett. 2012, 11, 152–155.
- Kronberger, R.; Knie, T.; Leonardi, R.; Dettmar, U.; Cremer, M.; Azzouzi, S. UHF RFID Localization System Based on a Phased Array Antenna. In Proceedings of the IEEE International Symposium on Antennas and Propagation (APSURSI)/USNC/URSI National Radio Science Meeting, Spokane, WA, USA, 3–8 July 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 525–528.
- David, M.; Prasad, N.R. Providing Strong Security and High Privacy in Low-Cost RFID Networks. In Proceedings of the 1st International ICST Conference, Turin, Italy, 03–05 June 2009; Volume 17, pp. 172–179.
- Chen, C.L.; Chen, Y.Y.; Huang, Y.C.; Liu, C.S.; Lin, C.I.; Shih, T.F. Anti-counterfeit ownership transfer protocol for low cost RFID system. WSEAS Trans. Comput. 2008, 7, 1149–1158.
- Li, T.; Jin, Z.; Pang, C. Secured ownership transfer scheme for low-cost RFID tags. In Proceedings of the 3rd International Conference on Intelligent Networks and Intelligent Systems, Shenyang, China, 1–3 November 2010; pp. 584–587.
- Jia, X.; Feng, Q.; Fan, T.; Lei, Q. RFID technology and its applications in Internet of Things (IoT). In Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks, Yichang, China, 21–23 April 2012; pp. 1282–1285.
- Aggarwal, R.; Das, M. RFID security in the context of internet of things. In Proceedings of the 1st International Conference on Security of Internet of Things, Kollam, India, 17–19 August 2012; pp. 51–56.
- Chen, B.; Dai, Y.; Jin, B.; Zou, X.; Zhou, L. The RFID-based electronic identity security platform of the Internet of Things. In Proceedings of the 2011 International Conference on Mechatronic Science, Electric Engineering and Computer, Jilin, China, 19–22 August 2011; pp. 246–249.
- Sahin, E.; Dallery, Y.; Gershwin, S. Performance evaluation of a traceability system: An application to the radio frequency identification technology. In Proceedings of the 2002 IEEE International Conference on Systems, Man and Cybernetics, Yasmine Hammamet, Tunisia, 6–9 October 2002; Volume 3, pp. 647–650.
- Zelbst, P.J.; Green Kenneth, W., Jr.; Sower, V.E.; Baker, G. RFID utilization and information sharing: The impact on supply chain performance. J. Bus. Ind. Mark. 2010, 25, 582–589.
- Coustasse, A.; Arvidson, C.; Rutsohn, P. Pharmaceutical counterfeiting and the RFID technology intervention. J. Hosp. Mark. Public Relat. 2010, 20, 100–115.
- Taylor, D. RFID in the Pharmaceutical Industry: Addressing Counterfeits with Technology. J. Med Syst. 2014, 38.
- Wyld, D. Genuine medicine?: Why safeguarding the pharmaceutical supply chain from counterfeit drugs with RFID is vital for protecting public health and the health of the pharmaceutical industry. Compet. Rev. 2008, 18, 206–216.
- Kelepouris, T.; Pramatari, K.; Doukidis, G. RFID-enabled traceability in the food supply chain. Ind. Manag. Data Syst. 2007, 107, 183–200.
- Parreno-Marchante, A.; Alvarez-Melcon, A.; Trebar, M.; Filippin, P. Advanced traceability system in aquaculture supply chain. J. Food Eng. 2014, 122, 99–109.
- Abad, E.; Palacio, F.; Nuin, M.; Gonzalez de Zarate, A.; Juarros, A.; Gomez, J.M.; Marco, S. RFID smart tag for traceability and cold chain monitoring of foods: Demonstration in an intercontinental fresh fish logistic chain. J. Food Eng. 2009, 93, 394–399.
- Hsu, Y.C.; Chen, A.P.; Wang, C.H. A RFID-Enabled Traceability System for the Supply Chain of Live Fish. In Proceedings of the IEEE International Conference on Automation and Logistics, Qingdao, China, 1–3 September 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 81–86.
- Li, Y.; Ding, X. Protecting RFID communications in supply chains. In Proceedings of the 2nd ACM Symposium on Information, Computer and Communications Security, Singapore, 20–22 March 2007; pp. 234–241.
- Singh, M.; Li, X.; Li, Z. Security and privacy protection in RFID-enabled supply chain management. Int. J. Radio Freq. Identif. Technol. Appl. 2011, 3, 294–318.
- Henseler, M.; Rossberg, M.; Schaefer, G. Credential Management for Automatic Identification Solutions in Supply Chain Management. IEEE Trans. Ind. Inform. 2008, 4, 303–314.
- Kerschbaum, F. An Access Control Model for Mobile Physical Objects. In Proceedings of the 15th ACM Symposium on Access Control Models and Technologies, Pittsburgh, PA, USA, 9–11 June 2010; pp. 193–202.
- Atluri, V.; Shin, H.; Vaidya, J. Efficient security policy enforcement for the mobile environment. J. Comput. Secur. 2008, 16, 439–475.
- Hoque, M.E.; Rahman, F.; Ahamed, S.I.; Park, J.H. Enhancing Privacy and Security of RFID System with Serverless Authentication and Search Protocols in Pervasive Environments. Wirel. Pers. Commun. 2010, 55, 65–79.
- Shih, D.H.; Lin, C.Y.; Lin, B. RFID tags: Privacy and security aspects. Int. J. Mob. Commun. 2005, 3, 214–230.
- Weber, R. Internet of Things—New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30.
- Molnar, D.; Wagner, D. Privacy and security in library RFID issues, practices, and architectures. In Proceedings of the 11th ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; pp. 210–219.
- Yang, G.; Geng, G.; Du, J.; Liu, Z.; Han, H. Security threats and measures for the Internet of Things. Qinghua Daxue Xuebao/J. Tsinghua Univ. 2011, 51, 1335–1340.
- Esposito, A.; Tarricone, L.; Zappatore, M.; Catarinucci, L.; Colella, R. A framework for context-aware home-health monitoring. Int. J. Auton. Adapt. Commun. Syst. 2010, 3, 75–91.
- Lopez-de Ipina, D.; Diaz-de Sarralde, I.; Garcia-Zubia, J. An Ambient Assisted Living Platform Integrating RFID Data-on-Tag Care Annotations and Twitter. J. Univers. Comput. Sci. 2010, 16, 1521–1538.
- Wamba, S.; Ngai, E. Internet of things in healthcare: The case of RFID-enabled asset management. Int. J. Biomed. Eng. Technol. 2013, 11, 318–335.
- Liu, C.F.; Gu, Y.M. The Research of Intelligent Medical Devices Management System Based on RFID Technology. In Proceedings of the International Conference on Information System and Artificial Intelligence (ISAI), Hong Kong, China, 24–26 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 29–33.
- Adame, T.; Bel, A.; Carreras, A.; Melia-Segui, J.; Oliver, M.; Pous, R. CUIDATS: An RFID-WSN hybrid monitoring system for smart health care environments. Future Gener. Comput.-Syst.- Int. J. Escience 2018, 78, 602–615.
- Tsirbas, H.; Giokas, K.; Koutsouris, D. “Internet of Things”, an RFID—IPv6 scenario in a healthcare environment. In Proceedings of the 12th Mediterranean Conference on Medical and Biological Engineering and Computing, Chalkidiki, Greece, 27–30 May 2010; Volume 29, pp. 808–811.
- Fan, K.; Jiang, W.; Li, H.; Yang, Y. Lightweight RFID Protocol for Medical Privacy Protection in IoT. IEEE Trans. Ind. Inform. 2018, 14, 1656–1665.
- Jisha, S.; Philip, M. Rfid based security platform for internet of things in health care environment. In Proceedings of the Online International Conference on Green Engineering and Technologies (IC-GET), Coimbatore, India, 19 November 2016; IEEE: Piscataway, NJ, USA, 2016.
- Ai, L.; Jun, D.Z.; Yun, S.; Ling, W.X. The intelligent signing system of internet of things about environmental health workers based on RFID. In Proceedings of the 6th International Conference on Electronics and Information Engineering (ICEIE), Dalian, China, 26–27 September 2015; 2015; Volume 9794.
- Almanza-Ojeda, D.L.; Hernandez-Gutierrez, A.; Ibarra-Manzano, M.A. Design and implementation of a vehicular access control using RFID. In Proceedings of the 3rd International Conference on Advanced Optoelectronics and Lasers/3rd International Conference on Precision Oscillations in Electronics and Optics/1st International Workshop on Image and Signal Processing (MEP 2006), Guanajuato, MEXICO, 7–11 November 2006; IEEE: Piscataway, NJ, USA, 2006.
- Park, N. Customized Healthcare Infrastructure Using Privacy Weight Level Based on Smart Device. In Proceedings of the 5th International Conference on Convergence and Hybrid Information Technology (ICHIT), Daejeon, Korea, 22–24 September 2011; Volume 206, pp. 467–474.
- Rahman, F.; Bhuiyan, M.Z.A.; Ahamed, S.I. A privacy preserving framework for RFID based healthcare systems. Future Gener. Comput.-Syst.- Int. J. Escience 2017, 72, 339–352.
- Qi, S.; Zheng, Y.; Li, M.; Liu, Y.; Qiu, J. Scalable Industry Data Access Control in RFID-Enabled Supply Chain. IEEE-ACM Trans. Netw. 2016, 24, 3551–3564.
- Deng, H.F.; Deng, W.; Li, H.; Yang, H.J. Authentication and access control in RFID based logistics-customs clearance service platform. Int. J. Autom. Comput. 2010, 7, 180–189.
- Nowicki, T.; Kiedrowicz, M.; Waszkowski, R.; Chodowska, A.; Lach, A. Access control system for RFID-tagged documents in supply chain management. Logforum 2017, 13, 91–101.
- Michael, K.; Michael, M.G. The future prospects of embedded microchips in humans as unique identifiers: The risks versus the rewards. Media Cult. Soc. 2013, 35, 78–86.
- Perakslis, C.; Michael, K. Indian Millennials: Are microchip implants a more secure technology for identification and access control? In Proceedings of the 2012 IEEE Conference on Technology and Society in Asia (T&SA), Singapore, 27–29 October 2012; 2012.
- Perakslis, C.; Michael, K.; Michael, M.G.; Gable, R. Perceived Barriers for Implanting Microchips in Humans: A Transnational Study. In Proceedings of the IEEE Conference on Norbert Wiener in the 21st Century (21CW)—Driving Technology’s Future, Boston, MA, USA, 24–26 June 2014; IEEE: Piscataway, NJ, USA, 2014.
More
Information
Subjects:
Engineering, Electrical & Electronic
Contributor
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.3K
Revisions:
2 times
(View History)
Update Date:
15 Jul 2021
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




