
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Zhiyu Chen | + 1227 word(s) | 1227 | 2020-04-26 10:06:29 | | | |
| 2 | Catherine Yang | Meta information modification | 1227 | 2020-05-11 11:16:46 | | |
Video Upload Options
Considering the complexity of the power grid environment and the diversity of power communication transmission losses, this paper proposes a quantum key distribution (QKD) network structure suitable for power business scenarios. Through the simulation of the power communication transmission environment, the performance indicators of quantum channels and data interaction channels in the power QKD system are tested and evaluated from six aspects, such as distance loss, galloping loss, splice loss, data traffic, encryption algorithm, and system stability. In the actual environment, this paper combines the production business to build a QKD network suitable for power scenarios, and conducts performance analysis. The experimental results show that the power QKD technology can meet the operation index requirements of power business, as well as provide a reference for the large-scale application of the technology.
The traditional power system constructs a network security protection system through security equipment such as firewalls, intrusion detection systems, VPNs and encryption devices, which ensures the secure transmission of data to a certain extent. However, new network attack methods are emerging in an endless stream, which poses new challenges to the security, reliability and timeliness of control/management instruction transmission. In practice, some businesses rely on offline keys to update keys, and the update frequency is slow, which affects the security level of information transmission. Considering that the traditional key online transmission has the hidden danger of being stolen, resulting in insufficient security and timeliness of online key distribution, and further affecting the security performance of the power system. In view of the above, this section proposes a security protection mode based on power QKD technology. At the same time, a new generation of data security transmission architecture based on QKD for dispatching automation, distribution automation, electricity information collection and video conference are designed.
QKD-Based Power Dispatching Automation
The safe and stable operation of the power dispatching automation system needs to meet the characteristics of reliability, safety, integrity, real time and consistency, etc. It is necessary to ensure the safe transmission of instructions and improve the anti-intrusion ability of the system. Traditional power dispatching longitudinal encryption and authentication device (LEAD) has the problems of slow key update and incapable of online secure distribution [1]. Precise data encryption technology based on power QKD technology can effectively prevent threats such as tampering, theft and illegal injection during the transmission of dispatching instructions. Figure 1 shows the QKD-based dispatching automation encryption transmission architecture. In this paper, QKD device is used for key negotiation to avoid key online transmission, and the key online real-time update of LEAD is realized, which solves the shortage of online distribution and update timeliness of traditional encryption key. By adding a key acquisition module, LEAD is transformed, and the method of obtaining the key by encryption device is changed to obtain the quantum key from QKD device. It realizes data encrypted transmission based on quantum key, such as telemetry, remote signaling, remote adjustment, etc. In addition, it guarantees the safe delivery of remote adjustment and remote-control information, the secure uploading of remote monitoring and remote signaling information of dispatching substations, and thus, the secure transmission of power dispatching information.

Figure 1. Dispatching automation system based on QKD.
QKD-Based Distribution Automation
Distribution automation is an important technology that serves the construction of urban distribution networks. The safety of distribution instructions is critical. Compared with dispatching automation, the distribution network is multi-faceted, multiple communication methods coexist, and are greatly affected by environmental and social factors. It is prone to the risk of theft or tampering of unidirectional authentication and message transmission due to insufficient border protection [2]. Considering that the information exchange of new-type urban distribution networks is more frequent and more open, the use of QKD technology to encrypt the transmission data of distribution automation production is proposed. This study uses quantum keys to perform encryption on important authentication information and uses quantum relay technology to ensure long-distance transmission of quantum networks. Finally, tamper-proof and anti-eavesdropping of information distribution is realized, thereby improving the anti-risk capability of the distribution network and ensuring the quality of electricity for urban residents. Figure 2 shows the network structure of quantum key encryption for distribution of automation data.
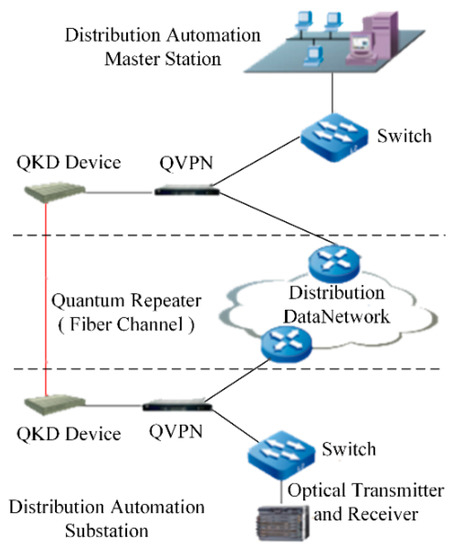
Figure 2. Distribution automation architecture based on QKD.
QKD-Based Electricity Information Collection
The electricity information collection system is one of the important components of the smart grid. It provides timely, complete and accurate feedback of user power consumption information to provide a reference for power control. Since the power consumption information contains a large amount of private data, if the data are manipulated by a third party, it will not only affect the daily power consumption of users, but also cause the leakage of sensitive data and private information [3]. In order to ensure the safe collection of a large number of electricity consumption information, it is necessary to build a highly secure and reliable transmission network. Therefore, QKD technology is used to increase the update frequency of the encryption key for the electricity information collection service, and to ensure the secure data transmission of the electricity information collection system. Figure 3 shows the structure of QKD-based electricity information collection.

Figure 3. Electricity information collection based on QKD.
QKD-Based Video Conference System
The large-scale popularity of the video conference system has improved the efficiency of administrative negotiations, cross-regional consultations and cross-regional exchanges, while reducing the costs of meetings. Accompanying system security issues have gradually become apparent and major decision-making consultations face third-party threats. At the same time, video information has the characteristics of large data volume, controllable encoding rate and strict synchronization. The encryption method is different from text encryption. Combined with the complicated overhead power lines in operation, in order to guarantee the performance of quantum key distribution, QKD equipment with fast deviation feedback function is equipped, and quantum relay equipment is used to guarantee the key rate on large-span lines. As a result, it satisfies the need for secure transmission of large amounts of video data. Finally, high-efficiency, high-security data protection is achieved, and the level of security protection for video conference scenarios in fixed venues and outdoor emergency is improved. Figure 4 shows the operation chart of video conference.
Figure 4. Video conference system based on QKD.
QKD-Based Data Disaster Recovery System
Data disaster recovery refers to the establishment of a remote multi-point backup of data through the establishment of a disaster recovery center to improve resistance to operations during a disaster. According to the security level protection and grading standards of power companies, the security protection level of disaster recovery and backup services is S2A2G2 in the second level. The protection measure of traditional system is to deploy servers with different risk levels in different physical areas, and each area is safely isolated by a firewall. The protective measures are limited, and the level of protection is insufficient. Since the disaster recovery data involves sensitive information of most of the core power business, ensuring the safe transmission of core data of the power grid business is a point worth paying attention to in disaster recovery backup. In order to improve the security of disaster recovery services and rely on the secure distribution mechanism of quantum keys, this paper designs a disaster recovery service system based on the encryption and decryption of quantum key. Figure 5 shows a QKD-based disaster recovery backup system.
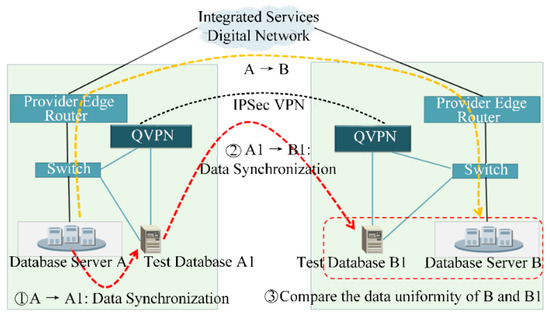
Figure 5. Disaster recovery backup based on QKD.
References
- Dongxu Yang; Hua Wei; Yun Zhu; Peijie Li; Jian-Cheng Tan; Yang Dongxu; Zhu Yun; Li Peijie; Tan Jiancheng; Virtual Private Cloud Based Power-Dispatching Automation System—Architecture and Application. Mixture Density-PoseNet and Its Application to Monocular Camera-based Global Localization 2018, 15, 1756-1766, 10.1109/tii.2018.2849005.
- Lv, Z.; Zhang, W.; Li, N.; Chen, C.; Cai, J. A highly reliable lightweight distribution network communication encryption scheme. In Proceedings of the IEEE International Conference on Power Data Science, Taizhou, China, 22–24 November 2019; pp. 11–14.
- Xu, W.; Li, B.; He, B.; Lv, Y. Design on security communication protocol of electricity acquisition terminal based on the password techniques. In Proceedings of the IEEE International Conference on Information Science and Control Engineering, Changsha, China, 21–23 July 2017; pp. 261–264.




