Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Blockchains are a decentralized storage network that is completely unrelated to the data included within each block and that exhibits crucial qualities such as decentralization, anonymity, immutability, and transparency.
- blockchain adoption
- diffusion of innovation
- technology readiness index
- task technology fit
- technology acceptance model
- Technology–Organization–Environment
- VOSviewer
1. Blockchain Technology
Nakamoto [1] first presented the idea of Bitcoin, a decentralized currency backed by a distributed payment mechanism. Decentralization is a term that refers to a system of operation that enables P2P exchanges or transactions without the intervention of a central authority. This disruptive invention removes the need for dependence on third parties. The Bitcoin cryptocurrency is based on Blockchain technology, which is a continuously expanding list of blocks, each of which maintains scrambled transactional data and may have further decentralization potential [2]. In this type of collaborative network, each functioning node maintains a duplicate record of transactional data, referred to as a “ledger”. Since DLT is intrinsically shared across participating nodes, it enables the creation of a trustless operating environment devoid of conventional trusted institutions like banks and clearinghouses. P2P exchanges enable the development of confidence with participating nodes as the nodes maintain the shared ledger. To validate new data in a Blockchain ledger, computer nodes adhere to an encrypted protocol. This type of distributed system reaps the advantages of decentralized governance, potentially resolving the problem of data exposure and accountability [3]. This intrinsic characteristic supports counterparty interactions in the context of commercial activities [4]. Critical data may be preserved without verifying the consistency of individual datapoints, and each node has a copy of the transactional data, boosting the openness and visibility of business activity.
1.1. Characteristics of Blockchain
Effectively, Blockchains are a decentralized storage network that is completely unrelated to the data included within each block and that exhibits crucial qualities such as decentralization, anonymity, immutability, and transparency [5].
Decentralization refers to the fact that Blockchain technology lacks a central authority to administer the network among contributors [6]. A Blockchain network is composed of a distributed computer network and a decentralized P2P network [7]. The participant in the decentralization network interacts with the system and verifies the transactions without the need for a third party. These features ensure a reduced risk of failure and improve service trust with guaranteed availability [8].
Immutability, meaning something that cannot be altered or changed, is a distinguishing characteristic of Blockchain. Once a block in the ledger contains a record of transactions, it cannot be edited or amended. Since each block contains a cryptographic hash of the original data, each hash is unique, every block includes the previous block’s hash, and transactions are stored on separate nodes throughout the dispersed network, therefore eliminating any need to modify the block content [9]. One of the disadvantages of the immutability feature is that it is also impossible to modify data that might be erroneous before entering the Blockchain [10]. However, it facilitates the tracking of data sequences.
Anonymity a key characteristic of public Blockchain, which permits users to interact with each other in a public Blockchain network. Each user has a private key and a public key, which allows users in the network to interact but does not disclose anyone’s identity. The user is only recognized by the public key [8]. No single institution or authority is required to administer and maintain classified information. Consequently, real-world identity cannot be determined based on transaction information, which significantly supports and protects privacy. On the other hand, in circumstances like private and permissioned Blockchains, where systems are administered and governed by known organizations, identification is typically necessary [11].
Blockchain facilitates read-only access to transactions and inspected contents of smart contracts for anyone in the Blockchain network. This supports efficient and accurate record-keeping, but may interfere with privacy to some extent [12]. Blockchain technology has the potential to provide transparency not just in financial transactions but also in corporate operations [9].
1.2. Blockchain Types
Blockchains are classified into three forms based on how the network operates and who may join: public Blockchain, private Blockchain, and consortium Blockchain.
Public Blockchains: A public Blockchain can also be called permissionless [13]. It is a Blockchain in which participation in a public network is entirely free and open without any approval. Anyone with a computer with specialized software of a particular Blockchain can act as user, developer, miner, or community member [5]. Public Blockchains are constructed to be completely decentralized, and all their transactions are completely transparent. Bitcoin is the first example of a public Blockchain. Generally, public Blockchains are mainly used for cryptocurrencies [14].
Private Blockchains: Also referred to as permission Blockchains (e.g., Hyperledger), these allow for selecting which nodes should be operated and viewing transactions on the ledger, as well as who may transact with it since the privacy is improved [15]. This means that participants require permission to join these networks. In contrast to public networks, private Blockchains are managed by a centralized entity. Blockchain communities consider private Blockchains to be distributed databases with a full history that cannot be deleted or changed. Private Blockchains are mainly used in private enterprises with sensitive information that users do not want to be known to the public [11].
Consortium Blockchains: Consortium Blockchains are hybrids of private and public Blockchains. They enable only a select group of nodes to participate in the consensus process. They are partially centralized and open for limited public use and can be used in scenarios where there are various organizations involved in business activities (e.g., insurance companies, financial institutions, governmental institutions) [5].
1.3. Blockchain Generations
According to the literature, there are four generations of Blockchain [13]:
The first generation (Blockchain 1.0): The cryptocurrency, Bitcoin, represents the first generation of Blockchain technology, which is also called Blockchain 1.0. Other examples of this generation are Dash, Monero, and Litecoin.
The second-generation (Blockchain 2.0): The second-generation appeared with the start of the Ethereum network, where smart contracts were introduced. Smart contracts are software programs that contain the rules governing the management and control of smart properties. Ethereum Classic, Ethereum, QTUM, and NEO are all examples of Blockchain 2.0.
The third generation (Blockchain 3.0): With the rapid advancement of Blockchain technology, Blockchain has become more widespread, as in this generation, and it has exceeded the application of Blockchain in the financial field to various fields and industries such as contract management, Internet of Things (IoT), supply chain management, identity management, healthcare, and insurance. Currently, Blockchain technology is considered a general-purpose technology.
The fourth-generation (Blockchain 4.0): This generation is still in development. In Blockchain 4.0, artificial intelligence (AI) will be an essential part of the platform, reducing the need for human management since the work and decision making will depend on systems.
2. Technology Adoption Theories
According to [16], the rate at which payment systems evolve is primarily determined by the conflict between rapid technology development and natural impediments to the new product or service uptake. Numerous hypotheses have been advanced to account for customers’ adoption of innovative technologies and their desire to utilize them.
2.1. Diffusion of Innovation (DOI)
The DOI theory is used to establish a framework for research on innovation acceptance and adoption, as advocated by [17]. Rogers integrated findings from over 508 diffusion studies and developed the “diffusion of innovation” hypothesis to explain how individuals and organizations embrace innovative technologies. The idea elucidates “the method by which an invention is communicated among the members of a social organization over time through certain channels” [17]. Essentially, diffusion is the process through which individuals in a social system disseminate inventions over time via certain channels. According to DOI theory, innovation and adoption happen over a series of phases, including comprehension, persuasion, decision, implementation, and confirmation, which results in the development of [17] S-shaped adoption curves for innovators, early adopters, early majority, late majority, and laggards, as illustrated in Figure 1.
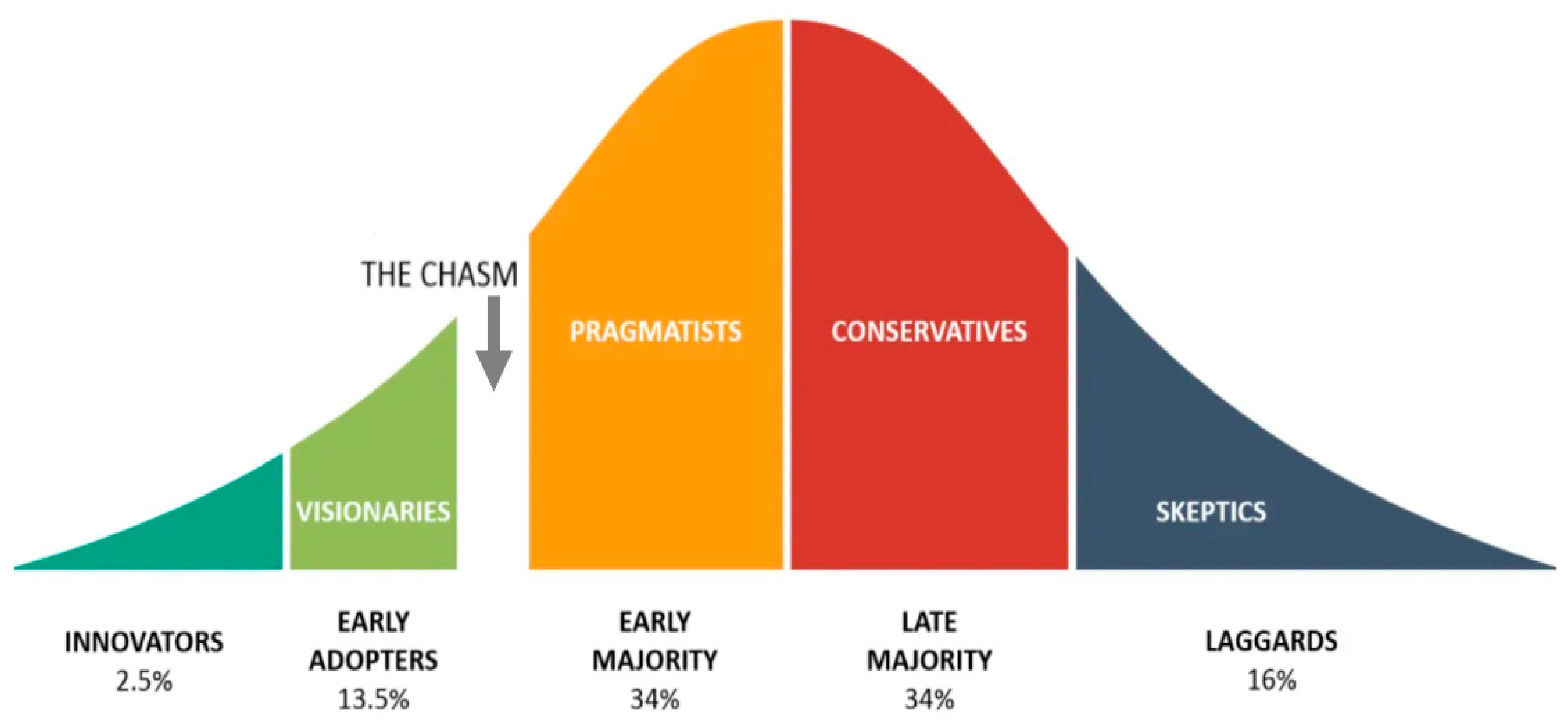
Figure 1. Adoption curve of innovation.
2.2. Technology Readiness and Acceptance Model (TRAM)
TRAM was introduced by [11] following a study of TAM and the architecture of technology readiness. The original research concentrated on customer intentions to engage in internet activity. TRAM associates TRI’s four dimensions with TAM’s two dimensions, namely, perceived utility and perceived ease of use, as mediators of intention to use. According to their investigation, a user’s intention to use is impacted by his or her feelings and past experiences [12]. Nevertheless, no attempt has been made to utilize TRAM to research the adoption of data-sharing systems, although these systems are extensively used by individuals, businesses, and governments.
2.3. Technology Readiness Index (TRI)
The TRI dimension was developed to measure a firm’s readiness to accept innovative technologies. The optimism factor is a good measure of the sense of certainty and optimism in a company. The higher the optimism, the more the company believes in utilizing technology to simplify its jobs. Users with an optimistic outlook are more likely to sense that innovative technology is both straightforward and beneficial. Following that, it will send them to the next stage to enhance job performance and quality, according to [18]. Technological readiness refers to “customers’ enthusiasm to implement technologies to improve their effectiveness in life and work.”
2.4. Theory of Planned Behavior (TPB)
TPB was established by [19], and it focuses on a single element that influences a person’s behavioral intention and attitudes to that behavior, as seen in Figure 2. The first two components are identical to those discovered in the Theory of Reasonable Action [20].
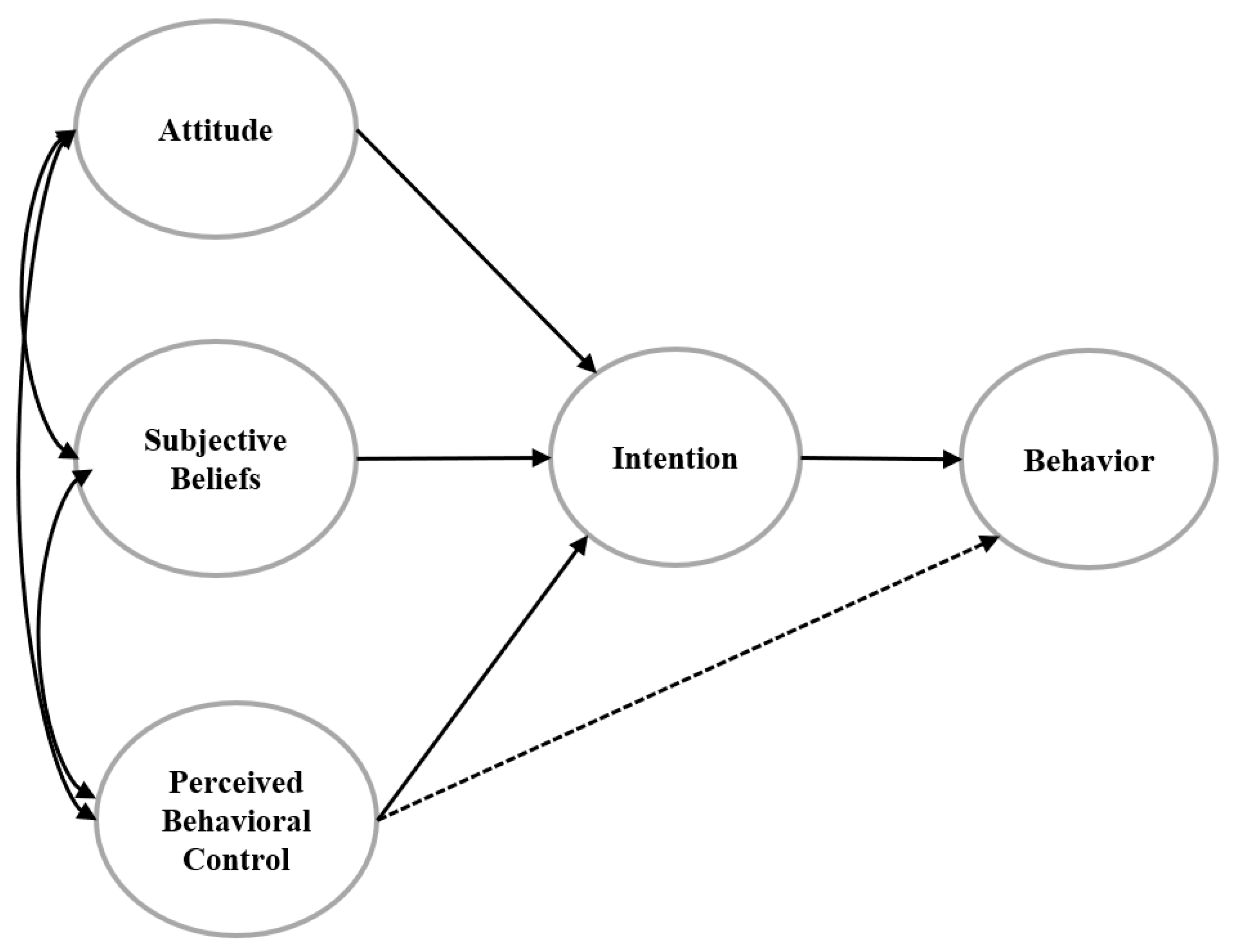
Figure 2. The theory of planned behavior.
The TPB is broken down into three major components that influence behavioral intention and actual behavior adoption: attitude, subjective norms, and perceived behavior control. The authors of [21] evaluated online banking adoption using both the TPB and the Decomposed TPB.
2.5. Task Technology Fit Model (TTF)
TTF, as defined by [22], places a premium on individual effect. The individual impact is measured in terms of increased efficiency, effectiveness, and/or quality. According to [22], a strong suit among tasks and technology increases the chance of usage and performance impact because the technology more closely matches users’ work demands and desires. As seen in Figure 3, this paradigm is well suited for examining the real usage of technology, particularly for testing innovative technology in order to obtain feedback. The TTF is valuable for evaluating technological apps that have already been released in the marketplace, such as on Google Play.
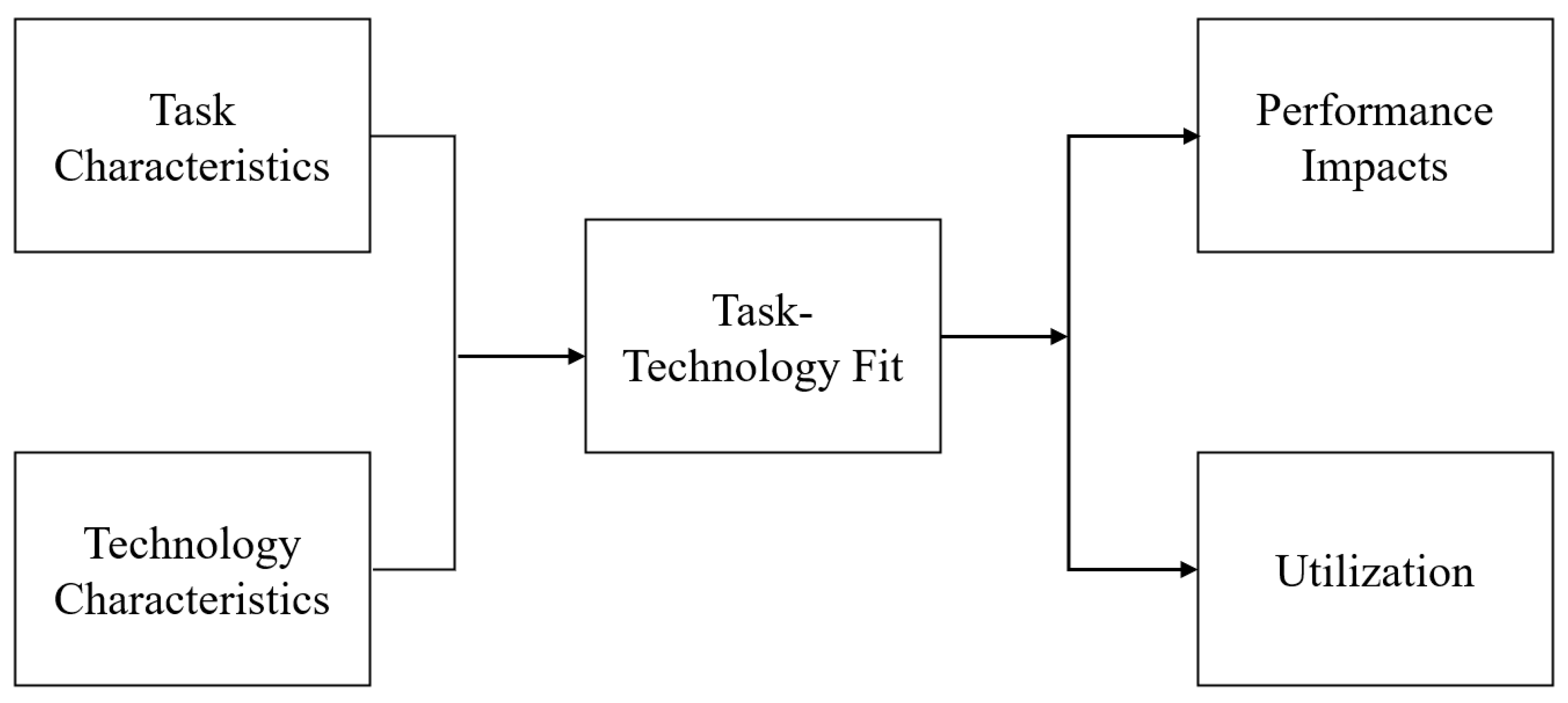
Figure 3. Task technology fit.
2.6. Technology Acceptance Model (TAM)
TAM was developed from TRA theory; however, the subjective norm in TRA theory had not been used in TAM. TAM is considered the first model to use psychological factors that affect the acceptance of new technology [23][24]. Two factors are added to attitude (A), namely, perceived usefulness (PU) and perceived ease of use (PEOU). TAM assumes that perceived ease of use (PEOU) impact affects the perceived usefulness (PU) directly, and that the perceived usefulness (PU) and perceived ease of use (PEOU) impact attitude directly and behavior intention (BI) indirectly. Additionally, TAM takes into consideration external variables like system attributes, training, etc., as shown in Figure 4. The technology acceptance model is the most common model and is utilized in technology adoption studies [25].
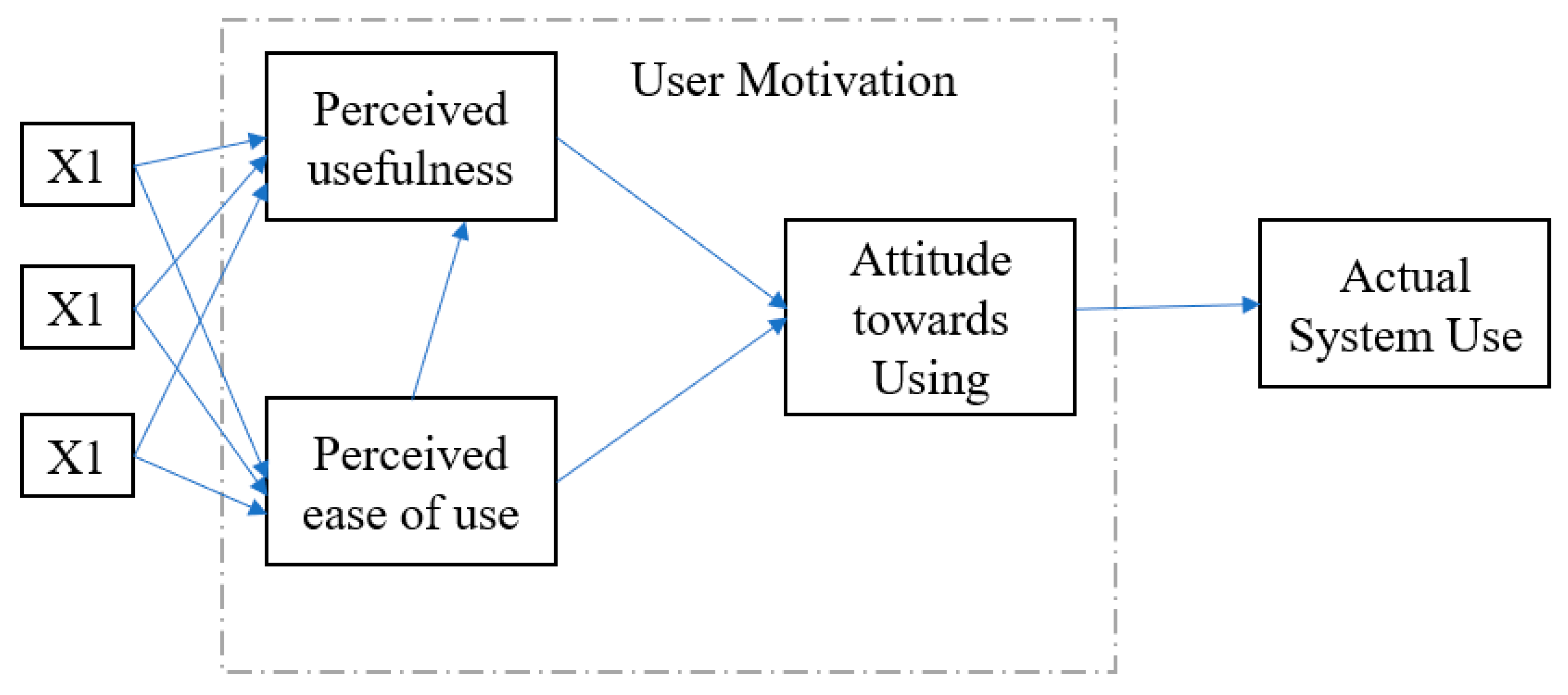
Figure 4. Technology acceptance model.
2.7. Unified Theory of Acceptance and Use of Technology (UTAUT)
Ref. [26] analyzed prior models/theories and developed the UTAUT depicted in Figure 5. The UTAUT identifies four determinants of users’ behavioral intention: performance expectations, effort expectations, social influence, and enabling factors. The UTAUT model’s performance expectancy is composed of five associated elements: perceived usefulness, intrinsic motivation, job-fit, relative advantage, and result expectancies, whereas effort expectancy contains the concepts of perceived ease of use and complexity. In terms of the social environment, ref. [26] discovered that social influence was negligible in voluntary settings.
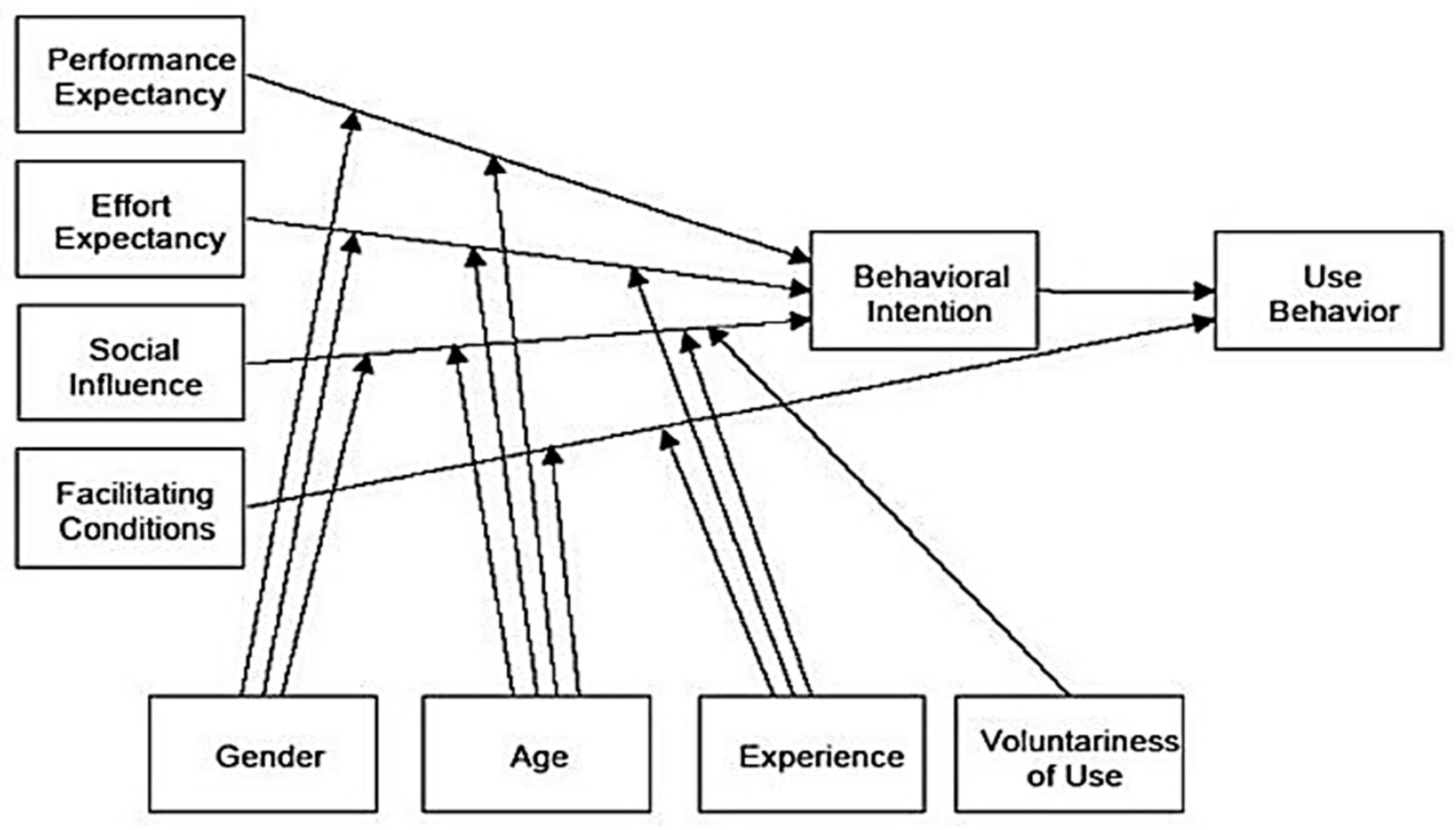
Figure 5. Unified theory of acceptance and use of technology.
2.8. Technology–Organization–Environment (TOE)
By taking into consideration technological, organizational, and environmental circumstances, the TOE framework can provide a unique viewpoint on IT adoption [27]. The investigation of contingent factors affecting company choices is one of the most exhaustive methods for understanding creativity [28]. To justify outcomes in organizations, such concerns may be classified as infrastructure, TOE, and organizational effects [29]. The TOE approach may be used to conduct a systematic examination of an organization’s innovation effect. According to the study in [30], TOE enables the distinction of intrinsic creative features, organizational capabilities, and motivations, as well as broader environmental factors of innovation.
3. Sustainable Factors
3.1. Relative Advantage
The term “relative advantage” refers to “the degree to which an invention is judged to be superior to the concept it replaces” [17]. The relative advantage enhances the likelihood of adopting innovative technology [31]. In comparison to other technologies, Blockchain enables the highest degree of traceability and provenance through the use of trustworthy data [32].
3.2. Security
Security is described as “the capacity to safeguard stakeholders’ information and transaction data throughout transmission” [33]. Through distinctive characteristics, such as a secured database [34] and a privacy-preserving architecture, Blockchain technology enables a high degree of IS [35] and enables users to conduct transactions anonymously. Information security threats are cited in the literature as a factor influencing the adoption of technology [36][37].
3.3. Compatibility
Compatibility describes “the degree to which an innovation is judged to be compatible with potential adopters’ existing values, prior experiences, and requirements” [17]. Blockchain systems are built on a proprietary distributed ledger technology that comes with a variety of governance models [38]. When choosing a distributed ledger technology for Blockchain deployment, businesses should ensure that it is compatible with the many financial services and products provided and that it meets regulatory criteria. The evolution of governance structures is challenging, since several Blockchain apps are running on a range of several platforms. Additionally, there are other aspects and protocols for public and private Blockchains, each of which may be used for a variety of purposes [39].
3.4. Complexity
Complexity refers to “the perceived difficulty of learning to use and understand a new system or technology” [40]. The major sources of complexity in Blockchain applications are scalability [41], selfish mining [42], and lack of computing power [43]. Scalability refers to the phenomenon where a company that adopts an innovation expects their affiliates to possess a similar innovation process to employ the innovation at an inter-organizational level.
3.5. Organisational Readiness
Organizational readiness assesses a manager’s opinion of his company’s capability of embracing technology based on a variety of variables, including awareness, resources, commitment, and governance. This criterion is mostly concerned with financial stability [44].
3.6. Top Management Support
Authors in [45] define top management support as the extent to which top management recognizes the strategic value of information systems and participates in information system operations [46]. Support from senior management creates a compelling vision that enables a business to overcome any obstacle and to foster an atmosphere of dedication and creativity [32].
3.7. Perceived Usefulness
TAM postulates a relationship between the notions of perceived utility and technological adoption. Perceived ease of use has a positive influence on perceived utility since technologies that require less effort might be more beneficial. Numerous studies have shown perceived utility to be a significant predictor of technology adoption [47].
3.8. Perceived Ease of Use
The term “perceived ease of use” refers to the extent to which individuals think that utilizing an innovative technology will be effortless. PEoU is a major structural element in the TAM model. This element has a direct influence on PU and attitude in two ways. The TAM hypothesis has been validated and applied in many research projects to predict customer behavior when it comes to new technologies [47]. PEoU refers to the probability that a user expects the target system to be effort-free. In this context, PEoU refers to the degree to which a user anticipates and feels that utilizing a service or technological system will be effortless [47].
3.9. Competitive Pressure
Competitive pressure is a term that refers to the level to which a business considers pressure from competitors within its business [48]. Supply chains may use Blockchain technology to develop a variety of sharing applications, including peer-to-peer, automated payment methods; foreign exchange platforms; digital rights management; and cultural heritage management. Many businesses would like to reap these benefits in today’s ever-increasingly competitive market. By implementing information systems, firms may be able to modify the laws of competition and exploit novel methods of outperforming competitors, ultimately altering the competitive structure of the industry [49].
3.10. Performance Expectancy
Performance expectation is a theoretical concept developed from UTAUT that refers to the extent to which the adoption of a technology enables actors to perform daily tasks more efficiently. According to [50], PE is the strongest predictor of the desire to employ a certain technology. Blockchain can increase efficiency and effectiveness in the long run, hence affecting this latter component [51].
3.11. Effort Expectancy
In the UTAUT, effort expectancy (EE) refers to the level of ease involved in the usage of information systems [50]. It denotes the essential commitment that players, by definition, must display during any learning process connected with the adoption of innovative technology. The literature indicates that a user’s desire to embrace new technology will likely grow if they believe that integrating this tool into their regular activities will not demand excessive work [52].
3.12. Social Influence
The term “social influence” refers to a person’s norms, roles, affiliations, and values, which affect how they perceive what they will do [53]. The social influence component has been included in the most successful online services, allowing the consumer to connect with the platform at the appropriate moment to gain sufficient experience without jeopardizing his or her loyalty to the business. Additionally, social influence is a distinct construct since it affects the level of confidence in the technology. These encounters and communication contexts prompt the consumer to investigate, assess the degree of risk, and develop trust to determine whether or not to utilize the service [53]. The estimated impact of social influence on Blockchain technology will provide a better awareness of client perceptions of this innovative technology and the anticipated benefits of adoption.
3.13. Facilitating Conditions
Facilitating conditions refer to an employee’s perception of an organization’s technological infrastructure that supports system utilization. Additionally, condition facilitation refers to an understanding of the tools accessible to organizations to support Blockchain adoption. In other words, if consumers perceive a suitable amount of technological, organizational, network, and people support when utilizing Blockchain, they are more likely to have an uncomplicated and enjoyable experience with the technology and, hence, to be more engaged with it. Indeed, the Blockchain maintains a copy of each transaction, supporting the system and streamlining transaction monitoring for all participants.
3.14. Attitude
The term “attitude” refers to a user’s favorable or negative thoughts about a new technological advancement [54]. The notion of reasoned action led researchers to discover real behavior, which they defined as a user belief system, which was in turn defined as an attitude to utilize and study things such as technological systems. Individuals examine their attitudes towards each alternative in a situation when generating behavioral intentions, and it appears that the attitude-comparable choice procedure does not reveal the formulation of an individual’s estimations of whether they should conduct many actions [55].
3.15. Intention
Intention is a term that relates to the user’s anticipated possibility or probability of engaging in a specific action; in this example, experiencing innovative technology. Intention aids in the early phases of the application development life cycle by identifying well-formed measurements of user acceptability. Additionally, it assists clients in accepting beneficial technologies or rejecting ineffective ones, hence reducing the danger of supplying ineffective technologies before their rejection [54]. Intention is defined as the capacity of a user’s subjective reasoning to cause an application to behave in a particular way. The motivation for a user to perform and utilize a technological system is the source of his/her belief in purposeful conduct.
3.16. Trust
Trust is a term that relates to a customer’s sense of comfort, confidence, and security while interacting with technology [56]. The relationship between the client and the vendor is defined by trust. Trust becomes critical to maintaining an active and sustained communication channel and maintaining confidence in a commercial partner. It is a characteristic of trustworthy partnerships that can help mitigate risk. Trust is defined as the client’s attitude toward the service provider; similarly, protection against negative acts that may be anticipated in advance is defined as providing additional protection and monitoring for customer actions to improve their trust [57]. When confidence erodes, customers become less willing to take risks, and the likelihood of disloyalty increases. In cases where one must take a risk and cannot control the outcome, trust is the only option. In the case of Blockchain, the risk likelihood should be minimal from the customer’s perspective, while trust should be high.
3.17. Regulatory Support
Regulatory framework and government assistance refer to regulatory frameworks established by the government to oversee and guarantee that both technology service providers and consumers adhere to their commitments and prevent infractions. Government regulation and legislation are critical for e-commerce and service quality monitoring, as well as for authorizing and deploying new technologies within a nation’s rule of law [58]. These statutes are employed to guarantee that all processes run smoothly and fairly. Similarly, when it comes to client behavior towards Blockchain technology and cryptocurrencies, the same holds true. Regulation is required to minimize or mitigate any uncertainty that emerges. Government rules and directives may affect customers’ willingness to trust technology and secure its use. Nevertheless, there are other obstacles to the worldwide expansion of cryptocurrencies, including lax government regulations [59].
3.18. Behavioural Expectation
Previously published UTAUT research has indicated that the behavioral intention construct affects the behavioral expectation construct [60]. In this perspective, [50] argues that, “The motivational drive to perform a target behavior stems from an individual’s internal evaluation of the behavior”. Therefore, the behavioral purpose of an individual is related to his or her internal appraisal. Thus, behavioral intention precedes Behavioral Expectation. That is, “Behavioral expectation, therefore, reflects the strength of the focal behavioral intention over other (competing) behavioral intentions” [50].
Blockchain not only refers to the better flow of the information superhighway but also to the workforce and assets of susceptible organizations. Potential Blockchain methods can be lethal to operational controls, financial information, and the workforce associated with the organizations. The benefits of these methods can be maximized by organizational arrangements and support for organizational Blockchain. Additionally, with this sensitive issue under investigation, an organization needs to focus on strategic and acceptable Blockchain methods within the organization. Fear of losing critical organizational transactions, due to complex or unrealistic organizational patterns, can be dealt with by involving the end-users of computing and network facilities (employees) in decisive stages of Blockchain adoption. It is time to focus upon shared visions/goals in dealing with Blockchain issues at the organizational level.
This entry is adapted from the peer-reviewed paper 10.3390/su14095176
References
- Nakamoto, S.; Bitcoin, A. A Peer to Peer Electronic Cash System. 2009. Available online: https//bitcoin.org/bitcoin.pdf (accessed on 17 January 2022).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71.
- Neisse, R.; Steri, G.; Nai-Fovino, I. A blockchain-based approach for data accountability and provenance tracking. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; pp. 1–10.
- White, G.R.T. Future applications of blockchain in business and management: A Delphi study. Strateg. Chang. 2017, 26, 439–451.
- Hölbl, M.; Kompara, M.; Kamišalić, A.; Nemec Zlatolas, L. A systematic review of the use of blockchain in healthcare. Symmetry 2018, 10, 470.
- Akbar, N.A.; Muneer, A.; ElHakim, N.; Fati, S.M. Distributed Hybrid Double-Spending Attack Prevention Mechanism for Proof-of-Work and Proof-of-Stake Blockchain Consensuses. Future Internet 2021, 13, 285.
- Vafiadis, N.V.; Taefi, T.T. Differentiating blockchain technology to optimize the processes quality in industry 4.0. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 864–869.
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375.
- Hewa, T.; Ylianttila, M.; Liyanage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857.
- AL-Ashmori, A.; Basri, S.; Dominic, P.D.D.; Muneer, A.; Al-Tashi, Q.; Al-Ashmori, Y. Blockchain-Oriented Software Development Issues: A Literature Review. Proc. Comput. Methods Syst. Softw. 2021, 232, 48–57.
- Almekhlafi, S.; Al-Shaibany, N. The literature review of blockchain adoption. Asian J. Res. Comput. Sci. 2021, 7, 29–50.
- Clohessy, T.; Acton, T. Investigating the influence of organizational factors on blockchain adoption: An innovation theory perspective. Ind. Manag. Data Syst. 2019, 119, 35.
- Colomo-Palacios, R.; Sánchez-Gordón, M.; Arias-Aranda, D. A critical review on blockchain assessment initiatives: A technology evolution viewpoint. J. Softw. Evol. Process 2020, 32, e2272.
- Mohammed, A.; Potdar, V.; Yang, L. Key factors affecting blockchain adoption in organizations. In Proceedings of the International Conference on Big Data and Security, Nanjing, China, 20–22 December 2019; pp. 455–467.
- Ali, R.F.; Muneer, A.; Dominic, P.D.D.; Taib, S.M. Hyperledger Fabric Framework with 5G Network for Blockchain-based Security of IoT Smart Home Applications. In Proceedings of the 2021 International Conference on Decision Aid Sciences and Application (DASA), Online, 7–8 December 2021; pp. 1109–1114.
- Lai, P.C. Design and Security impact on consumers’ intention to use single platform E-payment. Interdiscip. Inf. Sci. 2016, 22, 111–122.
- Everett, M. (Ed.) Diffusion of Innovations, 4th ed.; Free Press: New York, NY, USA, 1995.
- Charles, L.; Colby, A. (Eds.) Techno-Ready Marketing: How and Why Customers Adopt Technology; Free Press: New York, NY, USA, 2001.
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211.
- Fishbein, M.; Ajzen, I. Belief, attitude, intention, and behavior: An introduction to theory and research. Philos. Rhetor. 1977, 10, 244–245.
- Shih, Y.-Y.; Fang, K. The use of a decomposed theory of planned behavior to study Internet banking in Taiwan. Internet Res. 2004, 14, 213–223.
- Goodhue, D.L.; Thompson, R.L. Task-technology fit and individual performance. MIS Q. 1995, 19, 213–236.
- Albaom, M.A.; Sidi1, F.; Jabar, M.A.; Abdullah, R.; Ishak, I.; Yunikawati, N.A.; Priambodo, M.P.; Husen, J.H.; Issac, O.; Al-Harasi, A.H.; et al. The Impact of Tourist’s Intention to Use Web 3.0: A Conceptual Integrate, d Model Based on Tam & Dmism Faculty of Business and Management, Universiti Teknologi MARA (UITM) Malaysia. J. Theor. Appl. Inf. Technol. 2021, 31, 24.
- Alzubi, M.M.; Al-Dubai, M.M.; Farea, M.M. Using the technology acceptance model in understanding citizens’ behavioural intention to use m-marketing among Jordanian citizen. J. Bus. Retail Manag. Res. 2018, 12, 12.
- Samaradiwakara, G.; Gunawardena, C.G. Comparison of existing technology acceptance theories and models to suggest a well improved theory/model. Int. Tech. Sci. J. 2014, 1, 21–36.
- Venkatesh, V. Determinants of perceived ease of use: Integrating control, intrinsic motivation, and emotion into the technology acceptance model. Inf. Syst. Res. 2000, 11, 342–365.
- Pan, Y.; Froese, F.; Liu, N.; Hu, Y.; Ye, M. The adoption of artificial intelligence in employee recruitment: The influence of contextual factors. Int. J. Hum. Resour. Manag. 2022, 33, 1125–1147.
- Wisdom, J.P.; Chor, K.H.B.; Hoagwood, K.E.; Horwitz, S.M. Innovation adoption: A review of theories and constructs. Adm. Policy Ment. Heal. Ment. Heal. Serv. Res. 2014, 41, 480–502.
- Tornatzky, L.G.; Fleischer, M.; Chakrabarti, A.K. Processes of Technological Innovation; Lexington Books: Lanham, MD, USA, 1990.
- Dedrick, J.; West, J. Why firms adopt open source platforms: A grounded theory of innovation and standards adoption. In Proceedings of the Workshop on Standard Making: A critical Research Frontier for Information Systems, Seattle, WA, USA, 12–14 December 2003; pp. 236–257. Available online: https://www.researchgate.net/profile/Joel-West-2/publication/239184573_Why_firms_adopt_open_source_platforms_A_grounded_theory_of_innovation_and_standards_adoption/links/55d1f0a008ae3dc86a4f354e/Why-firms-adopt-open-source-platforms-A-grounded-theory-of-innovation-and-standards-adoption.pdfc (accessed on 17 January 2022).
- Gangwar, H.; Date, H.; Ramaswamy, R. Understanding determinants of cloud computing adoption using an integrated TAM-TOE model. J. Enterp. Inf. Manag. 2015, 28, 107–130.
- Wang, Y.; Han, J.H.; Beynon-Davies, P. Understanding blockchain technology for future supply chains: A systematic literature review and research agenda. Supply Chain Manag. Int. J. 2018, 24, 62–84.
- Hua, Y.; Jiang, H.; Zhu, Y.; Feng, D.; Tian, L. SmartStore: A new metadata organization paradigm with semantic-awareness for next-generation file systems. In Proceedings of the Conference on High Performance Computing Networking, Storage and Analysis, Portland, OR, USA, 14–20 November 2009; pp. 1–12.
- Huckle, S.; Bhattacharya, R.; White, M.; Beloff, N. Internet of things, blockchain and shared economy applications. Procedia Comput. Sci. 2016, 98, 461–466.
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Towards a novel privacy-preserving access control model based on blockchain technology in IoT. In Europe and MENA Cooperation Advances in Information and Communication Technologies; Springer: Berlin/Heidelberg, Germany, 2017; pp. 523–533.
- Ali, R.F.; Dominic, P.D.D.; Ali, S.E.A.; Rehman, M.; Sohail, A. Information security behavior and information security policy compliance: A systematic literature review for identifying the transformation process from noncompliance to compliance. Appl. Sci. 2021, 11, 3383.
- Belkhamza, Z.; Wafa, S.A. The effect of perceived risk on the intention to use e-commerce: The case of Algeria. J. Internet Bank. Commer. 1970, 14, 1–10.
- Pazaitis, A.; De Filippi, P.; Kostakis, V. Blockchain and value systems in the sharing economy: The illustrative case of Backfeed. Technol. Forecast. Soc. Chang. 2017, 125, 105–115.
- Mthethwa, S. The analysis of the blockchain technology and challenges. World Acad. Sci. Eng. Technol. Int. Sci. Index Comput. Inf. Eng. 2016, 10, 1937–1948.
- Sonnenwald, D.H.; Maglaughlin, K.L.; Whitton, M.C. Using innovation diffusion theory to guide collaboration technology evaluation: Work in progress. In Proceedings of the 10th IEEE International Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises, Washington, DC, USA, 20–22 June 2001; pp. 114–119.
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; Van Renesse, R. Bitcoin-NG: A Scalable Blockchain Protocol. In Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI 16), Santa Clara, CA, USA, 2 February 2016; pp. 45–59.
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411.
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies without proof of work. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 22–26 February 2016; pp. 142–157.
- Musawa, M.S.; Wahab, E. The adoption of electronic data interchange (EDI) technology by Nigerian SMEs: A conceptual framework. J. Bus. Manag. Econ. 2012, 3, 55–68.
- Raghunathan, B.; Raghunathan, T.S. Impact of top management support on IS planning. J. Inf. Syst. 1988, 2, 15–23.
- Ghaleb, E.A.A.; Dominic, P.D.D.; Fati, S.M.; Muneer, A.; Ali, R.F. The Assessment of Big Data Adoption Readiness with a Technology–Organization–Environment Framework: A Perspective towards Healthcare Employees. Sustainability 2021, 13, 8379.
- Davis, F.D. Perceived Usefulness, Perceived Ease of Use, and User Acceptance of Information Technology. MIS Q. 1989, 13, 319–340.
- Zhu, K.; Kraemer, K.L. Post-adoption variations in usage and value of e-business by organizations: Cross-country evidence from the retail industry. Inf. Syst. Res. 2005, 16, 61–84.
- Porter, M.E.; Millar, V.E. How Information Gives You Competitive Advantage 1985. Available online: http://faculty.yu.edu.jo/iaad/Lists/Taught%20Courses/Attachments/5/Reading%205-How%20Information%20Gives%20You%20Comp-Fall2015.pdf (accessed on 17 January 2022).
- Venkatesh, V.; Thong, J.Y.L.; Xu, X. Consumer Acceptance and Use of Information Technology: Extending the Unified Theory of Acceptance and Use of Technology. MIS Q. 2012, 36, 157–178.
- Schmitz, J.; Leoni, G. Accounting and auditing at the time of blockchain technology: A research agenda. Aust. Account. Rev. 2019, 29, 331–342.
- Martins, C.; Oliveira, T.; Popovič, A. Understanding the Internet banking adoption: A unified theory of acceptance and use of technology and perceived risk application. Int. J. Inf. Manag. 2014, 34, 1–13.
- Chaouali, W.; Yahia, I.B.; Souiden, N. The interplay of counter-conformity motivation, social influence, and trust in customers’ intention to adopt Internet banking services: The case of an emerging country. J. Retail. Consum. Serv. 2016, 28, 209–218.
- Davis, F.D. A Technology Acceptance Model for Empirically Testing New End-User Information Systems: Theory and Results; Massachusetts Institute of Technology: Cambridge, MA, USA, 1985.
- Sheppard, B.H.; Hartwick, J.; Warshaw, P.R. The theory of reasoned action: A meta-analysis of past research with recommendations for modifications and future research. J. Consum. Res. 1988, 15, 325–343.
- McCloskey, D.W. The Importance of Ease of Use, Usefulness, and Trust to Online Consumers: An Examination of the Technology Acceptance Model with Older Customers. In End-User Computing: Concepts, Methodologies, Tools, and Applications; IGI Global: Hershey, PA, USA, 2008; pp. 1620–1636.
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An integrative model of organizational trust. Acad. Manag. Rev. 1995, 20, 709–734.
- Peters, G.; Panayi, E.; Chapelle, A. Trends in cryptocurrencies and blockchain technologies: A monetary theory and regulation perspective. J. Financ. Perspect. 2015, 3, 30–31.
- Lu, Y. Blockchain: A survey on functions, applications and open issues. J. Ind. Integr. Manag. 2018, 3, 1850015.
- Maruping, L.M.; Bala, H.; Venkatesh, V.; Brown, S.A. Going beyond intention: Integrating behavioral expectation into the unified theory of acceptance and use of technology. J. Assoc. Inf. Sci. Technol. 2017, 68, 623–637.
This entry is offline, you can click here to edit this entry!
