Electronic voting (e-voting) is an electronic system that allows users to make a collaborative decision or vote for candidates in an election. It handles the registration of voters, input of vote, vote casting, vote encryption, the transmission of the ballot to the server, vote storing, vote counting, and tabulation of the election result.
- blind signature-based e-voting
- blockchain-based e-voting
- cryptography
- homomorphic e-voting
- hybrid e-voting
- mix-net based e-voting
- post-quantum e-voting
1. Introduction
The e-voting system can be used in various applications such as punched cards, smart cards, direct-recording e-voting systems (DRE), optical scan systems, and computers connected to the Internet. The e-voting system offers more accurate election results, faster result tabulation, minimises human errors, more convenience towards disabled or handicapped people, and self-tallying election results [1]. However, according to Peng [2] and Oo and Aung [3], e-voting faces challenges of scalability for large-scale elections, security challenges, unpredictable malfunctions of servers, and others. Some people feel uncomfortable adopting e-voting systems due to voter privacy as voter identity might be disclosed. The most important security properties to preserve as mentioned by Peng [2] and Sebé et al. [4] are the privacy of the voter, fairness, receipt-freeness, coercion-resistance, individual verifiability, universal verifiability, robustness, double-voting prevention, etc. Thus, many researchers have proposed schemes to enhance the security of e-voting systems and put e-voting systems in practice. In this entry, the researchers focus on conventional approaches which cover mix-net-based e-voting, homomorphic e-voting, and blind signature-based e-voting, and latest developments which cover blockchain-based e-voting, post-quantum e-voting, and hybrid e-voting.
1.1. Entities in e-Voting System
1.2. Structure of e-Voting System
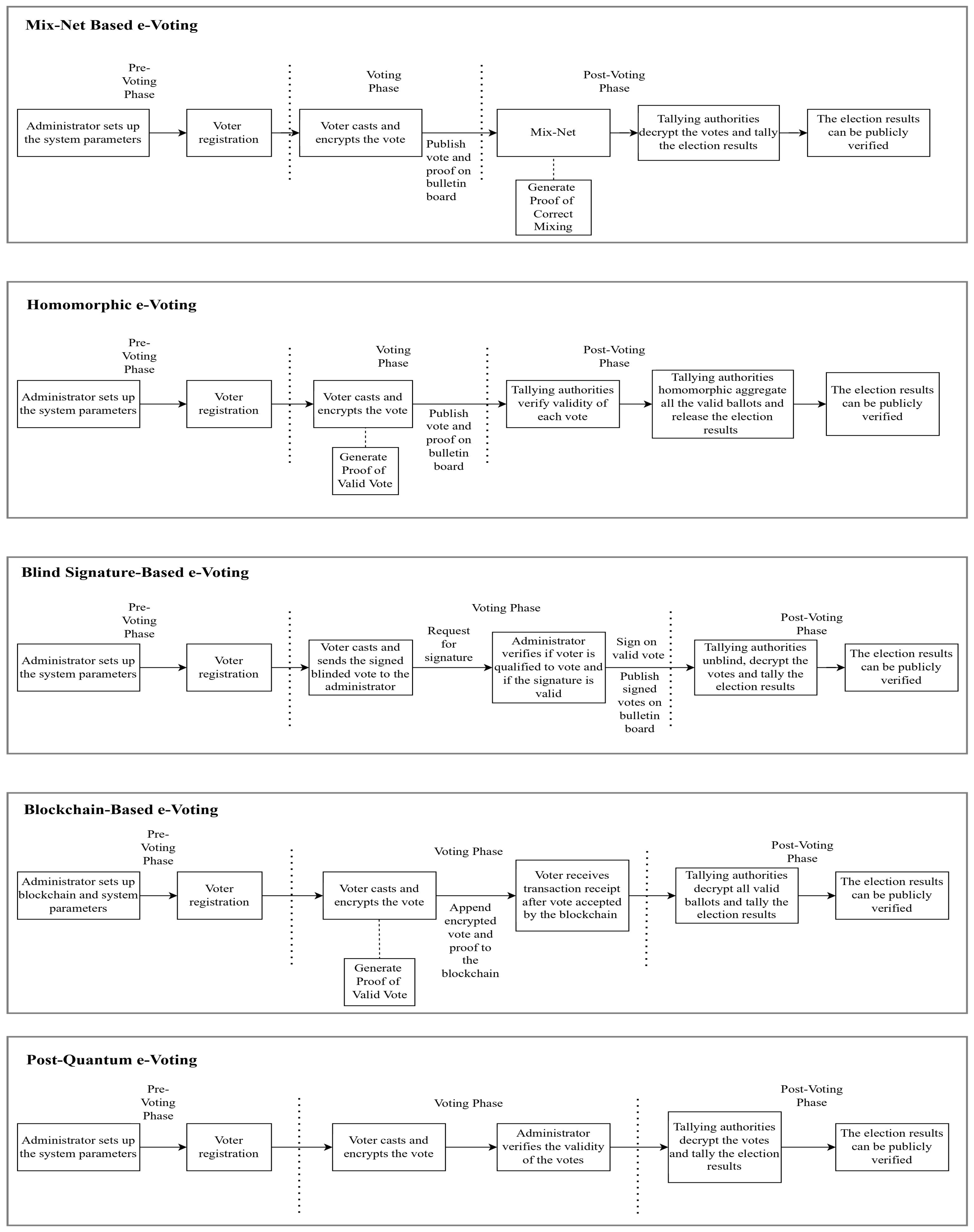
1.3. Advantages and Disadvantages of Various e-Voting Approaches
| Approach | Advantages | Disadvantages |
|---|---|---|
| Mix-net-Based e-Voting |
|
|
| Homomorphic e-Voting |
|
|
| Blind Signature-Based e-Voting |
|
|
| Blockchain-Based e-Voting |
|
|
| Post-Quantum e-Voting |
|
|
As observed from the comparison analysis in Table 1, it is worth mentioning that hybrid schemes are more practical and efficient than other approaches. A hybrid scheme refers to the scheme that is constructed by integrating two or more approaches. A hybrid scheme inherits the advantages and security properties of combined cryptographic tools and eliminates the weaknesses of cryptographic tools individually. However, the use of these e-voting approaches varies depending on the application to which they are applied [15]. Therefore, different e-voting approaches may be suited for different applications.
2. Practical Considerations in e-Voting
-
Denial-of-service (DoS) attacks. The main goal of DoS attacks is to slow down computer systems and to the extent that it affects the casting of votes, tallying of votes, and the auditing process.
-
Malware attacks. Malicious software that can disrupt the casting of votes and the auditing process, and alter or destroy stored ballots.
-
Malicious individuals or servers break into the system to retrieve administrator-level sensitive data such as voters’ credentials.
-
If the system is designed properly.
-
If the system is configured and updated accordingly.
-
If the system is operated and managed accordingly.
-
Resources and skills of potential attackers.
3. Potential Research Directions
This entry is adapted from the peer-reviewed paper 10.3390/sym14050858
References
- Kiayias, A.; Yung, M. Self-Tallying Elections And Perfect Ballot Secrecy. In Public Key Cryptography; Lecture Notes in Computer Science; Naccache, D., Paillier, P., Eds.; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2274, pp. 141–158.
- Peng, K. An Efficient Shuffling Based eVoting Scheme. J. Syst. Softw. 2011, 84, 906–922.
- Oo, H.N.; Aung, A. A Survey Of Different Electronic Voting Systems. Int. J. Sci. Eng. Res. 2014, 3, 3460–3464.
- Sebé, F.; Miret, J.M.; Pujolàs, J.; Puiggalí, J. Simple And Efficient Hash-Based Verifiable Mixing For Remote Electronic Voting. Comput. Commun. 2010, 33, 667–675.
- Li, H.; Kankanala, A.R.; Zou, X. A Taxonomy And Comparison Of Remote Voting Schemes. In Proceedings of the 2014 23rd International Conference on Computer Communication and Networks (ICCCN), Shanghai, China, 4–7 August 2014; pp. 1–8.
- OASIS (Organization for the Advancement of Structured Information Standards); Office of the e-Envoy. Election Markup Language (EML) Process and Data Requirements 4.0a. 2013. Available online: https://www.oasis-open.org/standards (accessed on 12 December 2020).
- Lee, B.; Boyd, C.; Dawson, E.; Kim, K.; Yang, J.; Yoo, S. Providing Receipt-Freeness In Mixnet-Based Voting Protocols. In Information Security and Cryptology. ICISC 2003; Lecture Notes in Computer Science; Lim, J.I., Lee, D.H., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; Volume 2971, pp. 245–258.
- Xia, Z.; Schneider, S. A New Receipt-Free E-Voting Scheme Based On Blind Signature (Abstract). WOTE 2006, 6, 127–135.
- Zhang, H.; You, Q.; Zhang, J. A Lightweight Electronic Voting Scheme Based On Blind Signature And Kerberos Mechanism. In Proceedings of the 2015 IEEE 5th International Conference on Electronics Information and Emergency Communication, Beijing, China, 14–16 May 2015; pp. 210–214.
- Bibiloni, P.; Escala, A.; Morillo, P. Vote Validatability in Mix-Net-Based eVoting. In E-Voting and Identity. Vote-ID 2015; Lecture Notes in Computer, Science; Haenni, R., Koenig, R.E., Wikström, D., Eds.; Springer International Publishing: Cham, Switzerland, 2015; Volume 9269, pp. 92–109.
- AboSamra, K.M.; AbdelHafez, A.A.; Assassa, G.M.; Mursi, M.F. A Practical, Secure, and Auditable e-Voting System. J. Inf. Secur. Appl. 2017, 36, 69–89.
- Dong, H.; Yang, L. A Voting Scheme with Post-Quantum Security Based on Physical Laws. arXiv 2018, arXiv:1805.12480.
- Hardwick, F.S.; Gioulis, A.; Akram, R.N.; Markantonakis, K. E-Voting With Blockchain: An E-Voting Protocol with Decentralisation And Voter Privacy. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Communications in Computer and Information Science. Halifax, NS, Canada, 30 July–3 August 2018; pp. 1561–1567.
- Çabuk, U.; Adiguzel, E.; Karaarslan, E. A Survey On Feasibility And Suitability of Blockchain Techniques for the E-Voting Systems. Int. J. Adv. Res. Comput. Commun. Eng. (IJARCCE) 2018, 7, 124–134.
- Chow, S.; Liu, J.; Wong, D. Robust Receipt-Free Election System With Ballot Secrecy And Verifiability. In Proceedings of the Network and Distributed System Security Symposium, NDSS 2008, San Diego, CA, USA, 10–13 February 2008; The Internet Society: San Diego, CA, USA, 2008; Volume 8, pp. 81–94.
- National Academies of Sciences, Engineering, and Medicine. Securing the Vote: Protecting American Democracy; The National Academies Press: Washington, DC, USA, 2018.
- Chillotti, I.; Gama, N.; Georgieva, M.; Izabachène, M. A Homomorphic LWE Based E-voting Scheme. In Post-Quantum Cryptography; Lecture Notes in Computer Science; Takagi, T., Ed.; Springer International Publishing: Cham, Switzerland, 2016; Volume 9606, pp. 245–265.
- Rønne, P.B.; Atashpendar, A.; Gjøsteen, K.; Ryan, P.Y.A. Short Paper: Coercion-Resistant Voting in Linear Time Via Fully Homomorphic Encryption. In Financial Cryptography and Data Security; Lecture Notes in Computer Science; Bracciali, A., Clark, J., Pintore, F., Rønne, P.B., Sala, M., Eds.; Springer International Publishing: Cham, Switzerland, 2020; Volume 11599, pp. 289–298.
- Juels, A.; Catalano, D.; Jakobsson, M. Coercion-Resistant Electronic Elections. In Proceedings of the 2005 ACM Workshop on Privacy in the Electronic Society, WPES ’05, Alexandria, VA, USA, 7 November 2005; Association for Computing Machinery: New York, NY, USA, 2005; pp. 61–70.
- Jafar, U.; Aziz, M.J.A. A State of the Art Survey and Research Directions on Blockchain Based Electronic Voting System. In Advances in Cyber Security; Communications in Computer and Information Science; Anbar, M., Abdullah, N., Manickam, S., Eds.; Springer: Singapore, 2021; Volume 1347, pp. 248–266.
- Liu, Y.; Wang, Q. An E-voting Protocol Based On Blockchain. IACR Cryptol. EPrint Arch. 2017, 2017, 1043.
- Gao, S.; Zheng, D.; Guo, R.; Jing, C.; Hu, C. An Anti-Quantum E-Voting Protocol in Blockchain with Audit Function. IEEE Access 2019, 7, 115304–115316.
- Esgin, M.F.; Zhao, R.K.; Steinfel, R.; Liu, J.K.; Liu, D. MatRiCT: Efficient, Scalable And Post-Quantum Blockchain Confidential Transactions Protocol. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, CCS ’19, London, UK, 11–15 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 567–584.
- Fernandez-Carames, T.M.; Fraga-Lamas, P. Towards post-quantum blockchain: A review on blockchain cryptography resistant to quantum computing attacks. IEEE Access 2020, 8, 21091–21116.
- McEliece, R.J. A Public-Key Cryptosystem Based On Algebraic. Coding Thv 1978, 4244, 114–116.
- Pinilla, R.M. Fully Post-Quantum Protocols for e-Voting, Coercion Resistant Cast as Intended and Mixing Networks. Ph.D. Thesis, Universitat Politècnica de Catalunya, Barcelona, Spain, 2018.
- Boyen, X.; Haines, T.; Müller, J. A Verifiable and Practical Lattice-Based Decryption Mix Net with External Auditing. In Computer Security. ESORICS 2020; Lecture Notes in Computer Science; Chen, L., Li, N., Liang, K., Schneider, S., Eds.; Springer International Publishing: Cham, Switzerland, 2020; Volume 12309, pp. 336–356.
- Gong, B.; Lu, X.; Fat, L.W.; Au, M.H. Blockchain-Based Threshold Electronic Voting System. In Security and Privacy in Social Networks and Big Data; Communications in Computer and Information Science; Meng, W., Furnell, S., Eds.; Springer: Singapore, 2019; Volume 1095, pp. 238–250.
- Chaieb, M.; Yousfi, S. LOKI Vote: A Blockchain-Based Coercion Resistant E-Voting Protocol. In Information Systems. EMCIS 2020; Lecture Notes in Business Information Processing; Themistocleous, M., Papadaki, M., Kamal, M.M., Eds.; Springer International Publishing: Cham, Switzerland, 2020; Volume 402, pp. 151–168.
- Aziz, A.; Qunoo, H.; Abusamra, A. Using Homomorphic Cryptographic Solutions on E-voting Systems. Int. J. Comput. Netw. Inf. Secur. 2018, 10, 44–59.
- Liao, G. Multi-Candidate Electronic Voting Scheme Based on Fully Homomorphic Encryption. J. Phys. Conf. Ser. 2020, 1678, 012064.
- Cruz, J.P.; Kaji, Y. E-voting System Based on the Bitcoin Protocol and Blind Signatures. IPSJ Trans. Math. Model. Its Appl. 2017, 10, 14–22.
- Zhou, Y.; Liu, Y.; Jiang, C.; Wang, S. An Improved FOO Voting Scheme Using Blockchain. Int. J. Inf. Secur. 2020, 19, 303–310.
- Kaim, G.; Canard, S.; Roux-Langlois, A.; Traoré, J. Post-quantum Online Voting Scheme. In Financial Cryptography and Data Security. FC 2021 International Workshops; Springer: Berlin/Heidelberg, Germany, 2021; Volume 12676, pp. 290–305.
- Kho, Y.X.; Heng, S.H. Comparison Analysis of Cryptographic Electronic Systems. In Proceedings of the 7th International Cryptology and Information Security Conference 2020, CRYPTOLOGY 2020, Putrajaya, Malaysia, 9–10 June 2020; pp. 151–164.
