Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Cyber–Physical Systems (CPS) connect the physical world (systems, environments, and humans) with the cyber world (software, data, etc.) to intelligently enhance the operational environment they serve. CPS are distributed software and hardware components embedded in the physical world and possibly attached to humans. CPS are vulnerable to security risks, which requires incorporating appropriate forensics measures in the design and operations of these systems.
- cyber-physical systems
- CPS
- digital forensics
- network forensics
1. Introduction
Cyber–physical Systems (CPS) provide useful integration and interactions between the physical and the cyber worlds [1]. CPS offer promising technology that adds many capabilities to different physical-based applications in diverse domains. CPS can be used to enhance automation capabilities in manufacturing processes for better productivity, efficiency, accuracy, safety, and reliability [2,3]. It can be used in healthcare applications to provide useful real-time services for patients and healthcare professionals [4,5]. CPS can be used in large commercial and residential buildings to improve energy efficiency and living/working conditions [6,7]. They can also be used in transportation systems to enhance safety and efficiency [8]. CPS utilize and integrate numerous technologies, features, and ideas from networking, distributed systems, sensors, embedded systems, software systems, and hardware devices such as microcontrollers and actuators. CPS also encompass different disciplines such as mechanical, biomedical, construction, systems, and electrical engineering along with healthcare, transportation, and energy fields to add value to applications in the physical world [9].
While CPS can offer many smart enhancements for improving physical systems and processes, they are, like any other computerized and distributed system, vulnerable to security attacks and criminal activities. Unlike other systems, however, security attacks may cause not only data, software and hardware damages but also major physical damages. These physical damages may include human deaths and injuries, infrastructure damages, loss of resources, and machine breakdowns or malfunctions. An interesting case involving a security attack on a CPS known as the Stuxnet worm is analyzed in [10]. The Stuxnet worm is a highly sophisticated cyber-attack using several security attack techniques with a specific goal of disabling a manufacturing facility. Another attack was discovered a few years later on the US power grid (Calpine Corporation, Houston, TX, USA) with the intentions of causing a major blackout in the country [11].
When a general-purpose software is attacked or breached, forensics (digital criminal investigations) will involve analyzing operational and access logs, tracking network traffic sources, and figuring out how it was done, who did it, and of course why. Forensics efforts will also use this information and additional software operational information to create defense mechanisms for future attacks. As the applications of CPS are rapidly being developed and deployed in different critical domains, various security measures are considered and included to protect them. Along with the security measures, it is extremely important that CPS also include suitable and effective forensics capabilities. These are critical, yet difficult to achieve, when attacks are detected and investigations to find the culprits and mitigate the damages are needed. In CPS, the forensics process becomes a much wider and more complex endeavor. Analysis, tracking, and investigations will have to cover all software and hardware components, digital and physical evidence, and all interactions across the whole system, which usually involves largely distributed and heterogeneous components. In addition, currently available CPS forensics methods rely mainly on traditional techniques that, despite their effectiveness in some fields, may not be effective enough for CPS forensics. As a result, CPS forensics can benefit from another native behavior/feature of CPS, which is access to huge amounts of data. Data collected before, during and after a security attack are available for analysis to arrive at more definitive forensics evidence. The key is to adapt forensics techniques and create new ones that can take advantage of these data.
2. Background
This section covers some related work and background information about CPS, forensics, and the relevant work in these fields.
2.1. Cyber-Physical Systems
CPS are networked embedded systems, categorized by solid and constant interactions between physical and cyber components [9]. CPS are being progressively utilized everywhere to enhance physical domains. A great part of CPS is designed to support smart and context-aware mission-critical applications [1]. Predefined objectives of the related application domain are realized through the monitoring and control processes, as provided by CPS. The control decisions are usually performed by the cyber world using smart algorithms constructed by software.
Unlike regular embedded systems, CPS are networked embedded systems that consist of several heterogeneous distrusted components. These components may be computing nodes, sensors, actuators, smart devices, and software. These components are connected through wired and/or different types of wireless networks, as shown in Figure 1. Both sensor and actuator components are tightly attached to their physical environment. Sensors and actuators provide the interface between the cyber world and the physical world. Sensors are used to monitor the physical world, while the actuators are used to manipulate the physical world. One or more computation units are used to execute control software for the environment. These computation units can be computers or microcontrollers.
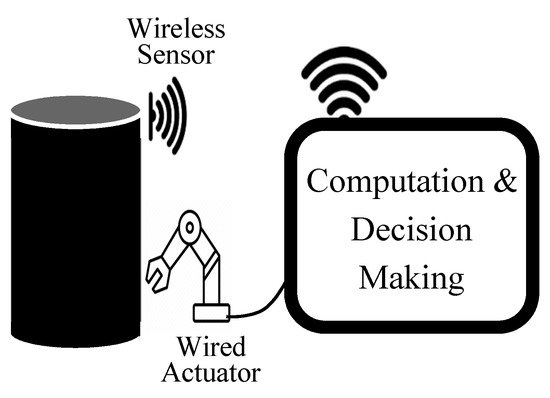
Figure 1. Cyber–physical Systems (CPS) components connected by wired and wireless networks.
The three main functions in CPS of operations are: monitoring using sensors, making decisions using smart software, and applying actions using actuators [12]. These three functions operate within a feedback loop covering the whole CPS as shown in Figure 2.
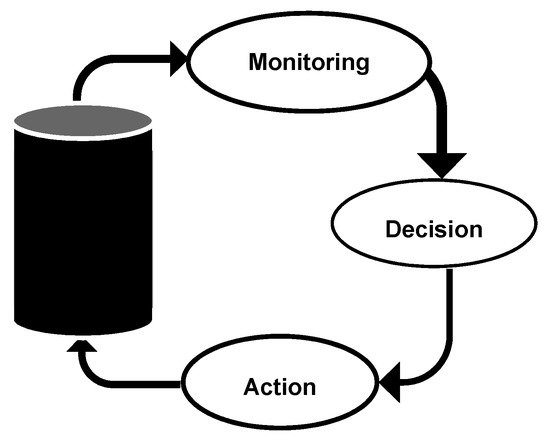
Figure 2. Closed-loop control steps of CPS.
Multiple connected CPS can also work together to complete a task or mission. These CPS form large-scale CPS that consist of multiple resources utilized for completing the assigned task or mission. Each CPS has its own sensors, actuators, and computation resources, but they need to work together. These CPS can be homogenous or heterogeneous in terms of their resources and capabilities. However, these collaborative CPS share their resources for the benefit of the application they are being used for. Such a system is referred to as a Collaborative Cyber-Physical System (CCPS) [13]. One example of CCPS is industrial collaborative robotic CPS that form the main requirement to create smart manufacturing [14].
CPS can also be connected to other systems such as cloud and fog computing to use the advanced services and large-scale resources provided by such systems. Cloud computing can provide scalable and flexible computational and storage services as well as advanced software services to support CPS. In smart manufacturing, for example, CPS collected data can be off-loaded to the cloud for storage and future analysis [15]. Fog computing can provide more localized services such as limited processing services, real-time services, data caching, short-term storage services, and efficient communication services [12]. In the smart manufacturing CPS, fog nodes can be the points of control and decision making based on the data collected locally in the area. Such functions require some storage and processing power but cannot tolerate the delays of using the cloud. When CPS utilize cloud and fog computing for their operations, they are referred to as Cyber-Physical Cloud Systems (CPCS) [16].
2.2. Forensics
Forensic science is an ancient profession associated with any type of criminal activity. Criminal investigations and the use of forensic science advanced a lot over time [17,18,19]. In the past few decades computers and software applications supporting forensics have been created and are in use for various activities such as facial recognition, DNA analysis, examining crime scene devices and content, and crime scene simulations [20]. Quickly, computers and computing devices became the crime scene for criminal activities such as stealing data, disrupting operations, or spying on others. Digital crimes led to the need for new and more sophisticated forensic approaches to computing devices, software, and data to collect evidence [21,22].
The technical and the law enforcement communities had to work together to address digital crimes and digital investigations. In addition, the legal system needed to extend some of its laws and regulations to incorporate these developments. A lot of effort and advances were made in this direction [23,24,25,26]. These rapid advancements in computing and technology increased the complexity of computer systems, and, as a result, forensics also became difficult and complex. A study of the historical development in this area is presented in [27]. A simple example to illustrate this is securing the evidence found. In a physical crime scene, the location can be isolated and access control is implemented. With digital crimes, access points to crime scenes can be unlimited and change can be done quickly and remotely. Investigators have to work methodically and fast to identify and isolate evidence before anyone can remove or modify it through digital means. This will involve severing all physical connections, disabling wireless connectivity, and possibly finding components (cyber and/or physical) that may change or destroy evidence. With CPS, the issues are combined and magnified, adding more requirements to achieve effective and efficient forensics.
2.3. Related Work
Several researchers investigated and highlighted the importance of securing CPS and the associated issues. General security issues and challenges in CPS are investigated by many researchers such as Humayed et al. [28], Ashibani and Mahmoud [29], Wang et al. [30], Alguliyev et al. [31], Neuman [32], Banerjee et al. [33], Burg et al. [34], and Cardenas et al. [35]. Some research efforts focused mainly on security for specific CPS applications. Sridhar et al. [36] and Sun et al. [37], for example, studied the CPS security of power grids. Huang et al. [38] investigated CPS security for industrial processes. Wells et al. [39] investigated the challenges of securing manufacturing CPS.
Other research efforts offered different techniques and frameworks to evaluate CPS security. Wurm et al. [40] investigated the security vulnerabilities of some implemented CPS from a cross-layer perspective. This investigation includes the CPS and the underlying hardware platforms. DiMase et al. [41] developed a system engineering framework to evaluate the well-being of CPS security. Hahn et al. [42] developed a framework for understanding cyber-attacks and the associated security risks to CPS.
Forensic issues and solutions were investigated in many emerging related areas. Some examples of these areas are in cloud computing [43,44,45,46], fog and edge computing [47,48,49], smartphones [50,51,52,53], and internet of things (IoT) [54,55,56,57]. Cloud computing, fog computing, smartphones, and IoT are usually components of and enabling technologies for CPS. Therefore, all their challenges will be inherited by the CPS using them. Moreover, there are two major differences between the forensics of CPS and those of the other technologies. The first one is that the forensics of the other technologies are mainly of the cyber/digital type. That is the issues investigated are mostly in the software part of the system or sometimes in the directly connected devices in this system. CPS forensics, in addition to the two types above, also involve forensics on the physical environment the CPS is serving. The second difference is that CPS operations rely heavily on the utilization of the feedback and control loops. These loops span all parts of the CPS (physical, cyber/physical, and cyber). This means that the effects of an attack may cause more damage or generate effects in areas not directly connected to the location of the attacks. This unique feature in CPS will also affect the methods by which forensic data are collected and preserved for analysis. These two differences create additional challenges for CPS forensics investigations. Yet, these same unique features in CPS create opportunities to create better proactive CPS security and forensics.
Some researchers also investigated issues and proposed solutions for forensics in specific areas of CPS. One area is concerning SCADA (Supervisory Control and Data Acquisition), which is used for monitoring and controlling industrial facilities such as oil and gas refineries as illustrated in [58,59,60]. Other areas include the electrical power grid [61], smart homes [62], smart cities [63], connected vehicles [64], and additive manufacturing systems [65]. However, these efforts were mainly investigating the cyber/digital and network forensics of the CPS applications in their respective domains.
3. Security Attacks on CPS
Implementing and deploying CPS solutions benefit many applications; however, they have major security risks if they are exposed. These risks may escalate to the levels of resulting in human deaths, infrastructure damages, and negative economic impact. In CPS both the cyber part and the physical part need to be protected from any possible attacks, since these can target the physical parts, the cyber parts, or both. In addition, the effects or damages from the attacks initiated on the cyber parts may propagate to the physical parts and vice versa. One example of such an attack is gaining unauthorized access to a control software function (cyber part) leading to the injection of fake control messages, such as one making one of the actuators in the CPS perform unwanted actions. Another example could be blocking a sensor (physical part) from obtaining the correct measurements for a specific condition which may lead the software to generate incorrect results or decisions leading the whole CPS system to operate in the wrong direction.
In actual incidents, many CPS security attacks targeted parts of the CPS that could lead to physical damages by directly attacking SCADA systems or the ICS (Industrial Control System) and affecting the actual operations of the industry. In some cases, the attack may target the computing infrastructure that runs and operates the control systems. Examples include the cyberattack on the Ukrainian power grid leading to massive power outages in 2015 [66] and the cyberattack on Saudi Aramco, where over 30,000 workstations were infected with a virus resulting in operational disruptions company-wide in 2012 [67]. Several additional examples are discussed in [68,69].
Attacks on CPS can be categorized into passive and active attacks and each has some different characteristics and effects. They also differ in modes such as sources, intentions, and targets. Each of these categories is further divided into several other types as shown in Figure 3. Different passive and active attacks can compromise different CPS components and some examples of these attacks are depicted in Figure 4. The attacks may target any or all components (cyber and physical) and have effects on both. For example, attacks on ICS affecting how the device/machine will behave; disrupting or modifying messages causing some software modules to trigger the wrong actions; and hacking into a video camera and using the videos to discover trade secrets. This is in addition to the more typical attacks on the software components.
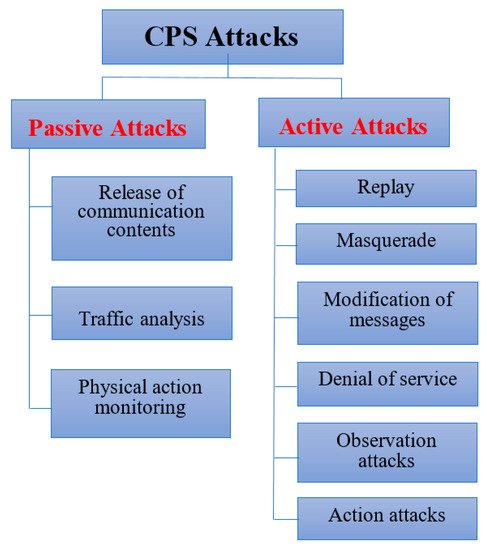
Figure 3. General CPS Attacks.
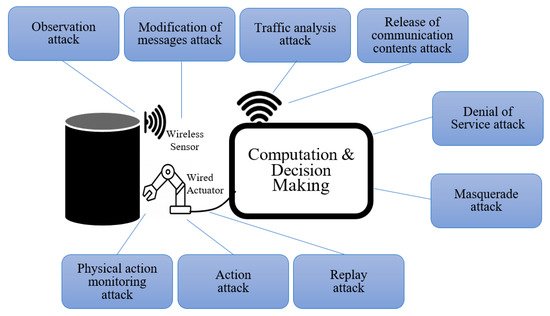
Figure 4. CPS components with possible passive and active security attacks.
3.1. Passive Attacks
Passive security attacks are recognized as attacks that provide access of some form to the CPS but does not directly affect it. Examples include eavesdropping and monitoring information transmissions; reading information stored in the system; or observing actions taken in the CPS. All of these activities will expose the CPS but will not cause any alternations or damages in the transmitted or stored information, or the CPS cyber or physical resources. As this category of attacks will not alter or damage the CPS and their operations, it is difficult to discover them. There are three possible outcomes of passive attacks: the release of communication contents; communication traffic analysis leading to, for example, trade secrets being exposed; and physical action monitoring that may help the attacker learn about operational procedures or trade secrets.
The release of communication contents will expose information that may be sensitive or private such as system information, control information, internal decisions, or other information among CPS components, among collaborative CPS, or between a CPS and other supported systems such as cloud and fog computing. Monitoring communication traffic allows intruders to know the contents of the communications in the CPS if the messages are not encrypted. If encrypted, the monitoring may not disclose the information, but can provide the intruders with the pattern of communication and sensing and control messages among different components of the CPS. Using this information, the intruders could identify the type of sensing or control messages, location of CPS components, and the type and frequency of current CPS operations.
Monitoring physical activities will allow the intruders to learn about the CPS activities and the actual operations taking place in the physical world. All of this can create multiple problems and consequences, such as violating the confidentiality of the system; violating the privacy of consumers, patients, or organizations; and enabling industrial and commercial espionage. Fortunately, many of the passive attacks can be thwarted by employing good physical security measures and using strong encryption/decryption methods for data in transit and at rest to hide exchanged information, control signals, and feedback content.
3.2. Active Attacks
The main characteristic of these attacks is that they will cause some form of alteration or damage to the CPS or some of its components. Intruders could attack by finding ways to access the system and alter communication messages, stored information, or actions to be taken. Unlike passive attacks, active attacks could be noticed relatively quickly through the alterations or damages they cause. There are six general types of active attacks on CPS: replay, masquerade, modification, denial of service, observation, and action attacks.
The first four types are attacks on the cyber parts, while the last two are physical attacks which require physical access to the system. In a replay attack, the intruder passively captures messages or action signals being exchanged and resends them in the CPS to create unauthorized outcomes including erroneous cyber or physical actions. The masquerade attack is when an intruder without any privileges or having limited privileges in the CPS impersonates entities with higher privileges to gain unheroized access and to gain access to restricted data or resources or conduct unauthorized actions. In message modification attacks, the intruders either alter, delay, or reorder some sensing or control messages to produce unauthorized cyber or physical actions. The denial of service attack is when intruders avert the regular use of CPS by flooding it with fake requests and message exchanges. This type of attack is usually performed by overloading some components of the CPS with messages greater than their capacity that will make the component and possibly the whole CPS stop or degrade operational performance. This is usually possible when the components of the CPS are connected through wireless networks or there are possible access points to the CPS components from outside the system (e.g., access through internet connections).
Observation attacks require intruders to have physical access to some sensing components in the CPS. The attack is performed by blocking the sensors or generating wrong observations through these sensors (e.g., deliberately increasing the heat near a temperature sensor to report an incorrect situation). Based on the wrong observations, the CPS may make incorrect decisions and take inappropriate actions (e.g., starting the sprinkler system in the area being monitored due to the faked high temperature readings). This type of attack usually starts as a physical attack but could quickly propagate to the cyber parts leading to software issues as well. The action attacks are also physical attacks targeting the actuators and action controllers in the CPS. Intruders may alter the actuator’s responses to change the outcomes of their operations. One example is changing the type of material in a 3D printer in the CPS so that the printed product will be faulty or will not match the specifications. Physical attacks cannot be performed without actual physical access to some CPS components.
Many methods to protect CPS from active attacks are possible such as ramping up physical security of the physical operational sites, implementing strong access and control policies, adding multiple message validation steps in critical parts of the CPS, and including active monitoring techniques in the CPS operations.
3.3. Attack Modes
CPS security attacks, whether passive or active, may come from different sources, have different targets, and have different objectives. Similar to other systems, CPS security attacks may be internal, external, or both. Internal attacks are the ones initiated by a user who is authorized to access CPS resources and services (an employee for example); nonetheless, they use these access privileges to attack the CPS. They may, for example, alter operations, use resources for alternate goals, or steal/corrupt data or information. On the other hand, external attacks are the ones initiated by unauthorized attackers without prior access privileges to the CPS, such as criminals, competitors, terrorists, or hostile governments.
CPS security attacks may also target different parts (physical or cyber) of the CPS or all of it. For example, some passive attacks may only target digital data, for example, obtaining personnel data or spying on the message exchanges in the CPS. While others are initiated to observe physical activities to learn about operations or steal trade secrets. One example of an attack targeting physical parts is described in [65], where a thermal video camera was used to record the process of printing an object on a 3D printer and using that to obtain a detailed view of the structure and design on the object. This is also an insider attack since the camera had to be installed at the 3D printing location and passive since it did not alter the original system attacked. Passive digital security attacks will directly target the data or computational components of the CPS to steal or learn secrets.
Active attacks also have many consequences on any and all the components of the CPS. These could vary from major physical damages and loss of resources (including humans) to minor annoyances. Some catastrophic physical effects could be an explosion in a manufacturing facility, altering the operations of some manufacturing machines leading to unnoticed changes in the product, that later could cause major damages where it is used (e.g., altering the design of a medical device that could result in patients death or injuries). On the other side of the spectrum, attacks could also cause digital damages at varying levels. It could be a complete wipe out of software components or data on one end, to minor alterations of some interface layout. However, most damages in one type of resource will eventually lead to damages in the other. For example, losing some control data may lead to incorrect or delayed physical actions that may cause damages or problems. Furthermore, attacking sensors in the CPS by blocking their sensing mechanisms is a physical attack that could lead to incorrect data and incorrect results. Major examples here are the Stuxnet attack [10] and the Calpine Corporation [11]. More analysis of the propagation of attacks’ impact on CPS is presented in [70].
CPS that have direct links to humans, medical CPS for example, could suffer heavily from security attacks because the possibility of human harm is very high. In [71] the authors discuss four possible security attacks on implantable medical devices. One example discussed in the article is an attack on an implantable cardioverter defibrillator, where attackers were able to inject malicious messages that could change the devices treatment actions. Energy CPS can also be affected in many severe ways, but most will not likely cause direct human harm, except when power is lost in a critical situation such as a hospital operating room during surgery. However, massive infrastructure and loss of resources is possible. Plumer [72] discusses the possibility of causing a national blackout due to security attacks. With less severe effects, a water pipeline monitoring CPS failure due to a security attack may delay the discovery of leaks, alter pressure levels, or report nonexistent leaks; all of which can be verified and managed without major losses especially to humans. Table 1 provides a summary of major CPS applications covering their main objectives and potential security risks.
Table 1. CPS Applications Benefits and Potential Security Risks.
| CPS Applications | Major Objectives | Potential Security Risks |
|---|---|---|
| Medical CPS |
|
|
| Smart Buildings |
|
|
| Smart Grids |
|
|
| Pipelines Monitoring and Control |
|
|
| Smart Water Networks |
|
|
| Vehicular Safety |
|
|
| Smart Manufacturing |
|
|
| Self-Driving Vehicles |
|
|
| Intelligent Traffic Lights |
|
|
| Renewable Energy Production (Wind Farms, solar and Hydropower Plants) |
|
|
| Energy Efficiency in Data Centers |
|
|
| Greenhouse Efficient Controls |
|
|
The last factor to consider is one that many have not addressed or do not consider to be a security attack. This is whether the attack was intentional (pre-meditated) or non-intentional (accidental). The general trend is that any attack of any type and consequence is intentional. However, there are some possibilities of damages caused by an unintentional action or erroneous operations. For example, someone unintentionally forgetting to sign out of the system console, could lead to others exploiting the issue. Sometimes users may install or add something to a device that will later have some impact on the other software leading to damages. There is also the possibility of accidently copying or corrupting data or control signals leading to problems or damages. All these examples show that CPS forensics are also necessary to handle this type of issue. The main idea is that many damages assumed to be caused by a pre-meditated security attack could have simply happened by mistake. Therefore, forensics investigations should be carried out with the understanding of the possible discovery of an error or mistakes.
This entry is offline, you can click here to edit this entry!
